
Database Audit for MySQL

Introduction
In today’s business landscape, data is a critical asset. Protecting this valuable resource is paramount, especially databases. MySQL, a popular relational database management system, offers robust features for database auditing. This article explores the fundamentals of database audit for MySQL, helping you enhance your data security and compliance efforts.
What is Database Audit?
Database auditing is the process of monitoring and recording database activities. It involves tracking user actions, system events, and data modifications to ensure data integrity, security, and compliance with regulations. For MySQL, auditing helps administrators detect unauthorized access, track changes, and maintain an audit trail for forensic examination.
Key Components of built-in MySQL Database Audit
Audit Logging
MySQL provides built-in audit logging capabilities through its audit plugin. This feature allows you to capture various types of events, including:
- User logins and logouts
- SQL queries executed
- Schema changes
- Data modifications
However, it’s worth noting that you’ll need the Enterprise Edition of MySQL to enable the native audit extension.
You can easily enable the plugin by running the built-in MySQL script:
mysql -u root -p -D mysql < audit_log_filter_linux_install.sql
Enter password: (enter root password here)
Next, let’s set up additional log configuration:
audit-log-format=JSON audit-log-file=/var/log/mysql/audit.json
Here’s a snippet of what’s been logged:
[
{
"timestamp": "2024-10-03 13:50:01",
"id": 0,
"class": "audit",
"event": "startup",
},
{
"timestamp": "2024-10-03 15:02:32",
"id": 0,
"class": "connection",
"event": "connect",
},
{
"timestamp": "2024-10-03 17:37:26",
"id": 0,
"class": "table_access",
"event": "insert",
}
]
Event Filtering
Not all database activities require auditing. MySQL allows you to filter events based on various criteria, such as:
- User accounts
- Database objects
- Event types
To set up event filtering in the native MySQL audit, you’ll need to set additional parameters in either the /etc/my.cnf file or use stored MySQL procedures. For example, the following line in /etc/my.cnf will disable logging for the root user:
audit-log-exclude-accounts='root'
Log Analysis
Once you’ve collected audit logs, analyzing them is crucial. MySQL provides tools and techniques for efficiently analyzing logs:
- mysqlbinlog: A utility for processing binary log files
- MySQL Enterprise Monitor: A comprehensive monitoring solution
- Custom scripts using programming languages like Python or Perl
For instance, you can use the following command to view the contents of a binary log file:
mysqlbinlog /var/lib/mysql/mysql-bin.000001 | less
This file contains a log of various events and changes in the database.
Benefits of Database Auditing using native MySQL tools
By implementing native MySQL audit solution you can gain several advantages:
- Enhanced security: Detailed audit logs can help you prevent data breaches and unauthorized access attempts
- Compliance: the solution can help you meet regulatory requirements, such as GDPR, HIPAA, or SOX
- Troubleshooting: Identify and resolve performance issues or application errors.
- Data analysis: Audit logs can be used to extract various metrics
MySQL Database Audit with DataSunrise
While MySQL offers built-in auditing capabilities, third-party tools like DataSunrise provide enhanced functionality for database activity monitoring. DataSunrise’s audit tool for MySQL offers several advanced features:
Granular rule-based auditing
In DataSunrise, you can adjust audit settings by creating rules that monitor transactions based on specific criteria, such as IP address, application, or database username. Let’s create a simple audit rule to log all activity of the root user in the database:
You have a variety of options to choose from. In our case, we need to filter the connection sessions that should be audited:
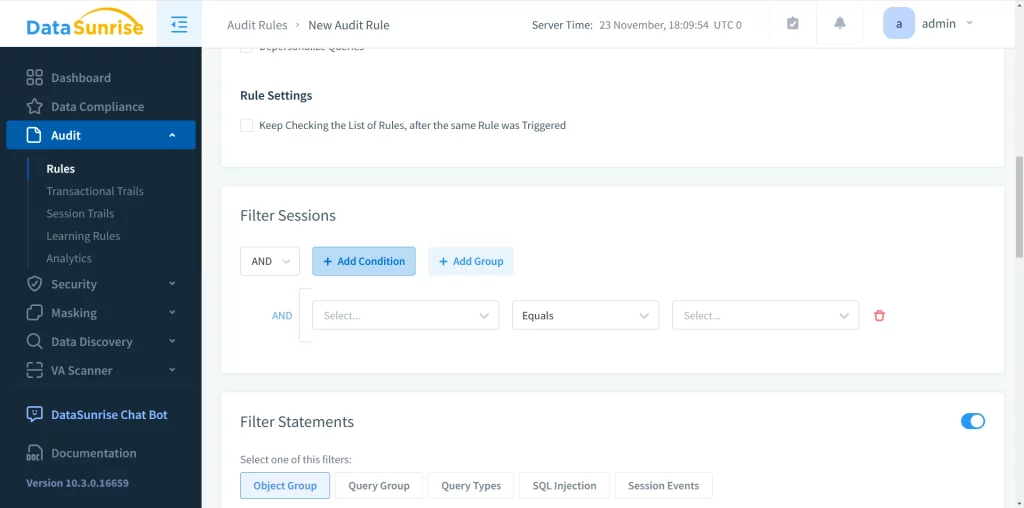
The process is straightforward: you set different filters and their values, then choose whether the filter should be inclusive (triggered by at least one condition) or exclusive (triggered only when all conditions are met). Below is an example of a session filter that audits all activity of the root user:
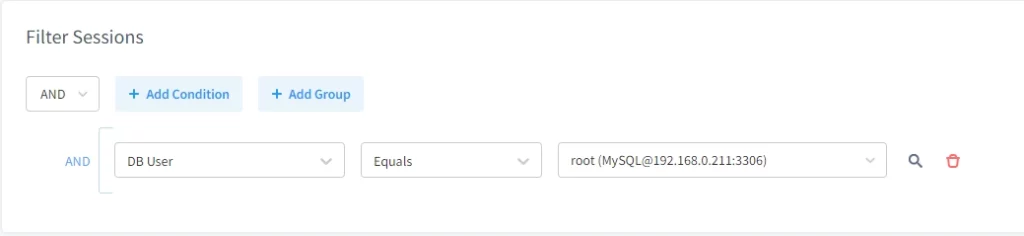
Now, we can track all activity of the root user in the “Transactional Trails” tab:
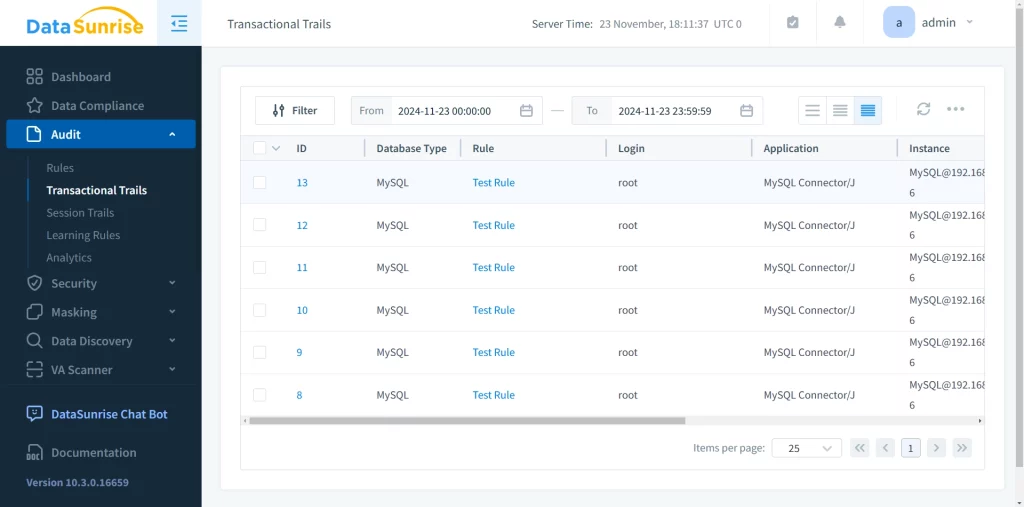
Advanced real-time tracking
With DataSunrise, audit logs are interactive, allowing you to explore the objects and users involved in a query. Let’s take a look at what has been captured by the rule we just created. To view the details, click on the rule:
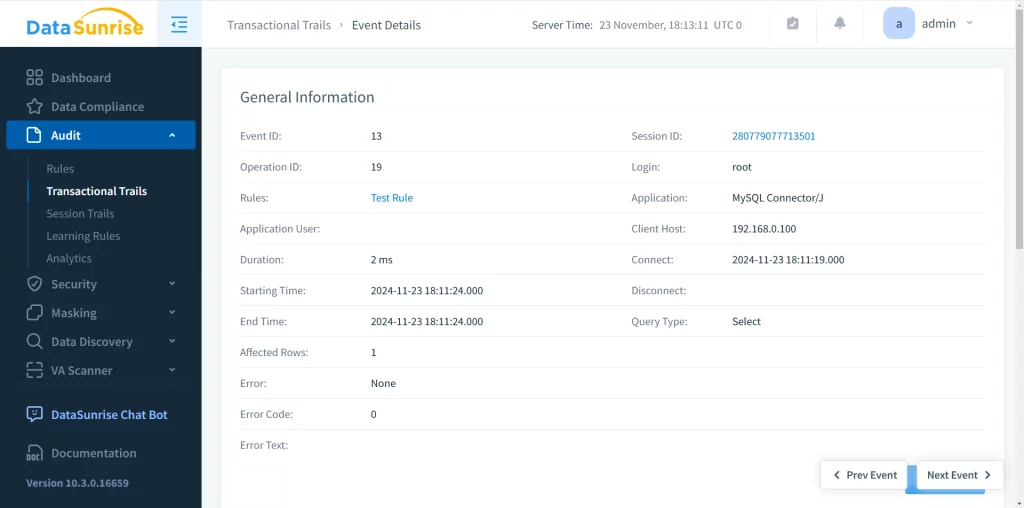
We can see general information and even automatically create another rule to monitor this kind of activity.
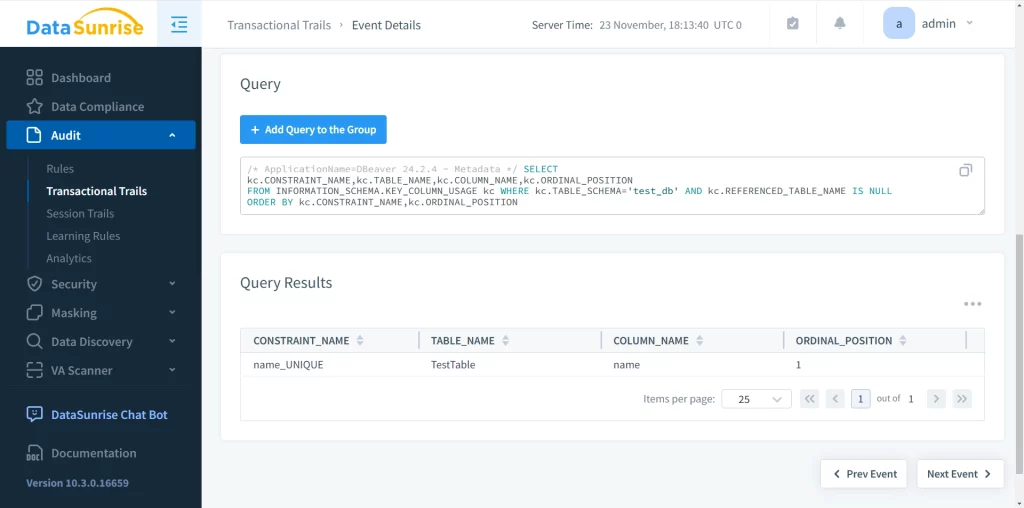
Additionally, we can see query content and its results. This is much more informative compared to a built-in MySQL database audit, which is only available in the commercial edition of MySQL.
Automatic discovery with Learning Rules
Learning Rules in DataSunrise allow you to create audit rules more efficiently. They enable the creation of Object/Statement groups, making it easier to apply different policies for auditing incoming database traffic.
For example, let’s create a similar learning rule to see what it learns from root user’s activity:
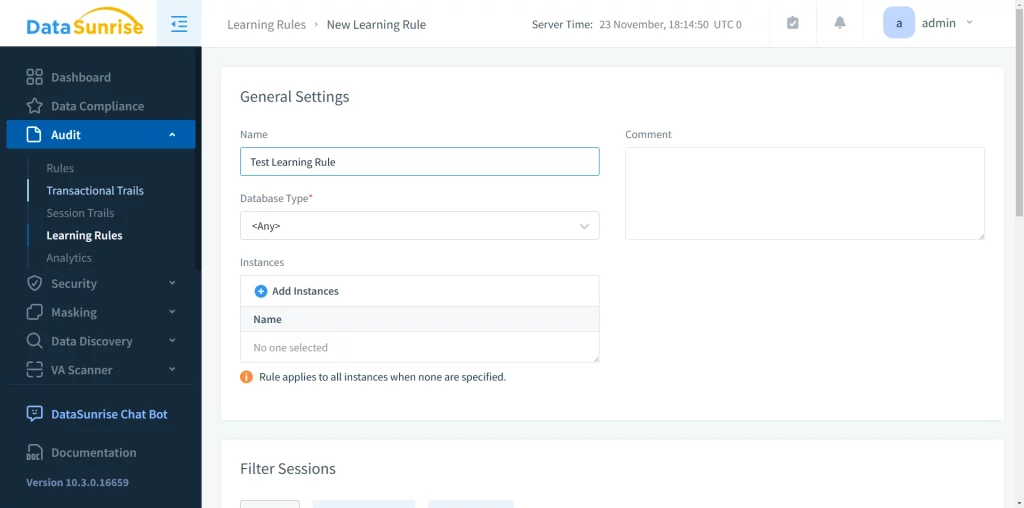
First, we need to configure filter sessions to monitor the activity of the root user:
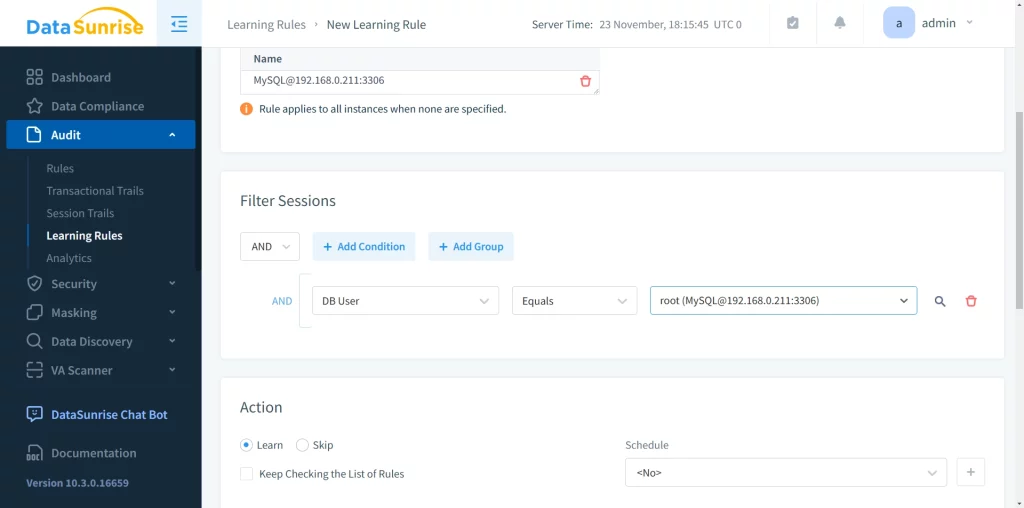
Next, we need to adjust the “Filter Statements” section to ensure the results are saved somewhere:
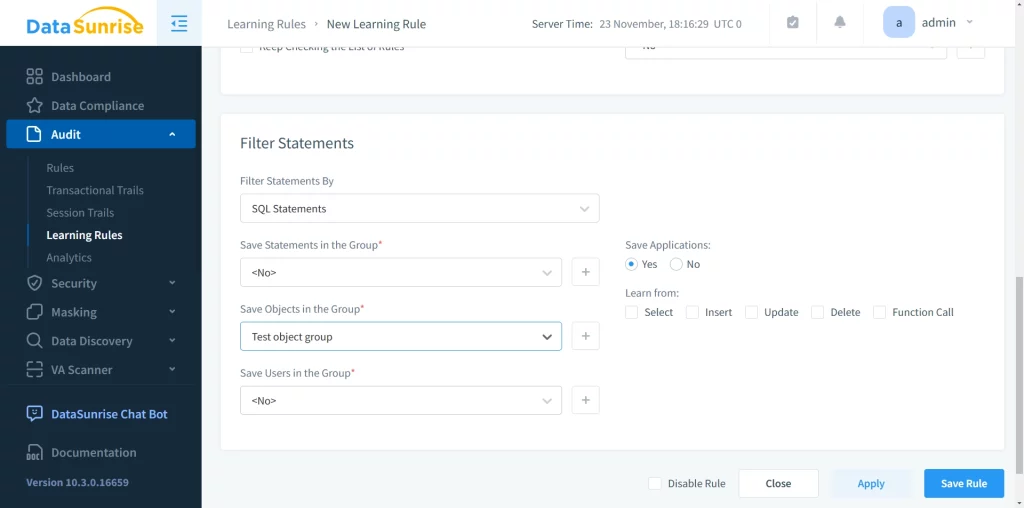
DataSunrise offers numerous options for filtering incoming activity and specifying where to save it. In this case, I’ve chosen to save the types of objects the root user interacts with.
After saving the rule and executing some queries as root, we can see what has been added to the object group we just created:
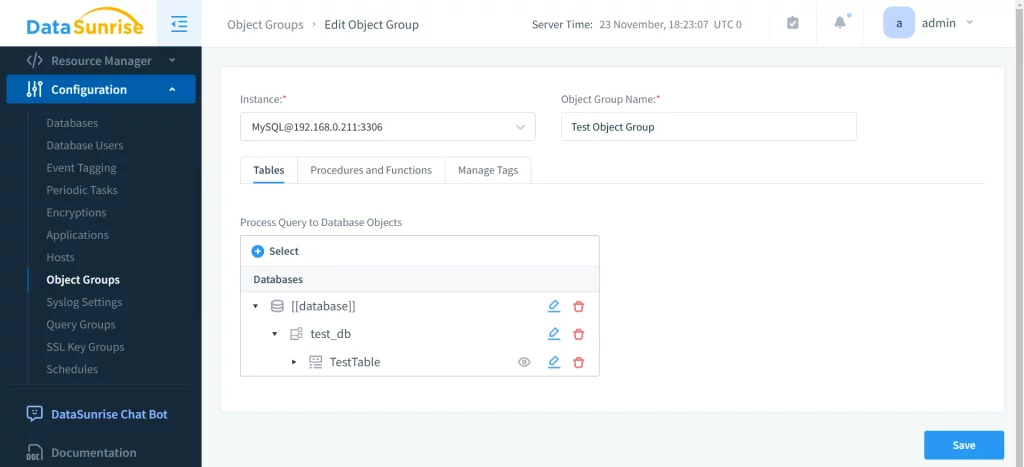
As shown, all the objects I interacted with have been added to this object group. Now, we can use this group to create a new audit rule for more granular exploration of activity.
DataSunrise has much more features for database auditing and security for MySQL. If you’re interested in more advanced security practices, be sure to schedule an online demo.
Database Audit for MySQL Best Practices
To maximize the effectiveness of your database auditing efforts, consider these best practices:
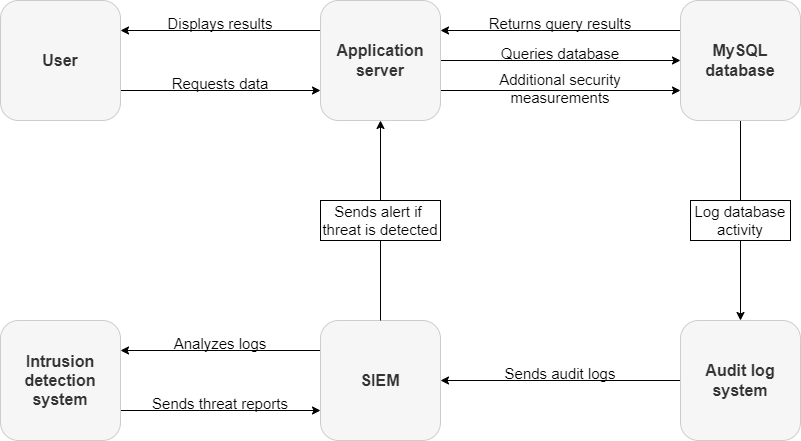
- Define clear auditing objectives
- Implement least privilege access
- Regularly review and analyze audit logs
- Secure audit logs from tampering
- Establish retention policies for audit data
- Integrate auditing with other security measures
Challenges and Considerations
While database auditing is essential, it comes with some challenges:
Performance impact: Extensive auditing can affect database performance.
- Storage requirements: Audit logs can consume significant disk space.
- False positives: Distinguishing between normal and suspicious activities.
- To address these challenges, carefully plan your auditing strategy and regularly fine-tune your configuration.
Conclusion
Database audit for MySQL is a crucial aspect of maintaining data integrity and security. By using auditing techniques, you can protect your data, follow rules, and learn about database activities. Remember to balance your auditing needs with performance concerns. Regularly review your auditing strategy to stay ahead of new threats.
