
Enhancing Data Security with Dynamic Data Masking in Amazon DynamoDB

Introduction
Data breaches often reveal the critical importance of information protection. Amazon DynamoDB, a widely-used NoSQL database service, houses enormous data volumes for numerous organizations. This abundance of data demands heightened security measures. Dynamic data masking emerges as a robust solution, shielding sensitive information while preserving functionality.
Did you know that data breaches cost companies an average of $4.88 million in 2024? This staggering statistic highlights the importance of robust data protection measures. In this article, we’ll explore dynamic data masking for Amazon DynamoDB, covering both native methods and advanced solutions like DataSunrise.
Understanding Dynamic Data Masking
What is Dynamic Data Masking?
Dynamic data masking is a security feature that hides sensitive data in real-time. It allows authorized users to see the full data while masking it for others. This technique helps organizations comply with data privacy regulations and protect sensitive information.
Why Use Dynamic Data Masking for DynamoDB?
DynamoDB stores various types of data, including personally identifiable information (PII). Implementing dynamic data masking helps:
- Protect sensitive data from unauthorized access
- Comply with regulations like GDPR and CCPA
- Reduce the risk of data breaches
- Maintain data utility for authorized users
Native Data Masking in DynamoDB
The test data in the DynamoDB is as follows:
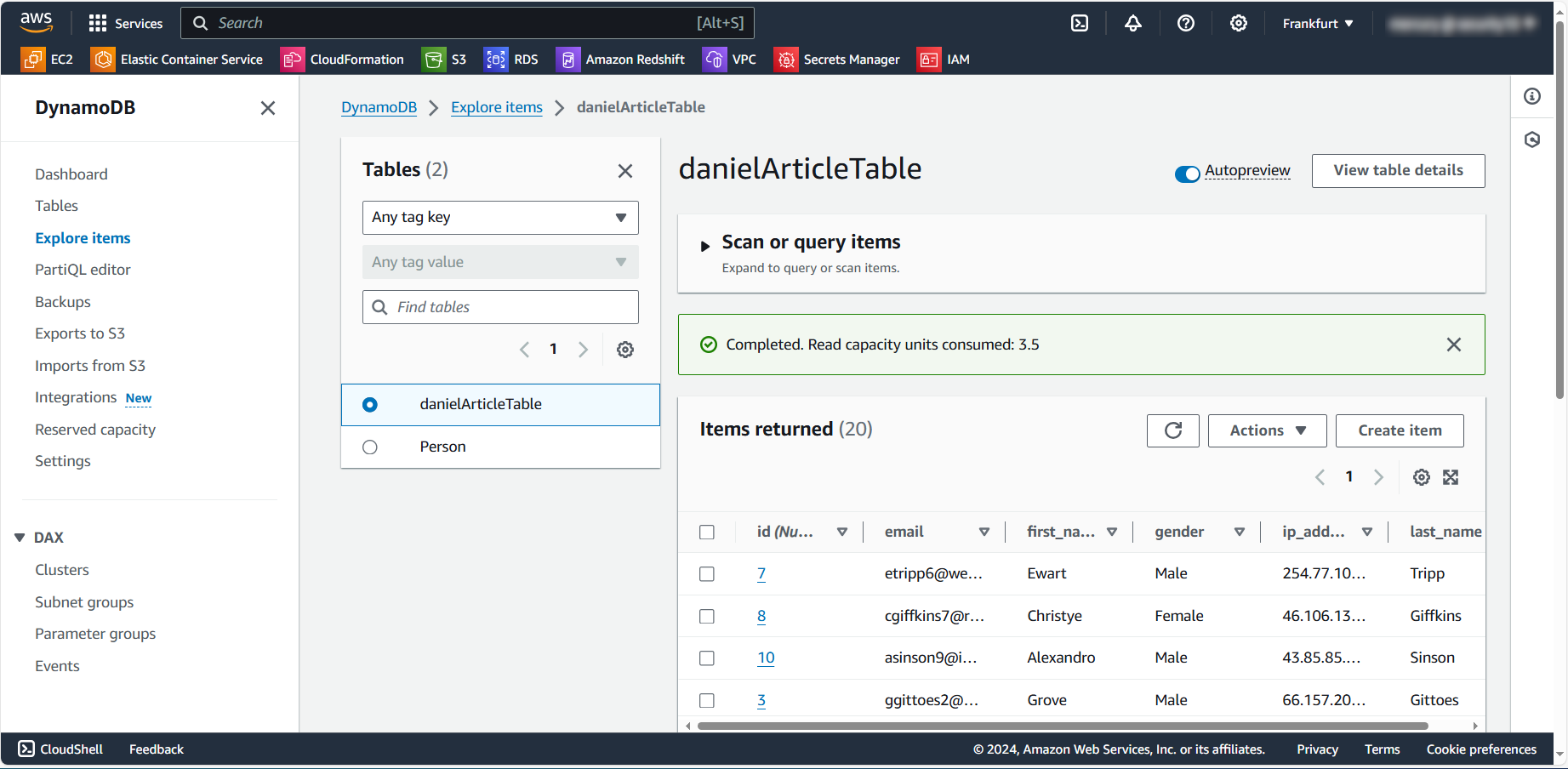
Masking with AWS CLI
To use AWS CLI make sure you configured it with
aws configure
In a previous article, we covered DynamoDB’s masking capabilities. Let’s revisit the process using AWS CLI:
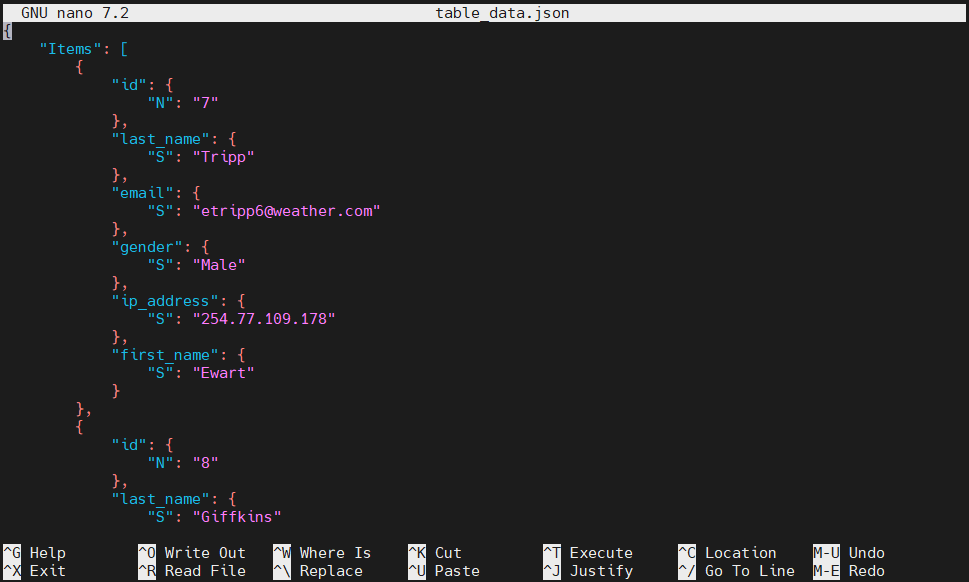
- First, download the data:
aws dynamodb scan --table-name danielArticleTable > table_data.json
nano table_data.json
- Then, mask the sensitive fields:
cat table_data.json | jq '.Items[] | {
id: .id.N,
first_name: .first_name.S,
last_name: .last_name.S,
email: "masked_email@example.com",
gender: .gender.S,
ip_address: .ip_address.S
}' > masked_data.jsonnano masked_data.json
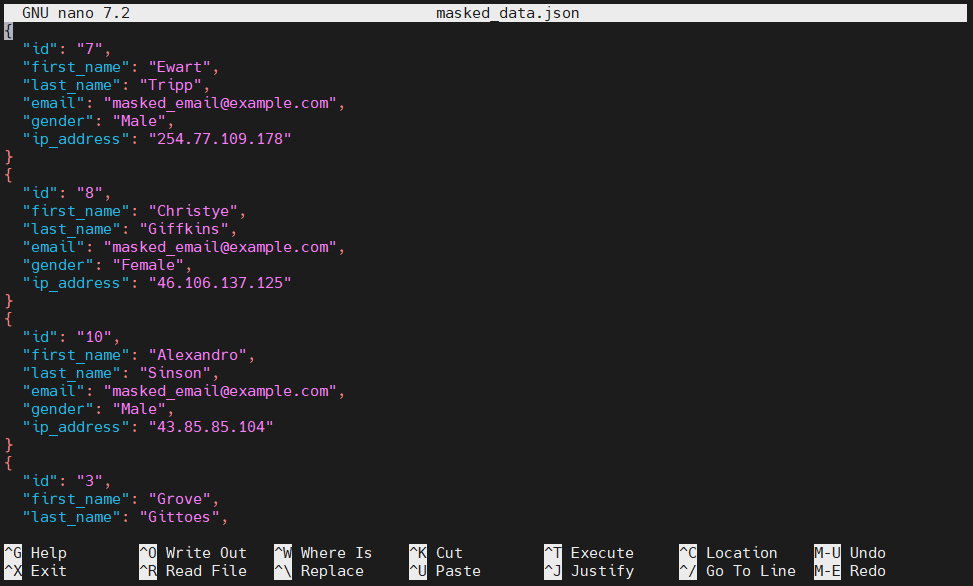
This method masks the email field with a generic value. However, it has limitations:
- It’s a manual process
- Masking rules are not centralized
- It requires post-processing of query results
Accessing DynamoDB Data with Python
The ‘Scripts/activate.bat’ file (for Windows) in the virtual environment should include three additional variables:
set AWS_ACCESS_KEY_ID=... set AWS_SECRET_ACCESS_KEY=... set AWS_DEFAULT_REGION=...
Add these lines to the end of the batch file.
Unmasked Data Access
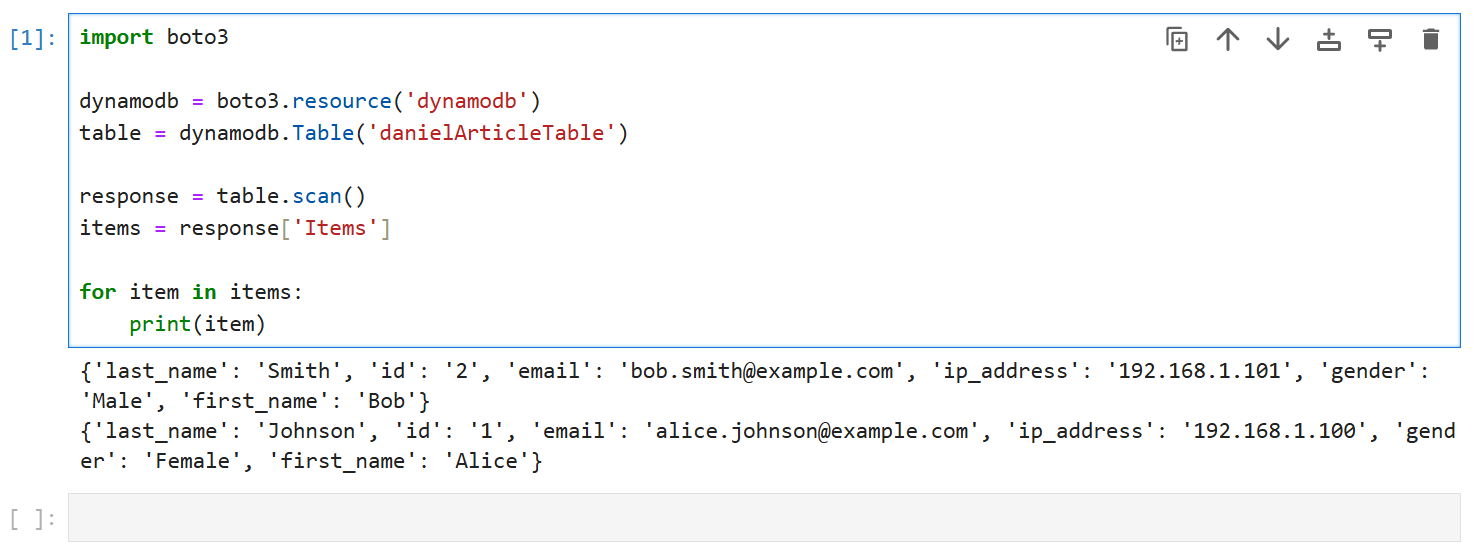
To retrieve data from DynamoDB using Python, you can use the boto3 library:
import boto3
dynamodb = boto3.resource('dynamodb')
table = dynamodb.Table('danielArticleTable')
response = table.scan()
items = response['Items']
for item in items:
print(item)This code retrieves all items from the table, including sensitive data.
Introducing DataSunrise for Dynamic Data Masking
DataSunrise offers a more robust and centralized approach to dynamic data masking for DynamoDB.
Setting Up DataSunrise Instance
To use DataSunrise for dynamic data masking:
- Add your DynamoDB instance
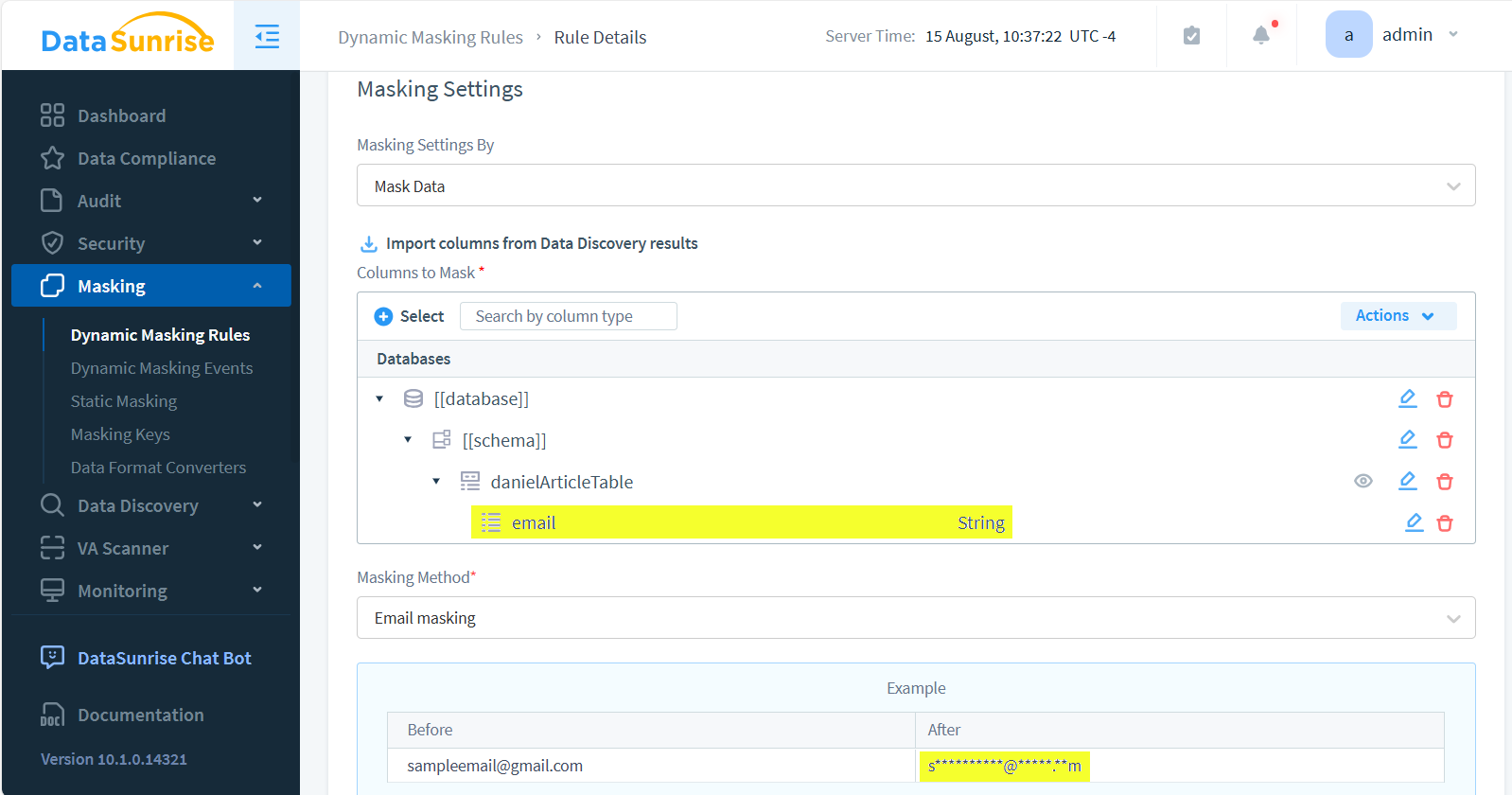
- Configure masking rules for sensitive fields and set the masked objects. Save the rules.
- Make masked data requests to check the rules work properly (see below).
Accessing Masked Data through DataSunrise
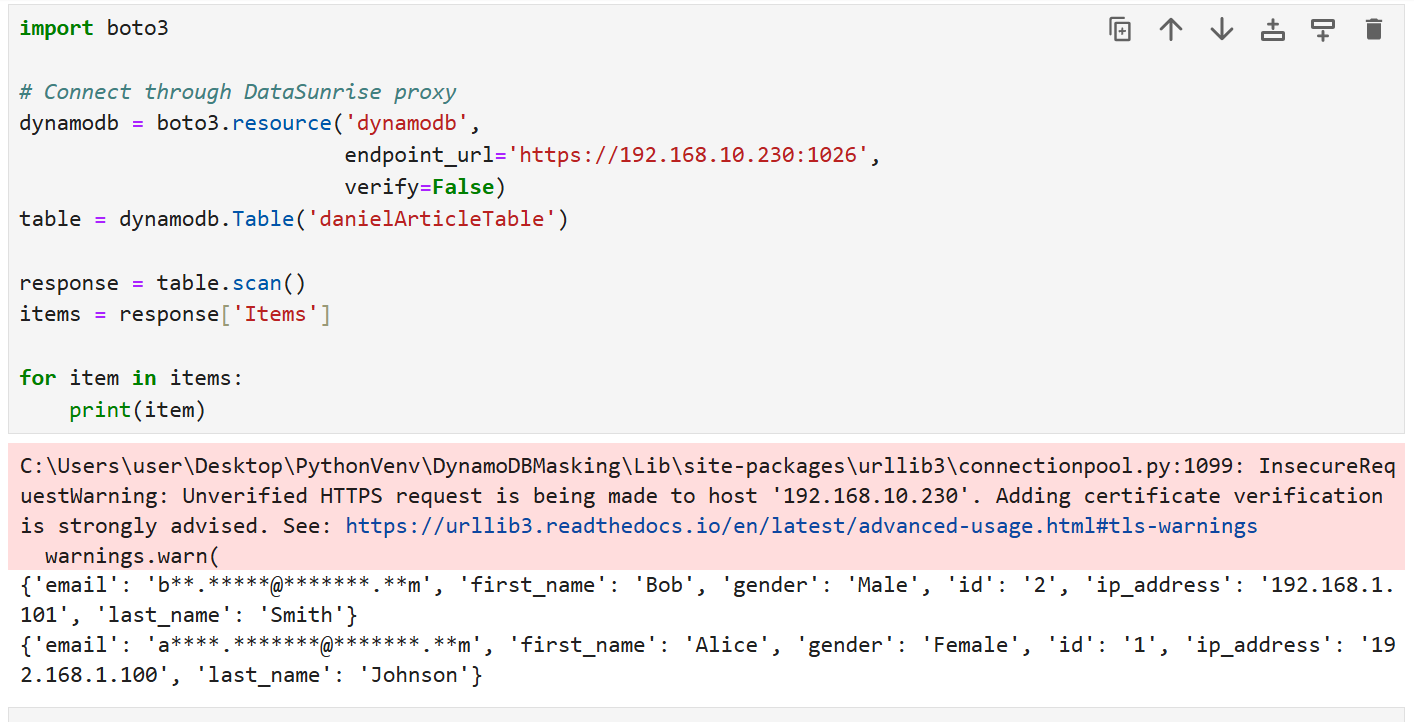
When using DataSunrise, your Python code remains the same. The difference lies in the connection:
import boto3
# Connect through DataSunrise proxy
dynamodb = boto3.resource('dynamodb',
endpoint_url='https://192.168.10.230:1026',
verify=False)
table = dynamodb.Table('danielArticleTable')
response = table.scan()
items = response['Items']
for item in items:
print(item)Now, the data is dynamically masked based on the rules set in DataSunrise.
Benefits of Using DataSunrise for DynamoDB Masking
DataSunrise offers several advantages over native masking:
- Centralized control: Manage all masking rules from a single interface
- Uniform application: Apply consistent masking across your entire data setup
- Dynamic masking: Data is masked in real-time, without modifying the original data
- Flexible rules: Create complex masking rules based on user roles, data types, and more
- Audit capabilities: Track access to sensitive data for compliance purposes
Best Practices for Dynamic Data Masking
To maximize the benefits of dynamic data masking:
- Identify sensitive data fields
- Create clear masking policies
- Regularly review and update masking rules
- Train staff on data handling procedures
- Monitor and audit data access
Conclusion
Dynamic data masking for Amazon DynamoDB is a crucial tool in your data security arsenal. While native masking methods offer basic protection, solutions like DataSunrise provide comprehensive, centralized, and flexible masking capabilities.
By implementing robust dynamic data masking, you can protect sensitive information, comply with regulations, and maintain data utility. Remember, data security is an ongoing process – stay vigilant and keep your masking strategies up-to-date.
DataSunrise offers cutting-edge tools for data security, including audit and VA (vulnerability assessment) features. Visit the DataSunrise website for an online demo and explore how our comprehensive security suite can enhance your data protection strategy.
