
Database Audit for Qdrant

Introduction
As organizations increasingly adopt AI and machine learning technologies, vector databases like Qdrant have become essential infrastructure for modern applications. Qdrant, designed to manage complex, high-dimensional data, powers recommendation systems, semantic search, and AI-driven personalization. While it excels at managing such data, when it comes to maintaining data governance and compliance database audit for qdrant introduces unique challenges.
Understanding Vector Data Compliance Challenges
Vector databases store data as mathematical embeddings rather than raw information. However, these embeddings often retain indirect but traceable links to sensitive data, raising significant compliance concerns. For example:
- Recommendation systems may encode user preferences and behaviors.
- Document search vectors can capture the semantic essence of confidential data.
- Customer similarity models may reveal patterns that inadvertently identify individuals.
Under regulations like GDPR and HIPAA, even indirect data representations may require auditing and protection if they can be traced back to individuals. For example, The GDPR Article 4(1) explicitly defines personal data to include any information that can lead to indirect identification of natural persons, setting a precedent for treating derived data representations as potentially personal data. data. That's why database audit for Qdrant and easy access to detailed audit trails becomes crucial when vector embeddings are derived from or could be linked to personal data, such as user behavior patterns, preferences, or transaction histories.
Database Audit for Qdrant with System Logs
Implementing database audit for Qdrant presents quite significant challenges, as the platform currently offers only basic system logging capabilities without comprehensive built-in audit functionality. These logs can help track operations, though they require substantial customization to meet compliance needs. Here’s a breakdown of the available sources and their coverage:
| Source | Coverage | Limitations |
|---|---|---|
| WebUI History | Queries executed via the WebUI console | Stored only in browser cache, lost when cache is cleared or accessed from other devices, limited to WebUI-only queries |
| Telemetry Data | Basic performance metrics (e.g., query completion times, types) | Logs only query types, not actual queries, lacks a detailed audit trail for compliance purposes |
| System Logs | Detailed records of query activities (operations performed, results) | Requires extra tools for filtering and querying, not structured for easy long-term retention or analysis |
Accessing Qdrant System Logs
When it comes to database audit for qdrant, utilizing system logs could be a good starting point. For Qdrant container-based deployments, these logs can be accessed via Docker commands:
# View logs directly
docker logs qdrant-container
# Follow log output in real-time
docker logs -f qdrant-container
# Export logs to a file
docker logs qdrant-container > qdrant_logs.txt`
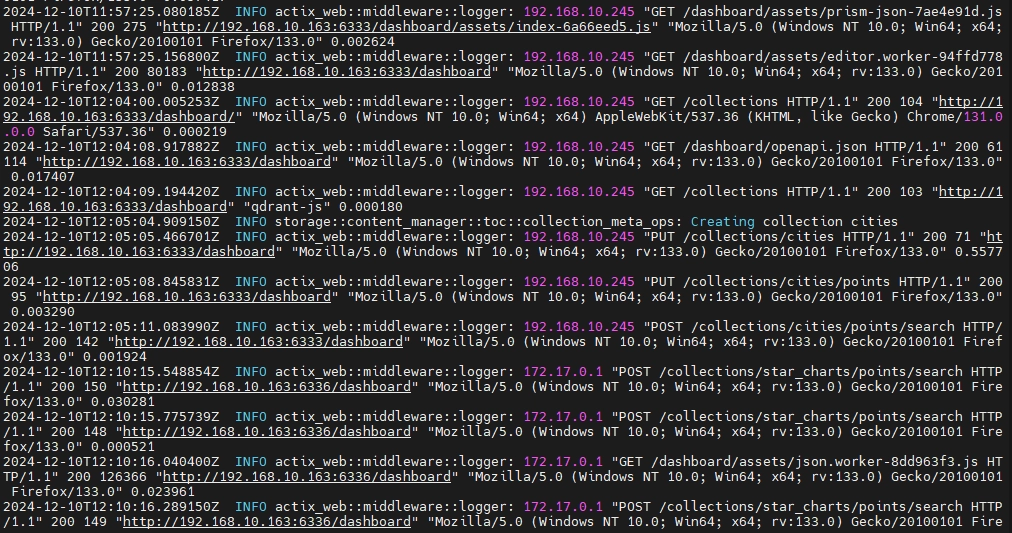
The actix_web::middleware::logger component logs HTTP requests, detailing origin IP, request method, status codes, and response times. However, logs are stored in plaintext, and JSON formatting is currently unsupported.
You can also use Linux utilities to query and format the logs in a more readable way, such as this example:
docker logs qdrant | grep "cities" | awk '{print $1, $2, $3, $4, $5, $6, $7}'This command filters the logs for the "cities" collection and formats the output to display only the selected columns, making the logs easier to read and analyze.

Available Log Data
System logs capture key activities, including:
- Collection creation and deletion
- Point insertions and updates
- Query and search operations
- Configuration changes
- Error events
Limitations of Qdrant logs include:
- No built-in audit-specific logging.
- Limited granularity in tracking operations.
- Lack of user action attribution.
- Logging capabilities are limited (plain text output, no rotation support, etc.)
- No built-in log analysis tools (for easy querying, filtering, etc.)
Summary
Overall, built-in system logs in Qdrant are fairly basic and very limited, you can read more about specific Qdrant configurations on their official documentation
Qdrant's built-in logging system offers only basic functionality with limited settings. For more details about available Qdrant configuration options, you can check their official documentation.
Addressing Audit Limitations
Given those limitations, a comprehensive database audit for Qdrant might require organizations to employ these strategies:
1. Custom Solutions
- Develop log collectors and processors tailored for Qdrant.
- Build dedicated audit trail databases for compliance.
- Design custom compliance reporting tools.
2. Third-Party Integration
- Use log management platforms for centralized storage and processing.
- Integrate Qdrant logs with SIEM (Security Information and Event Management) systems.
- Leverage compliance monitoring tools to meet regulatory requirements.
3. Architectural Modifications
- Implement proxy layers for detailed logging of user requests.
- Deploy authentication and authorization services for better control.
- Add dedicated audit logging services to track changes comprehensively.
Enhanced Database Audit for Qdrant with DataSunrise
Qdrant’s native logging features are basic and not sufficient for full compliance. DataSunrise, with its advanced tools, simplifies database auditing by offering robust monitoring, traceability, and reporting features.
Steps to Enable Qdrant Database Auditing in DataSunrise
Connect Your Qdrant Instance Easily link your database to the DataSunrise platform.
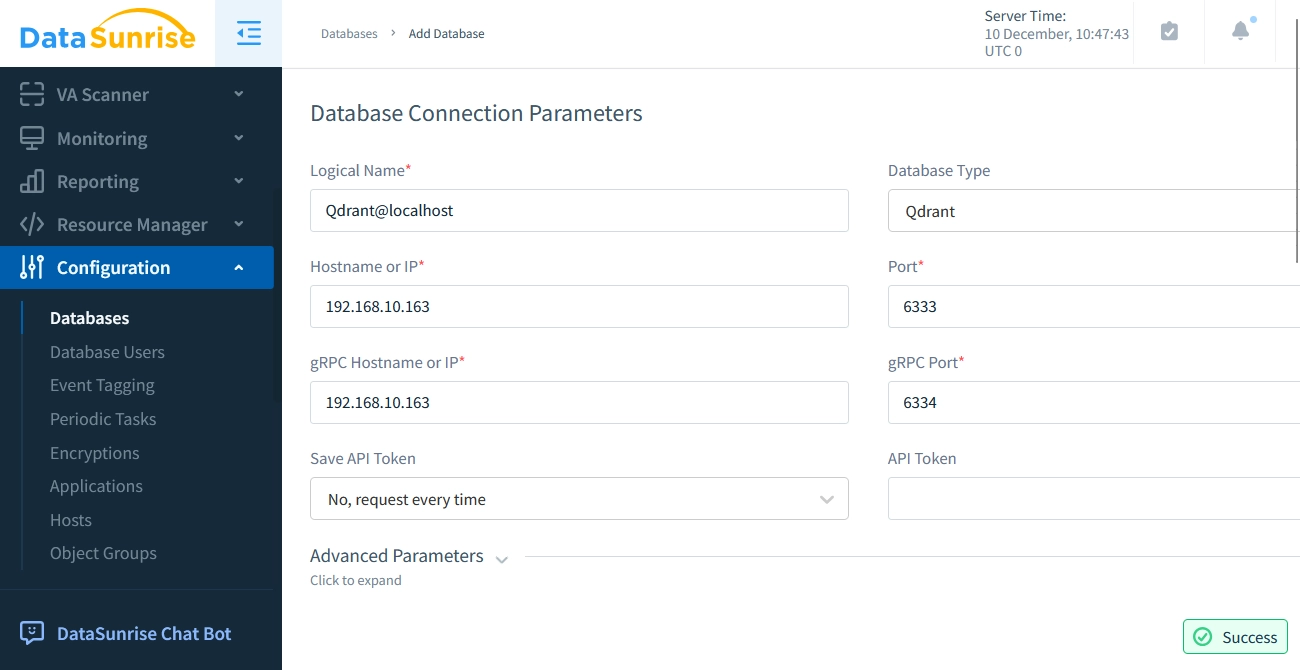
Connecting Qdrant Instance in DataSunrise Create Custom Audit Rules
Define rules to monitor specific activities or access patterns.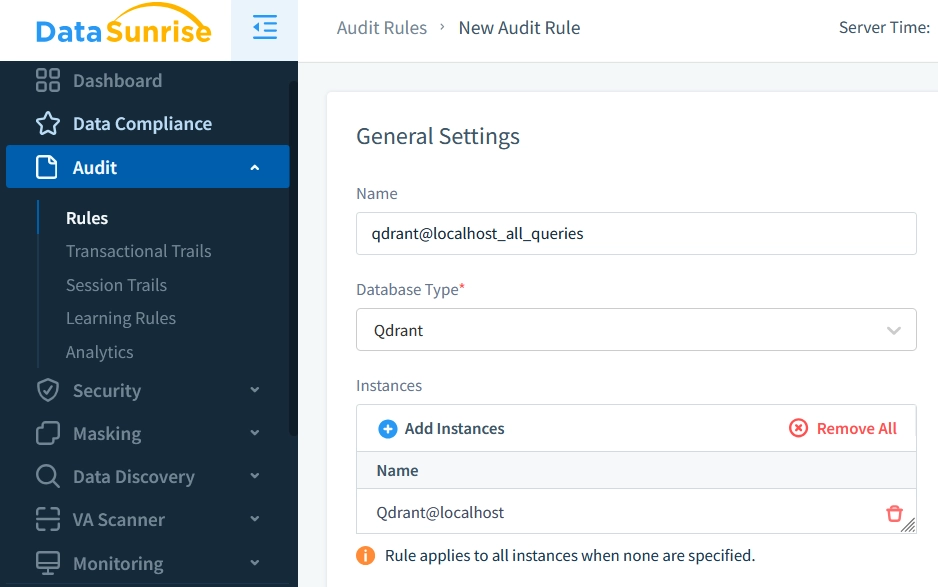
Creating Qdrant Audit Rule in DataSunrise Run Queries and Monitor Activity
Run some test queries to check that the audit rule settings were applied.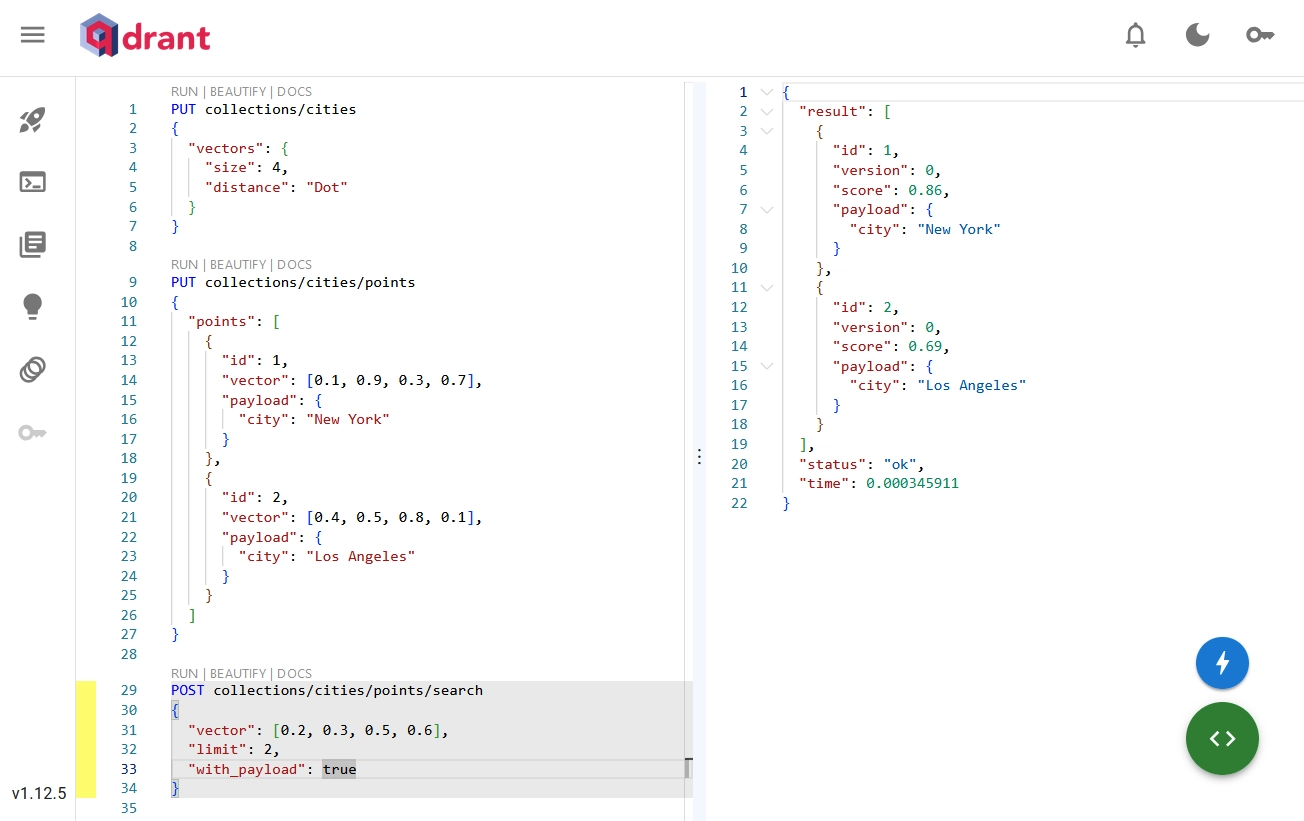
Sample Queries for Audit Testing in Qdrant WebUI Analyze Results
Open Transactional Trails in DataSunrise's Audit submenu to see detailed query history information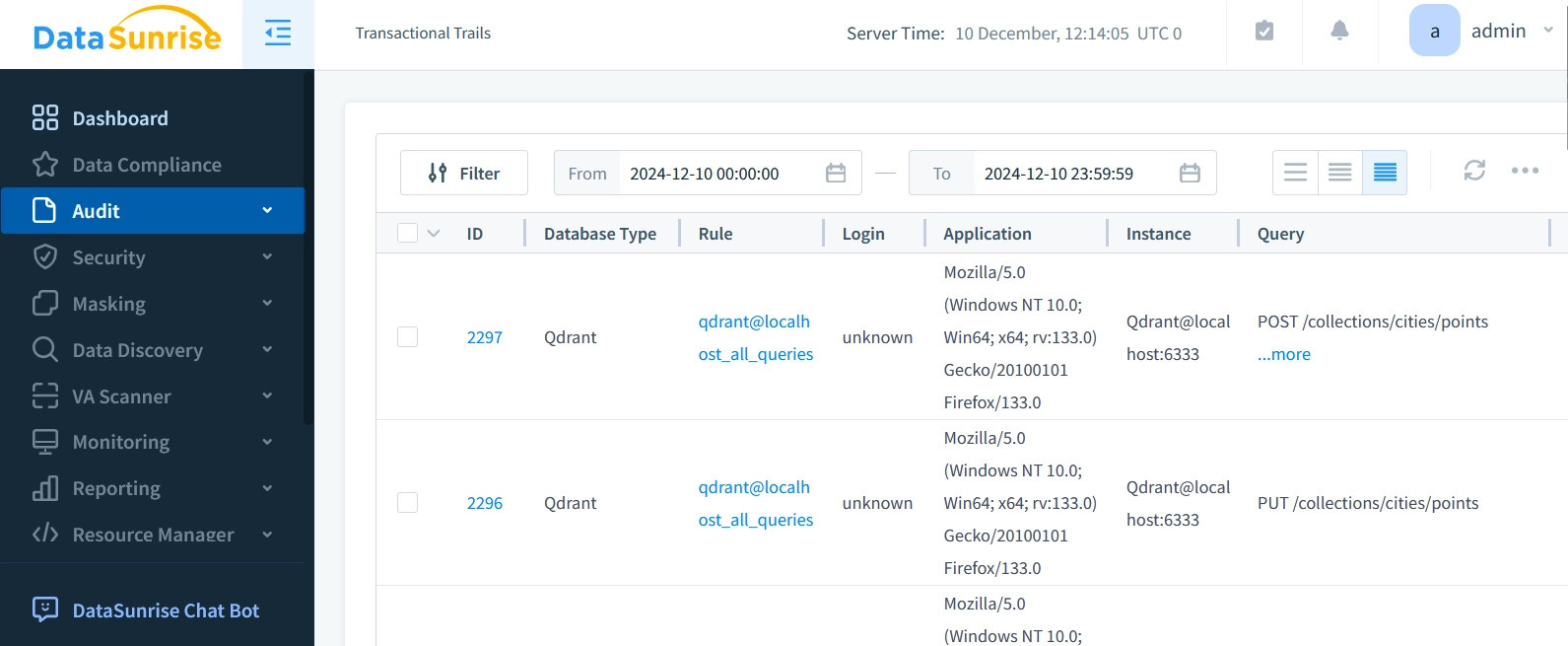
Qdrant Transactional Trails Captured in DataSunrise
DataSunrise offers extensive logging and query details, designed to meet all compliance and audit requirements. The auditing process can be quickly configured without the need for heavy development, integration of various different tools, or ongoing maintenance.
Audit rules are highly flexible, with a wide range of options, filters, priorities and constraints to tailor logging to specific needs. For instance, you can apply rules to particular database objects—such as sensitive data—or schedule audits to occur at specific times.
Additionally, the logs can be directed to designated databases and storage locations with customizable rotation settings to ensure long-term data integrity and performance. The logging mechanism is optimized for efficiency, allowing it to be deployed on a separate server using one of the various deployment modes, ensuring it suits your organizational requirements and development environment.
DataSunrise's additional benefits include:
- Detailed Audit Trail Management
Maintain comprehensive audit trails across all database instances and operations, with granular tracking of queries, access patterns, and modifications for enhanced accountability and compliance verification.
LLM-Powered Intelligent Rule Creation
Harness the power of large language models (LLMs) for automated, intelligent rule generation, simplifying complex database security configurations.Advanced Behavioral Analytics
Detect anomalies and safeguard your data with in-depth behavior pattern analysis, designed to proactively identify potential threats.Comprehensive Regulatory Support
Stay compliant with built-in support for a wide range of security standards and regulatory frameworks, offering peace of mind and streamlined operations.
DataSunrise: Greater Security and In-Depth Database Audit for Qdrant
While Qdrant is a powerful vector database, its native audit capabilities are fairly limited and quite basic, falling short of comprehensive compliance requirements.
DataSunrise addresses these concerns, offering advanced features for monitoring, security, and compliance. With its cross-platform support and flexible deployment options, DataSunrise provides a complete package to protect sensitive data, streamline audits, and safeguard against potential risks, all while ensuring compliance and operational efficiency.
Experience the benefits irsthand—schedule an online demo today and redefine your Qdrant auditing process with DataSunrise.
