
Database Audit for Azure SQL

Database auditing is a critical aspect of data security, particularly when dealing with sensitive data in cloud environments. For organizations utilizing Azure SQL, it is essential to implement robust database audit practices to monitor and track activity in the Azure SQL environment.
Azure SQL offers many ways to audit database activities. These include built-in auditing features, SQL commands, views, stored procedures, and Azure CLI tools to ensure a comprehensive database audit for Azure SQL.
This article looks at these features. It shows how to use SQL commands for auditing and monitoring database activities. The focus is on performing a thorough database audit for Azure SQL databases.
Why is Database Auditing Important for Azure SQL?
Data security and compliance are paramount for any organization managing sensitive information, and Azure SQL is no exception. Auditing for Azure SQL is a proactive security measure. It helps administrators track activities like who accessed data, when, and why. This helps detect potential misuse, unauthorized access, or any activities that could harm data integrity.
Effective auditing for Azure SQL is necessary to maintain compliance with regulations like GDPR, HIPAA, and others, which require organizations to monitor and protect sensitive data. A database audit provides valuable insights into user activity, helping organizations meet these legal obligations.
Azure SQL Data Audit Features
Before diving into SQL auditing methods, it’s essential to note the built-in Azure SQL data audit capabilities. Azure SQL has a built-in feature for database auditing that tracks events like login attempts, query execution, and schema changes.
You can set up auditing logs to store in Azure Monitor, Log Analytics, or Event Hubs. This gives you flexibility in how you capture and analyze data for a comprehensive database audit in Azure SQL.
For more detailed help on setting up Azure SQL data auditing, check out an article focused on this topic. Here, we focus on enhancing those capabilities with manual auditing through SQL commands, views, and procedures.
Auditing with SQL Language Features for Azure SQL
SQL Server provides powerful features for auditing, particularly through SQL language features like queries, views, and stored procedures. These features allow you to track and analyze changes directly within the SQL environment, which is crucial for an effective audit of Azure SQL databases.
Connecting to Your Azure SQL Database for Auditing
Before you start auditing, you need to connect to your Azure SQL Database. You can use a tool like SQL Server Management Studio (SSMS), Azure Data Studio, or Azure CLI to manage your database activities.
Example command to connect to your Azure SQL Database using Azure CLI:
az sql db connect --name <db_name> --server <server_name> --resource-group <resource_group>
Once connected, you can begin using SQL to check logs and monitor activities for your Azure SQL database.
Querying System Views for Database Auditing in Azure SQL
Azure SQL supports several system views that allow you to retrieve information about database activity, which is key for a successful database audit. For example, you can use the sys.dm_exec_sessions and sys.dm_exec_requests views. These views help you monitor session and request information.
Example SQL query to check active sessions:
SELECT session_id, login_name, host_name, status, start_time FROM sys.dm_exec_sessions WHERE is_user_process = 1;
This query will return active user sessions, which is a key part of tracking who is accessing your database.
Auditing DDL and DML Changes with Triggers in Azure SQL
For deeper auditing of Data Definition Language (DDL) and Data Manipulation Language (DML) operations, you can create triggers. For example, to track changes to a sensitive table, you can create an AFTER trigger. This trigger will log any insert, update, or delete operations as part of your database auditing in Azure SQL.
Example of an audit trigger for logging changes to a “customers” table:
CREATE TRIGGER trg_AuditCustomerChanges ON customers AFTER INSERT, DELETE, UPDATE AS BEGIN DECLARE @action VARCHAR(10); IF EXISTS(SELECT * FROM inserted) BEGIN SET @action = 'INSERT'; END ELSE IF EXISTS(SELECT * FROM deleted) BEGIN SET @action = 'DELETE'; END ELSE BEGIN SET @action = 'UPDATE'; END INSERT INTO audit_log (action, table_name, timestamp, user_id) VALUES (@action, 'customers', GETDATE(), USER_ID()); END;
This trigger will log all changes to the “customers” table in the “audit_log” table. The system will track the action type (INSERT, UPDATE, DELETE), the time of the action, and the user who made the change.
Using Stored Procedures for Database Auditing in Azure SQL
Stored procedures provide an excellent way to centralize your auditing logic. Database administrators can invoke them, or certain database operations can automatically trigger them, making auditing more efficient.
Example of a stored procedure for auditing:
CREATE PROCEDURE sp_AuditTableChanges @action VARCHAR(10), @table_name VARCHAR(100), @user_id INT AS BEGIN INSERT INTO audit_log (action, table_name, timestamp, user_id) VALUES (@action, @table_name, GETDATE(), @user_id); END;
You can call this stored procedure in your DML or DDL triggers. You can also run it manually whenever you want to log specific actions.
Azure CLI for Database Auditing
Administrators who prefer using the Azure Command-Line Interface (CLI) can set up and manage auditing easily. Azure CLI helps you manage audit settings, review logs, and run queries on your database. You can do this without needing a graphical interface.
Viewing Logs Using Azure CLI
You can use Azure CLI commands to review audit logs for your Azure SQL Database. First, ensure that you direct the audit logs to Azure Monitor or Log Analytics. Then, you can use a command like this to review logs:
az monitor log-analytics query -w <workspace_id> --analytics-query "AuditLogs | where OperationName == 'INSERT' or OperationName == 'UPDATE'"
This will return logs of INSERT and UPDATE operations, helping you track changes and identify potential security issues.
Benefits of Using DataSunrise for Azure SQL Auditing
SQL commands and Azure features are good for auditing. However, DataSunrise adds more value with its database security suite. DataSunrise helps organizations monitor, track, and secure sensitive data across their Azure SQL environment with a centralized approach to database auditing.
Centralized Control for Database Audits in Azure SQL
DataSunrise lets you manage all your database audits from one console. This gives you a clear view of all security events and database activities. This helps reduce the complexity of monitoring multiple databases and provides real-time insights into potential risks.
Enhanced Security for Sensitive Data in Azure SQL
DataSunrise offers tools to find and protect sensitive data in your Azure SQL environment. This includes personal information and financial records. These tools help you stay compliant with privacy laws. The data masking and encryption features help mitigate data breaches by obfuscating or encrypting sensitive data.
Simplified Compliance and Reporting for Azure SQL Auditing
With DataSunrise, you can easily create detailed audit reports. These reports help show compliance with regulations like PCI-DSS, GDPR, and HIPAA. You can customize these reports to fit your needs. This makes the auditing process quicker and more efficient for your Azure SQL audit.
Integrating DataSunrise with Azure SQL
If you already have DataSunrise installed, integrating it with your Azure SQL environment is straightforward. You can configure DataSunrise to automatically collect and analyze audit logs, monitor database activity in real-time, and alert administrators to suspicious actions in your Azure SQL database.
Creating a DataSunrise Instance for Azure SQL
To implement the DataSunrise solution with your Azure SQL environment, set up an instance through the Configuration menu for effective auditing.
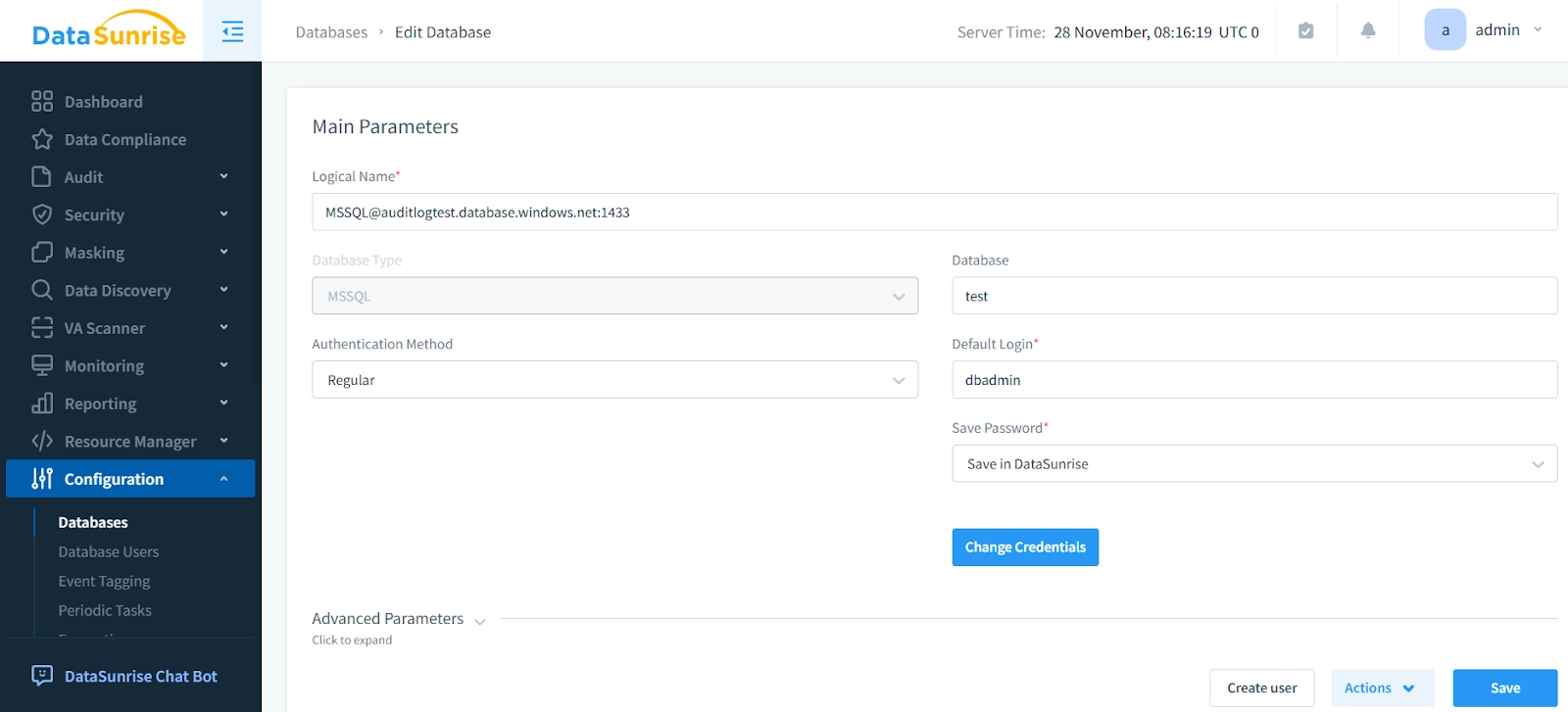
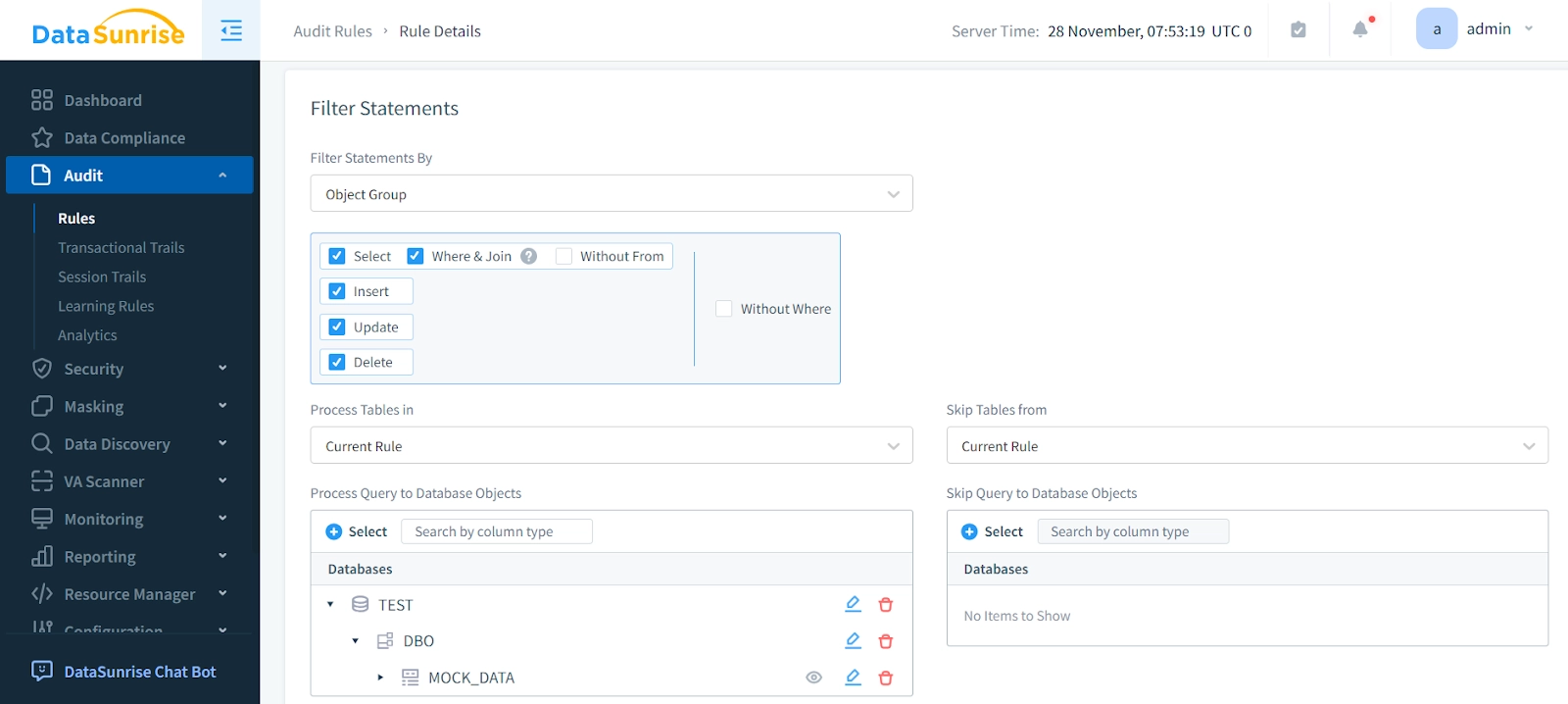
Creating an Audit Rule for Azure SQL
Follow these steps to create an audit rule:
- Navigate to the “Audit” section.
- Click “Rules”.
- Proceed to “Add New Rule”.
- Specify an audit rule, define clear objectives, configure the access controls and set up scheduled reports for auditing.
- Save and activate the rule.
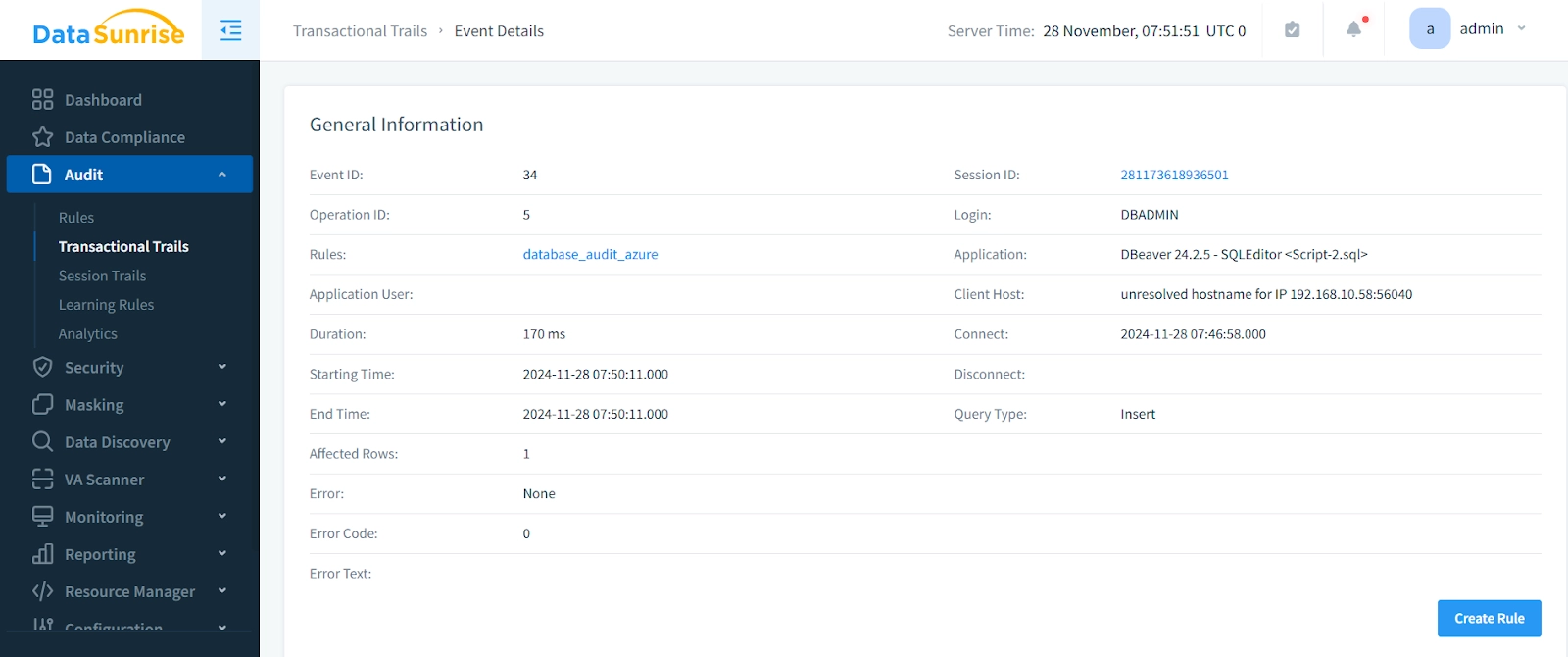
DataSunrise will now monitor your Azure database according to the defined rule.
Conclusion
Effective Azure SQL database auditing is a critical practice for securing your data and maintaining regulatory compliance. You can watch and check database activity by using SQL commands, system views, stored procedures, and tools like Azure CLI. Additionally, integrating a powerful tool like DataSunrise enhances your auditing capabilities, providing centralized control and protection for sensitive data as part of your comprehensive audit of Azure SQL databases.
As organizations use cloud-based solutions like Azure SQL, it is important to have strong auditing practices. This helps protect against unauthorized access and keeps data safe. To learn more about DataSunrise’s advanced tools for database security, visit our website. You can schedule an online demo of our audit and compliance features for your Azure SQL auditing needs.
