
Elasticsearch Data Activity History

Introduction
In today’s data-driven world, the security of search engines and large language models (LLMs) has become a critical concern. As organizations increasingly rely on these technologies to process and analyze vast amounts of information, the need for robust audit capabilities has never been more pressing. This article delves into the realm of Elasticsearch data activity history, exploring its significance in maintaining database security and ensuring the integrity of search operations.
Did you know that according to recent studies by Skyquest, the global search engine market size was valued at USD 185.39 billion in 2022 and is projected to reach USD 368.93 billion by 2031? With such rapid growth, the importance of securing search data and monitoring user activities cannot be overstated.
Understanding Elastic Cloud and Elasticsearch
What is Elastic Cloud?
Elastic Cloud is a fully managed, cloud-based platform that provides access to Elasticsearch and other Elastic Stack components. It offers a scalable and flexible solution for organizations looking to implement powerful search and analytics capabilities without the hassle of managing infrastructure.
While open-source, self-hosted Elasticsearch deployments offer limited built-in auditing capabilities, they fall short of robust data auditing needs. Therefore, this article focuses on the enhanced capabilities provided by Elastic Cloud.
Accessing Elasticsearch
Within the Elastic Cloud ecosystem, Elasticsearch is readily available through endpoints and API keys. This accessibility allows developers and data analysts to interact with the search engine seamlessly, but it also underscores the need for robust security measures.
To gather sample data for testing purposes, you can use web crawling techniques:
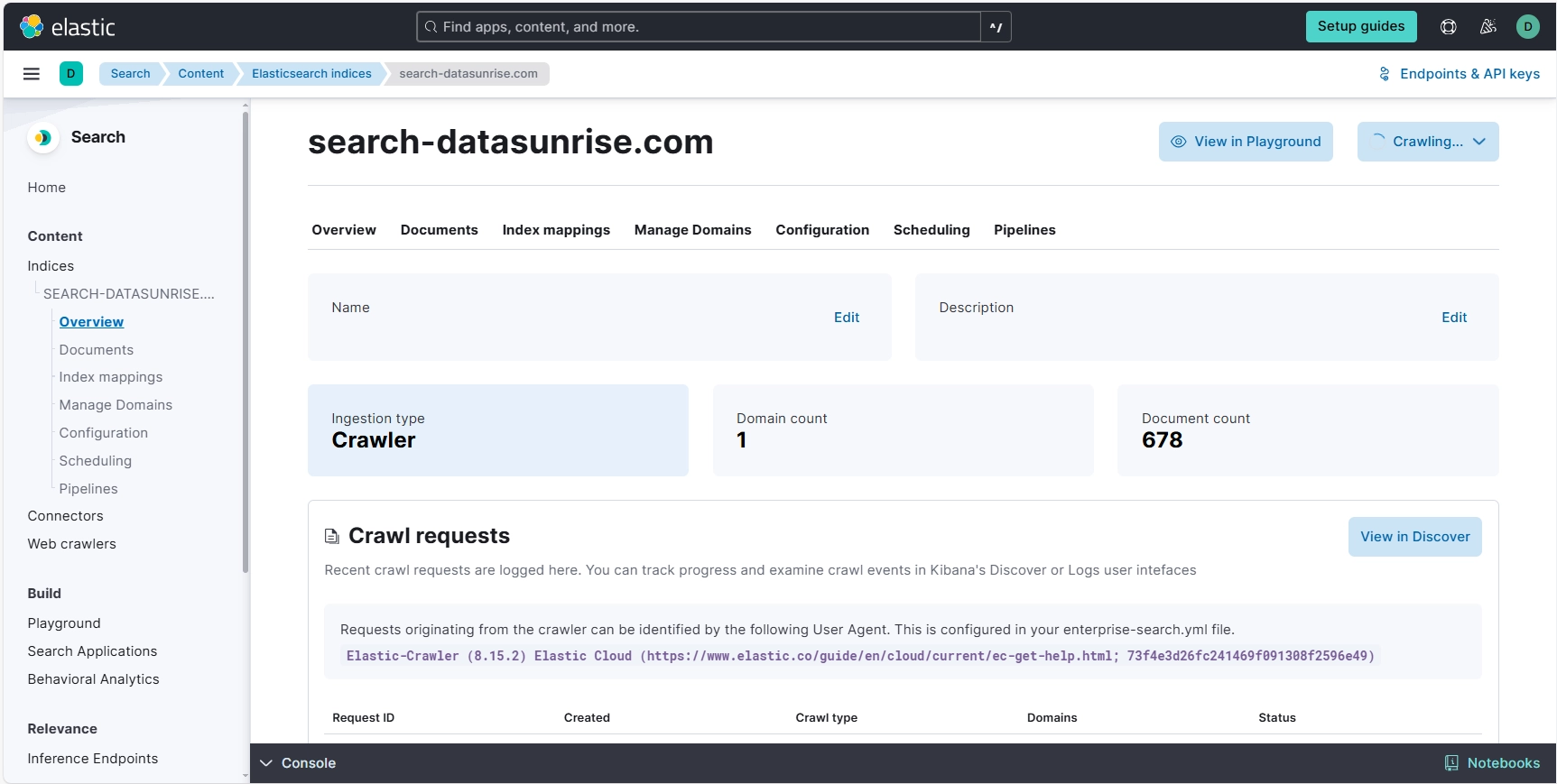
Our website’s complete crawl and document ingestion into Elasticsearch took approximately 15 minutes. All metadata events are now efficiently stored and accessible in the logs explorer.
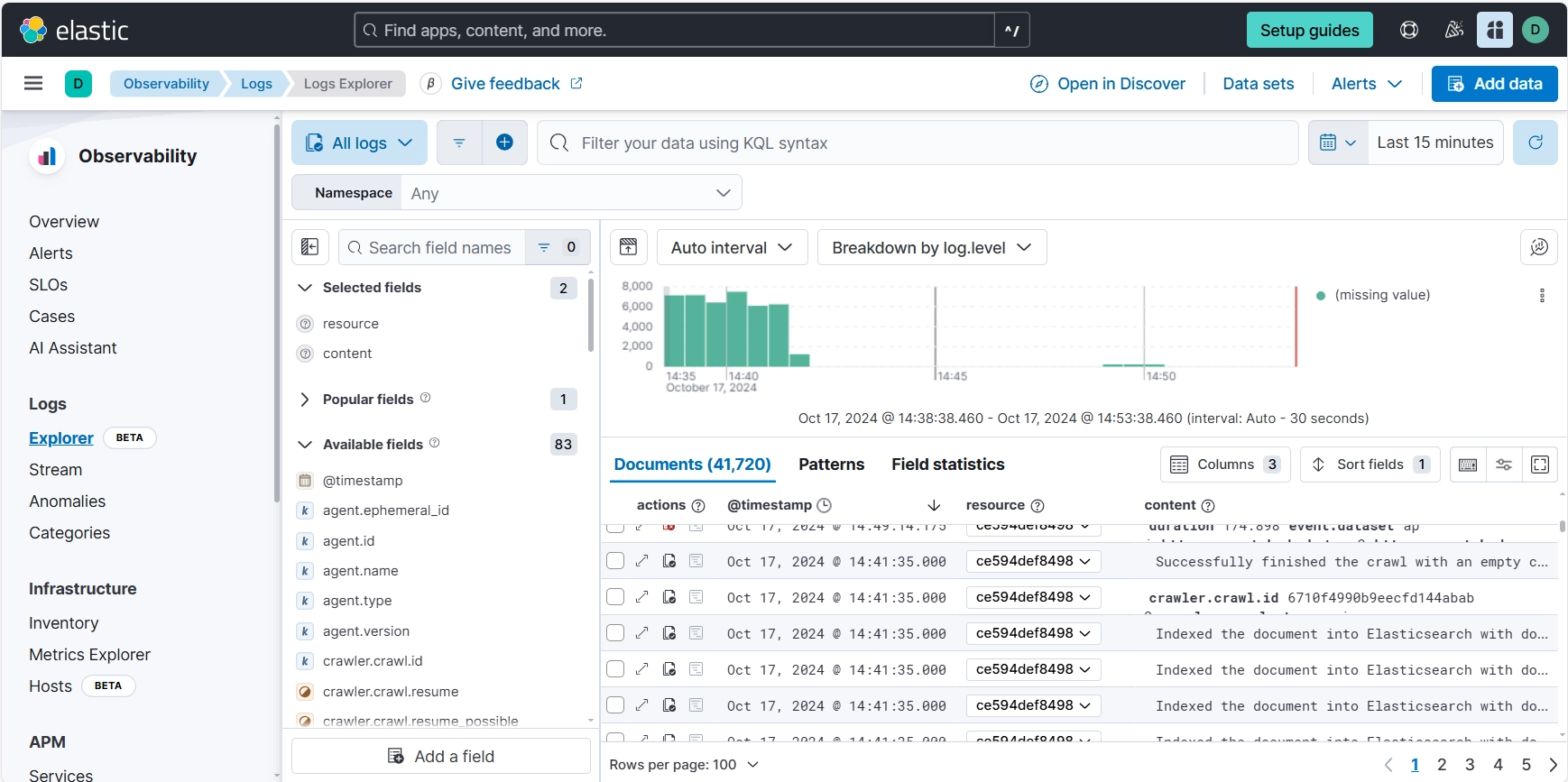
Data is ingested via an internet-accessible endpoint using an API key. It’s crucial to note that API keys are not stored within the system. Therefore, you must securely record the key immediately upon creation.
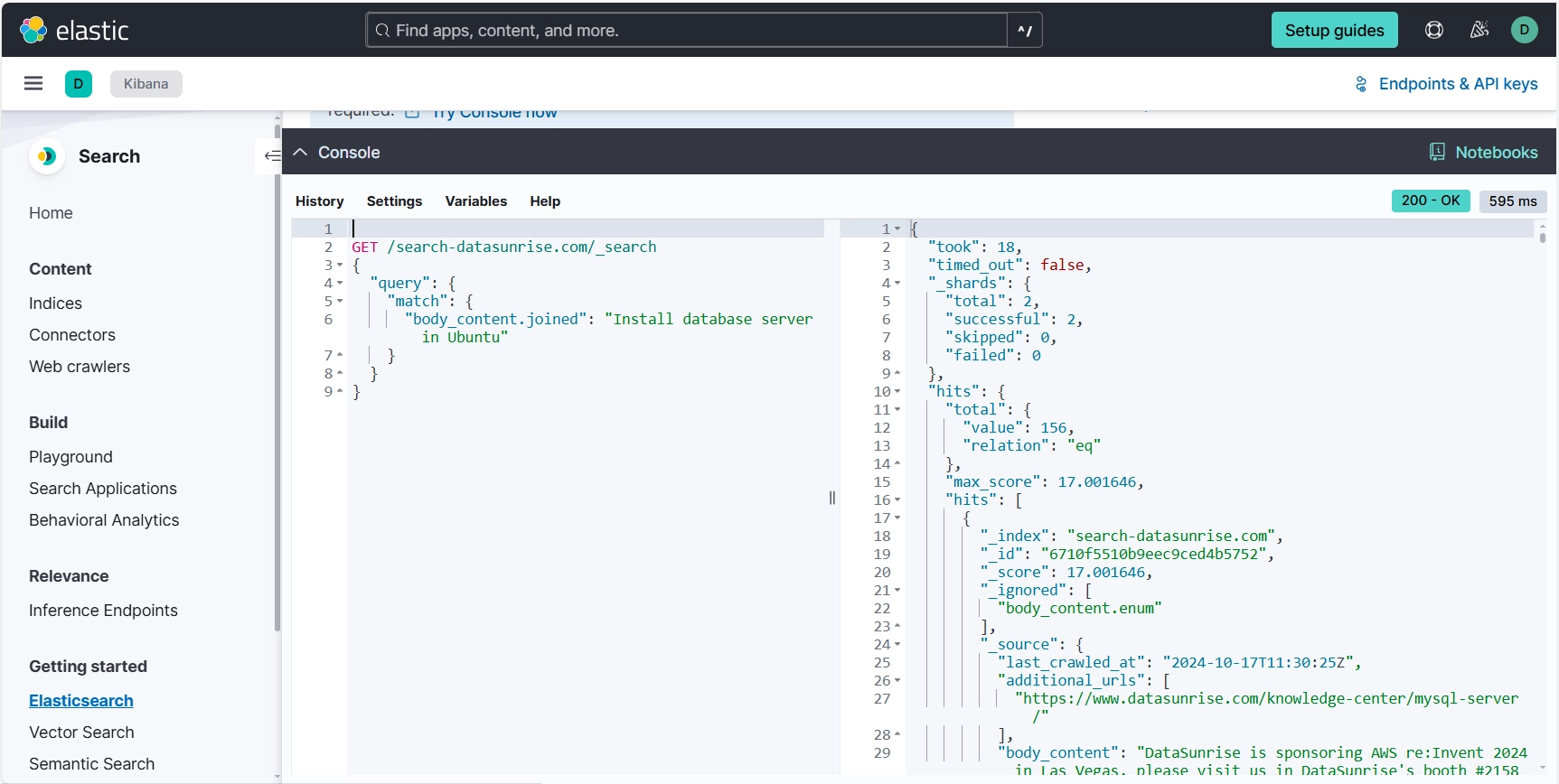
To use the API key in a batch script, you can structure it as follows:
@echo off
setlocal enabledelayedexpansion
set "ELASTICSEARCH_URL=https://9d60c…75b06.us-central1.gcp.cloud.es.io:443"
set "API_KEY=WktCNW…NVY5UQ=="
set "QUERY={\"query\":{\"match\":{\"body_content.joined\":\"Notably, Percona supports dynamic configuration directly from SQL using the auto.conf file (/var/lib/postgresql/16/main/postgresql.auto.conf). However, be cautious not to mix configurations between this file and the main postgresql.conf in /etc/postgresql/16/main/.\"}}}"
curl -X GET "%ELASTICSEARCH_URL%/search-datasunrise.com/_search" ^
-H "Content-Type: application/json" ^
-H "Authorization: ApiKey %API_KEY%" ^
-d "%QUERY%"
pauseAnd in Elastic Cloud Console:
The Importance of Data Activity History
Enhancing Data Security
As the demand for in-depth audit capabilities grows, Data Activity History has emerged as a crucial tool for maintaining data security. By tracking and recording user interactions with the search engine, organizations can:
- Identify potential security breaches
- Monitor unusual search patterns
- Ensure compliance with data protection regulations
Real-time Threat Detection
Proper data auditing enables the interception of unusual behavior and sensitive data access in real-time. This proactive approach to security helps organizations stay one step ahead of potential threats and data leaks.
Built-in Capabilities of Elastic Cloud
Rules and Audit Implementation
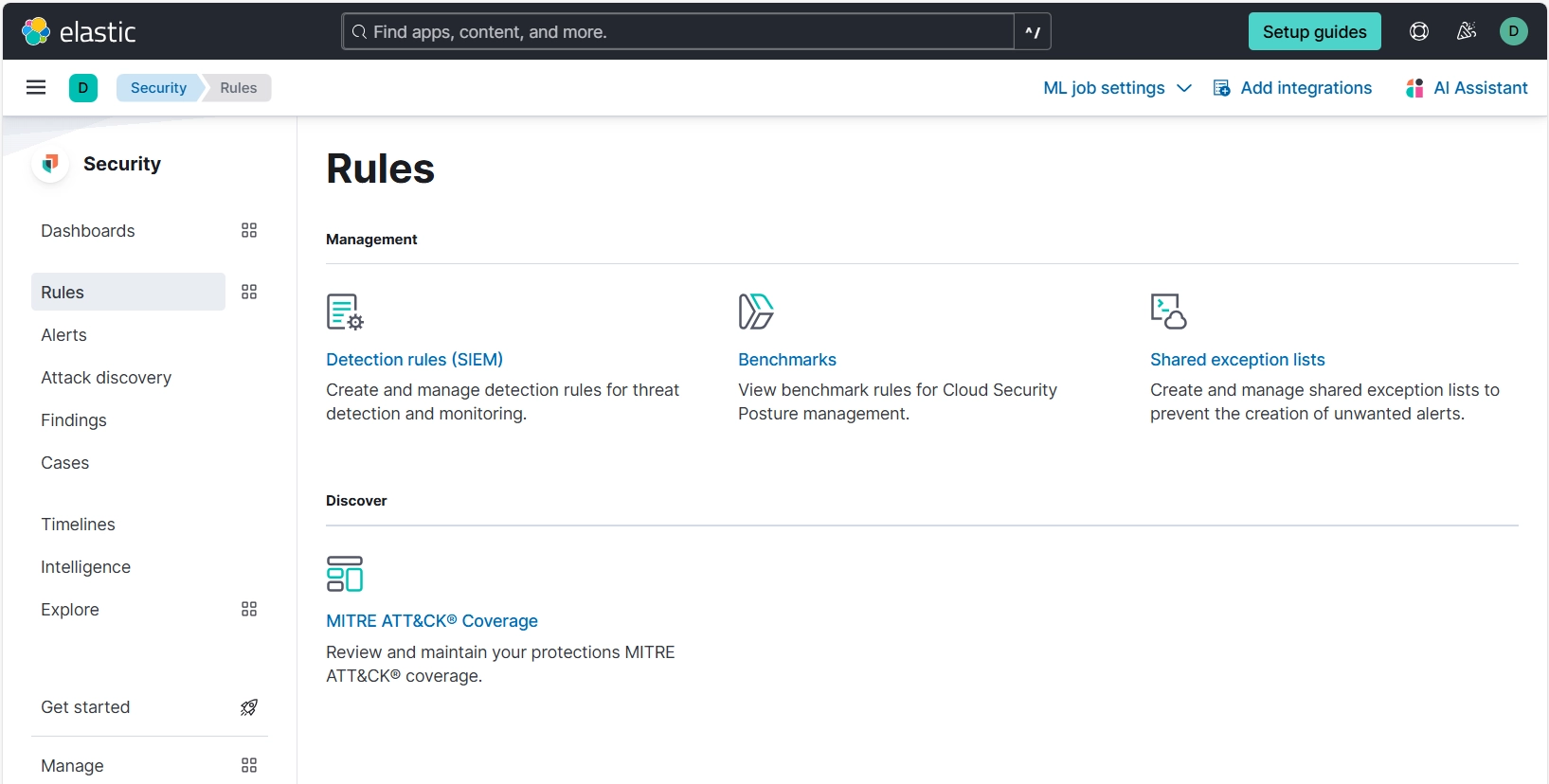
Elastic Cloud offers built-in capabilities for rules and audit implementation, though these are limited to Elasticsearch and available only in paid editions.
While these built-in tools provide a solid foundation for basic security needs, they may not offer the comprehensive coverage required by many organizations.
DataSunrise: A Comprehensive Solution
DataSunrise also offers a robust and versatile approach to Elasticsearch Data Activity History. It seamlessly integrates with numerous popular databases, requiring no modifications to your existing infrastructure.
- Advanced proxy technology for in-depth transaction and session auditing
- Comprehensive monitoring for Elasticsearch and other databases and storages
- Customizable alerting and reporting capabilities
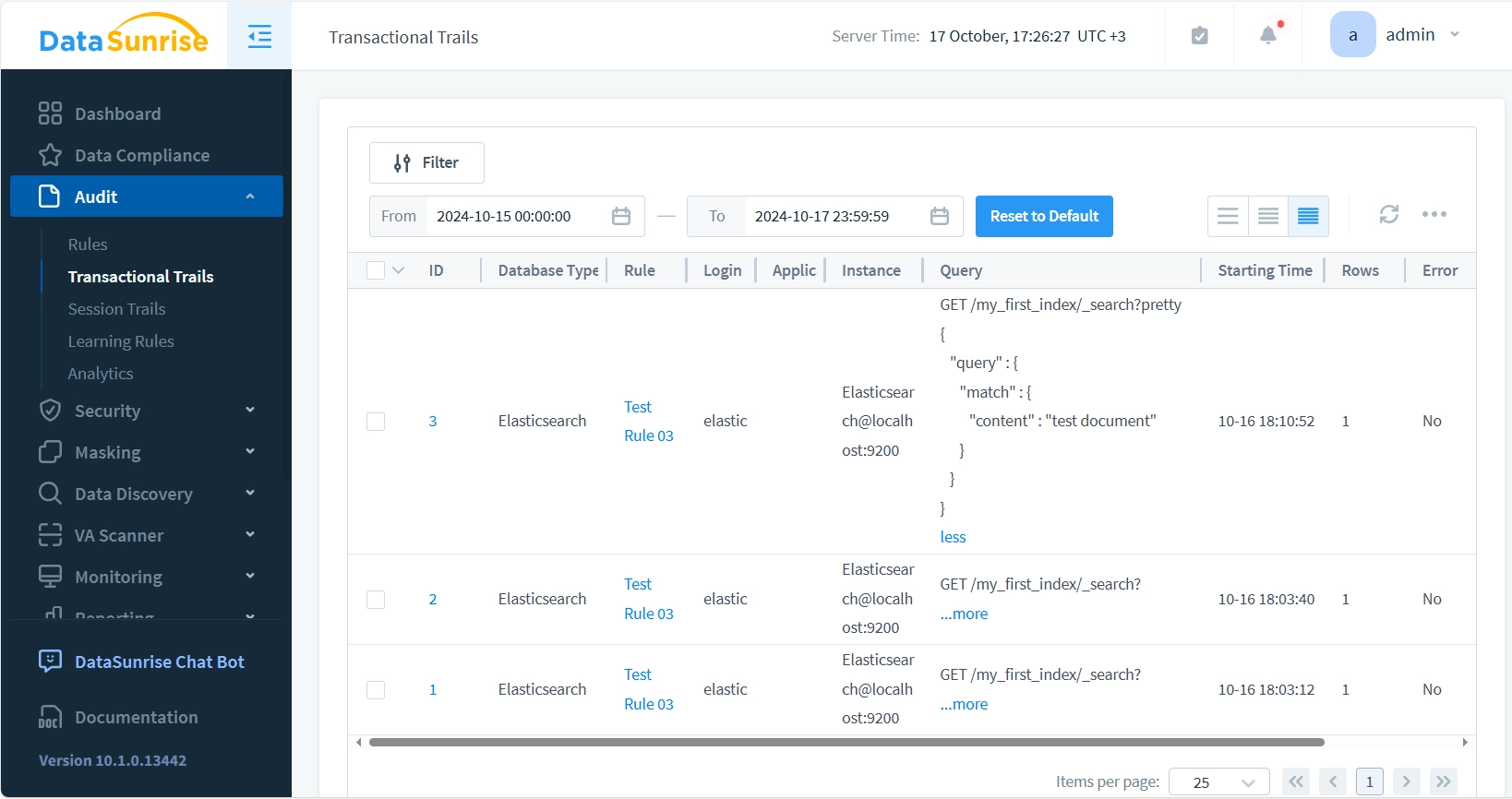
While both solutions come at a cost, DataSunrise’s offerings provide a more extensive toolkit for organizations seeking thorough security coverage.
Important: DataSunrise is fully compatible with self-hosted Elasticsearch and cloud-based deployments like AWS EC2. However, it does not currently support Elastic Cloud’s Elasticsearch engine or API keys.
Implementing Elasticsearch Data Activity History
Best Practices
To maximize the benefits of data activity history, consider the following best practices:
- Define clear audit policies
- Regularly review and analyze audit logs
- Implement role-based access controls
- Encrypt sensitive data at rest and in transit
Overcoming Common Challenges
Implementing a robust data activity history system can present challenges, such as:
- Managing large volumes of audit data
- Balancing security with performance
- Ensuring compliance across diverse data sources
By addressing these challenges head-on, organizations can create a more secure and efficient search environment.
The Role of AI in Enhancing Data Activity History
AI-powered Anomaly Detection
Advanced AI algorithms can significantly improve the effectiveness of data activity history by:
- Identifying complex patterns of suspicious behavior
- Reducing false positives in threat detection
- Adapting to evolving security threats in real-time
Predictive Analytics for Proactive Security
By leveraging LLM assistants and machine learning models, organizations can move beyond reactive security measures and adopt a more proactive stance in protecting their Elasticsearch deployments.
Future Trends in Search Engine Security
The Rise of Quantum-resistant Encryption
As quantum computing threatens traditional encryption methods, the search engine security landscape is likely to evolve. Implementing quantum-resistant encryption for data activity history logs will become increasingly important.
Integration with Zero Trust Architectures
The future of Elasticsearch data activity history lies in its seamless integration with Zero Trust security models, providing continuous authentication and authorization for all search activities.
Conclusion
Elasticsearch data activity history plays a pivotal role in safeguarding the integrity and security of search operations. As organizations navigate the complex landscape of data protection, comprehensive solutions like those offered by DataSunrise become increasingly valuable. By implementing robust data activity history systems, businesses can not only enhance their security posture but also gain valuable insights into user behavior and data access patterns.
In an era where data breaches can have devastating consequences, investing in advanced Elasticsearch data activity history tools is not just a luxury—it’s a necessity for any organization serious about protecting its digital assets and maintaining trust with its users.
DataSunrise – Cutting-edge Database Security
DataSunrise stands at the forefront of database security innovation, offering a suite of flexible and AI-powered tools designed to meet the evolving needs of modern organizations. Our comprehensive solution goes beyond basic data activity history, encompassing:
- Advanced data and LLM session monitoring
- Vulnerability assessment and remediation
- Dynamic data masking and encryption
- AI-driven threat detection and response
By leveraging cutting-edge technology and a deep understanding of database security challenges, DataSunrise empowers organizations to protect their most valuable asset—their data.
We invite you to explore the full range of DataSunrise’s capabilities and see firsthand how our solutions can transform your approach to database security. Visit our website today to schedule an online demo and take the first step towards a more secure data environment.
