
Dynamic Data Masking in MariaDB

Dynamic Data Masking in MariaDB
Database security remains a top priority for organizations handling sensitive information. MariaDB, a popular open-source relational database management system, offers a powerful feature called dynamic data masking. This tool helps protect sensitive data by concealing it from unauthorized users. Let’s explore how dynamic data masking works in MariaDB and why it’s crucial for modern data protection strategies.
Understanding Dynamic Data Masking in MariaDB
Dynamic data masking is a security technique that hides sensitive information in real-time. It works by replacing actual data with masked or scrambled values when unauthorized users access it. The original data remains intact in the database, but users without proper permissions see only the masked version. This approach adds an extra layer of security without changing the underlying data structure.
MariaDB’s dynamic data masking feature operates at the database level. It applies masking rules to specific columns to ensure that it protects sensitive information. When a user queries the database, MariaDB checks their permissions and applies the appropriate masks before returning results. This process happens seamlessly, without the need for application-level changes.
Key benefits of MariaDB dynamic data masking include enhanced security, simplified compliance with data protection regulations, flexible implementation, and improved testing and development scenarios. By concealing sensitive data, organizations reduce the risk of unauthorized access and potential data breaches. It also helps meet various data protection regulations, such as GDPR and HIPAA.
Implementing Dynamic Data Masking in MariaDB
The implementation involves either usage of native resources of MariaDB or third-party solutions, like DataSunrise.
To use dynamic data masking, enable the feature, create masking rules, give permissions, and test the setup. Start by activating dynamic data masking in your MariaDB configuration.
Then, specify which columns need masking and what type of mask to apply. Determine which users or roles can see the unmasked data. Finally, ensure the masking rules work as expected by running queries with different user permissions.
MariaDB offers several masking methods to suit various data types and security needs. Various ways exist to protect data. One method involves full masking, where it replaces data with a fixed string. Another method is partial masking, which hides part of the data.
Randomization involves using realistic-looking random data. Tokenization replaces sensitive data with a token that can link back to the original data if needed.
Conversely, to implement the same using DataSunrise, an instance of MariaDB must be registered in DataSunrise client:
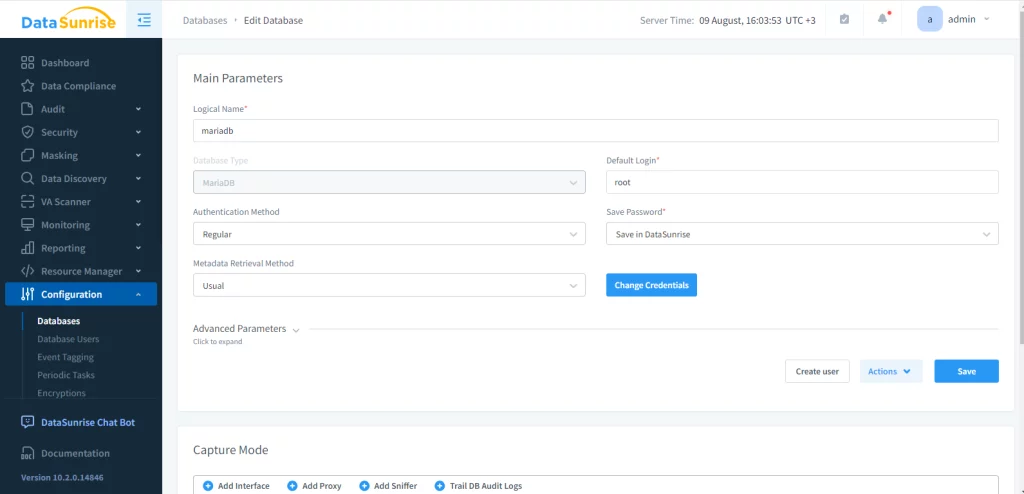
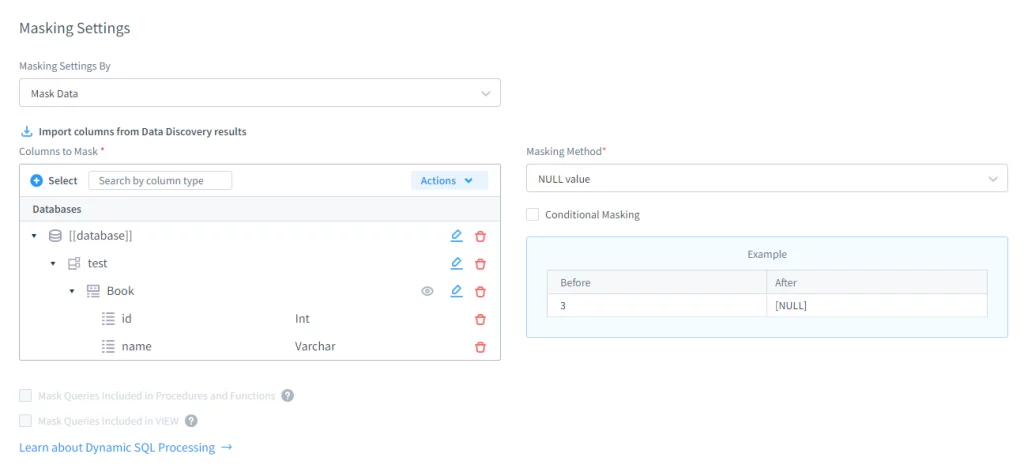
Then, create a dynamic masking rule for the required tables. In this case, we will mask the ‘Book’ table.
Now let’s compare the same ‘SELECT * FROM BOOK;’ query executed into the source database and the created proxy:
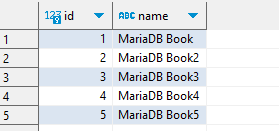
Before masking
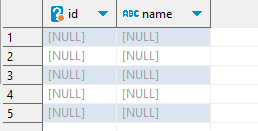
After masking
Best Practices and Considerations
When implementing dynamic data masking, it’s crucial to follow best practices. Start by carefully identifying which columns contain sensitive information that needs protection.
Choose masking techniques that balance security with usability. Conduct regular audits to review and update masking rules, ensuring continued effectiveness. Educate staff on the importance of data masking and how to work with masked information.
While dynamic data masking offers significant benefits, it’s important to consider potential challenges. Complex masking rules may affect query performance, especially on large datasets.
Ensure that masked values remain consistent across related tables and queries. Be cautious when masking data used in joins or as foreign keys to maintain database integrity. Remember that data masking is just one part of a comprehensive security strategy.
Conclusion
As data protection concerns continue to grow, MariaDB is likely to enhance its dynamic data masking capabilities. Future updates could involve better masking algorithms, AI threat detection integration, more unstructured data support, and automated compliance reporting.
Dynamic data masking in MariaDB provides a powerful tool for protecting sensitive information. By implementing this feature, organizations can enhance their data security posture, simplify compliance efforts, and enable safer data sharing. As data privacy threats change, MariaDB’s dynamic data masking will become more important for modern database security strategies.
