
Dynamic Data Masking for Amazon Redshift

Introduction
Organizations face increasing pressure to safeguard personal data while maintaining regulatory compliance. Enter dynamic data masking for Amazon Redshift – a powerful solution that helps businesses secure their data without compromising functionality.
Let’s dive into the world of dynamic data masking and explore how it can revolutionize your data security strategy.
According to the National Vulnerability Database (NVD) Dashboard, as of August 2024, there have been 24,457 new Common Vulnerabilities and Exposures (CVE) records reported this year—and we’re only halfway through.
This staggering statistic underscores the critical need for robust data protection measures. Dynamic data masking offers a cutting-edge approach to safeguarding sensitive information in Amazon Redshift databases.
Understanding AWS Redshift Capabilities for Data Masking
Amazon Redshift provides several built-in functions that can be used for basic data masking. While these functions are not as comprehensive as dedicated masking solutions, they offer a starting point for protecting sensitive data.
Test data
create table MOCK_DATA ( id INT, first_name VARCHAR(50), last_name VARCHAR(50), email VARCHAR(50) ); insert into MOCK_DATA (id, first_name, last_name, email) values (6, 'Bartlet', 'Wank', 'bwank5@who.int'); insert into MOCK_DATA (id, first_name, last_name, email) values (7, 'Leupold', 'Gullen', 'lgullen6@moonfruit.com'); insert into MOCK_DATA (id, first_name, last_name, email) values (8, 'Chanda', 'Matiebe', 'cmatiebe7@gov.uk'); …
Using REGEXP_REPLACE
One of the simplest ways to mask data in Redshift is by using the REGEXP_REPLACE function. This function allows you to replace parts of a string based on a regular expression pattern.
Here’s an example of how you can use restrictions and REGEXP_REPLACE to mask a phone number:
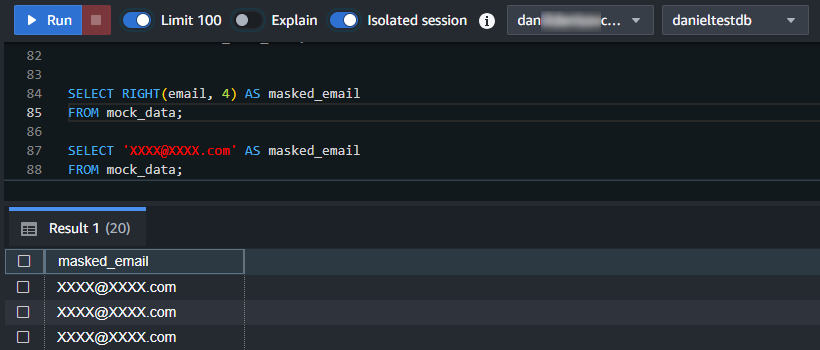
SELECT RIGHT(email, 4) AS masked_email FROM mock_data;
SELECT REGEXP_REPLACE(email, '.', '*') AS masked_email FROM mock_data;
This query replaces the first six digits of a phone number with ‘X’ characters, leaving only the last four digits visible.
Or even simpler:
SELECT 'XXXX@XXXX.com' AS masked_email FROM mock_data;
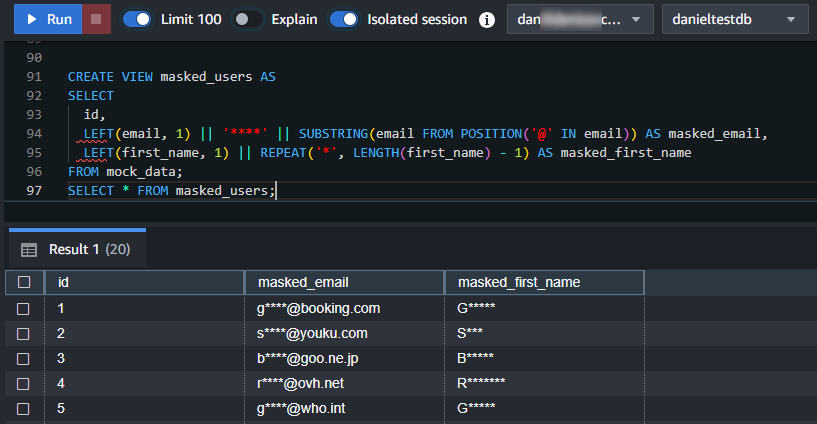
Masking Views
CREATE VIEW masked_users AS
SELECT
id,
LEFT(email, 1) || '****' || SUBSTRING(email FROM POSITION('@' IN email)) AS masked_email,
LEFT(first_name, 1) || REPEAT('*', LENGTH(first_name) - 1) AS masked_first_name
FROM mock_data;SELECT * FROM masked_users;
Leveraging Built-in Python Functions
Redshift also supports user-defined functions (UDFs) written in Python. These can be powerful tools for implementing more complex masking logic.
Here’s a simple example of a Python UDFs that mask an email addresses and first names:
-- Mask Email --
CREATE OR REPLACE FUNCTION f_mask_email(email VARCHAR(255))
RETURNS VARCHAR(255)
STABLE
AS $$
import re
def mask_part(part):
return re.sub(r'[a-zA-Z0-9]', '*', part)
if '@' not in email:
return email
local, domain = email.split('@', 1)
masked_local = mask_part(local)
domain_parts = domain.split('.')
masked_domain_parts = [mask_part(part) for part in domain_parts[:-1]] + [domain_parts[-1]]
masked_domain = '.'.join(masked_domain_parts)
return "{0}@{1}".format(masked_local, masked_domain)
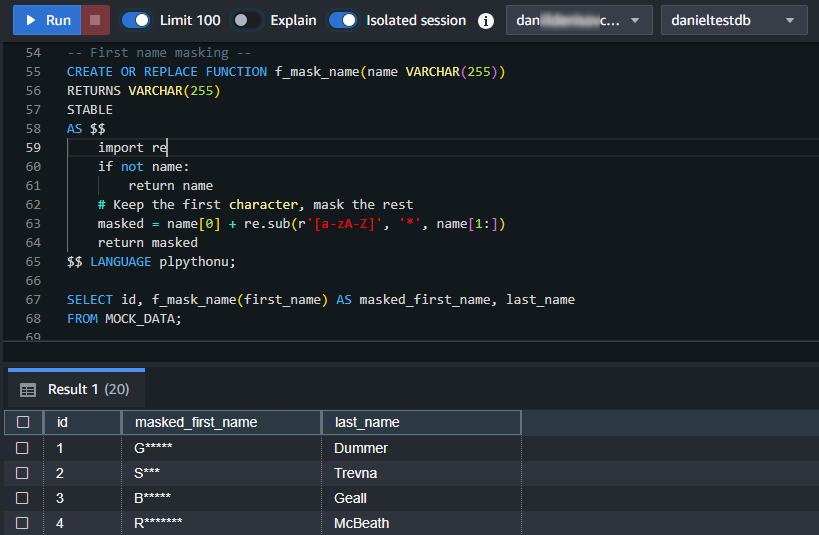
$$ LANGUAGE plpythonu;-- First name masking -- CREATE OR REPLACE FUNCTION f_mask_name(name VARCHAR(255)) RETURNS VARCHAR(255) STABLE AS $$ import re if not name: return name # Keep the first character, mask the rest masked = name[0] + re.sub(r'[a-zA-Z]', '*', name[1:]) return masked $$ LANGUAGE plpythonu;
SELECT id, f_mask_name(first_name) AS masked_first_name, last_name FROM MOCK_DATA;
Creating a DataSunrise Instance for Dynamic Data Masking
While Redshift’s built-in capabilities offer basic masking, they lack the flexibility and ease of use provided by specialized solutions like DataSunrise. Let’s explore how to set up dynamic data masking using DataSunrise.
Configuring Dynamic Data Masking
To set up dynamic data masking:
- In the dashboard, navigate to the “Masking” section.
- Select “Dynamic Masking Rules” from the menu.
- Click “Add New Rule” to create a masking rule.
- Choose your Amazon Redshift database instance from the list of connected databases.
- Select the table and column you want to mask.
- Choose a masking method (more on these in the next section).
- Save your rule and apply the changes.
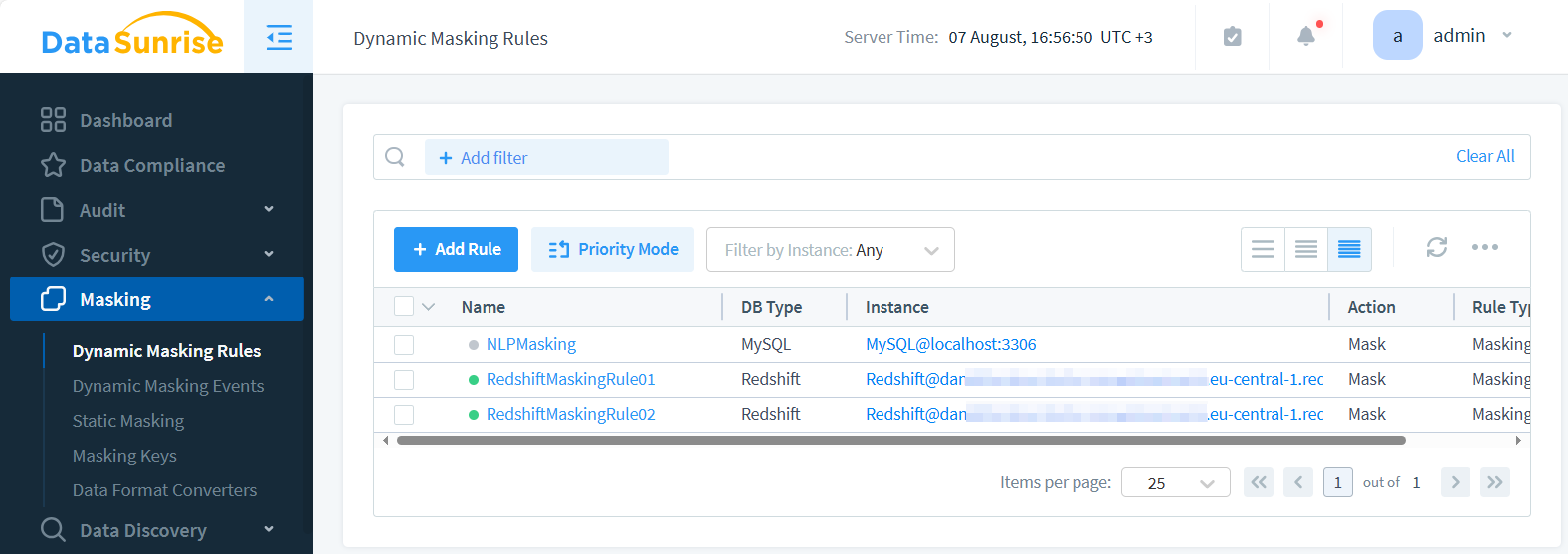
The image displays two dynamic data masking rules. The first rule, labeled ‘RedshiftMaskingRule01’, is configured to mask email addresses. The second rule, ‘RedshiftMaskingRule02’, is set up to mask first names.
After configuring the rules, you can run a test query to see the dynamically masked data in action. DBeaver masked data access is illustrated below.
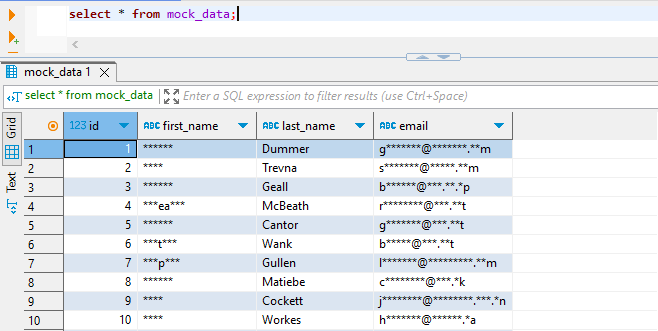
Creating dynamic masking rules with DataSunrise is remarkably simple, requiring just a few clicks. This streamlined process stands in stark contrast to the more complex native approaches. Best of all, this ease of use applies across dozens of supported databases and storage systems, offering unparalleled versatility and efficiency in data protection.
Exploring Masking Methods
DataSunrise offers several masking methods to suit different data types and security requirements. Let’s examine three common approaches:
Format Preserved Encryption (FPE)
FPE is an advanced masking technique that encrypts data while maintaining its original format. This is particularly useful for fields like credit card numbers or social security numbers, where the masked data needs to retain the same structure as the original.
Example: Original: 1234-5678-9012-3456 Masked: 8736-2940-5281-7493
Fixed String Value
This method replaces the entire field with a predetermined string. It’s simple but effective for cases where the actual data structure isn’t important.
Example: Original: John Doe Masked: [REDACTED]
Null Value
Sometimes, the best way to protect sensitive data is to completely hide it. The null value method replaces the original data with a null value, effectively removing it from query results for unauthorized users.
Example: Original: johndoe@example.com Masked: NULL
DataSunrise offers a diverse array of masking methods, providing you with numerous options to tailor your data protection strategy:
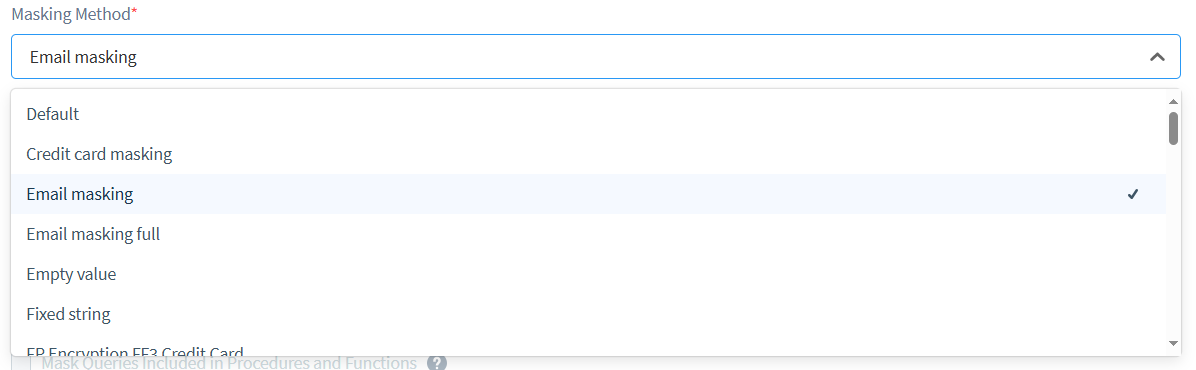
Benefits of Dynamic Data Masking
Implementing dynamic data masking for Amazon Redshift offers several key advantages:
- Enhanced data security: Protect sensitive information from unauthorized access.
- Regulatory compliance: Meet requirements for data protection regulations like GDPR and CCPA.
- Flexibility: Apply different masking rules based on user roles or specific data elements.
- Seamless integration: Mask data dynamically without modifying the underlying database structure.
- Improved testing and development: Provide realistic but safe data for non-production environments.
Best Practices for Implementing Dynamic Data Masking
To maximize the effectiveness of your data masking strategy:
- Identify sensitive data: Conduct a thorough data discovery process to locate all sensitive information.
- Define clear policies: Establish consistent masking rules across your organization.
- Test thoroughly: Verify that masking doesn’t break application functionality.
- Monitor and audit: Regularly review masking rules and their effectiveness.
- Train your team: Ensure all stakeholders understand the importance of data masking and how to use it properly.
Conclusion
Dynamic data masking for Amazon Redshift is a powerful tool in the modern data security arsenal. By implementing robust masking strategies, organizations can protect sensitive data, maintain regulatory compliance, and mitigate the risks associated with data breaches.
As data protection becomes increasingly critical, solutions like DataSunrise offer user-friendly and cutting-edge tools for comprehensive database security. In addition to dynamic data masking, DataSunrise provides features such as data audit and discovery, further enhancing your ability to safeguard valuable information.
Ready to take your Amazon Redshift data security to the next level? Visit the DataSunrise website for an online demo and discover how our advanced tools can transform your approach to data protection.
