
Database Audit for Couchbase
Computer systems can be at risk of security breaches. Researchers first noted this in IBM’s research papers from 1975, but people probably knew it before that. This important truth is still true today.
However, the stakes have increased a lot. The amount of sensitive data has grown from megabytes to petabytes in the digital age. As organizations increasingly adopt NoSQL databases like Couchbase, implementing robust audit mechanisms becomes crucial for security and compliance.
While Couchbase offers robust built-in audit and monitoring capabilities through its user interface, organizations often face challenges in more complex environments. Managing consistent audit levels across hybrid infrastructures can be challenging. This includes both on-premises and cloud deployments, as well as multi-database environments.
Moreover, maintaining uniform RBAC-based logging across these diverse systems poses additional complexity. DataSunrise addresses these challenges by providing comprehensive, standardized audit capabilities that seamlessly integrate across all deployment scenarios.
Understanding Database Auditing in Modern Infrastructure
Database auditing serves as your organization’s digital surveillance system. It tracks and records database activities, user actions, and system changes. For Couchbase environments, comprehensive auditing becomes even more critical due to its document-oriented storage architecture.
Modern auditing solutions must adapt to the unique challenges of NoSQL databases. They need to monitor both structured and unstructured data while maintaining performance and scalability. Organizations seeking robust security measures should consider implementing specialized auditing tools that complement native database capabilities.
Key Components of Couchbase Database Audit
Effective database audit for Couchbase focuses on several crucial elements. Access monitoring forms the foundation by tracking user interactions with the database. Change tracking ensures that all modifications to documents and structures get properly recorded.
Query analysis provides insights into database usage patterns and potential security issues. The security event detection system works continuously to identify and alert about potential threats and violations.
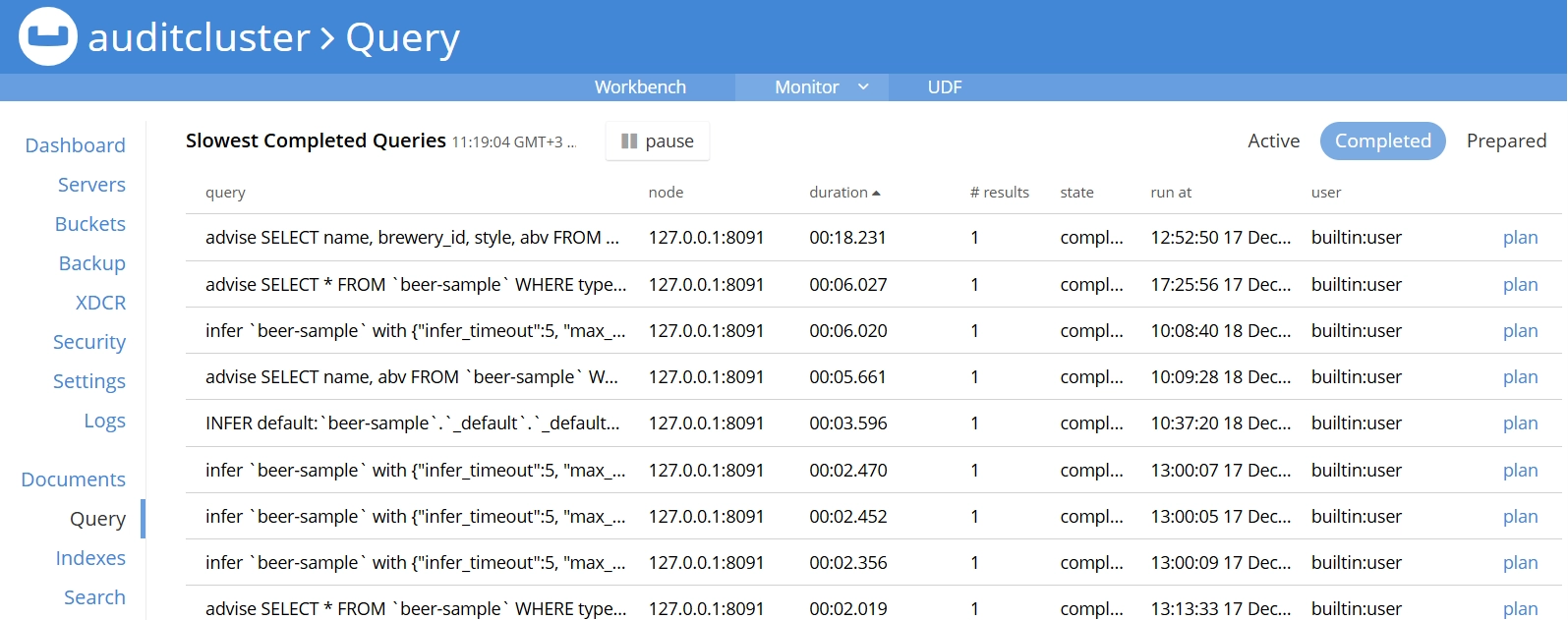
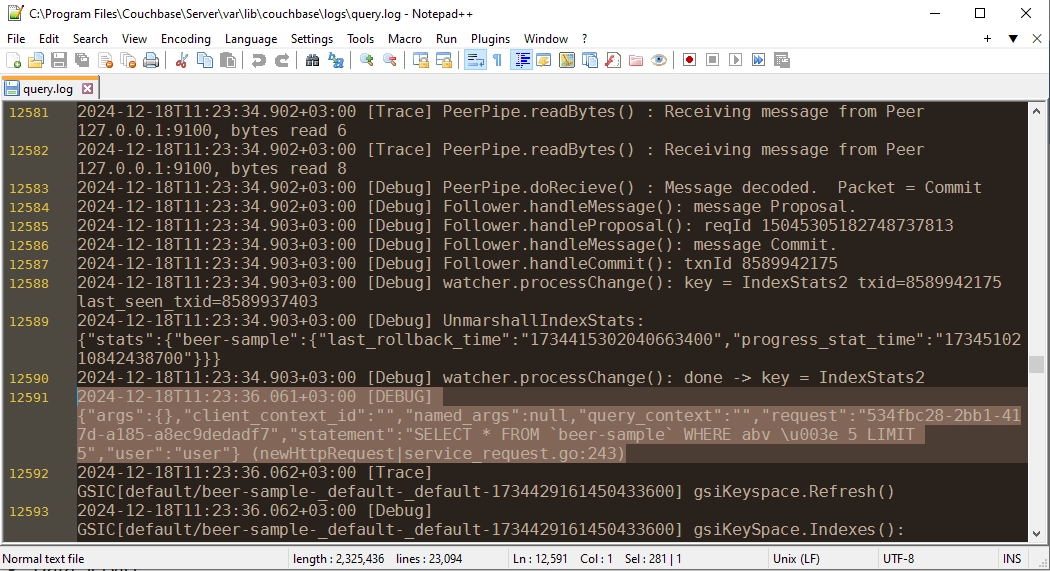
Couchbase maintains query history by default. Through the Security page, administrators can enable enhanced auditing features.
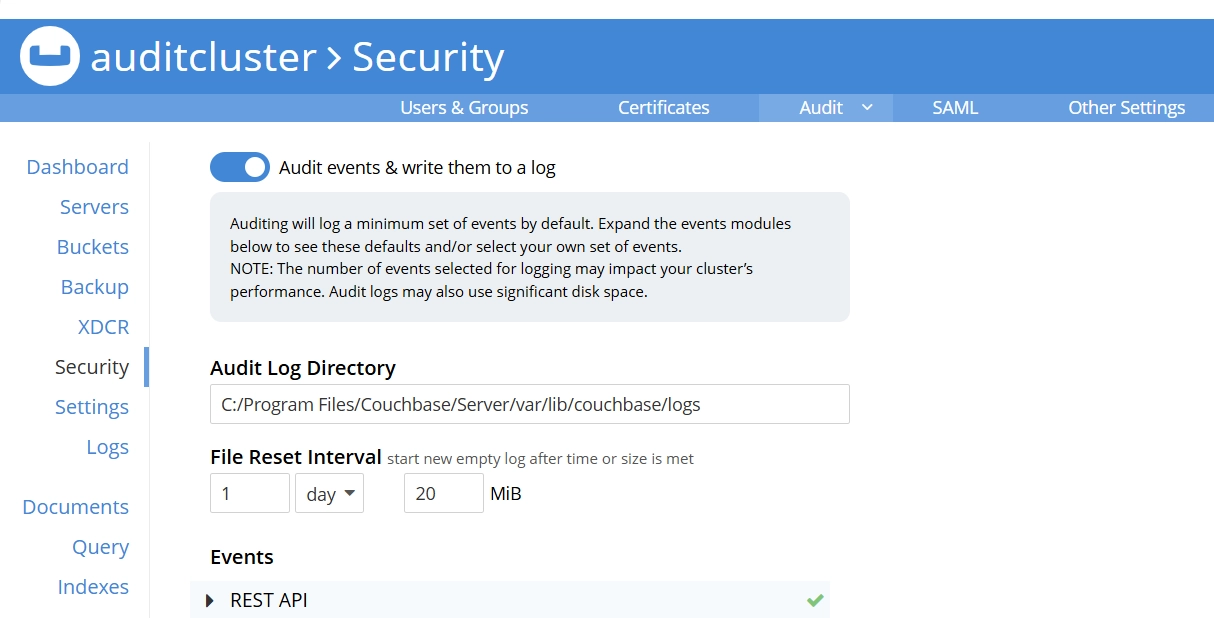
You can change the query logging detail levels for text file logs in Settings. Options range from ‘none’ to more detailed choices like ‘trace’ or ‘debug.’ This helps meet your specific monitoring needs.
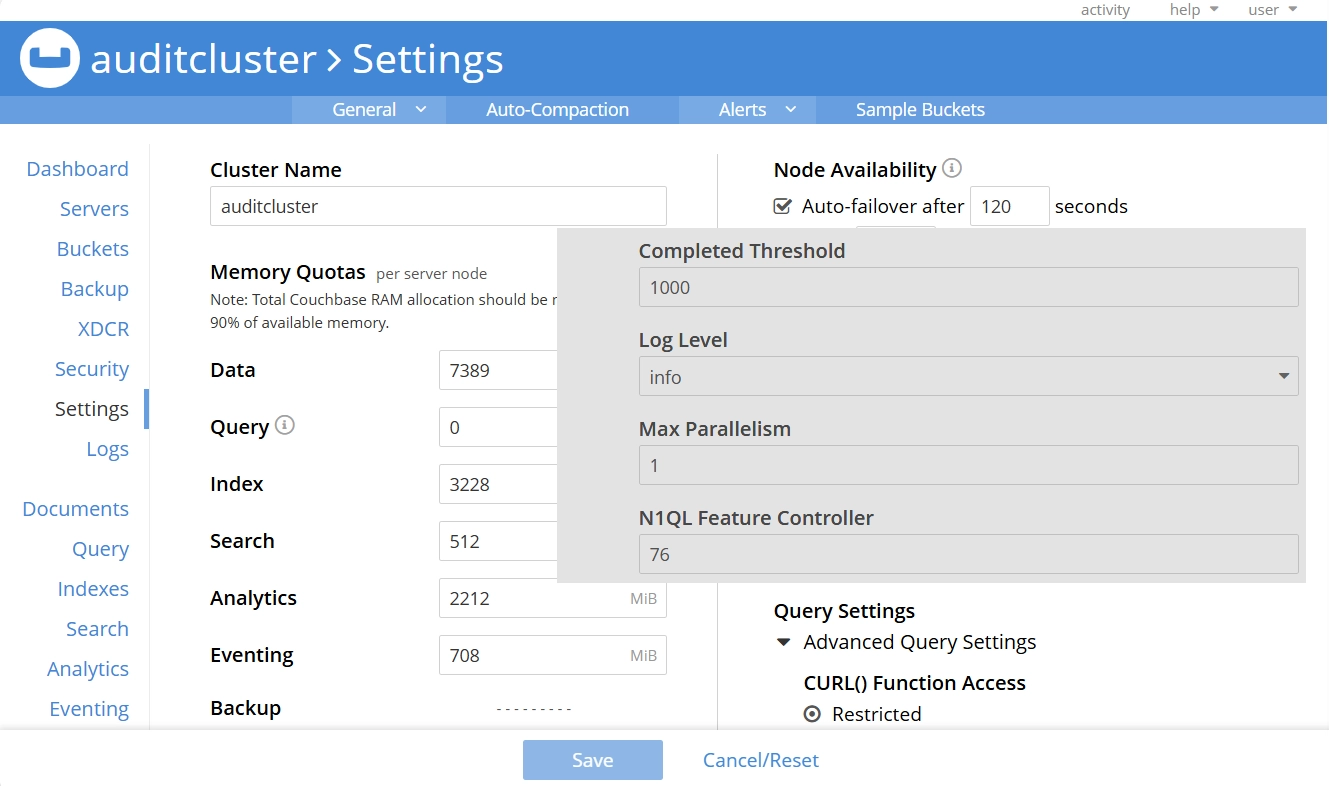
The log detail level can be configured through the dropdown menu, where ‘info’ is the default setting. This selection determines the granularity of logged information.
Beyond Native Tools: The Need for Third-Party Solutions
While Couchbase provides built-in auditing capabilities, organizations often require more robust solutions. Specialized third-party tools enhance security through real-time monitoring capabilities and advanced reporting features. These solutions integrate seamlessly with existing security infrastructure and allow organizations to implement customized audit rules based on their specific needs.
Compliance Requirements and Database Auditing
Modern organizations must comply with various regulations. HIPAA and GDPR stand out as two primary examples that demand strict data protection measures.
Meeting HIPAA Requirements
Healthcare organizations need to maintain detailed audit trails of all PHI access. The system must record who accessed the data, when it was accessed, what actions were performed, and which specific data was involved. Such comprehensive tracking enables healthcare providers to maintain compliance while protecting sensitive patient information.
GDPR Compliance Measures
The European privacy regulation requires organizations to maintain complete data access transparency. Companies must track data movement across their systems and document all processing activities. These requirements make robust database auditing essential for any organization handling European citizens’ data.
Advanced Auditing with DataSunrise
DataSunrise brings state-of-the-art security capabilities to Couchbase environments. The platform excels in providing comprehensive audit trails and real-time monitoring capabilities. Through automated compliance reporting and sophisticated behavior analysis, organizations can maintain robust security measures while reducing administrative overhead.
The Power of Uniform Auditing
DataSunrise stands out through its uniform auditing capabilities across different database platforms. This standardization makes security management more straightforward and efficient. Teams can monitor multiple database types through a single interface, streamlining compliance reporting and risk assessment processes.
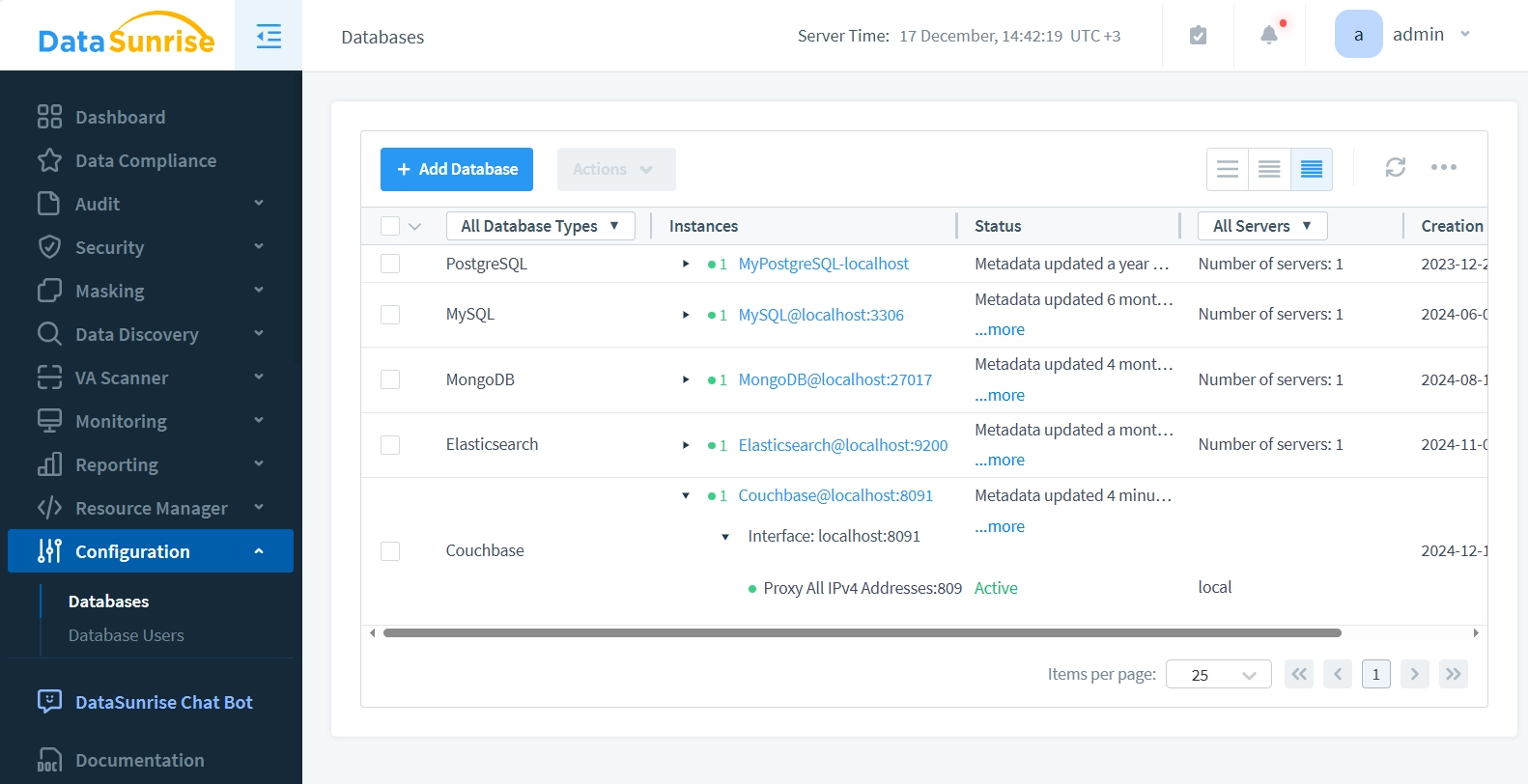
When a user connects to the Couchbase server using DataSunrise’s proxy port, all database queries can be checked. This is done based on the rules that have been set up. For example:
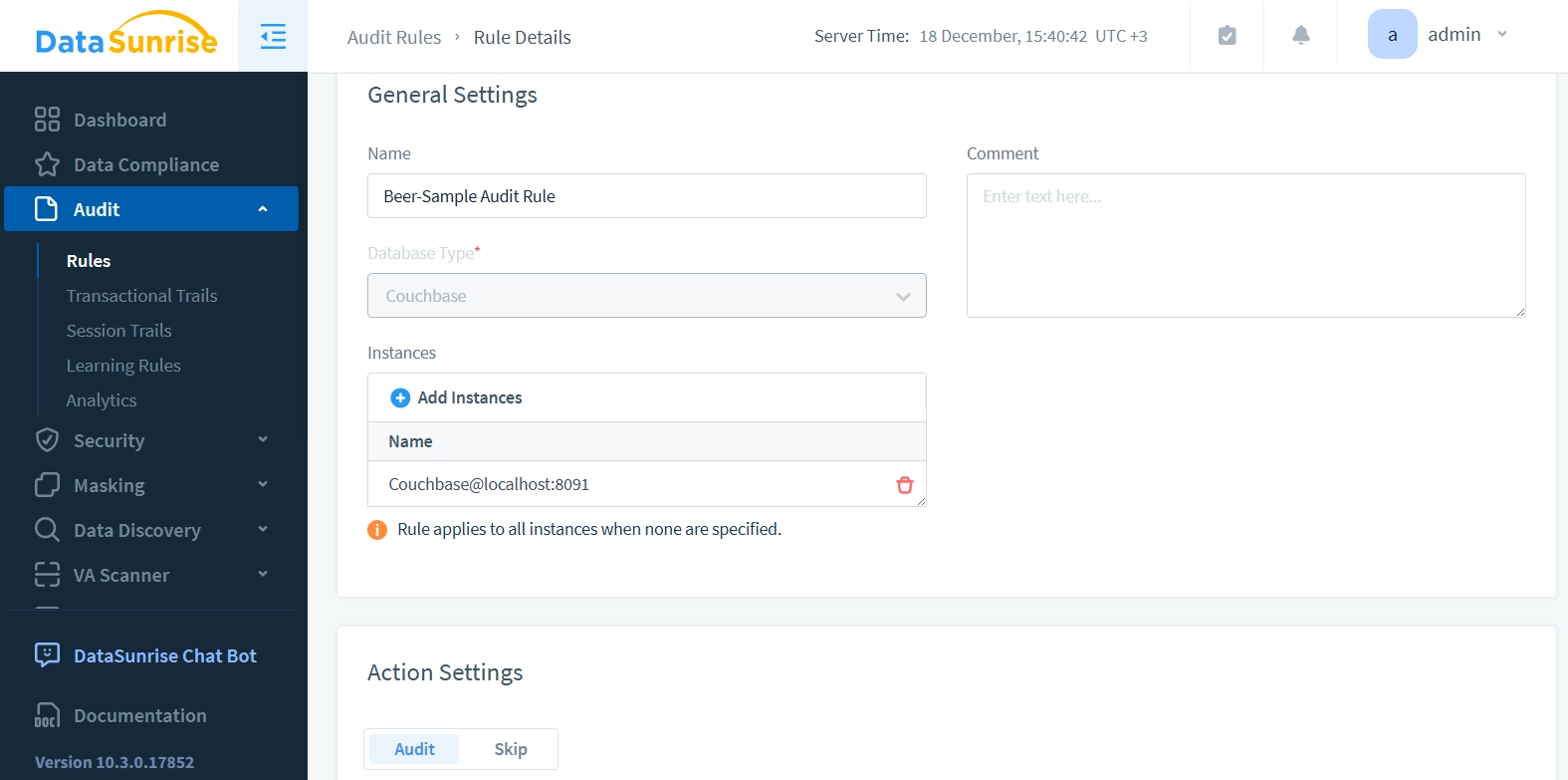
The Transaction Trail displays all queries from both Couchbase and other data sources where audit rules are enabled, providing comprehensive visibility across the infrastructure:
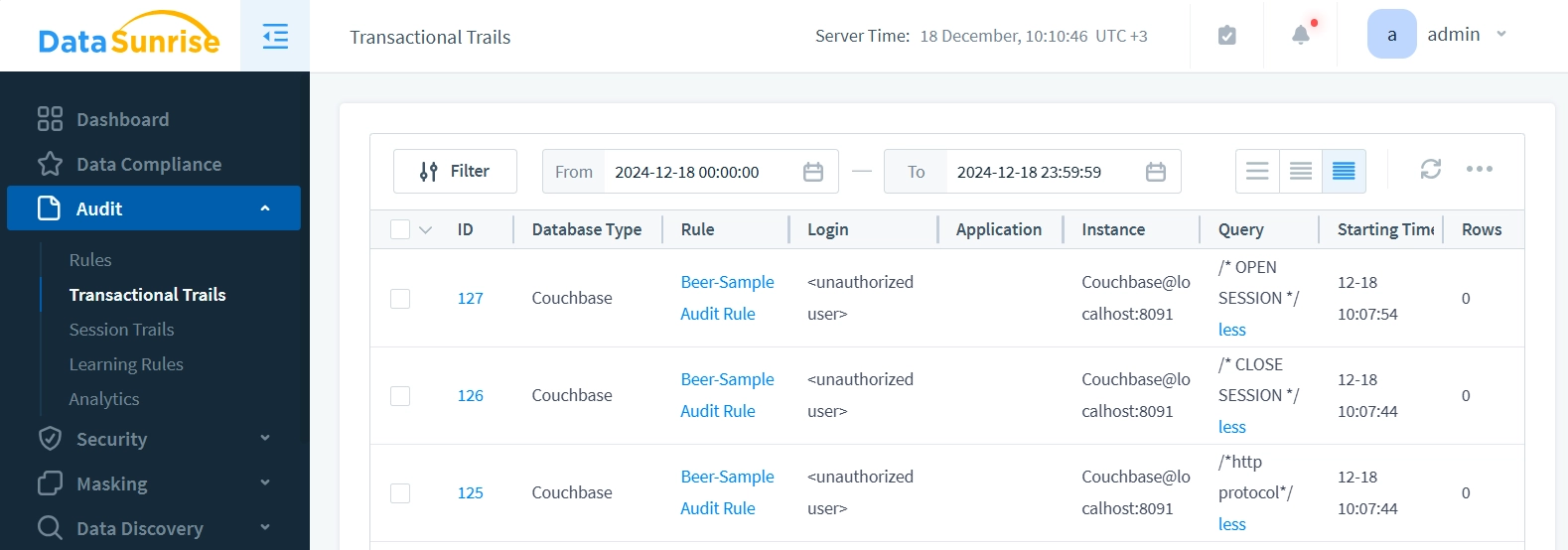
Click any Event ID in the Transaction Trail. This will show you detailed event information. You will see timestamps, query parameters, and execution details.
Enhanced User Experience through AI Assistance
DataSunrise incorporates an innovative LLM-based assistant that transforms how users interact with the platform. This intelligent guide helps users navigate the interface and understand essential security features.
The assistant helps make complex security ideas easier to understand. It breaks them down into simple terms. This method helps all users understand data protection and security. It doesn’t matter what their previous knowledge or experience in cybersecurity is.
The assistant explains these concepts clearly. It also gives detailed guidance on the features of DataSunrise, a strong data security platform.
Assistant guides users through each feature step-by-step. It shows how to use them to improve data security. This includes showing how to set up alerts for suspicious activities. For example, Assistant covers how to configure data masking to protect sensitive information.
Finally, it explains how to implement access controls. This ensures that only authorized personnel can view or change critical data.
By providing this support, the assistant makes it easier for teams with different skills to get started. The assistant helps all users, whether they have experience as IT professionals or are new to data security. It allows everyone to use the platform with confidence.
This inclusive approach creates a team environment. Team members can work together to protect their organization’s data. This leads to a more secure and strong data management strategy.
Overall, the assistant not only enhances the user experience but also empowers teams to take proactive steps in protecting their data, making DataSunrise a valuable tool for organizations committed to maintaining high standards of data security.
Best Practices for Database Audit Implementation
Successful database audit implementation requires careful planning and execution. Organizations should begin by defining clear audit objectives aligned with their security goals. Comprehensive logging must be implemented across all critical systems.
Regular reviews of audit logs help identify potential security issues early. The security of audit trails themselves must be maintained to prevent tampering. Finally, thorough documentation of all audit procedures ensures consistency and compliance.
Conclusion: Securing Your Couchbase Environment
Effective database audit for Couchbase requires a multi-layered approach. While native tools provide basic functionality, comprehensive solutions like DataSunrise offer the robust features needed for modern security challenges. The combination of advanced monitoring capabilities and user-friendly interfaces makes DataSunrise an ideal choice for organizations seeking to enhance their database security.
About DataSunrise
DataSunrise leads the industry in database security solutions. Our platform provides advanced activity monitoring and comprehensive vulnerability assessment capabilities. We offer dynamic data masking and sophisticated access control management features. Our real-time threat detection system keeps your data protected against emerging threats.
Ready to enhance your database security? Visit DataSunrise’s website to schedule an online demo and discover how our solutions can protect your valuable data assets.
