How to Audit Amazon Aurora MySQL?
Auditing your Amazon Aurora MySQL environment is essential for identifying unauthorized activities, tracking changes to sensitive data, and ensuring compliance with regulations like GDPR and PCI DSS. Whether you’re concerned about data breaches or simply want better control over user behavior, setting up a robust audit trail is critical.
Amazon Aurora MySQL supports native auditing through built-in features and can be enhanced further using external tools like DataSunrise. This article focuses on how to natively audit Amazon Aurora MySQL, how to track sensitive data, and how to extend those capabilities with advanced logging and security management tools.
See more about audit logs and how they support compliance and visibility across Aurora environments.

Native Aurora Audit Options
Aurora MySQL auditing is supported through the MySQL audit plugin. You can enable the server_audit plugin in Aurora versions that support it. This native plugin logs queries, connections, and table accesses in an Aurora-specific format.
To enable native auditing:
The audit logs are stored in CloudWatch, which allows integration with other monitoring tools. You can view or export these logs for long-term analysis, and manage thresholds efficiently using database performance tips.
Read more in the official AWS guide to understand compatibility by version.
To filter what gets logged:
This setup allows you to zero in on users accessing sensitive data. To align this with your security strategy, explore what data audits are used for.
Enhancing Visibility with AWS Tools
Audit data becomes more powerful when paired with AWS features. For example, exporting Aurora logs to S3 or processing them via AWS Lambda lets you detect threats in real-time. Aurora also works well with AWS DMS masking transformations for non-production migrations.
Having trouble with visibility? Here’s how to fix it using Aurora logging tips.

If you're relying on SQL-based tools, log querying across information_schema or exports helps automate some detections. However, maintaining consistent rule logic this way becomes tough. Consider learning about audit rules and learning-based policies to streamline the process.
How to Native Audit Amazon Aurora MySQL Securely
For better precision, combine user filtering with secure access practices. Avoid granting superuser rights to application accounts. Instead, leverage Aurora IAM authentication and encrypted connections.
Also consider:
- Enabling TLS between clients and Aurora
- Configuring role-based access control for different teams
- Isolating sensitive workloads using VPC routing
To effectively audit sensitive data, you need full visibility. Identify and label fields like ssn, email, or payment_card. Tools like data discovery help with scanning Aurora tables and tagging risk.
Advanced plugin parameters for auditing are described in the AWS Aurora audit plugin reference.
Using DataSunrise to Audit Amazon Aurora
Native tools work, but scaling audit and compliance across hybrid environments often requires more. DataSunrise offers deep Aurora integration via reverse proxy.
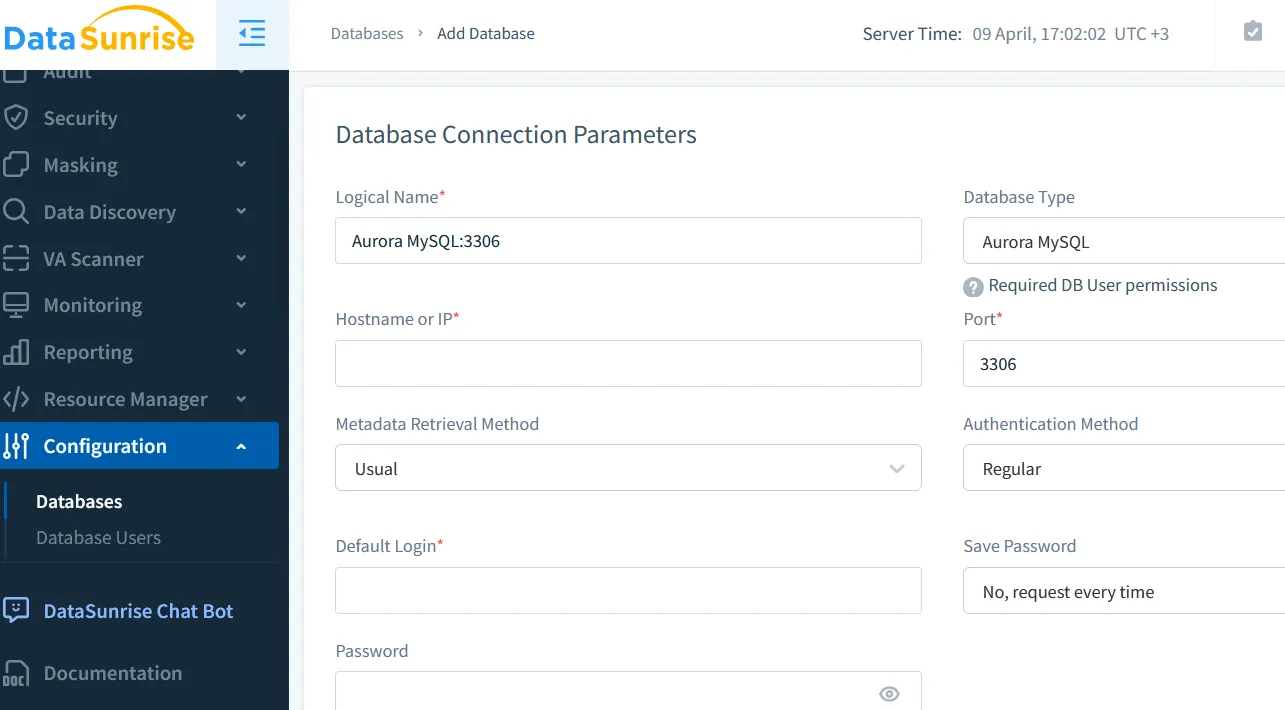
To connect DataSunrise to Aurora:
- Deploy a DataSunrise instance in the same VPC (or one with routing access).
- Use Aurora’s MySQL-compatible endpoint as your data source.
- Activate reverse proxy mode for traffic visibility.
- Enable TLS if required by policy.
More details on this setup are in the DataSunrise deployment guide.
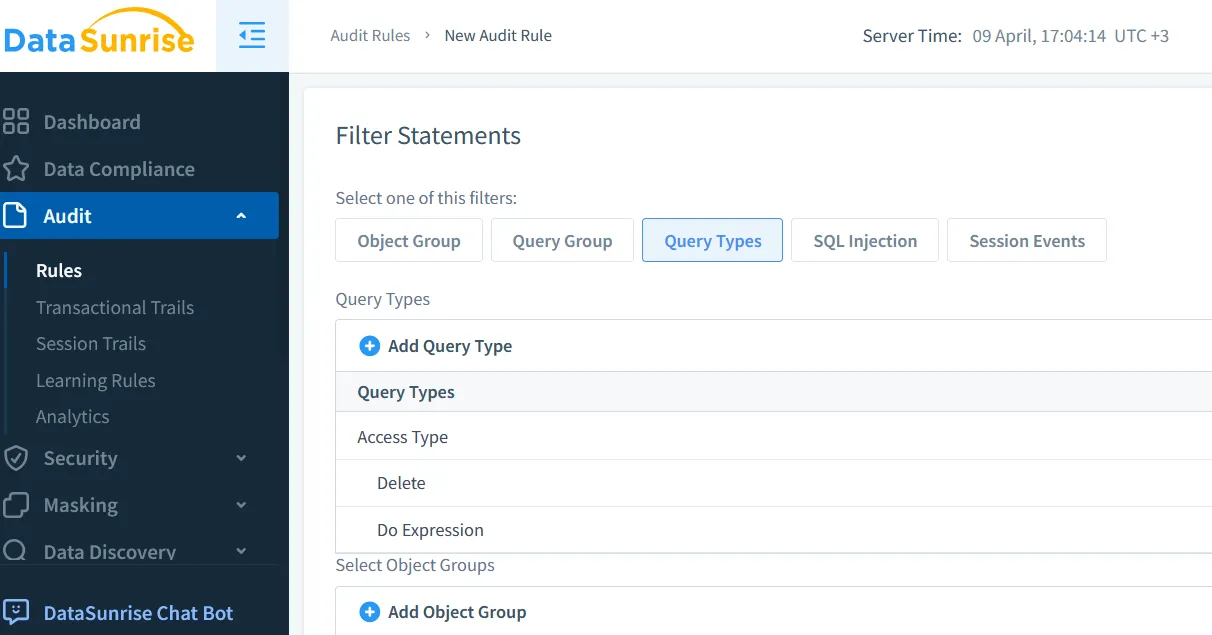
Configuring Logging Rules in DataSunrise
Once connected, set up rules:
- Go to Audit → New Rule in the console
- Choose your Aurora database and specify filters for operation types, tables, or even SQL keywords
- Apply restrictions to users or source IPs
You can tag PII or PHI using built-in templates. DataSunrise supports HIPAA compliance and other standards through pre-defined audit packs.
Managing Logs and Alerts
DataSunrise gives multiple export paths:
Syslog or JSON for SIEM systems
Amazon S3 for archive
Web dashboard for real-time search and filters
Enable alerts via Slack or email and pair it with automated report generation for audit-ready output.
Cross-check trends using activity history to detect behavioral anomalies.
Final Thoughts
Auditing in Amazon Aurora MySQL starts with the built-in plugin but scales best with a flexible platform like DataSunrise. Use native tools for low-level query tracking, then level up with user-aware rules, compliance tagging, and centralized logging.
Consider building your policies around an end-to-end audit trail aligned with regulation and business needs.
If your Aurora setup touches sensitive data or spans environments, don’t stop at logging—embrace smart audit systems with automation. For a practical walkthrough, request a demo of DataSunrise to see its capabilities in action.
Useful Resources
