
Database Audit for ScyllaDB

Introduction
In today’s data-driven world, organizations are grappling with petabytes of data. Consequently, the need to store and manage this data efficiently has never been greater. Leading IT companies are constantly competing to develop the most seamless and scalable solutions for managing large volumes of unstructured data, such as messages, logs, or sensor data. One of the most popular choices for distributed data storage is Apache Cassandra, a NoSQL database known for its scalability and fault tolerance.
However, a new contender has emerged: ScyllaDB. Promising to outperform Cassandra in terms of both speed and scalability, ScyllaDB is gaining attention for its high-performance capabilities and enterprise features, including native database auditing. In this article, we will explore ScyllaDB’s native audit capabilities and how they can be leveraged to enhance security, compliance, and operational transparency.
What is Database Audit?
Database auditing refers to the process of tracking and recording various database activities, such as login events, executed queries, and data modifications. Auditing serves multiple purposes, including:
- Regulatory Compliance: Ensuring that the database operations meet industry standards and legal requirements.
- Security Monitoring: Detecting and preventing unauthorized access or suspicious activities.
- Data Integrity: Maintaining the consistency and accuracy of data through comprehensive tracking.
- Sensitive Data Protection: Masking or logging access to sensitive information to prevent leaks.
While database auditing is a common practice in relational database management systems (RDBMS), it is less commonly available in NoSQL systems like ScyllaDB. However, ScyllaDB, in its Enterprise Edition, offers native auditing features that are built to meet the needs of security-conscious enterprises.
Native Database Audit in ScyllaDB
Native database auditing in ScyllaDB is available as part of the Enterprise Edition. It provides a powerful mechanism for logging and monitoring database activities, helping to ensure that sensitive data is protected and that compliance requirements are met.
By default, database auditing is disabled in ScyllaDB. To enable auditing, administrators must modify the ScyllaDB configuration file (scylla.yaml) and specify which events should be logged, as well as where the audit logs should be stored.
Configuring Database Audit in ScyllaDB
Here are the steps to enable and configure auditing in ScyllaDB:
- Access the ScyllaDB Instance: First, connect to the ScyllaDB container or instance where your ScyllaDB instance is running. This can typically be done through Docker or directly on a server hosting ScyllaDB.
- Edit the Configuration File: Open the
scylla.yamlconfiguration file, which is where you can enable and customize the audit settings.
docker exec -it <container_id> /bin/bash
nano /etc/scylla/scylla.yamlIn the configuration file, look for the following parameters and adjust them according to your needs:
audit: Set this parameter totableto enable logging to a specific table.audit_categories: Specify the types of database operations to audit. You can include categories likeDCL(Data Control Language),DDL(Data Definition Language), andAUTH(Authentication-related events).audit_keyspaces: Define the keyspaces for which you want to collect audit logs. For example, if you’ve created a keyspace calledmy_keyspace, specify it here.
Example configuration:
audit: "table"
audit_categories: "DCL, DDL, AUTH"
audit_keyspaces: "my_keyspace"- Save and Restart ScyllaDB: After making changes to the configuration, save the file and restart ScyllaDB to apply the new settings.
docker exec -it <container_id> supervisorctl restart scylla- Verify the Configuration: Once the changes have been applied, you can verify that auditing is working by connecting to ScyllaDB using cqlsh and performing some database operations, such as creating or dropping tables.
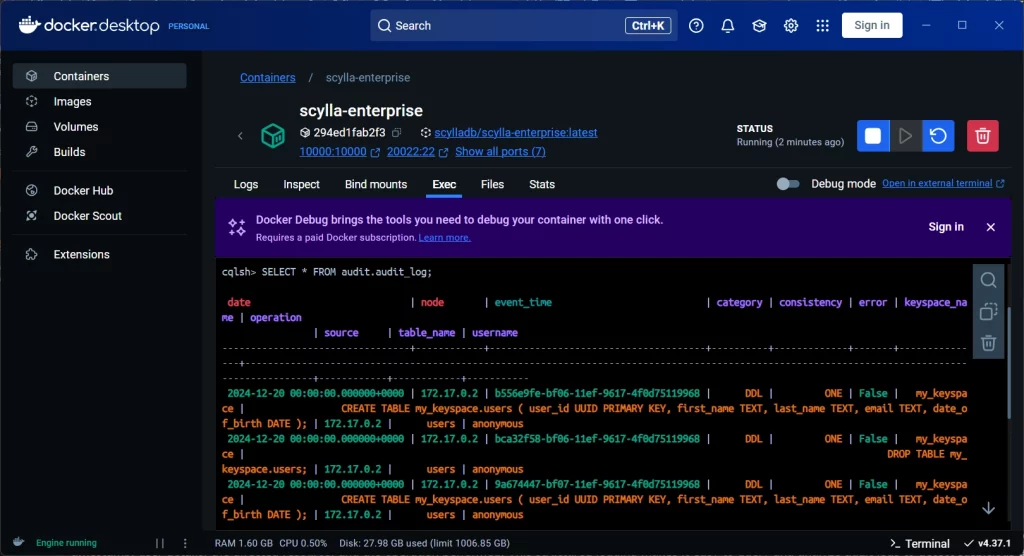
Example of creating a test table:
CREATE TABLE my_keyspace.users (
user_id UUID PRIMARY KEY,
first_name TEXT,
last_name TEXT,
email TEXT,
date_of_birth DATE
);After executing some queries, you can query the audit logs to check if the operations are being recorded.
Audit Categories and Customization
ScyllaDB’s audit feature provides flexibility in choosing which database operations you want to log. The available audit categories include:
- DCL (Data Control Language): Includes commands related to database permissions and access control, such as
GRANTandREVOKE. - DDL (Data Definition Language): Tracks schema changes, such as
CREATE,ALTER, andDROPcommands. - AUTH (Authentication and Authorization): Logs events related to user authentication and authorization, such as login attempts and permission changes.
These categories can be customized based on the organization’s needs. For example, if you only need to audit data schema changes, you can set the audit_categories to DDL alone.
Audit Table Structure
Audit logs in ScyllaDB are stored in a dedicated table that you specify in the configuration file. The default schema for the audit table typically includes columns for the event type, timestamp, user details, the affected resource, and the operation performed. This structured logging makes it easy to query and analyze audit logs to detect suspicious activity or compliance violations.
Integrating with DataSunrise
For enterprises that require advanced database security features, integrating ScyllaDB with DataSunrise Database Security provides enhanced protection. DataSunrise offers comprehensive database monitoring, auditing, and real-time threat detection capabilities, ensuring that critical data is safeguarded.
Adding ScyllaDB Database to DataSunrise
To integrate ScyllaDB into DataSunrise, follow these steps:
- Add ScyllaDB Instance: Open the DataSunrise management console and add your ScyllaDB instance by providing the necessary connection details (e.g., IP address, port, credentials).
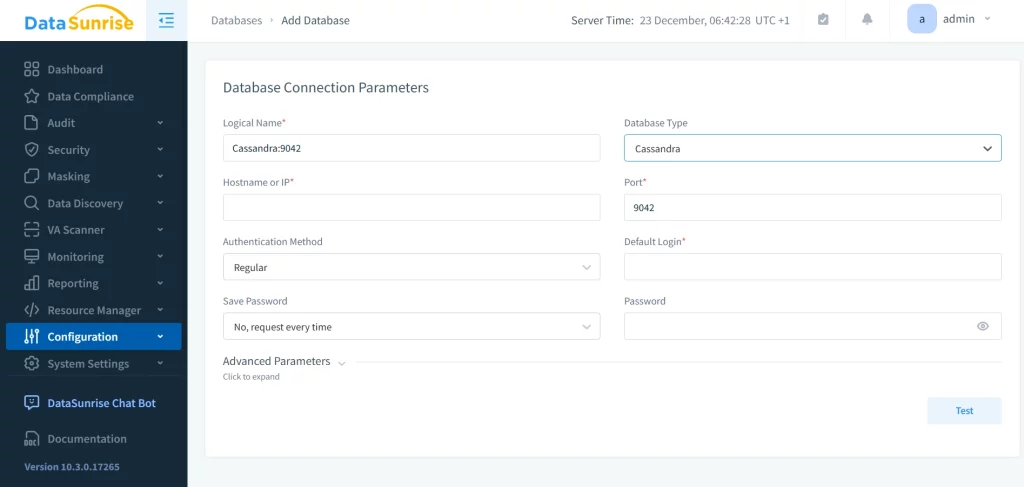
- Create Security Rules for ScyllaDB: DataSunrise allows you to create security rules tailored to ScyllaDB. These rules can be used to monitor access patterns, set alerts for suspicious activities, and ensure compliance with data protection regulations.
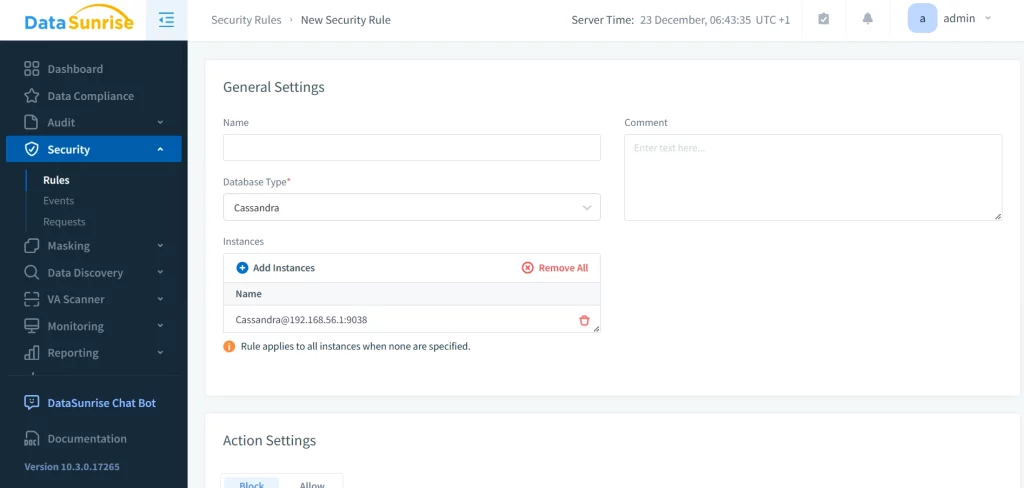
This brief overview highlights just a few of the capabilities of the DataSunrise Database Security toolchain. If you’d like a more in-depth review of the features most relevant to your needs, you can schedule a personalized online demo. Alternatively, you can explore the tool firsthand by downloading the trial version.
Conclusion
ScyllaDB’s native database audit capabilities in the Enterprise Edition provide an essential tool for organizations that need to maintain secure, compliant, and transparent database operations. By enabling and customizing auditing, administrators can ensure that critical database activities are tracked and logged in a way that supports security and regulatory requirements.
As ScyllaDB continues to evolve, its audit features will likely become even more robust, helping organizations better protect their data and meet the demands of modern compliance and security standards.
