
Database Firewall
Introduction
The consequences of data leakage and cyberattacks can be devastating. Companies must proactively secure their data and regularly update their security measures to stay ahead of potential threats. One effective way to achieve this is by deploying a database firewall like DataSunrise Database Firewall.
Data security and protection are paramount for preventing fraud, hacking, phishing, and identity theft. Every organization that wants to operate efficiently must prioritize data security by implementing a robust data protection strategy. As the volume of data stored and generated continues to grow, the importance of data protection increases.
DataSunrise Database FirewallUnderstanding Database Firewalls
A database firewall is like a security guard for databases, watching for and stopping attacks that target databases. These attacks primarily aim to access sensitive data stored in databases. Database firewalls also enable the monitoring and auditing of all access to cloud databases through logs.
Typically, organizations place security software called database firewalls in line with the database server. You can also install them right before the server or near the network gateway. This is especially important when protecting multiple databases on different servers. They create an additional layer of security, specifically designed to safeguard databases from unauthorized access and malicious activities.
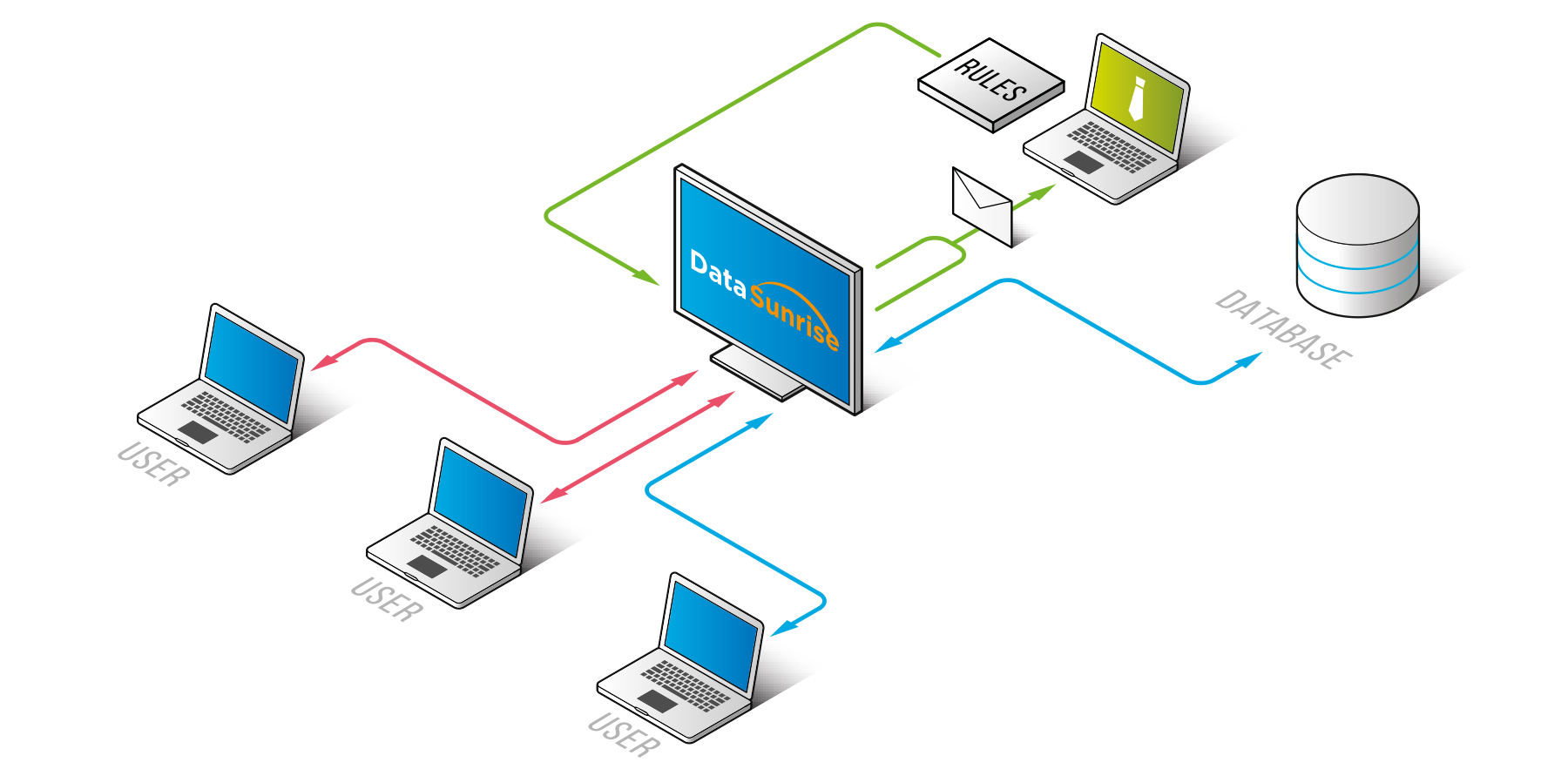
How Database Firewalls Secure Your Data
Database firewalls have security audit policies to detect threats based on known attack patterns or signatures. The firewall vendors regularly update these signatures to identify and protect against the latest database attack methods.
When a database executes a task, it typically implements it as a sequence of SQL statements. Database firewalls compare these SQL statements or queries against the known threat signatures to identify potential attacks.
Monitor Database Queries
DataSunrise continuously monitors all database queries, analyzing SQL statements for suspicious patterns or unauthorized access attempts in real-time.
Detect Threats
Using signature-based detection and behavioral analysis, DataSunrise identifies potential threats like SQL injection attacks, unusual data access patterns, or policy violations.
Block or Allow Access
Based on predefined security policies, DataSunrise decides whether to allow the query to proceed or block it to prevent a potential attack.
Generate Alerts & Logs
The system generates alerts for suspicious activities while maintaining comprehensive audit logs for compliance and security analysis.
DataSunrise Database Firewall can also detect weaknesses in databases, operating systems, and protocols. It alerts administrators to take appropriate action and fix any identified issues. Some firewalls can even monitor database responses to prevent data leakage. Instead of immediately blocking suspicious operations, database firewalls can send alerts to users, allowing them to investigate and take necessary actions.
The Importance of Database Firewalls in Today’s Threat Landscape
As cyber threats get smarter, regular network firewalls may not be enough to protect databases. Attackers can circumvent perimeter security, exploit trusted tiers, and even impersonate privileged users to gain access to sensitive data.
This is where DataSunrise Database Firewall comes into play. It creates a protective barrier specifically designed to monitor and enforce normal application behavior. This barrier prevents harmful activities such as SQL injections and application bypass from reaching the database.
of data breaches target database servers directly
reduction in database attacks with proper firewall implementation
average cost of a data breach in 2024*
By implementing DataSunrise Database Firewall, organizations can significantly reduce the risk of data breaches and ensure the privacy, integrity, and availability of their data.
DataSunrise’s Advantage
What sets DataSunrise apart is its ability to provide comprehensive protection without impacting database performance. The solution’s intelligent architecture ensures minimal latency while providing maximum security. Additionally, DataSunrise’s advanced learning capabilities allow it to adapt to your specific database environment, minimizing false positives while detecting genuine threats.
Learn About DataSunrise’s ApproachDataSunrise Database Firewall Advantages
When choosing a database firewall, organizations should think about how easy it is to set up with their current database system. DataSunrise Database Firewall works with many different types of databases, including Oracle, Microsoft SQL Server, MySQL, PostgreSQL, and many more.
Wide Platform Support
Compatible with over 50 database platforms, both on-premises and in the cloud.
Comprehensive Reporting
Detailed reporting capabilities for compliance with GDPR, HIPAA, PCI DSS, and other regulations.
Intuitive Interface
User-friendly centralized administration console with customizable dashboards for easy configuration and activity monitoring.
DataSunrise’s Unique Features
DataSunrise Database Firewall stands out from other solutions with several unique capabilities:
Dynamic Data Masking
Protect sensitive data in real-time without altering the original database.
User Behavior Analytics
Detect suspicious activity through advanced behavior analysis.
Automated Data Compliance
Streamline regulatory compliance with built-in templates and monitoring.
Multiple Deployment Options
Flexible deployment options to match your infrastructure needs.
Key Features of DataSunrise Database Firewall
SQL Injection Protection
DataSunrise Database Firewall protects against SQL injection attacks by analyzing SQL queries in real-time and blocking malicious requests before they reach your database.
Learn moreDatabase Activity Monitoring
The comprehensive monitoring capabilities allow you to track all database activities in real-time, ensuring compliance and identifying suspicious behavior.
Learn moreUser-Based Access Control
Implement granular access control policies based on user roles, time, location, and more to ensure only authorized personnel can access sensitive data.
Learn moreComprehensive Audit Logs
Generate detailed audit logs of all database activities to maintain compliance with regulatory requirements and simplify security investigations.
Learn moreReal-World Examples of Database Firewall Protection
Financial Institution
A large financial institution handles millions of sensitive customer records, including personal and financial information. By implementing DataSunrise Database Firewall, the institution can monitor all database access attempts and block any suspicious activities. The firewall stops SQL injection attacks, a common way for attackers to get into databases without permission.
Learn about PCI DSS Compliance
Healthcare Organization
A healthcare organization stores highly sensitive patient information, including medical records and personal details. DataSunrise Database Firewall helps organizations comply with privacy regulations such as HIPAA by controlling access to patient databases. The firewall controls who can access patient records based on their job, making sure only authorized people can view them.
Learn about HIPAA Compliance
Conclusion
Database firewalls provide an essential layer of security, specifically designed to safeguard databases from unauthorized access and malicious activities. DataSunrise Database Firewall helps organizations reduce the risk of data breaches, protect the privacy and integrity of data, and maintain the trust of customers and stakeholders.
As data grows, it’s important to invest in a strong security strategy, including database firewalls. This is a vital component of any company’s overall security posture.
Companies can protect their valuable assets by staying proactive and updating their database protection measures regularly. This will help them confidently navigate the constantly changing threat landscape.
Protect Your Databases with DataSunrise
Experience comprehensive database protection with DataSunrise Database Firewall. Our solution provides real-time protection against SQL injection attacks, unauthorized access, and other database threats while ensuring regulatory compliance.
Request a Demo Download Now