
Granular Data Access Control: Tips & Practices

Introduction
In today’s data-driven world, organizations handle vast amounts of sensitive information. Ensuring that the right people have access to data at the right time is important. This is crucial for protecting data security and privacy. This is where granular data access control comes into play.
Granular data access control lets organizations set detailed access rules for better security and control over their data. In this article, we’ll explore the basics of granular access, its benefits, implementation strategies, and best practices.
What is Granular Data Access Control?
Granular data access control is a security method that lets organizations control access to data at a detailed level. It means setting rules for who can access what based on roles, data importance, and business needs.
Granular data access control focuses on controlling access to specific data elements or records within an application or database. This method is different from other access control models that focus on controlling access at the application or system level.
For example, consider a healthcare application that stores patient records. Granular access lets doctors access only the medical records of their assigned patients. This means that the system restricts sensitive information such as personal identification numbers or financial details.
Benefits of Granular Data Access Control
Implementing granular access offers several benefits to organizations:
- Enhanced Data Security: By controlling who can view data, organizations can reduce the risk of unauthorized access and data breaches. Access policies limit user access to necessary data to prevent misuse and abuse. Users control the data they can access.
- Compliance with Regulations: Several industries must follow strict data protection rules, like HIPAA in healthcare or GDPR in the European Union. Granular data access control helps organizations comply with regulations by enforcing strict access rules and monitoring data access activities.
- Improved Data Privacy: With granular data access control, organizations can protect the privacy of sensitive information by limiting access to authorized individuals only. This is particularly important when dealing with personally identifiable information (PII) or protected health information (PHI).
- Increased Operational Efficiency: Organizations can improve efficiency and reduce errors by giving users access only to the data they need. Granular data access control simplifies managing user access rights. Defining and enforcing policies at a more specific level achieves this.
Implementing Granular Data Access Controls
To implement granular access, organizations can follow these steps:
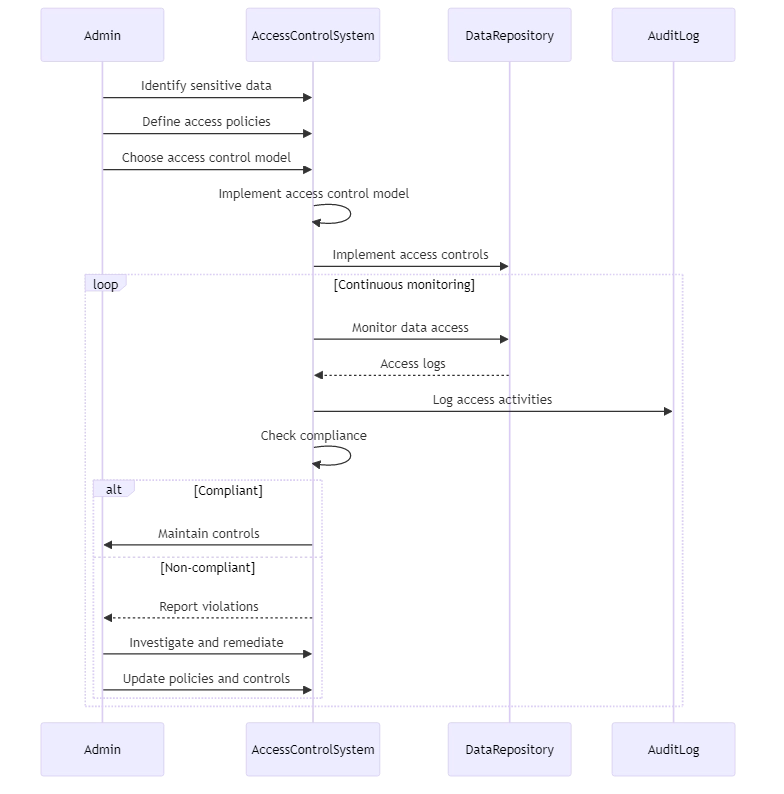
- Identify Sensitive Data: Start by identifying the sensitive data within your organization that requires granular access control. This may include customer information, financial data, intellectual property, or any other data that is critical to your business.
- Define Access Policies: Create rules for who can access certain data and when they can access it based on sensitive information. Consider factors such as user roles, data sensitivity, business requirements, and regulatory compliance.
- Choose an Access Control Model: Select an access control model that aligns with your organization’s needs. Common models include role-based access control (RBAC), attribute-based access control (ABAC), and policy-based access control (PBAC). Each model has its own strengths and considerations, so choose the one that best fits your requirements.
- Implement Access Controls: Implement the chosen access control model and enforce the defined access policies. This can involve deciding who can access certain things, assigning different roles to users, or connecting with identity management systems.
- Monitor and Audit: Regularly monitor and audit data access activities to ensure compliance with the defined access policies. Implement logging and reporting mechanisms to track who accessed what data and when. This helps detect and investigate any unauthorized access attempts or policy violations.
For example, let’s consider a scenario where you have a database table called customers that contains sensitive customer information. You want to control who can see certain columns of data based on their role. Only authorized users should have access. Here’s a code example using SQL to create roles and grant permissions:
-- Create roles CREATE ROLE sales_rep; CREATE ROLE manager; -- Grant permissions to roles GRANT SELECT (customer_id, name, email) ON customers TO sales_rep; GRANT SELECT ON customers TO manager; -- Create users and assign roles CREATE USER john WITH PASSWORD 'password123'; CREATE USER sarah WITH PASSWORD 'password456'; GRANT sales_rep TO john; GRANT manager TO sarah;
In this example, we create two roles: sales_rep and manager. The sales representative can only see customer_id, name, and email columns in the customers table. The manager, on the other hand, can see the entire table. We then create two users, john and sarah, and assign them the respective roles.
John has access to only the customer’s ID, name, and email. Sarah can see everything in the customers table. This demonstrates granular data access control at the column level.
Granular Data Access Control Best Practices
To ensure effective granular control, consider the following best practices:
- Principle of Least Privilege: Grant users the minimum level of access required to perform their tasks. Avoid granting excessive permissions that can lead to data exposure or misuse.
- Regular Access Reviews: Regularly review user access to match their current job duties and responsibilities. Remove or modify access rights as needed to maintain the principle of least privilege.
- Separation of Duties: Implement separation of duties to prevent any single user from having excessive control over sensitive data. For example, separate the roles of data administrators and data auditors to maintain checks and balances.
- Secure Data Storage: Securely store sensitive data by using encryption, tokenization, or other data protection mechanisms. This adds an extra layer of security in case of unauthorized access attempts.
- Employee Training: Educate employees about the importance of data security and their responsibilities in protecting sensitive information. Provide training on access control policies and best practices to foster a culture of security awareness.
Conclusion
Granular data access control is a powerful approach to securing sensitive data within organizations. Organizations can enhance data security, comply with regulations, safeguard privacy, and operate more effectively by managing data access closely.
Implementing granular data access controls involves identifying sensitive data, defining access policies, choosing an appropriate access control model, and enforcing access controls. Organizations can create a strong data access control system by following best practices.
These practices include implementing the principle of least privilege, conducting regular access reviews, and providing employee training.
