
Encryption Algorithms for Data Protection
Introduction
In today’s digital age, data security is paramount. With vast amounts of sensitive information stored in databases and data warehouses, it’s crucial to employ robust encryption algorithms to protect this data from unauthorized access and breaches. Encryption algorithms play a vital role in safeguarding the confidentiality, integrity, and availability of data. In this article, we’ll explore the basics of encryption algorithms, compare different approaches, and examine their usage in popular databases like PostgreSQL, MongoDB, and the Snowflake data platform.
What are Encryption Algorithms?
Encryption algorithms are mathematical functions that convert plaintext data into an unreadable format called ciphertext. The process of encryption involves applying a specific algorithm and a secret key to the plaintext, making it unintelligible to anyone without the corresponding decryption key. Encryption algorithms ensure that even if unauthorized individuals gain access to the encrypted data, they cannot decipher its contents without the proper key.
Types of Encryption Algorithms
There are two main types of encryption algorithms: symmetric and asymmetric.
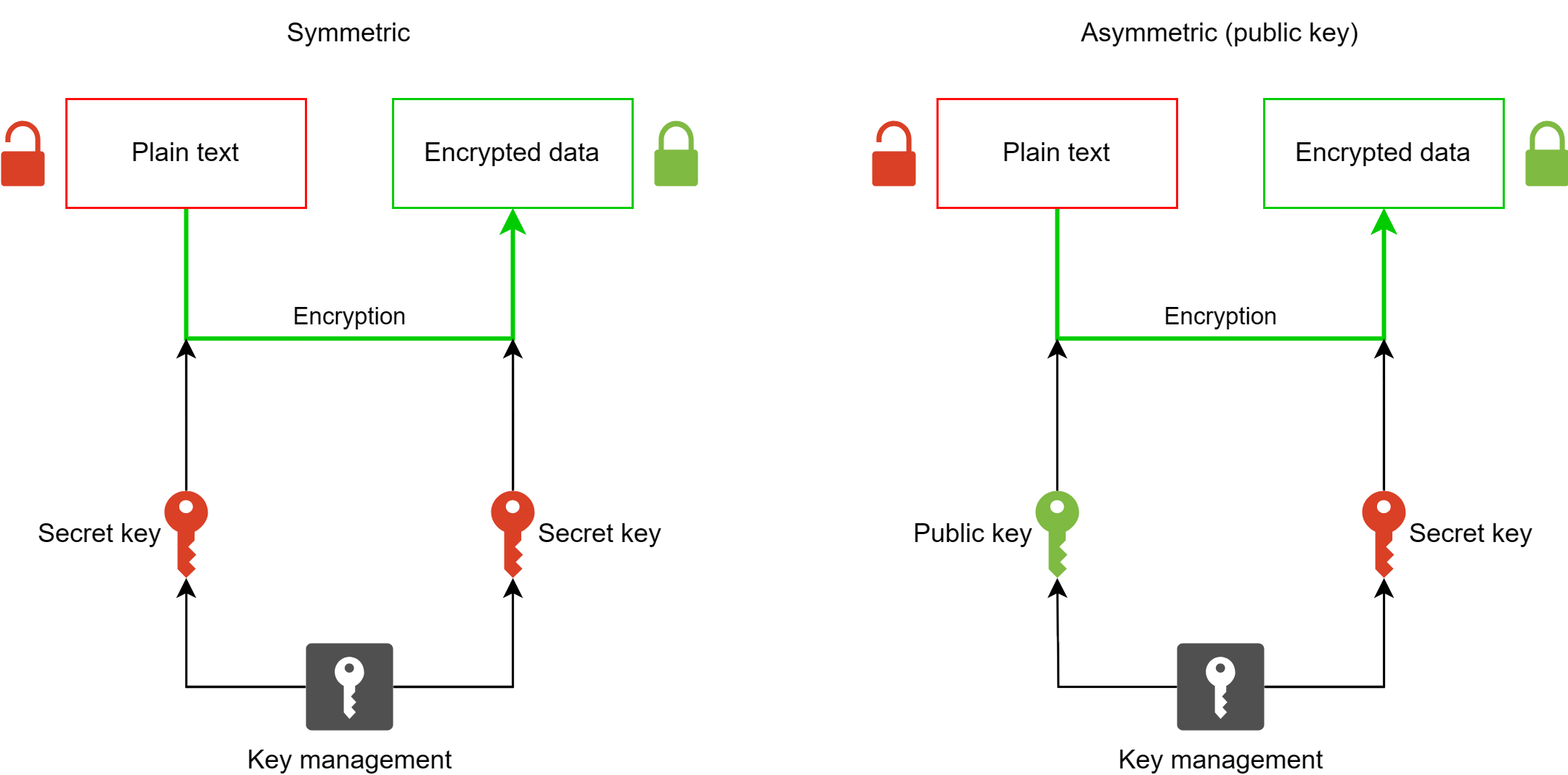
Symmetric Encryption Algorithms
Symmetric encryption algorithms use the same key for both encryption and decryption. The sender and receiver must securely share the secret key before communicating. Examples of symmetric encryption algorithms include:
- Advanced Encryption Standard (AES)
- Data Encryption Standard (DES, deprecated)
- Triple DES (3DES)
- Blowfish
Here’s an example of symmetric encryption using AES in Python:
from Crypto.Cipher import AES
key = b'0123456789abcdef' # 16-byte key
plaintext = b'This is a secret message'
cipher = AES.new(key, AES.MODE_EAX)
ciphertext, tag = cipher.encrypt_and_digest(plaintext)
print("Ciphertext:", ciphertext)Output:
Ciphertext: b'v\x97\xc7\x90\xfd\x12S\xb6\x82\x03\x1c\xf8\xdb(F\xc2'
In this output, ‘ciphertext’ is a byte string. The single backslash ‘\’ is used to indicate the start of an escape sequence, and the ‘\x’ followed by the hexadecimal digits represents a single byte value.
Asymmetric Encryption Algorithms
Asymmetric encryption algorithms, also known as public-key cryptography, use a pair of keys: a public key for encryption and a private key for decryption. The public key can be freely distributed, while the private key must be kept secret. Examples of asymmetric encryption algorithms include:
- RSA (Rivest-Shamir-Adleman)
- Elliptic Curve Cryptography (ECC)
- Diffie-Hellman key exchange
Here’s an example of asymmetric encryption using RSA in Python:
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
# Generate RSA key pair
key = RSA.generate(2048)
public_key = key.publickey()
plaintext = b'This is a secret message'
# Encrypt with public key
cipher = PKCS1_OAEP.new(public_key)
ciphertext = cipher.encrypt(plaintext)
print("Ciphertext:", ciphertext)Output:
Ciphertext: b'\x97\xf2\xf6~\x82\x8d\x1a\x98...'
Encryption in Databases and Data Warehouses
PostgreSQL
PostgreSQL supports various encryption algorithms for securing data at rest and in transit. It provides built-in functions for encrypting and decrypting data using algorithms like AES, 3DES, and Blowfish.
Example of encrypting a column in PostgreSQL using AES:
CREATE EXTENSION pgcrypto;
CREATE TABLE sensitive_data (
id SERIAL PRIMARY KEY,
name TEXT,
encrypted_ssn BYTEA
);
INSERT INTO sensitive_data (name, encrypted_ssn)
VALUES ('John Doe', pgp_sym_encrypt('123-45-6789', 'secret_key'));To decrypt the data:
SELECT name, pgp_sym_decrypt(encrypted_ssn, 'secret_key') AS ssn FROM sensitive_data;
MongoDB
MongoDB supports encryption at various levels, including transport encryption (TLS/SSL), storage encryption, and field-level encryption. It provides the MongoDB Encrypted storage engine for encrypting data at rest using AES-256 encryption.
Example of enabling encryption in MongoDB YAML configuration file:
security: enableEncryption: true encryptionKeyFile: /path/to/keyfile
For field-level encryption, MongoDB offers the Client-Side Field Level Encryption library. This library allows encrypting specific fields using various encryption algorithms.
Snowflake
Snowflake, a cloud-based data warehousing platform, provides encryption for data at rest and in transit. It automatically encrypts all data stored in Snowflake using AES-256 encryption. Additionally, Snowflake supports secure client connections using TLS/SSL encryption.
Snowflake also offers column-level encryption using a feature called “Column-Level Security.” It allows encrypting sensitive columns using customer-managed keys.
Example of creating an encrypted column in Snowflake:
CREATE OR REPLACE TABLE sensitive_data ( id NUMBER, name STRING, ssn STRING ENCRYPT );
Best Practices for Encryption
- Use strong encryption algorithms like AES with a minimum key size of 256 bits.
- Protect encryption keys securely and rotate them regularly.
- Enable encryption for data at rest and in transit.
- Implement proper key management solutions to safeguard encryption keys.
- Use salting and hashing techniques for storing passwords.
- Regularly monitor and audit encryption systems for vulnerabilities and breaches.
On deprecated encryptions
It’s important to keep up with the security of encryption algorithms. Some encryption algorithms that were once widely used are now considered unsafe. Using these deprecated or unsafe algorithms can put your data at risk of being compromised.
One notable example is the Data Encryption Standard (DES), which was once the standard encryption algorithm used by the U.S. government and many organizations worldwide. However, with the advancement of computing power, DES became susceptible to brute-force attacks. Its 56-bit key size was no longer considered secure enough to protect sensitive data. As a result, DES was officially deprecated and replaced by Triple DES (3DES) and AES.
Another algorithm that has faced security concerns is the Rivest Cipher 4 (RC4). RC4 was widely used in various protocols, including SSL/TLS and WEP (Wired Equivalent Privacy) for wireless network security.
However, numerous vulnerabilities and weaknesses were discovered in RC4. This made it susceptible to attacks. Consequently, RC4 has been prohibited in many security protocols.
It is important to be careful when using encryption algorithms. Some algorithms may have been created or endorsed by individuals or organizations with questionable reputations. Others may not have undergone proper peer review.
Some algorithms, such as the Dual_EC_DRBG random number generator, have been found to contain backdoors or weaknesses that could be exploited by attackers. Rely on well-established, extensively analyzed, and widely accepted encryption algorithms that have undergone rigorous scrutiny by the cryptographic community.
Algorithm Selection
When choosing an encryption algorithm, you should select one that is well-vetted and endorsed by reputable organizations. Currently, algorithms like AES and ChaCha20-Poly1305 are considered secure and widely used. It’s also essential to use encryption algorithms in conjunction with secure modes of operation, such as GCM (Galois/Counter Mode) or EAX mode. This ensures the confidentiality and integrity of the encrypted data.
Staying up to date with the latest security research and recommendations from trusted sources is crucial. National Institute of Standards and Technology (NIST) and the Open Web Application Security Project (OWASP) provide guidelines and recommendations on secure encryption practices.
Conclusion
Encryption algorithms play a crucial role in securing databases and data warehouses. By employing symmetric and asymmetric encryption techniques, organizations can protect sensitive data from unauthorized access and ensure confidentiality. Popular databases and data platforms like PostgreSQL, MongoDB, and Snowflake provide built-in encryption features that help safeguard data.
To further enhance data security and compliance, consider exploring the exceptional tools offered by DataSunrise. DataSunrise provides comprehensive solutions for data maintenance, security, audit rules, masking, and compliance. Contact DataSunrise team and request an online demo and discover how our expertise can help you fortify your data protection.
