
Understanding DDoS Attacks and How to Prevent Them
What Are DDoS Attacks?
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal traffic and availability of a targeted server, service or network by overwhelming it with a flood of Internet traffic from multiple sources. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices.
DDoS attacks are a significant challenge because they are difficult to prevent. The attacks come from many different IP addresses all over the world, making them tough to defend against. This makes it extremely challenging to distinguish malicious traffic from legitimate user traffic. DDoS attacks can cause major disruption, prevent access to important services, and lead to significant financial losses for organizations.
How Do DDoS Attacks Work?
During a DDoS attack, the attacker gains control of a vulnerable computer or machine. This transforms the device into a “bot” or “zombie” that carries out the attack. The attacker does this to many computers, creating a network of compromised machines known as a “botnet”.
The attacker commands the machines in the botnet to send a large amount of traffic to a specific IP address. This action causes difficulty for regular traffic to pass through. The owners of the compromised computers are often unaware that hackers have hijacked their system.
Various sources flood the target with traffic, making it hard to control. This traffic comes from hundreds or thousands of different IP addresses.
Several common methods attackers use to carry out DDoS attacks include:
- Traffic Attacks
- Bandwidth Attacks
- Application Attacks
Traffic flooding attacks send a huge volume of TCP, UDP and ICPM packets to the target. This high traffic overloads the target’s servers and infrastructure, consuming resources and eventually bringing the system down.
This DDoS attack overloads the target with massive amounts of junk data. This results in a loss of network bandwidth, equipment resources and eventually causes the target system to shut down.
Application-layer DDoS attacks overload applications with maliciously crafted requests. These attacks are especially difficult to detect and can disrupt specific functions of applications.
Common DDoS Attack Types
Several kinds of DDoS attacks use the above methods. Here are some of the most common:
UDP Flood
A UDP flood occurs when an attacker sends a large amount of data to random ports on a target. This overwhelms the target and disrupts its ability to function properly. The host searches for datagram-related applications and sends ICMP packets if it does not find any. As the system receives more UDP packets, it becomes overwhelmed and unresponsive to other clients.
A perpetrator can employ a botnet to transmit numerous UDP packets to ports 80 and 443 on a web server. This can overload the server and stop it from responding to real users’ HTTP and HTTPS requests.
ICMP (Ping) Flood
An ICMP flood, also known as a Ping flood, is a type of DDoS attack. It aims to overwhelm a device with ICMP echo-request packets. This makes the device inaccessible for normal traffic.
For instance, the attacker might send many ICMP packets from fake IP addresses to the server at a fast rate. The server has to process each request and attempt to respond, eventually becoming overwhelmed and unresponsive.
SYN Flood
A SYN Flood is a cyber attack that overwhelms a server by sending many connection requests, making it unresponsive. This attack floods the server with connection requests. The server cannot handle the large number of requests. As a result, the server becomes unresponsive.
The attacker sends repeated SYN packets to every port on the targeted host, often using a fake IP address. The server, unaware of the attack, receives multiple, apparently legitimate requests to establish communication. It responds to each attempt with a SYN-ACK packet and waits for the final ACK packet to complete the connection. But when an attack occurs, the server’s resources drain because the hostile client does not receive the ACK.
HTTP Flood
In an HTTP flood DDoS attack, the attacker uses fake HTTP requests to overwhelm a web server or application. HTTP floods do not use malformed packets, spoofing or reflection techniques, making them harder to detect and prevent.
A hacker could use a botnet to send multiple valid HTTP requests to a web app. They would try to make it appear as if it were real traffic. When more requests come in, the server gets overwhelmed and can’t handle more requests from actual users.
Slowloris
Slowloris is a type of attack that targets web servers. It can bring down a server without affecting other services or ports on the network. Slowloris does this by holding as many connections to the target web server open for as long as possible. It accomplishes this by creating connections to the target server, but sending only a partial request.
Periodically, it will send HTTP headers, adding to-but never completing-the request. Affected servers will keep these false connections open, eventually overflowing the maximum concurrent connection pool, and denying additional connection attempts from legitimate clients.
How to Prevent DDoS Attacks
A number of techniques can help prevent or mitigate the impact of DDoS attacks:
- Using firewalls and intrusion prevention systems to monitor traffic and filter out suspicious packets
- Deploying load balancers to distribute traffic evenly across a group of servers
- Setting up rate limiting to put a cap on the number of requests a server will accept over a certain time window
- Encouraging best practices like keeping systems patched and up-to-date
- Planning ahead and having an incident response plan ready
- Considering DDoS mitigation services that use traffic scrubbing techniques to separate good traffic from bad
DDoS attacks are always changing and getting more advanced, which makes it hard to find one solution for total protection. Security teams must be vigilant and employ a multi-layered approach to DDoS defense.
Configure DataSunrise to Prevent DDoS Attacks
You can configure DataSunrise, another powerful tool, to help prevent DDoS attacks. DataSunrise offers a comprehensive database security suite that monitors database traffic in real-time, identifies suspicious behavior, and can automatically block malicious requests.
DataSunrise can find DDoS attacks by creating special security rules. It looks for signs like a sudden increase in traffic from one IP address or lots of requests to one URL.
DataSunrise can quickly respond to potential attacks. It does this by stopping suspicious sessions or blocking the offending IP address. This helps protect the database server.
When configuring a Block DDoS Attacks in DataSunrise, you’ll need to specify the following parameters:
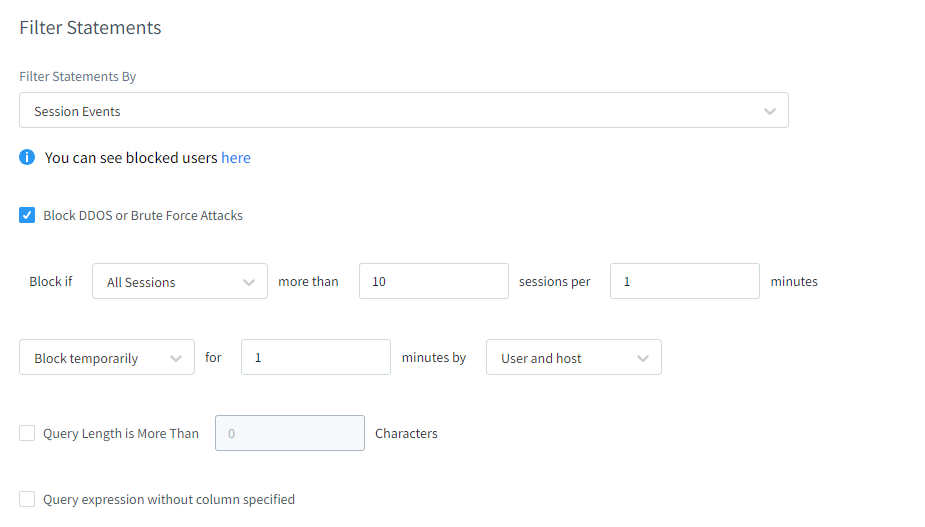
The platform offers flexible configuration options, empowering users to define precise conditions that trigger access blockages. Users can choose which sessions to watch and set limits for the most queries allowed in a certain time period.
DataSunrise allows users to decide what actions to take if a breach occurs. Users also can choose the duration of access blocking and whether to block a single user or the entire machine.
DataSunrise adds extra protection by letting users limit the length of queries, stopping certain injection attacks. For more information, you can book an online demo session.
Conclusion
This article explains what DDoS attacks are, how they work, common types, and ways to prevent or lessen their impact. DDoS attacks pose a significant threat to businesses. They can cause substantial financial and reputational harm if not adequately protected against. Businesses need to defend themselves against these attacks to avoid potential damage.
Cybersecurity is like an arms race. As long as organizations have online infrastructure, there will always be bad actors trying to attack or disrupt it.
To prevent DDoS attacks, you need to understand how they work and have proper security measures. This will safeguard your assets and data.
