
Enhancing Security and Compliance with Database Audit for Apache Hive

Introduction
In today’s landscape, where data is a critical asset, ensuring its security and integrity is paramount. Database auditing plays a crucial role in this process, especially for large-scale data platforms like Apache Hive. This article delves into the basics of database audit for Apache Hive, exploring its importance, implementation, and best practices.
What is Database Audit?
Database audit is a systematic process of monitoring, recording, and analyzing database activities. It helps organizations track user actions, detect suspicious behavior, and ensure compliance with security policies. For Apache Hive, database auditing is essential to maintain data integrity and meet regulatory requirements.
Importance of Database Audit in Apache Hive
Security Enhancement
Database auditing in Apache Hive significantly boosts security. It allows administrators to:
- Track user access patterns
- Identify unauthorized data modifications
- Detect potential security breaches
The audit log can show suspicious activity if someone views important information at an unusual time. This may suggest that we need to conduct further investigation.
Compliance Management
Many industries must comply with regulations like GDPR, HIPAA, or SOX. Hive database auditing helps meet these requirements by:
- Recording all data access and modifications
- Providing detailed reports for auditors
- Ensuring data privacy and integrity
A healthcare organization can use Hive auditing to monitor who accessed patient records and when, to comply with HIPAA.
Implementing Database Audit in Apache Hive
Enabling Audit Logging
To start auditing in Hive, you need to enable audit logging. This involves:
- Configuring hive-site.xml
- Setting up an audit log destination
Here’s a basic example of enabling audit logging in hive-site.xml:
<property> <name>hive.server2.logging.operation.enabled</name> <value>true</value> </property> <property> <name>hive.server2.logging.operation.log.location</name> <value>/var/log/hive/operation_logs</value> </property>
After applying these settings, restart the Hive service. You’ll find audit logs in the specified location.
Configuring Audit Filters
To focus on specific audit events, you can configure audit filters. This helps reduce noise and capture only relevant information. For example, to audit all SELECT queries:
<property> <name>hive.server2.logging.operation.level</name> <value>EXECUTION</value> </property> <property> <name>hive.server2.logging.operation.verbose</name> <value>true</value> </property>
These settings will log detailed information about SELECT query executions.
Database Activity Monitoring in Apache Hive
Database activity monitoring (DAM) is a crucial aspect of database auditing. It provides real-time insights into database operations, helping identify potential threats quickly.
Key Features of DAM in Hive
- Real-time alerts
- Analyze user behavior.
- Privileged user monitoring
- Detailed audit reports
For instance, you can set up alerts for specific high-risk operations:
CREATE TRIGGER sensitive_data_alert AFTER INSERT ON customer_data FOR EACH ROW EXECUTE PROCEDURE send_alert();
This trigger would notify administrators whenever new data is inserted into the sensitive customer_data table.
DataSunrise: Advanced Audit Tool for Apache Hive
While Apache Hive offers built-in auditing capabilities, third-party tools like DataSunrise provide more comprehensive and user-friendly auditing solutions. DataSunrise’s audit tool for Apache Hive offers enhanced features for robust database activity monitoring and security.
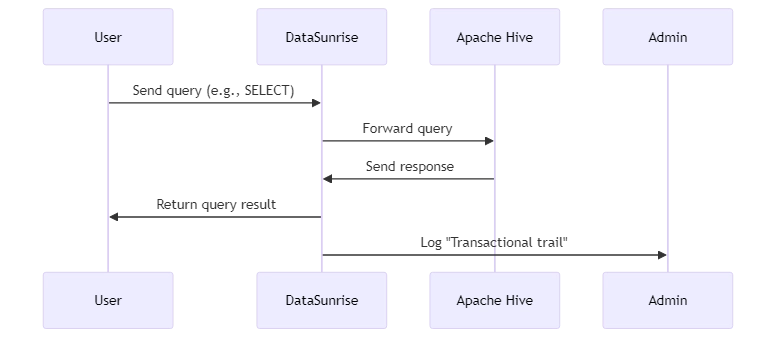
DataSunrise allows for easy creation of audit rules in Hive databases. For example, a rule can be set to audit any query involving CRUD operations (Create, Read, Update, Delete):
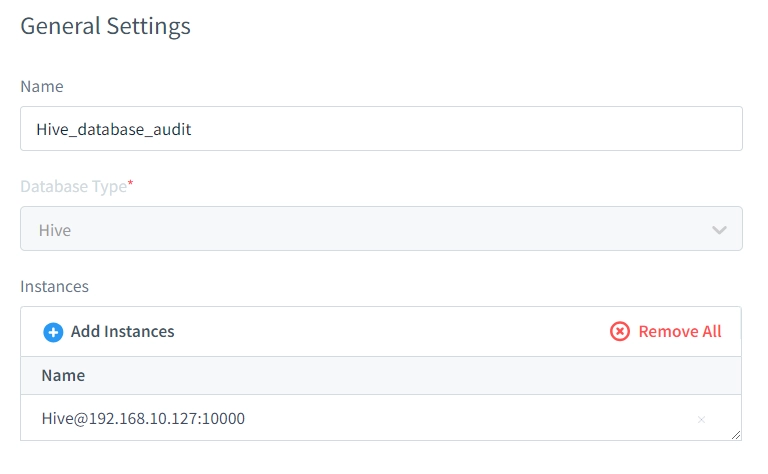
There we set up rule name “Hive_database_audit” and add instance for our Hive database
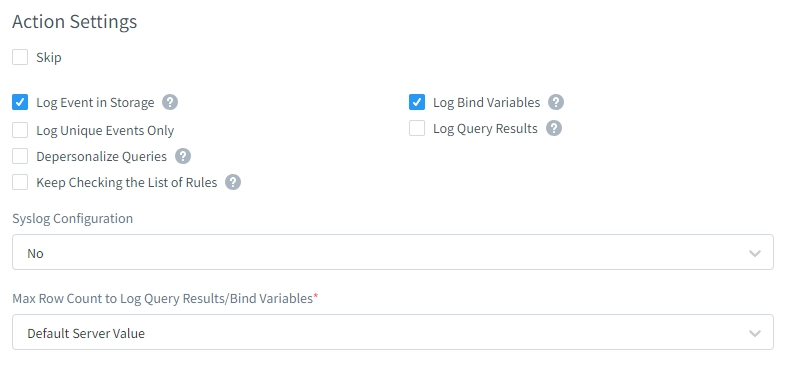
In this section we set up configs by default for auditing all queries in our Hive database
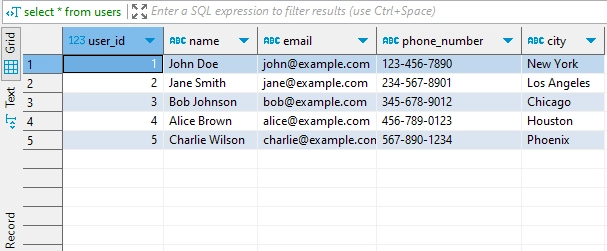
After executing a simple query:
select * from users;
DataSunrise captures detailed information about the transaction, including the query itself and other relevant data, in the Transactional Query section of the audit log:
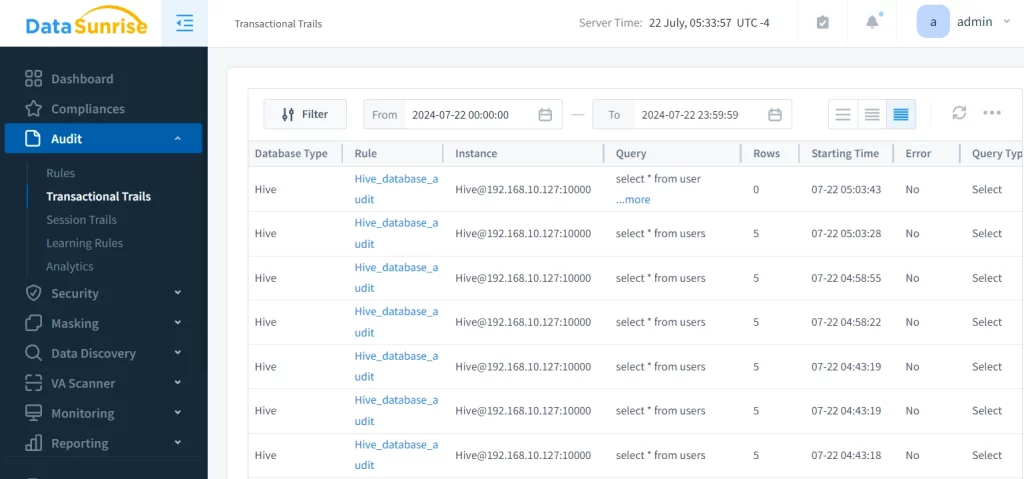
Transaction trails audit result: query itself and all necessary info that includes in audit.
For more information contact our team and check the demo.
Key Features of DataSunrise for Hive Auditing
- Real-time tracking: DataSunrise provides instant visibility into user actions on the database.
- Configuration monitoring: It tracks changes in database configuration and system settings, crucial for maintaining security baselines.
- Flexible storage options: Audit logs can be stored in the integrated SQLite database or external databases, offering scalability and integration with existing systems.
- Customizable audit rules: Administrators can create specific rules to audit transactions based on various parameters such as:
- Target database
- User identities
- Source IP addresses
- Client applications
Benefits of Using DataSunrise for Hive Auditing
- Comprehensive coverage: Captures a wide range of database activities, providing a complete audit trail.
- Easy compliance management: Helps meet regulatory requirements with detailed, customizable reports.
- Performance optimization: Offers efficient auditing with minimal impact on database performance.
- Advanced analytics: Provides tools for analyzing audit data, helping identify patterns and potential security threats.
By leveraging tools like DataSunrise, organizations can enhance their Apache Hive auditing capabilities, ensuring more robust security and compliance measures.
Best Practices for Apache Hive Database Auditing
To maximize the effectiveness of your Hive database audit strategy:
- Regularly review audit logs
- Use centralized log management
- Implement role-based access control
- Encrypt sensitive audit data
- Retain audit logs for an appropriate duration
Remember to balance comprehensive auditing with performance considerations. Over-auditing can impact system performance.
Conclusion
Database auditing for Apache Hive is a critical component of a robust data security strategy. It provides visibility into data access patterns, helps meet compliance requirements, and enhances overall security posture. By implementing proper auditing techniques and following best practices, organizations can significantly reduce the risk of data breaches and unauthorized access.
Remember, effective database auditing is an ongoing process. Regularly review and update your audit policies to adapt to evolving threats and compliance requirements. With the right approach, you can ensure that your Apache Hive environment remains secure and compliant.
Next
