
Hive Data Activity History

Introduction
Tracking Hive data activity history is essential for organizations leveraging this data warehouse. Monitoring your data activity history helps identify security threats and ensures compliance with legal and regulatory requirements.
Apache Hive , with its distributed architecture allowing data processing across multiple nodes and remote access points, introduces unique security considerations in today's hybrid work environment. According to IBM's research, data breaches involving remote work access points incur an average additional cost of $173,074, highlighting the critical need for comprehensive database auditing and monitoring in distributed systems.
Hive provides built-in tools that facilitate audit tracking, unauthorized access detection, and regulatory compliance. This guide offers a step-by-step approach to leveraging these capabilities.
Accessing Hive Data Activity History with Native Tools
HiveServer2 logs
HiveServer2 logging is enabled by default and logs operations to /var/log/hive/hiveserver2.log. These logs capture server operations, query execution details, and errors.
HiveServer2 logs are the primary way to track query activity in Hive. They provide a detailed record of every query executed through application clients, along with execution details and errors. These logs are usually turned on by default and can be commonly found in /var/log/hive/hiveserver2.log
Default Logging Content
HiveServer2 logs provide detailed operational information. A typical log entry follows this pattern:
2025-01-22 22:47:47,958 INFO [HiveServer2-Handler-Pool: Thread-2947] parse.ParseDriver: Parsing command: SELECT * from sample_07 LIMIT 7
Key components:
- Timestamp:
2025-01-22 22:47:47,958 - Log Level:
INFO - Thread Info:
[HiveServer2-Handler-Pool: Thread-2947] - Component:
parse.ParseDriver - Message: The actual operation details
Generate Hive Data Activity History with Test Queries
Execute queries to generate audit logs using the following script:
#!/bin/bash
hive -e "
DROP TABLE IF EXISTS audit_test;
CREATE TABLE audit_test (id INT, data STRING);
INSERT INTO audit_test VALUES (1, 'Test data 1');
INSERT INTO audit_test VALUES (2, 'Test data 2');
SELECT * FROM audit_test;
"
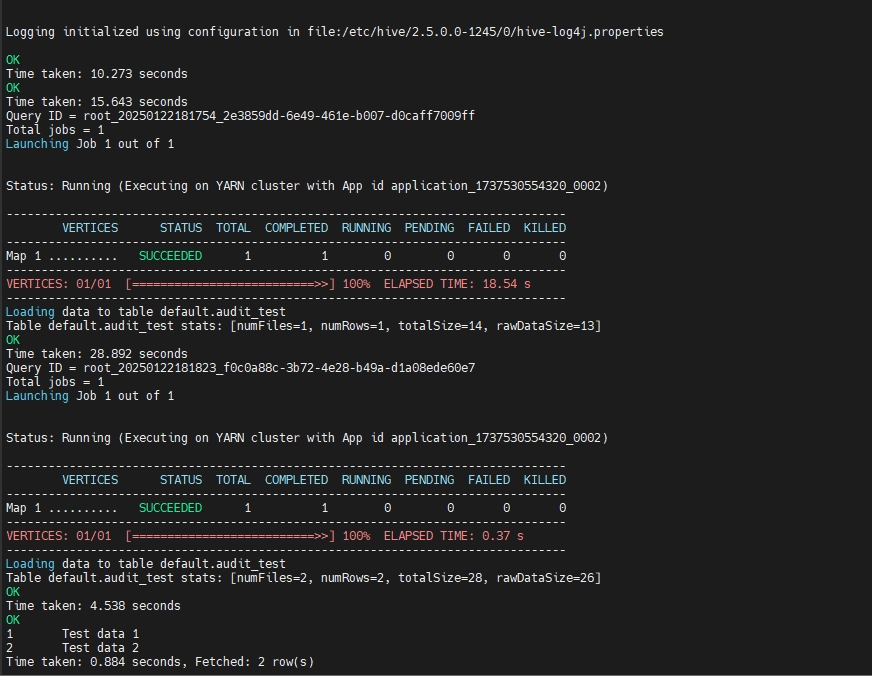
Additionally, you could simulate unauthorized access attempts to verify that logs capture security events.
Analyze Hive Data Activity History with Audit Logs
1. Viewing Logs:
Basic log viewing:
cat /var/log/hive/hiveserver2.log
Useful filtering commands:
# Follow log in real-time
tail -f /var/log/hive/hiveserver2.log
# Search for specific queries
grep "SELECT" /var/log/hive/hiveserver2.log
# View errors
grep "ERROR" /var/log/hive/hiveserver2.log
2. Interpreting Log Entries:
Logs provide details such as timestamps, user activities, and query executions. Analyzing these logs helps detect anomalies and unauthorized access.
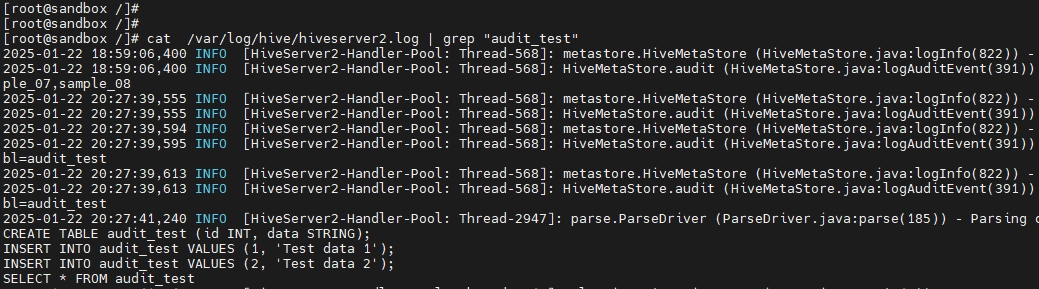
The logs capture various aspects of database activity, including query execution flow, metadata operations, authentication events, lock management, and performance metrics. These logs are most commonly used for debugging query issues and monitoring overall server health, providing valuable insights into system performance and potential operational challenges.
Important Note:
HiveServer2 logs are useful for query tracking and debugging, complementing Metastore, HDFS, and YARN logs, which focus on resource management and execution, as well as Ranger's security-focused audit logs. However, while HiveServer2 logging aids in troubleshooting and basic activity monitoring, it is not intended for comprehensive audit purposes. For more detailed and extensive audit requirements, one should consider solutions like Apache Ranger or other dedicated audit tools.
Extending Hive Data Activity History Logging Precision with Apache Ranger
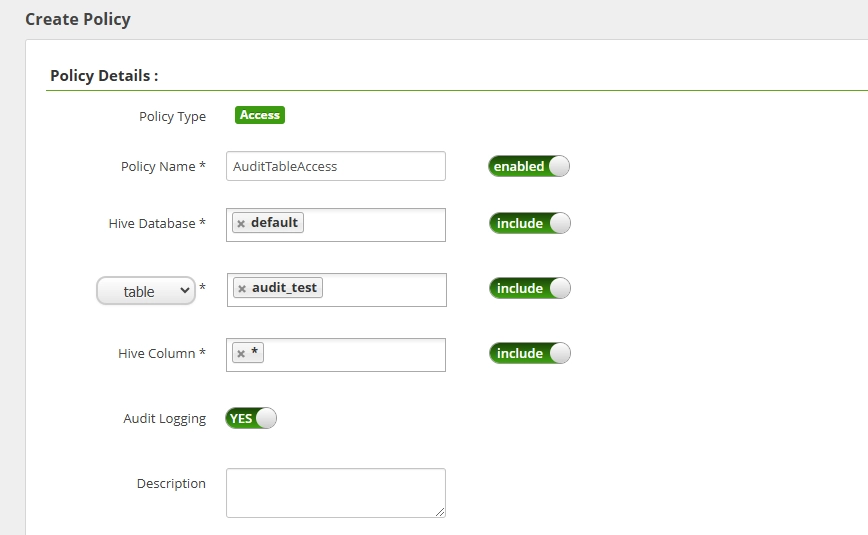
Implement Ranger policies to enable fine-grained audit control. For example:
Through Ranger Admin UI:
- Log in to Ranger Admin (default port 6080)
- Go to Access Manager > Hive policies
- Create policy:
- Policy Name: AuditTableAccess
- Database:
- Table: audit_test
- Audit Logging: Enabled
This policy enables logging for specific users accessing the audit_test table.
Best Practices for Hive Audit Management
Log Rotation: Regularly archive and rotate logs to avoid storage issues.
Securing Logs: Store logs securely to prevent unauthorized modifications.
Optimizing Audit Scope: Focus auditing on critical actions to minimize performance overhead.
DataSunrise: Enhancing Hive Data Activity Tracking
DataSunrise provides a comprehensive solution that overcomes the limitations of Hive's native audit tools. It offers advanced security features tailored to modern data environments.
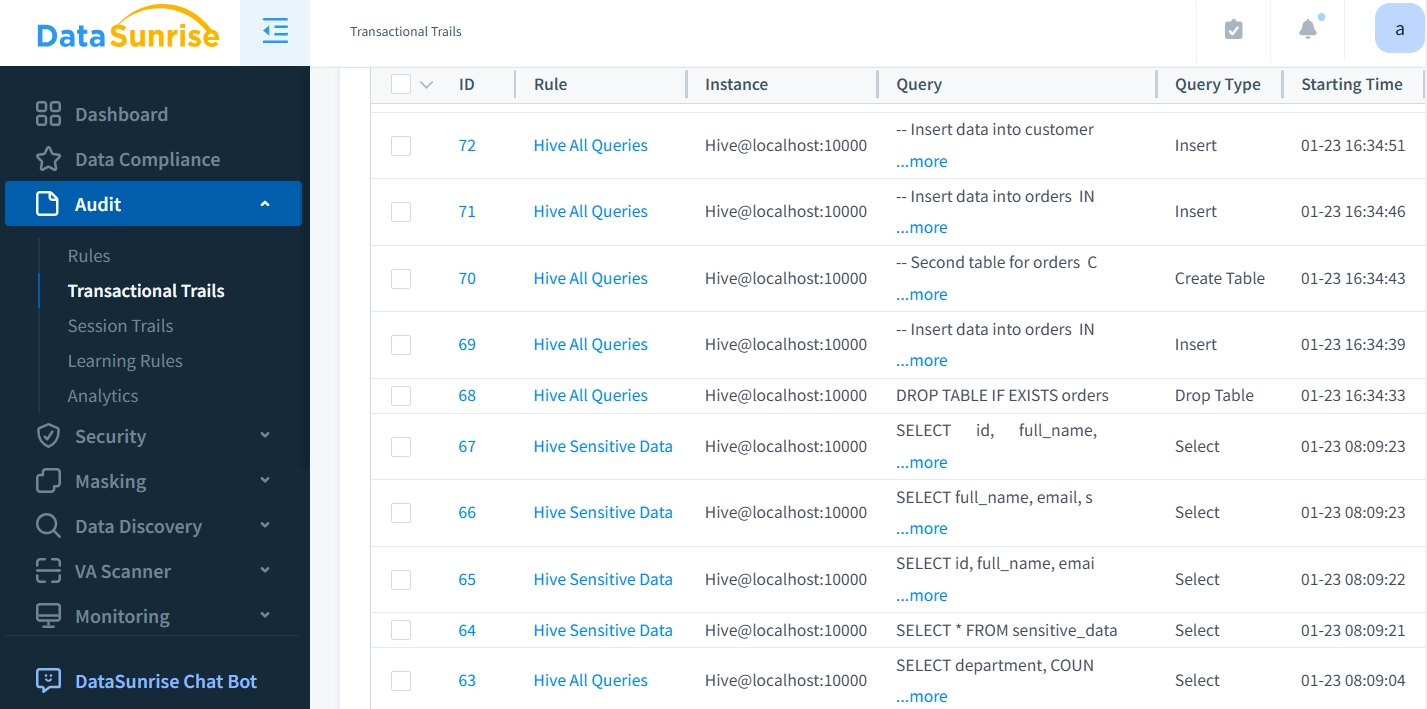
Centralized Management
DataSunrise provides a unified monitoring dashboard for managing multiple data storage systems, including Hive and Impala. With support for over 40 platforms, it simplifies administration and enhances response times to incidents.
Advanced Security Controls
The platform enhances Hive security with security policies and dynamic data masking, protecting sensitive data in real-time based on user roles and access levels.
Compliance Automation
DataSunrise simplifies compliance with frameworks such as SOX, GDPR, HIPAA, and PCI DSS, offering pre-configured monitoring templates and automated reporting.
Additional Features
- Real-Time Alerts: Instant notifications for critical security events.
- Behavior Analytics: AI-driven insights to detect suspicious activities.
- Machine Learning Security: Adaptive security capabilities leveraging AI.
Conclusion
While Hive's native tools provide basic auditing capabilities, modern environments require more advanced solutions. DataSunrise offers robust features that enhance audit trail management.
Looking to improve your Hive data audit process? Try our demo and experience the benefits of comprehensive audit solutions.
