
Greenplum Audit Tools

In today’s data-driven landscape, organizations managing large-scale data operations with Greenplum require robust tools for security monitoring and compliance. According to Verizon’s 2024 Data Breach Investigations Report, 83% of data breaches involve external actors, with database-related incidents remaining a primary attack vector. This highlights the critical importance of implementing proper audit mechanisms and tools for database security.
Understanding Greenplum’s Native Audit Tools
Greenplum Database provides several built-in tools for audit and security analysis. As organizations face increasingly sophisticated security threats, proper configuration of these tools becomes essential for maintaining data protection and regulatory compliance.
gplogfilter
The primary command-line utility for analyzing Greenplum Database log files. Key capabilities include:
- Log parsing and filtering based on multiple criteria
- Pattern matching across distributed log files
- Timestamp-based log analysis
- User activity tracking
- Error and warning identification
Example usage:
# View last 100 error messages gplogfilter -t ERROR -n 100 # Filter logs for a specific user gplogfilter -u admin -d database_name # Analyze logs within a time range gplogfilter -b '2024-02-01 00:00:00' -e '2024-02-14 23:59:59'
Example output:
| Timestamp | User | Database | Severity | Message |
|---|---|---|---|---|
| 2024-02-14 15:30:22 | admin | sales_db | ERROR | Failed connection attempt |
| 2024-02-14 15:28:15 | etl_user | warehouse | ERROR | Query timeout exceeded |
| 2024-02-14 15:25:03 | analyst | marketing | ERROR | Permission denied for relation |
gp_toolkit Administrative Schema
A built-in schema providing views and functions for:
- Log file analysis
- Query monitoring
- Resource utilization tracking
- Session management
- Configuration validation
Example queries:
-- Monitor active queries SELECT * FROM gp_toolkit.gp_log_system WHERE event_severity = 'LOG' AND event_time >= current_timestamp - interval '1 hour'; -- Track resource usage SELECT * FROM gp_toolkit.gp_resqueue_status;
Example output for active queries:
| Event Time | Username | Database | Event Type | Message |
|---|---|---|---|---|
| 2024-02-14 16:45:22 | analyst | sales | QUERY | SELECT * FROM orders |
| 2024-02-14 16:42:18 | admin | inventory | DDL | CREATE INDEX idx_product |
| 2024-02-14 16:40:05 | etl_user | warehouse | DML | INSERT INTO shipments |
Example output for resource usage:
| Queue Name | Active | Waiting | CPU Usage | Memory Usage |
|---|---|---|---|---|
| admin_queue | 5 | 2 | 45% | 2.5 GB |
| etl_queue | 8 | 3 | 75% | 4.8 GB |
| analyst_queue | 3 | 1 | 25% | 1.2 GB |
pg_stat Views
System views providing real-time statistics about:
- Database activity
- Table and index usage
- Backend processes
- Buffer utilization
- WAL activity
Example analysis query:
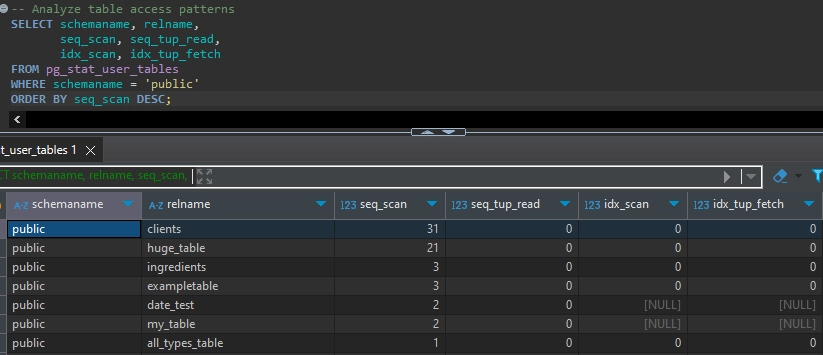
-- Analyze table access patterns
SELECT schemaname, relname,
seq_scan, seq_tup_read,
idx_scan, idx_tup_fetch
FROM pg_stat_user_tables
WHERE schemaname = 'public'
ORDER BY seq_scan DESC;Example output:
Advanced Audit Implementation
Configuring Comprehensive Auditing
1. Enable Basic Audit Settings:
ALTER SYSTEM SET logging_collector = on; ALTER SYSTEM SET log_destination = 'csvlog'; ALTER SYSTEM SET log_directory = 'pg_audit'; ALTER SYSTEM SET log_filename = 'gpdb-audit-%Y-%m-%d_%H%M%S.log';
2. Configure Detailed Event Tracking:
ALTER SYSTEM SET log_statement = 'all'; ALTER SYSTEM SET log_min_duration_statement = 1000; ALTER SYSTEM SET log_connections = on; ALTER SYSTEM SET log_disconnections = on;
3. Set Up Security Event Logging:
ALTER SYSTEM SET log_error_verbosity = 'verbose'; ALTER SYSTEM SET log_line_prefix = '%t [%p]: [%l-1] user=%u,db=%d,app=%a '; ALTER SYSTEM SET log_checkpoints = on; ALTER SYSTEM SET log_lock_waits = on;
Enhancing Audit Capabilities with DataSunrise
While Greenplum’s native tools provide essential functionality, DataSunrise offers advanced database activity history tracking and security capabilities specifically designed for enterprise environments. Operating as a proxy between applications and the database, DataSunrise provides comprehensive monitoring and threat detection without requiring changes to your existing infrastructure.
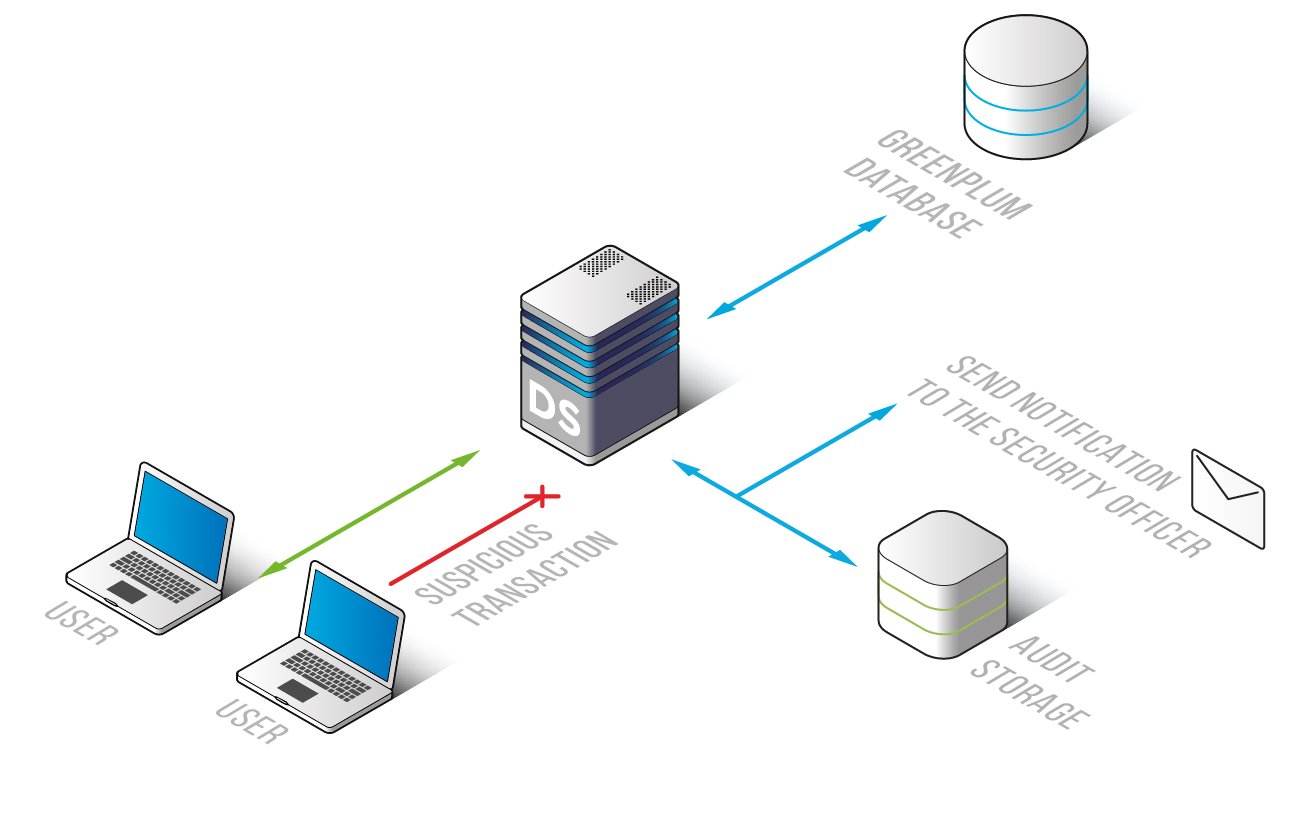
Key DataSunrise Features
Real-Time Monitoring Dashboard
- Live session tracking with detailed user attribution
- Query analysis and performance metrics
- Interactive visualizations of database activity
- Customizable alert thresholds
Audit Rule Configuration
DataSunrise provides an intuitive interface for creating and managing custom audit rules, allowing precise control over what database activities are monitored.
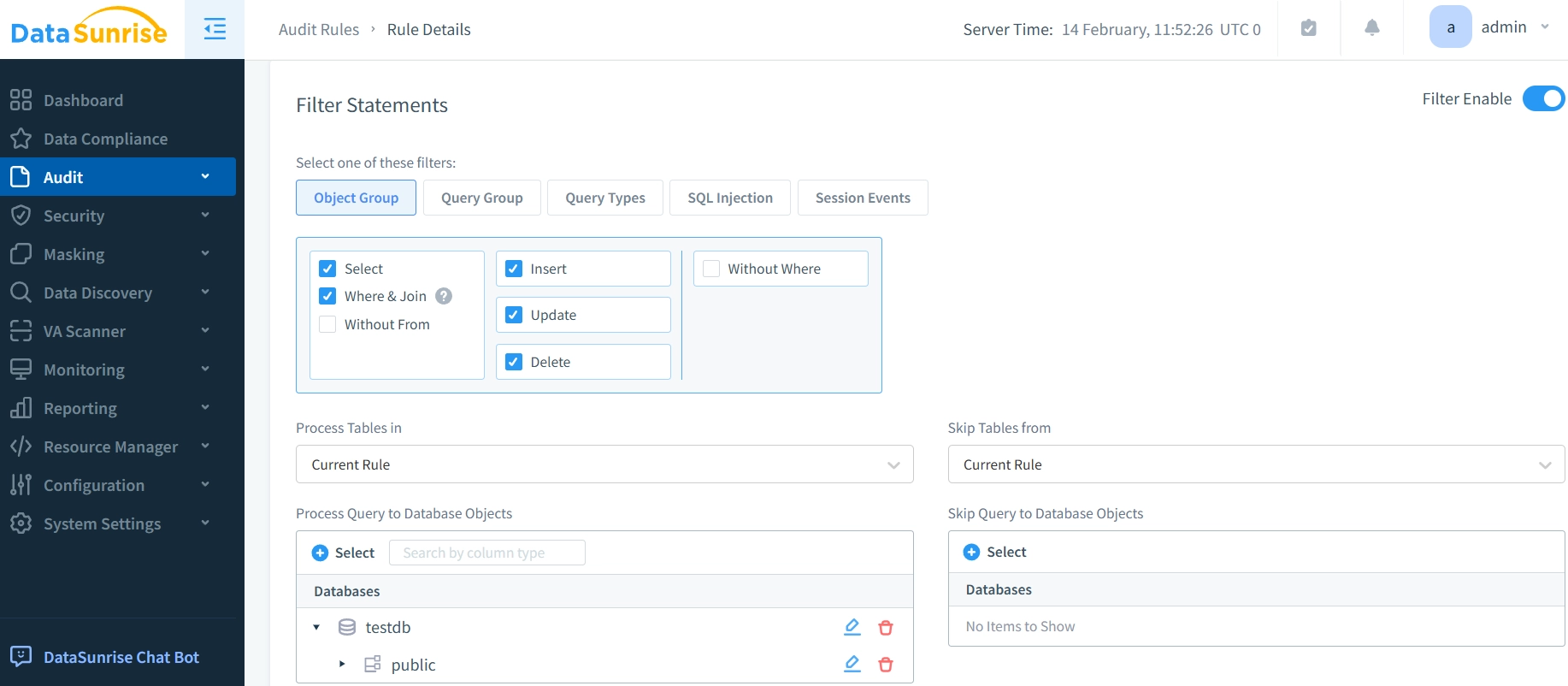
DataSunrise Audit Rule Configuration Interface for Greenplum Advanced Security Controls
- Dynamic data masking for sensitive information
- Automated threat detection using behavior analytics
- SQL injection prevention
- Access control policy enforcement
Compliance Management
- Automated compliance reporting for GDPR, HIPAA, PCI DSS
- Custom report generation
- Audit trail maintenance
- Policy-based data access monitoring
DataSunrise Implementation Benefits
Rapid deployment and seamless integration allow organizations to enhance their security posture without disrupting existing database operations. The proxy-based architecture eliminates the need for modifications to application code or database configurations.
Reduced administrative overhead comes from centralized policy management and automated workflows. Security teams can manage multiple database instances more efficiently, spending less time on routine tasks and more on strategic security initiatives.
Lower total cost of ownership results from consolidated tooling and automated processes. Organizations can reduce the number of separate security tools needed while improving their overall security effectiveness through integrated monitoring and protection.
Best Practices for Audit Tool Usage
Performance Optimization starts with appropriate logging levels and efficient rotation policies. Monitor system impact regularly and adjust configurations to maintain optimal performance while meeting security requirements.
Security Controls should focus on encryption of sensitive audit data and strong access controls. Regular security reviews and automated monitoring help maintain audit trail integrity.
Third-Party Solutions like DataSunrise extend native capabilities with advanced features such as real-time monitoring and automated threat detection. Choose solutions that integrate well with existing infrastructure and match security requirements.
Maintenance and Updates require regular review of audit policies and tool configurations. Schedule routine updates and performance tuning to ensure continued effectiveness as security needs evolve.
Conclusion
Effective audit tool implementation in Greenplum requires a balanced approach combining native capabilities with specialized solutions. While Greenplum provides robust built-in tools, organizations often benefit from integrating additional solutions to enhance their security and compliance capabilities.
Success in audit tool implementation depends on selecting appropriate tools, implementing them correctly, and maintaining them effectively. Regular assessment and updates of audit policies, combined with proper tool selection and configuration, enable organizations to maintain strong security postures while meeting operational requirements.
For organizations seeking to enhance their Greenplum audit capabilities, visit DataSunrise website and schedule an online demo to understand how it can complement your existing audit infrastructure.
