
Dynamic Data Masking for IBM DB2

Dynamic data masking for IBM DB2 has become an essential security measure in an era where data breaches cost organizations an average of $4.45 million. This important statistic from IBM’s 2023 Cost of a Data Breach Report shows why protecting sensitive information is vital. Dynamic data masking is now a key priority for DB2 users around the world.
IBM DB2 is a strong database management system. It has powerful built-in features for dynamic data masking. These features help protect against data exposure. By implementing these features, organizations can significantly reduce their risk exposure while maintaining full database functionality. Learn how to implement dynamic data masking in IBM DB2 and discover additional solutions for enhanced data protection.
What is Dynamic Data Masking?
Dynamic data masking (DDM) is a technique that hides sensitive data in real-time based on the user’s access level. Unlike traditional data masking methods, which modify the data at rest, DDM ensures that sensitive data is obfuscated at the time of access. This means that users with insufficient privileges see masked data while authorized users can view the original information.
For example, if a database contains customer data with email addresses and credit card numbers, DDM can display masked versions of these fields to non-privileged users while allowing authorized users to see the actual data. This is especially helpful in areas like development, testing, and reporting. Here, access to real production data is needed, but privacy must be kept.
IBM DB2 Native Dynamic Data Masking Capabilities
IBM DB2 offers several native features to implement dynamic data masking. These include the use of views, stored procedures, and SQL language constructs. While IBM DB2 does not have a dedicated “dynamic data masking” function like some other databases, its flexibility allows for the creation of custom masking solutions.
Using Views for Dynamic Data Masking in IBM DB2
A common method to achieve dynamic data masking for IBM DB2 is through the use of views. By creating a view that masks sensitive data fields, you can ensure that only the masked data is presented to users who do not have the required permissions.
Example: Creating a View for Masked Data
Suppose we have a table called customer_data with the following columns: id, first_name, last_name, email, and ip_address. To dynamically mask the email and ip_address fields, you can create a view like this:
CREATE VIEW masked_customer_data AS SELECT id, first_name, last_name, CASE WHEN CURRENT_USER = 'admin' THEN email ELSE 'xxx@xxx.com' END AS email, CASE WHEN CURRENT_USER = 'admin' THEN ip_address ELSE 'xxx.xxx.xxx.xxx' END AS ip_address FROM customer_data;
In this view:
- The email and ip_address fields are shown in their original form only for users with the admin role.
- For all other users, these fields are replaced with a masked value (xxx@xxx.com for email and xxx.xxx.xxx.xxx for IP address).
The CURRENT_USER function is used to check the privileges of the logged-in user. This method allows for real-time data masking based on user roles or other criteria.
Using Stored Procedures for Dynamic Data Masking
Another way to implement dynamic data masking for IBM DB2 is by using stored procedures. Stored procedures can offer more flexibility than views. This is especially true when you need to use complex logic or conditions for masking.
Example: Dynamic Masking with a Stored Procedure
Let’s assume you want to dynamically mask the email addresses but retain them for VIP customers. You can create a stored procedure like this:
CREATE PROCEDURE mask_email_addresses()
BEGIN
DECLARE v_email VARCHAR(255);
DECLARE v_id INT;
DECLARE cursor_email CURSOR FOR
SELECT id, email FROM customer_data;
OPEN cursor_email;
FETCH NEXT FROM cursor_email INTO v_id, v_email;
WHILE (SQLSTATE = '00000') DO
IF (v_email NOT LIKE '%@vip.com') THEN
UPDATE customer_data
SET email = CONCAT('xxx@xxx.com')
WHERE id = v_id;
END IF;
FETCH NEXT FROM cursor_email INTO v_id, v_email;
END WHILE;
CLOSE cursor_email;
END;In this example:
- The procedure iterates over the customer_data table.
- It checks the email address for the @vip.com domain and leaves it unchanged for VIP customers.
- For all other users, the email address is masked with a generic value (xxx@xxx.com).
The stored procedure can be started by a user or set to run on a schedule. This helps make sure that sensitive data is masked when needed.
Using IBM DB2 Web UI for Dynamic Data Masking
IBM DB2 provides a web-based interface that you can use to interact with the database and apply dynamic data masking. You can use IBM DB2 Web Console to manage your DB2 instance and execute SQL queries. Here’s how:
- Log in to the IBM DB2 web console.
- Navigate to the SQL editor or procedure execution interface.
- Run the SQL queries or stored procedures that implement dynamic data masking.
Using this tool you can mask sensitive data without needing to modify the original database schema.
DataSunrise: A Comprehensive Solution
While IBM DB2 provides a robust set of tools for dynamic data masking, third-party solutions like DataSunrise can offer more advanced features and simplify the process. DataSunrise is a powerful database security suite that includes dynamic data masking, auditing, encryption, and real-time monitoring for databases like IBM DB2.
Benefits of Using DataSunrise
- Centralized Management: DataSunrise provides a unified platform for managing dynamic data masking across all your databases, ensuring consistent masking rules are applied.
- Real-Time Masking: DataSunrise’s dynamic data masking ensures that sensitive information is masked in real-time based on user access levels, preventing unauthorized access to sensitive data.
- Audit and Compliance: DataSunrise includes built-in auditing features that help you track and record data access, which is crucial for compliance with regulations like GDPR, HIPAA, and PCI-DSS.
- No Schema Changes: DataSunrise can mask data without altering the underlying database schema, ensuring that applications continue to work as expected without disruption.
How to Use DataSunrise for Dynamic Data Masking
- Install DataSunrise: After installing DataSunrise in your environment, log in to the DataSunrise web interface.
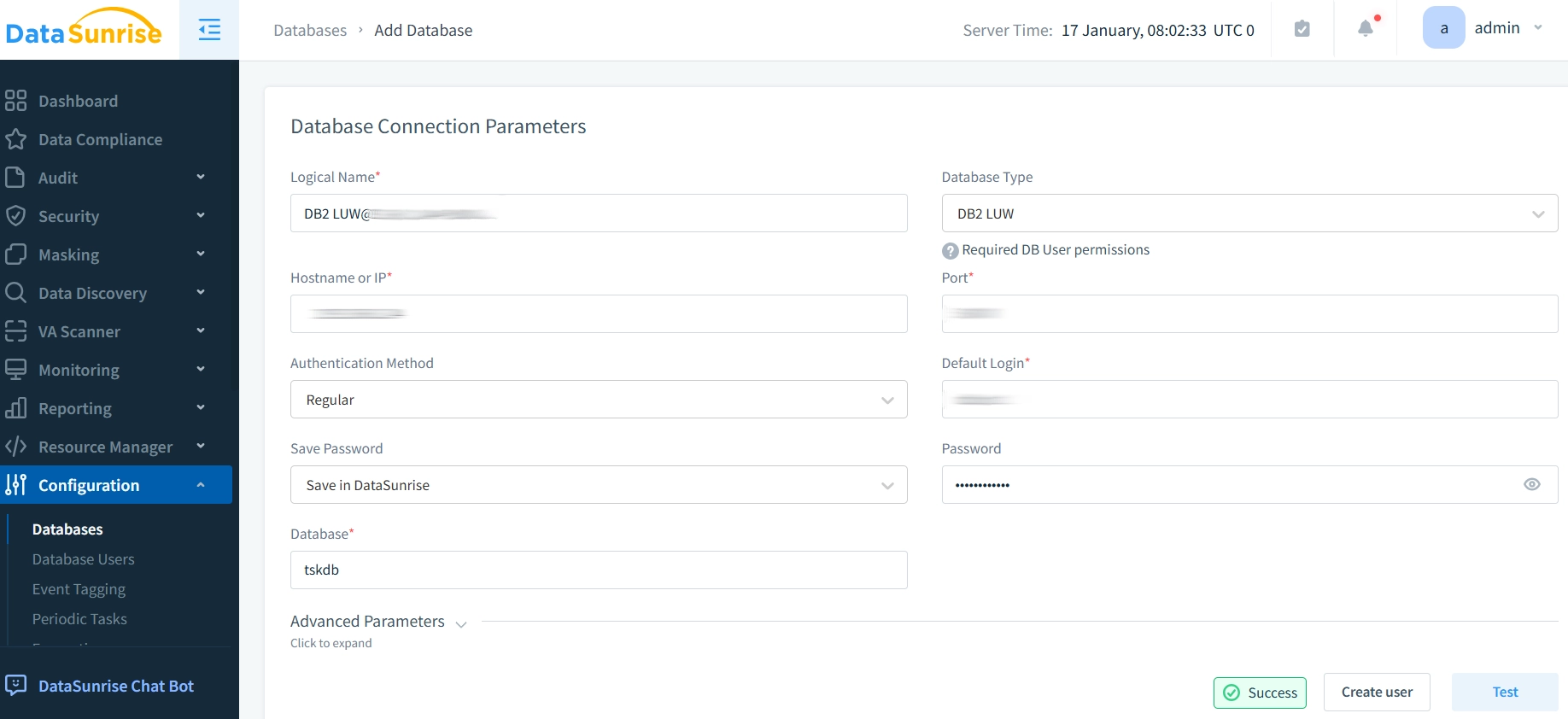
- Connect to IBM DB2: Add your IBM DB2 database instance to the DataSunrise interface by providing the necessary connection details (hostname, database name, username, and password).
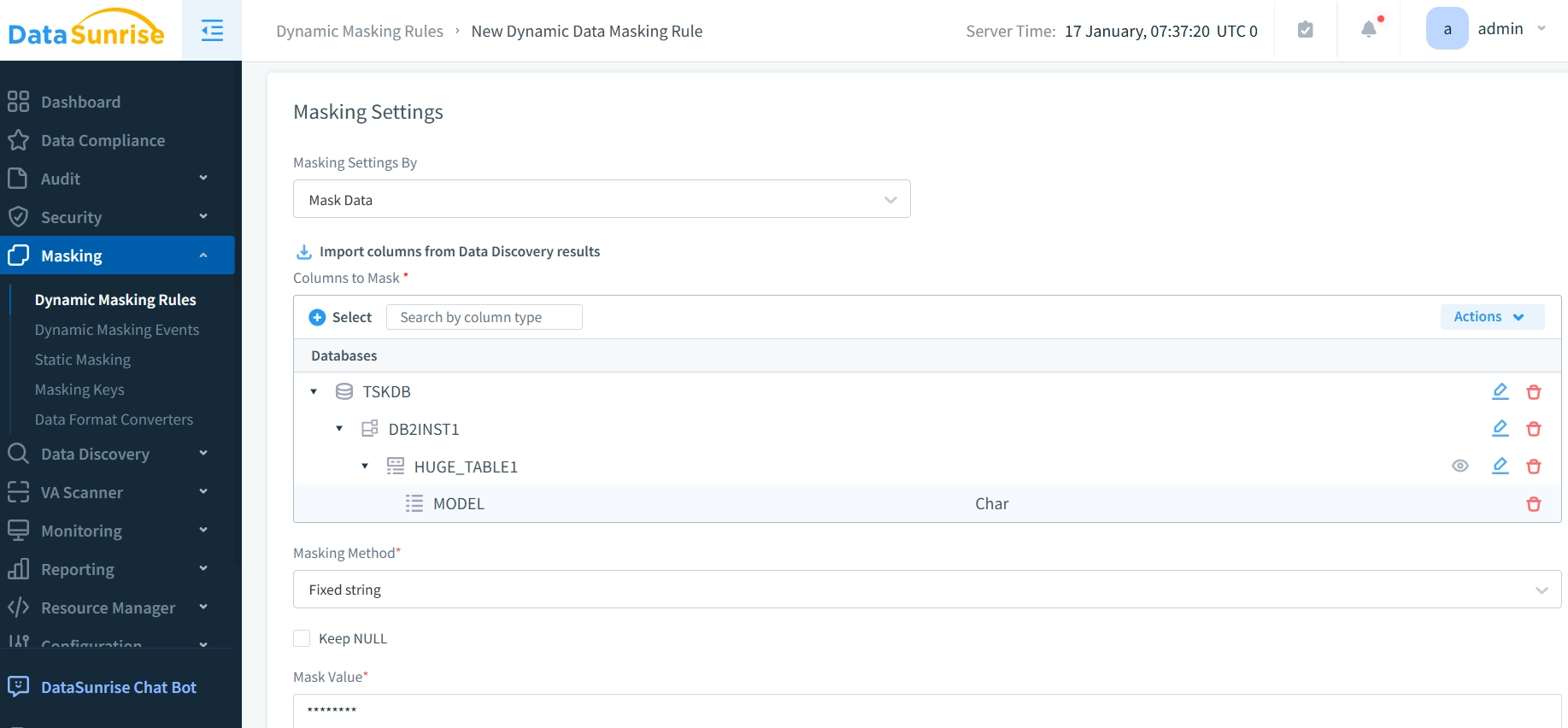
- Define Masking Policies: Use the intuitive UI to define dynamic data masking policies for your IBM DB2 database. You can specify which columns need to be masked and how they should be masked based on user roles or other criteria.
- Monitor and Manage: Once masking rules are in place, you can monitor database access in real-time and ensure compliance with privacy regulations.
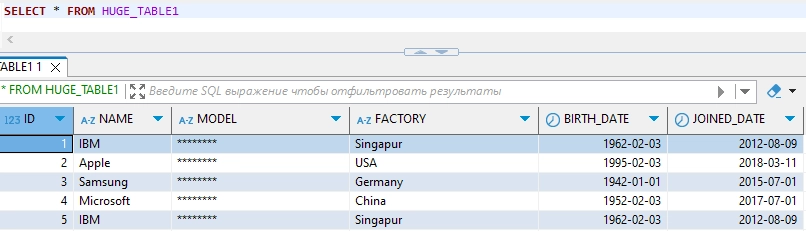
By leveraging DataSunrise’s powerful security suite, you can achieve a higher level of control over your sensitive data, ensuring both security and compliance without disrupting operations.
Best Practices for Dynamic Data Masking
Implementing effective data masking requires attention to several critical practices:
- Regular Rule Review and Updates The foundation of effective data masking begins with systematic evaluation of masking rules. Security teams must periodically review and update these rules to address emerging threats and changing compliance requirements. This ensures your masking strategy remains robust and current with evolving security needs.
- Role-Based Access Control Implementation Role-based access control serves as a cornerstone of data security, determining precisely who can view sensitive data in its unmasked form. This granular control allows organizations to maintain strict data access policies while ensuring operational efficiency.
- Continuous Monitoring and Analysis Proactive monitoring of masked data access patterns enables quick identification of potential security gaps and unusual behavior. Organizations should establish regular monitoring protocols and set up alerts for suspicious activities that might indicate attempted security breaches.
- Comprehensive Documentation Maintaining detailed documentation of all masking configurations ensures consistency across database environments and simplifies troubleshooting efforts. This documentation should include configuration changes, access policies, and regular testing results.
- Integration of Third-Party Solutions While IBM DB2’s native capabilities provide robust protection, specialized solutions like DataSunrise enhance this foundation significantly. DataSunrise offers centralized management, advanced masking algorithms, and seamless integration capabilities that complement DB2’s built-in features.
Conclusion
Dynamic data masking in IBM DB2 provides essential protection for sensitive information through both built-in features and specialized tools. Native features provide strong capabilities. However, third-party solutions like DataSunrise can improve your security. They offer advanced masking algorithms, thorough auditing, and real-time monitoring features. Visit DataSunrise’s website today to schedule an online demo and discover how our advanced security suite can strengthen your IBM DB2 data protection strategy while maintaining optimal database performance.
