
Greenplum Audit Log

The importance of maintaining comprehensive audit logs in Greenplum Database environments has become increasingly critical as organizations face growing cybersecurity challenges. Gartner research reveals that organizations implementing advanced database audit logging and monitoring solutions reduce their risk of data breaches by up to 70%, while also cutting incident response times by nearly half.
Understanding Greenplum Audit Logs
Greenplum’s audit logging system operates across all database instances (coordinator and segments), capturing detailed information about database operations, user activities, and system events. The logging infrastructure consists of several key components:
Core Components
CSV-format Log Files
- Each database instance maintains its own log files
- Logs are stored in a standardized CSV format
- Contains detailed event records with timestamps
- Includes user identification and session information
Log Management System
- Handles log rotation and archival
- Manages storage allocation
- Controls retention periods
- Coordinates distributed logging across segments
Analysis Tools
- gplogfilter utility for log analysis
- System catalogs for metadata tracking
- Custom SQL queries for log investigation
- Integration with external monitoring tools and logging facilities
Configuring Greenplum Audit Logs
Basic Configuration
To enable comprehensive audit logging in Greenplum, implement these essential settings:
-- Enable CSV logging ALTER SYSTEM SET log_destination = 'csvlog'; -- Configure basic logging parameters ALTER SYSTEM SET logging_collector = on; ALTER SYSTEM SET log_truncate_on_rotation = on; ALTER SYSTEM SET log_rotation_age = '1d'; ALTER SYSTEM SET log_rotation_size = '100MB'; -- Enable detailed logging ALTER SYSTEM SET log_error_verbosity = 'verbose'; ALTER SYSTEM SET log_min_messages = 'info';
Advanced Logging Configuration
For enhanced audit capabilities, add these additional settings:
-- Enable extended logging details ALTER SYSTEM SET log_connections = on; ALTER SYSTEM SET log_disconnections = on; ALTER SYSTEM SET log_duration = on; ALTER SYSTEM SET log_statement = 'all'; ALTER SYSTEM SET log_min_duration_statement = '1000'; -- Configure log line prefix for detailed context ALTER SYSTEM SET log_line_prefix = '%t [%p]: [%l-1] user=%u,db=%d,app=%a,client=%h ';
Practical Implementation Examples
1. Analyzing Authentication Attempts
Monitor failed login attempts and suspicious authentication patterns:
SELECT event_time,
user_name,
database_name,
remote_host,
event_message
FROM gp_toolkit.gp_log_system
WHERE event_severity = 'LOG'
AND event_message LIKE '%authentication failed%'
ORDER BY event_time DESC
LIMIT 10;Example output:
| Event Time | User Name | Database Name | Remote Host | Event Message |
|---|---|---|---|---|
| 2024-02-14 15:30:45 | analyst | salesdb | 10.0.1.100 | authentication failed |
| 2024-02-14 15:28:32 | etl_user | datamart | 10.0.1.101 | authentication failed |
| 2024-02-14 15:25:18 | admin | production | 10.0.1.102 | authentication failed |
2. Tracking DDL Operations
Monitor schema changes and structural modifications:
SELECT event_time,
user_name,
database_name,
event_message
FROM gp_toolkit.gp_log_system
WHERE event_severity = 'INFO'
AND (event_message LIKE 'CREATE%'
OR event_message LIKE 'ALTER%'
OR event_message LIKE 'DROP%')
AND event_time >= current_timestamp - interval '24 hours'
ORDER BY event_time DESC;Example output:
| Event Time | User Name | Database Name | Event Message |
|---|---|---|---|
| 2024-02-14 16:45:22 | admin | production | CREATE TABLE sales_2024 |
| 2024-02-14 16:30:15 | dev_lead | staging | ALTER TABLE customers ADD COLUMN |
| 2024-02-14 16:15:08 | etl_user | datamart | DROP INDEX idx_customer_id |
3. Query Performance Analysis
Analyze long-running queries and performance patterns on the clients table:
SELECT event_time,
user_name,
database_name,
substring(event_message from 'duration: (\d+\.\d+) ms') as duration_ms,
substring(event_message from 'statement: (.*)') as query
FROM gp_toolkit.gp_log_system
WHERE event_message LIKE '%duration:%'
AND database_name = 'testdb'
AND event_message LIKE '%public.clients%'
AND event_time >= current_timestamp - interval '1 hour'
ORDER BY duration_ms::float DESC
LIMIT 5;Example output:
| Event Time | User Name | Database Name | Duration (ms) | Query |
|---|---|---|---|---|
| 2024-02-14 16:45:22 | analyst | testdb | 5842.3 | SELECT * FROM public.clients WHERE birth_date > ‘1990-01-01’ |
| 2024-02-14 16:30:15 | admin | testdb | 4521.8 | UPDATE public.clients SET sex = ‘F’ WHERE id BETWEEN 1000 AND 2000 |
| 2024-02-14 16:15:08 | etl_user | testdb | 3845.2 | SELECT first_name, last_name FROM public.clients WHERE sex = ‘M’ |
| 2024-02-14 16:10:45 | dev_lead | testdb | 2954.7 | DELETE FROM public.clients WHERE id < 100 |
| 2024-02-14 16:05:33 | support | testdb | 2145.9 | SELECT COUNT(*) FROM public.clients GROUP BY sex |
Enhancing Audit Logs with DataSunrise
While Greenplum’s native audit logging provides essential capabilities, modern enterprise environments often demand more sophisticated solutions. DataSunrise addresses these requirements by extending Greenplum’s logging capabilities through its innovative database security platform.
Operating as a proxy between applications and Greenplum Database, DataSunrise intercepts and analyzes all database traffic in real-time. This enables comprehensive monitoring without modifying your existing database infrastructure or application code.
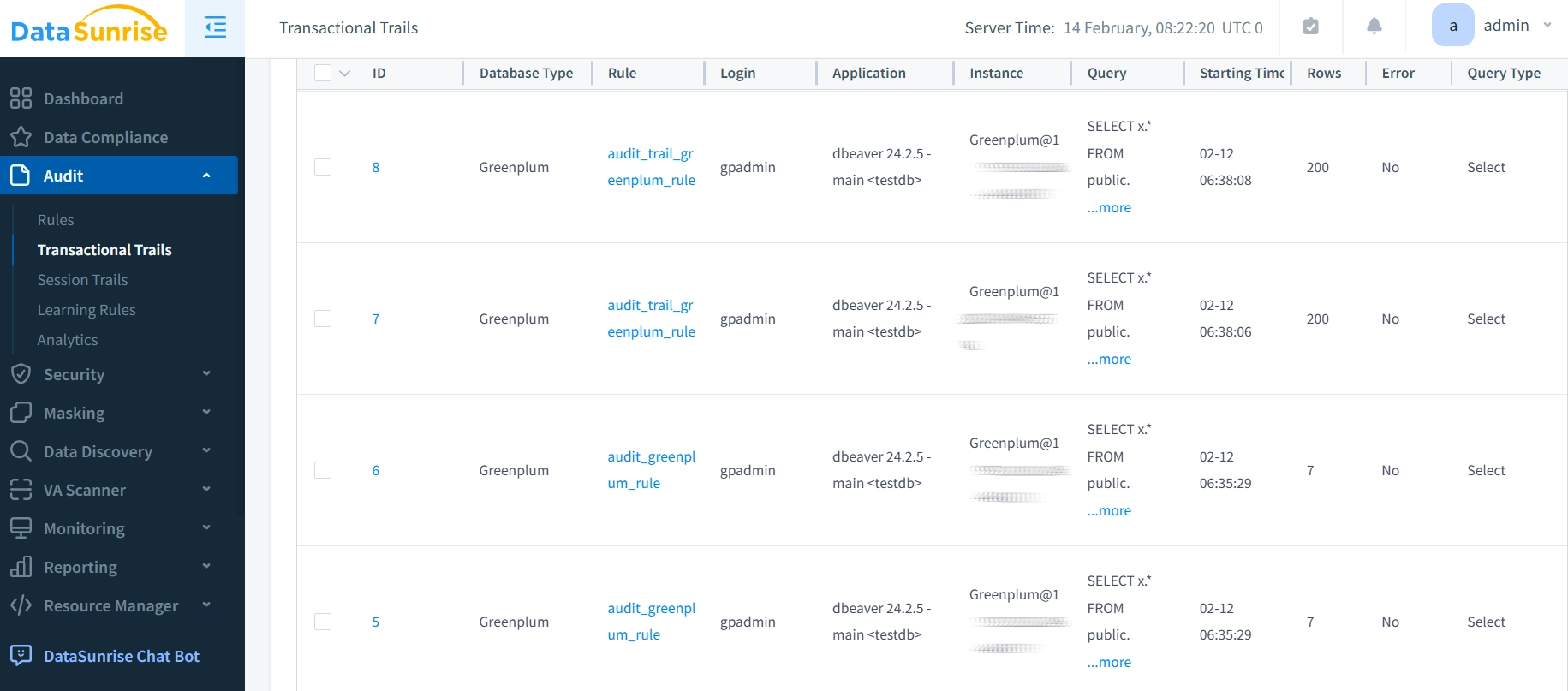
The platform transforms raw audit data into actionable security insights through:
- Centralized log collection and real-time analysis across all database instances
- Intelligent pattern detection and anomaly identification
- Automated compliance reporting for GDPR, HIPAA, and PCI DSS
- Integration with existing security infrastructure and SIEM systems
DataSunrise’s intuitive interface allows security teams to quickly identify and respond to potential security threats, while its customizable dashboards help filter out noise and focus on relevant security events. This combination of advanced monitoring capabilities and user-friendly design makes it an effective solution for organizations seeking to enhance their Greenplum audit logging infrastructure.
Best Practices for Audit Log Management
Performance and Storage
- Implement automated log rotation based on file size and age
- Enable selective logging based on operation criticality and data sensitivity
- Schedule intensive logging operations during off-peak hours
- Monitor storage capacity and adjust retention policies accordingly
- Use compression for archived logs to optimize storage utilization
Security and Access Control
- Encrypt log files both at rest and in transit
- Implement role-based access controls for log management
- Monitor and alert on unauthorized log access attempts
- Regularly validate log file integrity
- Maintain separate logging credentials from application credentials
Third-Party Solutions and Integration
- Use third-party solutions like DataSunrise to enhance native logging capabilities
- Implement centralized log management and analysis
- Configure real-time alerting and monitoring systems
- Enable automated security response mechanisms
- Leverage advanced analytics for threat detection
Compliance and Documentation
- Document all logging configurations and changes
- Generate automated compliance reports for regulatory requirements
- Maintain audit trails of log access and modifications
- Review and update logging policies regularly
- Establish clear retention policies aligned with industry regulations
Conclusion
Effective audit logging in Greenplum requires a balanced approach combining native capabilities with specialized tools. While Greenplum provides robust built-in logging features, organizations often benefit from implementing additional solutions like DataSunrise to enhance their security and compliance capabilities.
Success in audit log implementation depends on finding the right balance between comprehensive monitoring and system performance. Regular assessment and updates of logging policies, combined with appropriate tool selection, enable organizations to maintain strong security postures while meeting operational requirements.
Experience how DataSunrise can enhance your Greenplum audit logging capabilities by scheduling an online demo today.
