
Greenplum Audit Trail

Implementing an effective audit trail in Greenplum Database has become increasingly critical for modern organizations. With the rising frequency of security threats, maintaining detailed records of database activities is essential for both security and compliance. Recent cybersecurity studies indicate that inadequate audit trails contribute to delayed breach detection, emphasizing the need for robust database monitoring.
Greenplum Database provides comprehensive audit trail capabilities through its logging system. By implementing proper data security measures and audit configurations, organizations can effectively track database activities and maintain regulatory compliance.
Greenplum Audit Trail Fundamentals
According to the Greenplum documentation, audit trails in Greenplum capture various types of database events:
- User authentication attempts
- Database object access
- Schema modifications
- Data manipulation operations
- System configuration changes
- Query execution details
Basic Audit Trail Configuration
-- Enable comprehensive audit logging ALTER SYSTEM SET logging_collector = on; ALTER SYSTEM SET log_destination = 'csvlog'; ALTER SYSTEM SET log_directory = 'pg_log'; ALTER SYSTEM SET log_filename = 'gpdb-%Y-%m-%d_%H%M%S.log';
These settings ensure that:
- All log entries are collected systematically
- Logs are stored in CSV format for easy analysis
- File naming follows a consistent datetime pattern
- Log rotation is properly managed
Advanced Trail Configuration
1. Detailed Event Logging
-- Configure detailed event tracking ALTER SYSTEM SET log_statement = 'all'; ALTER SYSTEM SET log_duration = on; ALTER SYSTEM SET log_parser_stats = on; ALTER SYSTEM SET log_planner_stats = on; ALTER SYSTEM SET log_executor_stats = on;
2. Security Event Tracking
-- Enable security-related logging ALTER SYSTEM SET log_connections = on; ALTER SYSTEM SET log_disconnections = on; ALTER SYSTEM SET log_error_verbosity = 'verbose'; ALTER SYSTEM SET password_encryption = 'scram-sha-256';
Practical Trail Analysis Examples
Monitoring Client Table Access
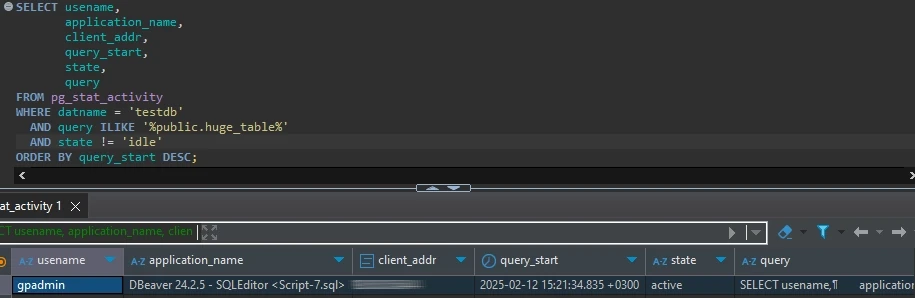
-- Track all access to the clients table
SELECT usename,
application_name,
client_addr,
query_start,
state,
query
FROM pg_stat_activity
WHERE datname = 'testdb'
AND query ILIKE '%public.huge_table%'
AND state != 'idle'
ORDER BY query_start DESC;
Example output:
Access Pattern Analysis
-- Analyze access patterns over time
SELECT date_trunc('hour', query_start) as access_time,
usename,
count(*) as access_count,
string_agg(DISTINCT client_addr::text, ', ') as source_ips
FROM pg_stat_activity
WHERE datname = 'testdb'
AND query ILIKE '%public.huge_table%'
AND query_start >= current_timestamp - interval '24 hours'
GROUP BY date_trunc('hour', query_start), usename
ORDER BY access_time DESC;
User Operation Summary
SELECT
usename,
client_addr,
date_trunc('day', query_start) as operation_date,
count(*) as total_operations,
sum(case when query ILIKE '%SELECT%' then 1 else 0 end) as reads,
sum(case when query ILIKE '%UPDATE%' OR
query ILIKE '%INSERT%' OR
query ILIKE '%DELETE%' then 1 else 0 end) as writes
FROM pg_stat_activity
WHERE datname = 'testdb'
AND query ILIKE '%public.huge_table%'
GROUP BY usename, client_addr, date_trunc('day', query_start)
ORDER BY operation_date DESC, total_operations DESC;
Example output:
| usename | client_addr | operation_date | total_operations | reads | writes |
|---|---|---|---|---|---|
| admin | 10.0.1.100 | 2024-02-12 | 156 | 120 | 36 |
| etl_user | 10.0.1.101 | 2024-02-12 | 89 | 45 | 44 |
| analyst | 10.0.1.102 | 2024-02-12 | 78 | 75 | 3 |
| support | 10.0.1.103 | 2024-02-12 | 45 | 42 | 3 |
| developer | 10.0.1.104 | 2024-02-12 | 34 | 30 | 4 |
Enhancing Greenplum Audit Trail with DataSunrise
While Greenplum provides native audit trail capabilities, DataSunrise offers enhanced features for comprehensive audit trail management. The solution provides advanced security monitoring, real-time alerts, and automated compliance reporting. By integrating DataSunrise with Greenplum, organizations can significantly improve their audit trail capabilities while streamlining compliance processes.
1. Advanced Trail Configuration
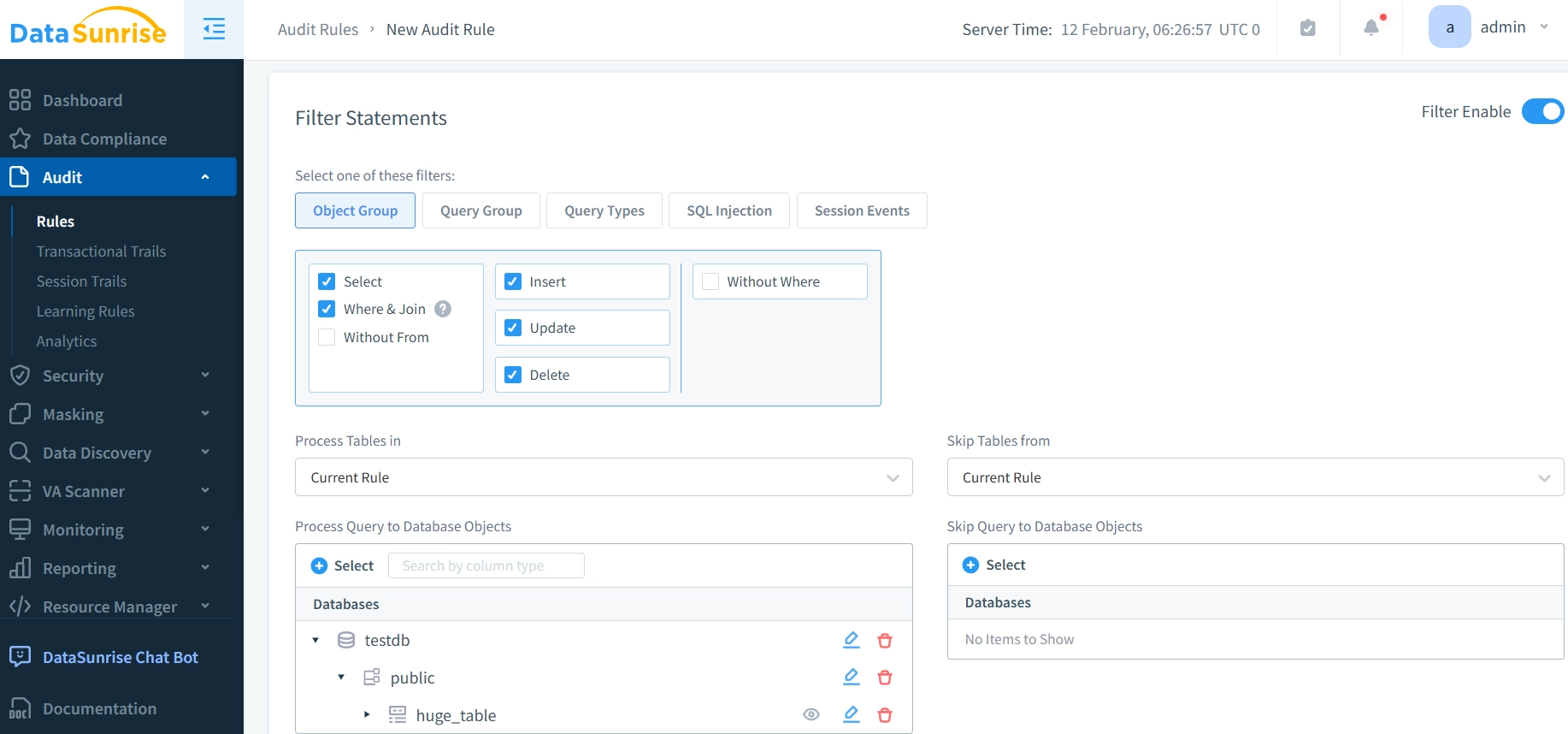
Key capabilities include:
- Customizable audit policies
- Real-time event monitoring
- Automated alert system
- Comprehensive trail collection
2. Centralized Trail Management
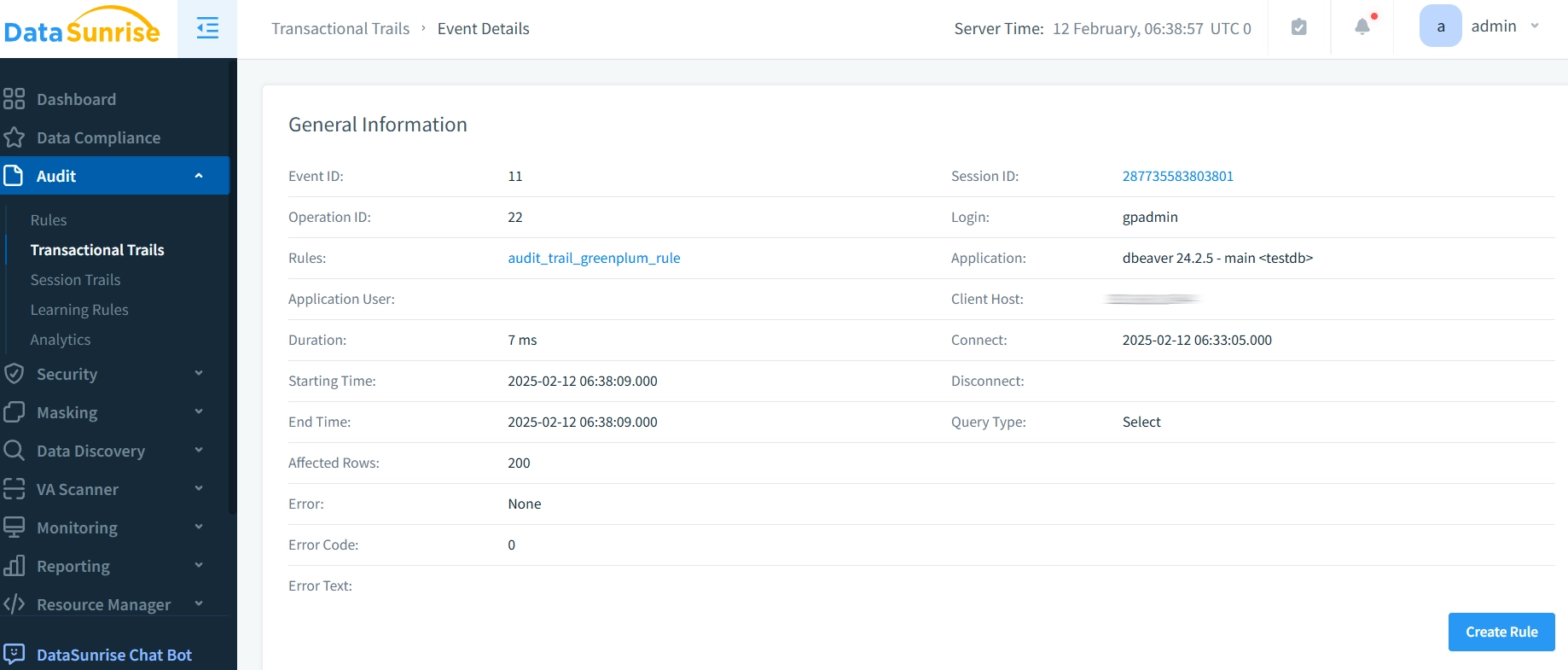
Features:
- Unified trail visualization
- Interactive dashboards
- Custom report generation
- Historical analysis tools
3. Implementation Process
- Install DataSunrise platform
- Configure Greenplum integration
- Define audit policies
- Set up monitoring rules
- Enable automated reporting
Best Practices for Audit Trail Management
Performance Considerations
Effective audit trail management requires careful attention to performance impact. Organizations should implement selective logging strategies that focus on critical operations while maintaining system performance. Regular archival of audit trails, combined with efficient storage management practices, helps ensure optimal database operation without compromising the completeness of audit records.
Security Implementation
Protecting audit trail integrity demands robust security measures. Organizations must implement encryption for sensitive audit data, especially when it contains personally identifiable information. Access controls should be strictly managed, with audit trail access limited to authorized personnel. Regular security reviews help maintain the confidentiality and reliability of audit records.
Third-Party Solutions
While Greenplum’s native audit capabilities provide a solid foundation, third-party solutions like DataSunrise can significantly enhance audit trail management. These tools offer advanced features such as centralized monitoring, automated compliance reporting, and real-time threat detection. Organizations should evaluate their audit requirements and consider implementing specialized solutions that can provide additional layers of security and streamline audit processes.
Compliance Management
Maintaining compliance through audit trails requires systematic approaches to documentation and retention. Organizations should establish clear policies for audit trail retention that align with regulatory requirements. Automated compliance reporting tools should be implemented to streamline audit processes and ensure consistent policy enforcement across the database environment.
Conclusion
Implementing an effective audit trail in Greenplum requires a balanced approach combining native capabilities with advanced security tools. While Greenplum offers robust built-in audit functionality, organizations often benefit from integrating specialized solutions like DataSunrise to enhance their security and compliance capabilities.
Success in audit trail implementation depends on finding the right balance between comprehensive monitoring, system performance, and usability. Regular assessment and updates of audit policies, combined with appropriate tool selection, enable organizations to maintain strong security postures while meeting operational requirements.
Learn more about enhancing your Greenplum audit trail capabilities by visiting DataSunrise’s website and scheduling an online demo.
