
Elasticsearch Audit Trail

Introduction: The Growing Need for Robust Audit Capabilities
Elasticsearch gained popularity due to its powerful full-text search capabilities, scalability, and real-time data analytics features, making it ideal for handling large volumes of diverse data quickly and efficiently. However, with this increased reliance comes a heightened need for data security and accountability. This article will explore the concept of Elasticsearch audit trail, its significance in maintaining data security, and how it addresses the challenges posed by modern search engines and LLMs.
Elasticsearch, a popular distributed search and analytics engine, processes vast amounts of data daily. As sensitive information flows through these systems, the need for comprehensive audit capabilities becomes paramount.
The Importance of Audit Trails for Data Security
In the context of increasing demand for in-depth audit capabilities, audit trail plays a vital role in several areas:
1. Compliance and Regulatory Requirements
Many industries are subject to strict data protection regulations such as GDPR, HIPAA, or SOX. An audit trail helps organizations demonstrate compliance by providing a detailed record of data access and usage.
2. Detecting Unusual Behavior
By analyzing audit logs, security teams can identify patterns of suspicious activity, such as unauthorized access attempts or unusual query patterns. This early detection can prevent potential data breaches or misuse.
3. Forensic Analysis
In the event of a security incident, audit trails provide valuable information for investigating the cause, extent, and impact of the breach. This data is crucial for both resolving the issue and preventing future occurrences.
4. Data Governance
Audit trails support better data governance by providing visibility into how data is being used across the organization. This insight can inform policy decisions and improve overall data management practices.
The Challenge of Sensitive Data in Search Engines and LLMs
One of the unique challenges in the context of search engines and LLMs is the potential for sensitive data to persist beyond its intended use. Users submitting queries may not realize that their sensitive information could be:
- Stored in search logs
- Cached in the search engine
- Used to train or fine-tune LLMs
- Accessible to other team members in shared environments
This scenario creates a significant risk of data exposure and underscores the need for robust audit capabilities. An effective audit trail can help organizations:
- Identify instances where sensitive data has been inadvertently submitted
- Track the propagation of sensitive information through the system
- Implement data retention and deletion policies more effectively
- Ensure compliance with data protection regulations
Elasticsearch Built-in Audit Capabilities: A Brief Overview
Elasticsearch offers built-in audit capabilities, but it’s important to note that these features are only available in paid editions. The native audit features include:
- Security event logging
- Access control logs
- System events monitoring
While these built-in capabilities provide a foundation for auditing, they may not offer the comprehensive coverage required by some organizations, particularly those dealing with highly sensitive data or complex compliance requirements.
Elasticsearch also offers the ability to log slow queries, primarily as a performance optimization feature. However, for comprehensive data auditing, it’s often more effective to log user application queries directly. This approach provides valuable data-driven insights into potential security issues and enables the generation of detailed reports on key company financial metrics. By capturing and analyzing these queries, organizations can gain a deeper understanding of data usage patterns, identify anomalies, and ensure compliance with security policies.
DataSunrise: A Comprehensive Alternative for Elasticsearch Auditing
For organizations seeking more robust and flexible audit capabilities, third-party solutions like DataSunrise offer an attractive alternative. DataSunrise’s Elasticsearch Audit capabilities provide a more comprehensive approach to monitoring and securing Elasticsearch environments.
Key features of DataSunrise’s Elasticsearch Audit solution include:
- Proxy-based auditing: DataSunrise uses proxy technology to audit Elasticsearch sessions and components, providing a non-intrusive way to monitor all interactions with the cluster.
- Granular logging: Capture detailed information about queries, responses, and data modifications.
- Real-time monitoring: Detect and alert on suspicious activities as they occur.
- Custom rule creation: Define specific audit rules based on your organization’s unique requirements.
- Compliance reporting: Generate reports tailored to various regulatory standards.
Elasticsearcgh Audit Trail with DataSunrise: Quick Tour
Creating an instance initiates the process.
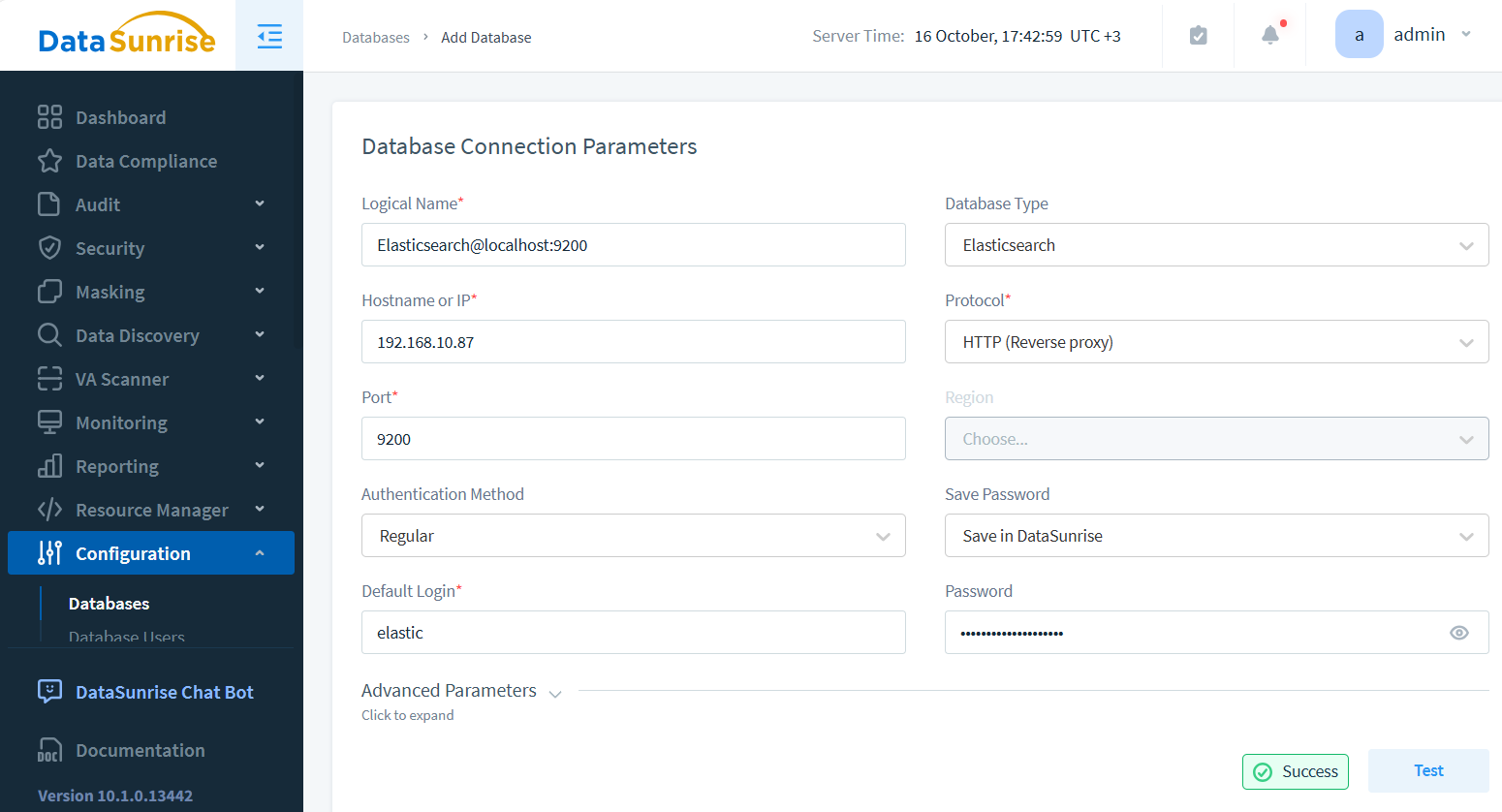
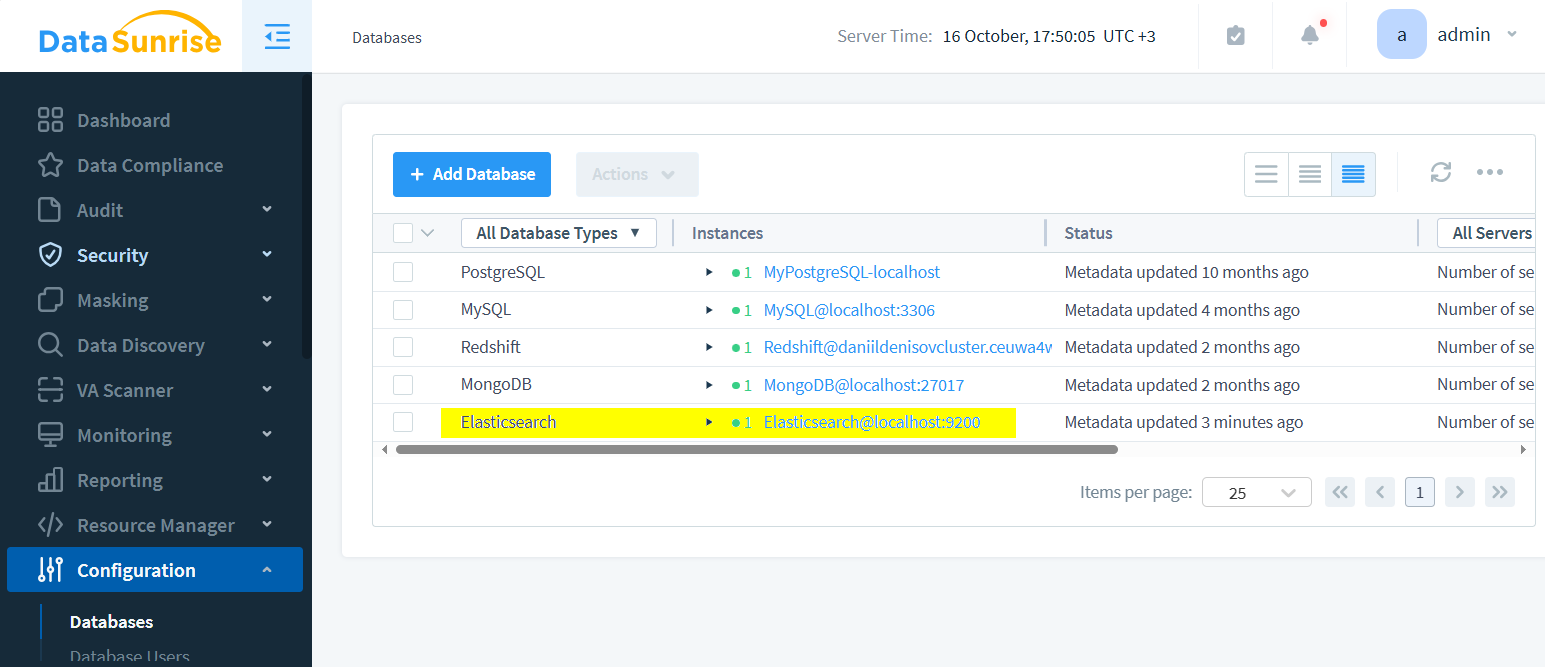
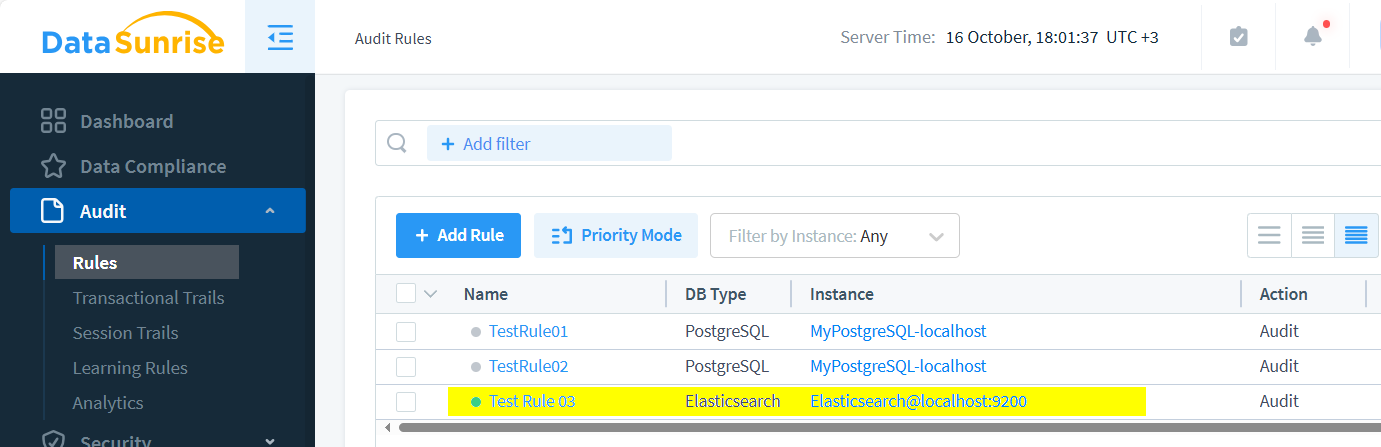
Next, establish a new rule to govern operations.
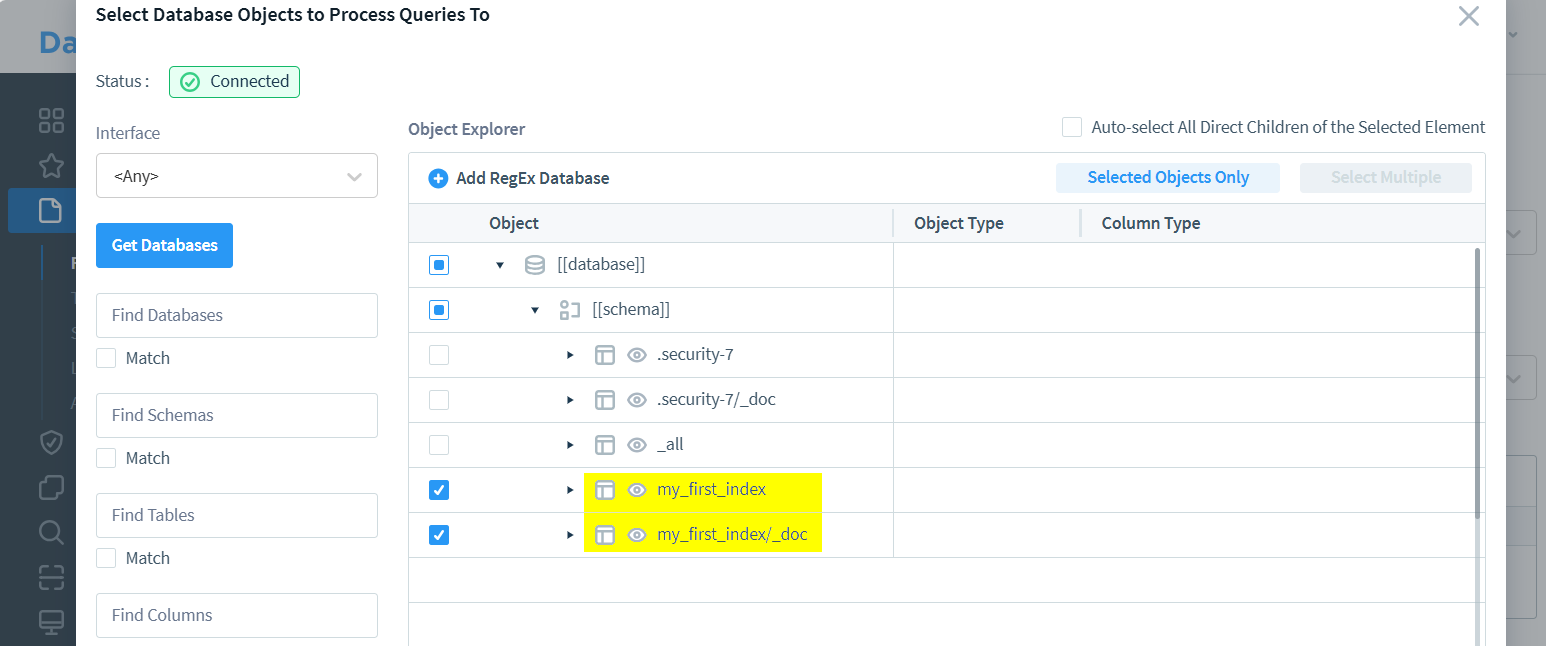
Configure the audited objects to specify monitoring targets.
Test the setup by executing a query via the instance’s designated proxy port. I requested using this bat-file (security and https is disabled on my test Elasticsearch)
@echo off
REM Query data
curl -X GET "http://localhost:9200/my_first_index/_search?pretty" -u elastic:MX_2O%YWidlSEh35%wHa -H "Content-Type: application/json" -d "{\"query\": {\"match\": {\"content\": \"test document\"}}}"
PauseThe output should look like this:
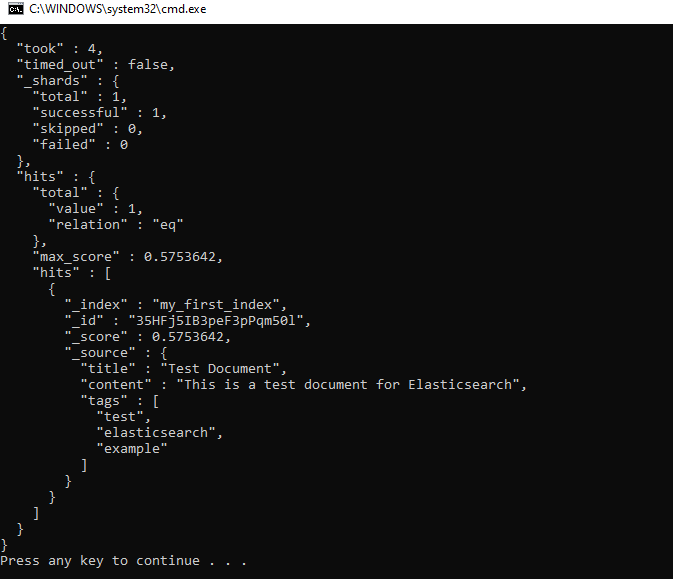
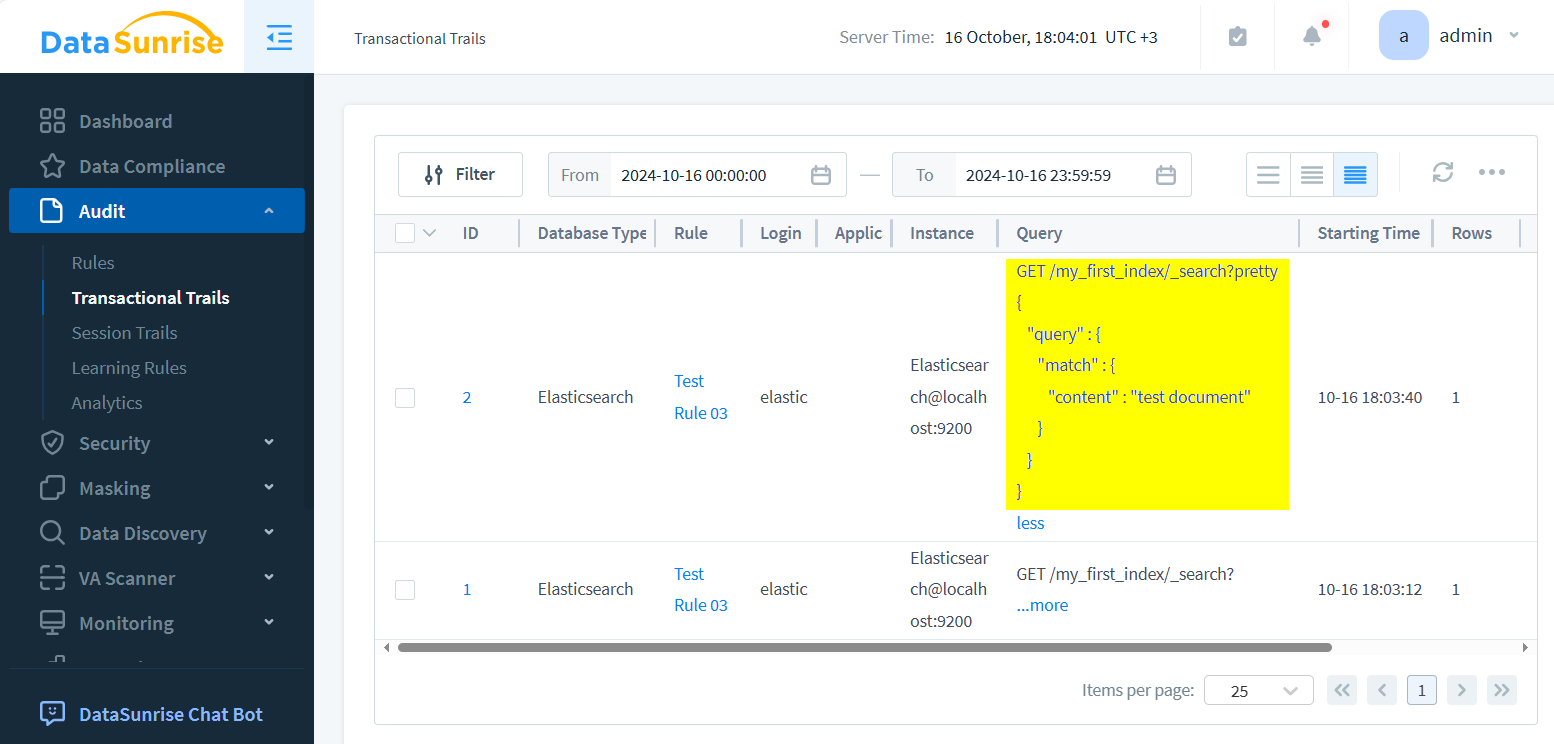
Finally, weave transactional trails to capture and log queries, ensuring comprehensive oversight of data interactions.
Implementing an Effective Elasticsearch Audit Trail
To maximize the benefits of an Elasticsearch audit trail, consider the following best practices:
1. Define Clear Audit Objectives
Identify what you need to track and why. This will help you configure your audit trail to capture the most relevant information.
2. Implement Proper Access Controls
Ensure that only authorized personnel can access and modify audit logs. This preserves the integrity of your audit trail.
3. Regular Log Analysis
Develop a routine for reviewing audit logs to identify patterns or anomalies that may indicate security issues.
4. Integrate with Security Information and Event Management (SIEM) Systems
Connect your Elasticsearch audit trail to your SIEM for a more comprehensive view of your security posture.
5. Establish Retention Policies
Define how long audit logs should be kept, balancing compliance requirements with storage constraints.
The Role of AI in Enhancing Audit Capabilities
As audit trails generate vast amounts of data, AI and machine learning techniques can be leveraged to:
- Detect anomalies in user behavior
- Predict potential security threats
- Automate log analysis and reporting
- Optimize storage and retrieval of audit data
These AI-driven enhancements can significantly improve the effectiveness of your Elasticsearch audit trail, providing deeper insights and more proactive security measures.
Conclusion: Securing Your Data with Elasticsearch Audit Trail
In an era where data breaches and privacy concerns are at the forefront of public consciousness, implementing a robust Elasticsearch audit trail is no longer optional—it’s a necessity. By providing transparency, accountability, and the ability to detect and respond to security threats, audit trails play a crucial role in safeguarding sensitive information.
Whether you opt for Elasticsearch’s built-in capabilities or a more comprehensive solution like DataSunrise, the key is to implement a system that aligns with your organization’s specific needs and compliance requirements. Remember, an effective audit trail is not just about logging data—it’s about gaining actionable insights that can enhance your overall security posture.
As you consider your options for implementing or improving your Elasticsearch audit trail, we invite you to explore DataSunrise’s cutting-edge AI-based tools for database security. Our comprehensive suite includes advanced data and LLM session monitoring, vulnerability assessment, and much more. Visit our website at DataSunrise.com to schedule an online demo and discover how we can help you secure your Elasticsearch environment with state-of-the-art audit capabilities.
