
Enterprise Data Protection Services

In today’s digital landscape, protecting sensitive information is paramount for businesses of all sizes. Large companies face a tough challenge because they deal with a lot of complex data. This article discusses Enterprise Data Protection Services. It explains what they are, how they work, and why they are important for businesses today.
What is Enterprise Data Protection?
Enterprise Data Protection is how large corporations safeguard their critical data. This encompasses a wide range of activities, including:
- Data encryption
- Access control
- Backup and recovery
- Compliance management
- Threat detection and prevention
The goal is to ensure data privacy, integrity, and availability across the entire enterprise ecosystem.
Implementing Enterprise Data Protection
Several approaches exist for implementing enterprise data protection:
On-Premises Solutions
Traditional on-premises solutions involve deploying hardware and software within the company’s physical infrastructure. This approach offers complete control over data and systems but requires significant upfront investment and ongoing maintenance.
Cloud-Based Services
Cloud-based enterprise data protection services leverage the power and flexibility of cloud computing. These solutions offer flexibility, cost-efficiency, and automatic updates. However, they may raise concerns about data sovereignty and control.
Hybrid Approaches
Many enterprises opt for a hybrid approach, combining on-premises and cloud-based solutions. This strategy allows organizations to balance control and flexibility, keeping sensitive data on-site while leveraging cloud services for less critical information.
Some advanced solutions, such as DataSunrise, allow you to control data security in both on-premise and cloud environments. This flexibility is increasingly important as enterprises adopt multi-cloud and hybrid infrastructures.
Challenges in Enterprise Data Protection
Protecting data at an enterprise level presents unique challenges:
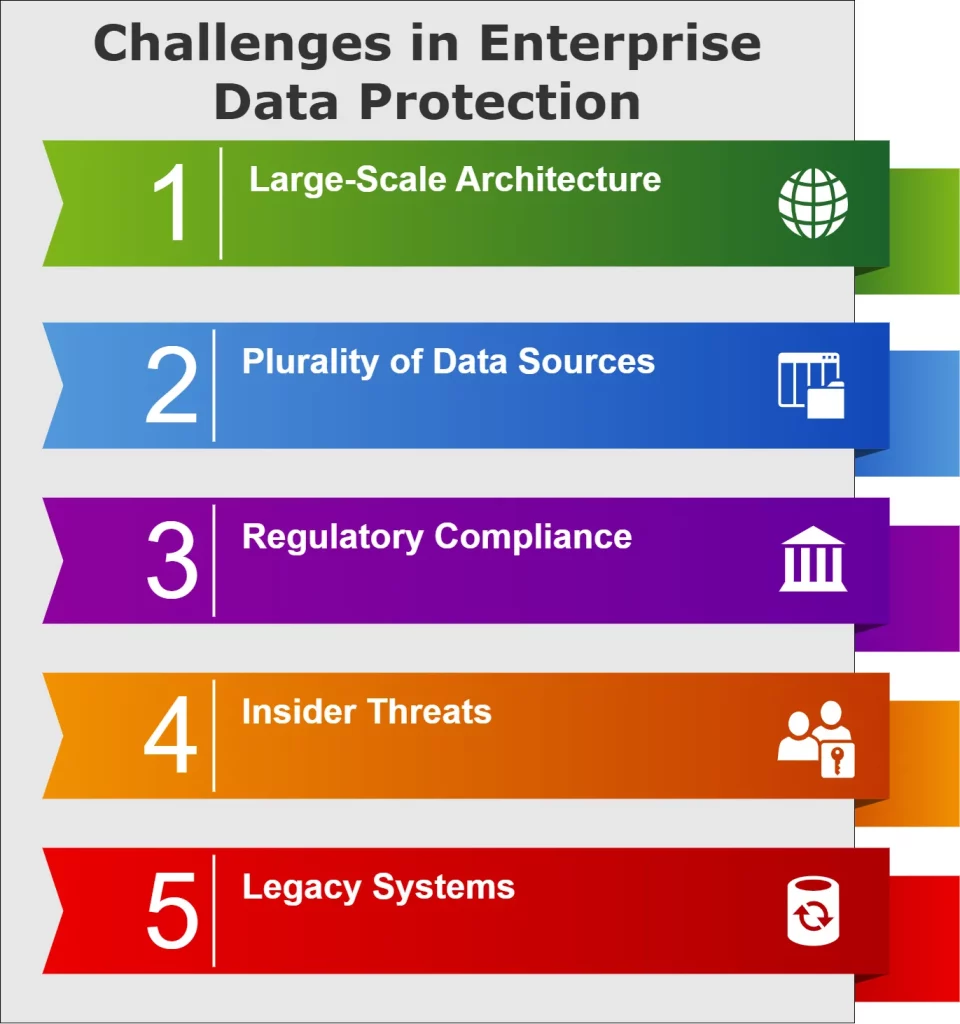
Large-Scale Architecture
Enterprises often have complex, distributed IT environments spanning multiple locations and systems. This complexity makes it difficult to maintain a consistent security posture across the organization.
Plurality of Data Sources
Large businesses typically deal with diverse data sources, including:
- Customer databases
- Financial records
- Business data
- IoT device inputs
- Third-party integrations
Each of these sources may require different protection strategies and compliance considerations.
Regulatory Compliance
Businesses need to follow various data protection rules like GDPR, CCPA. It may also need to follow industry-specific regulations such as HIPAA for healthcare. Ensuring compliance across all data assets is a significant challenge.
Insider Threats
With a large workforce and numerous access points, the risk of insider threats – whether malicious or accidental – increases significantly.
Legacy Systems
Many enterprises still rely on legacy systems that may not be compatible with modern security solutions, creating potential security breaches.
Enterprise Data Security as a Service
To address these challenges, many organizations are turning to Data Security as a Service (DSaaS) solutions. Sometimes people call this Data Management as a Service. This model offers several advantages:
- Scalability: Easily adapt to changing data volumes and business needs
- Cost-effectiveness: Reduce upfront investments and costs
- Expertise: Leverage specialized security knowledge and resources
- Continuous updates: Stay protected against evolving threats
Technologies Involved in DSaaS
DSaaS solutions typically incorporate a range of advanced technologies:
- Machine Learning and AI: For anomaly detection and predictive threat analyzing
- Blockchain: To ensure data integrity and create tamper-proof audit trails
- Zero Trust Architecture: Assumes no user or system is trustworthy by default
- Data Loss Prevention (DLP): Monitors and controls data in use, in motion, and at rest
- Cloud Access Security Brokers (CASBs): Secure cloud-based resources and applications
Key Components of Enterprise Data Protection Services
Let’s explore some essential elements of a comprehensive enterprise data protection strategy:
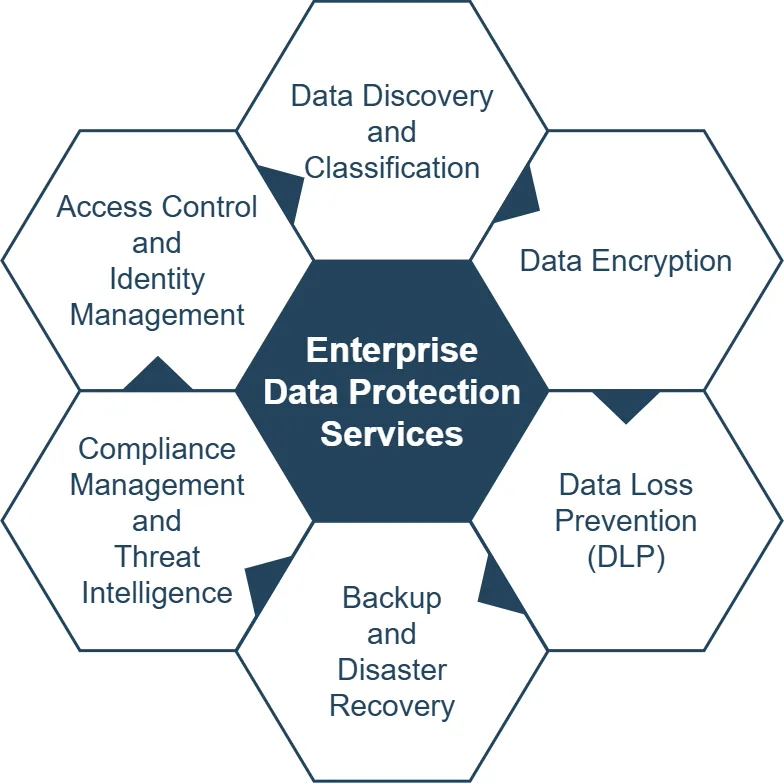
Data Discovery
Before you can protect your data, you need to know what you have and where it resides. Data discovery tools help identify sensitive information across your enterprise, while classification systems categorize data based on its sensitivity and importance.
Access Control and Identity Management
Implementing robust access control measures is crucial for enterprise data protection. This includes:
- Multi-factor authentication (MFA)
- Role-based access control (RBAC)
- Single sign-on (SSO) solutions
- Privileged access management (PAM)
These tools ensure that only authorized users can access sensitive data and systems.
Data Encryption
Encryption is a cornerstone of data protection. Enterprises should implement:
- At-rest encryption: Protects data stored on servers, databases, and endpoints
- In-transit encryption: Secures data as it moves across networks
- End-to-end encryption: Provides continuous protection from source to destination
Data Loss Prevention (DLP)
DLP solutions help prevent unauthorized data exfiltration. They monitor data movement and can block or alert on suspicious activities. For example, a DLP system might prevent an employee from emailing a sensitive document to an external address.
Backup and Disaster Recovery
Regular backups and a solid disaster recovery plan are essential for maintaining data availability. This includes:
- Automated backup systems
- Offsite data storage
- Regular disaster recovery drills
- Rapid restoration capabilities
Example:
The simplest way to backup PostgreSQL databases using the command line in Linux is to use the pg_dump utility. Syntax is as follows:
pg_dump -U username -d database_name > backup_file.sql
This command will create a SQL file named backup_file.sql in the current directory, containing a full backup of the “database_name” database.
Actually MySQL also has the same syntax utility (mysqldump):
mysqldump -u username -p database_name > backup_file.sql
Compliance Management
Enterprise data protection services often include tools for managing regulatory compliance. These solutions can:
- Track compliance requirements
- Automate compliance reporting
- Conduct regular audits
- Manage data retention policies
Threat Intelligence and Incident Response
Proactive threat detection and rapid incident response are crucial for minimizing data breaches. This involves:
- Real-time monitoring and alerting
- Threat intelligence feeds
- Automated incident response workflows
- Regular security assessments and penetration testing
Best Practices for Enterprise Data Protection
To maximize the effectiveness of your data protection efforts, consider these best practices:
- Develop a comprehensive data protection strategy
- Implement a zero-trust security model
- Regularly train employees on data security best practices
- Conduct frequent security audits and assessments
- Stay informed about emerging threats
- Implement a robust patch management program
- Establish clear data governance policies
- Regularly test your incident response plan
- Leverage automation to reduce human error
- Continuously monitor and improve your security posture
Case Study: Financial Services Firm Enhances Data Protection
Let’s look at a real-world example of enterprise data protection in action:
A large financial services firm was struggling to maintain consistent data security across its global operations. They implemented a comprehensive DSaaS solution that included:
- Automated data discovery
- Advanced encryption for all sensitive data
- Real-time monitoring and alerting
- Centralized access control and identity management
Results:
- 60% reduction in security incidents
- 40% improvement in compliance audit scores
- 25% decrease in data protection costs
- Enhanced ability to adapt to new regulations
This case demonstrates how enterprise data protection services can deliver tangible benefits to large organizations.
The Future of Enterprise Data Protection
As technology evolves, so too will the landscape of enterprise data protection. Some trends to watch include:
- Increased use of AI and machine learning for threat detection
- Greater integration of security tools across the enterprise
- Rise of quantum-resistant encryption methods
- Expansion of privacy-enhancing technologies (PETs)
- Growing focus on securing IoT and edge computing environments
Conclusion: Safeguarding Your Enterprise’s Most Valuable Asset
In today’s world, protecting business data is crucial. Data breaches can be costly and harm a company’s reputation. Strong data protection is essential for success. By leveraging advanced services and following best practices, organizations can safeguard their most valuable asset: their data.
Remember, effective data protection is an ongoing process that requires constant vigilance and adaptation. Stay informed, stay prepared, and prioritize the security of your enterprise data.
DataSunrise provides a range of user-friendly and flexible tools for database security and compliance, ideal for businesses. Visit the DataSunrise website for an online demo and discover how we can help protect your enterprise data assets.
