
How to Audit Aurora PostgreSQL

Introduction
Database auditing has become increasingly critical for organizations using Amazon Aurora PostgreSQL, driven by mounting security concerns and regulatory requirements. According to recent cybersecurity statistics, cyberattacks surged by 30% in Q2 2024 compared to the previous year. This underscores the importance of implementing robust database audit solutions.
That's why, in this article, we'll take a closer look at Aurora PostgreSQL’s built-in audit capabilities, exploring how they help organizations track database activity and maintain compliance. Then, we'll briefly discuss how DataSunrise can elevate these capabilities with advanced security features, real-time monitoring, and automated compliance reporting for a more robust auditing framework.
How to Audit Aurora PostgreSQL with Built-In Capabilities
Aurora PostgreSQL auditing is commonly done through one of these two methods: Database Activity Streams for real-time AWS integration and pgAudit for detailed session logging. Let’s explore how each one works.
Database Activity Streams
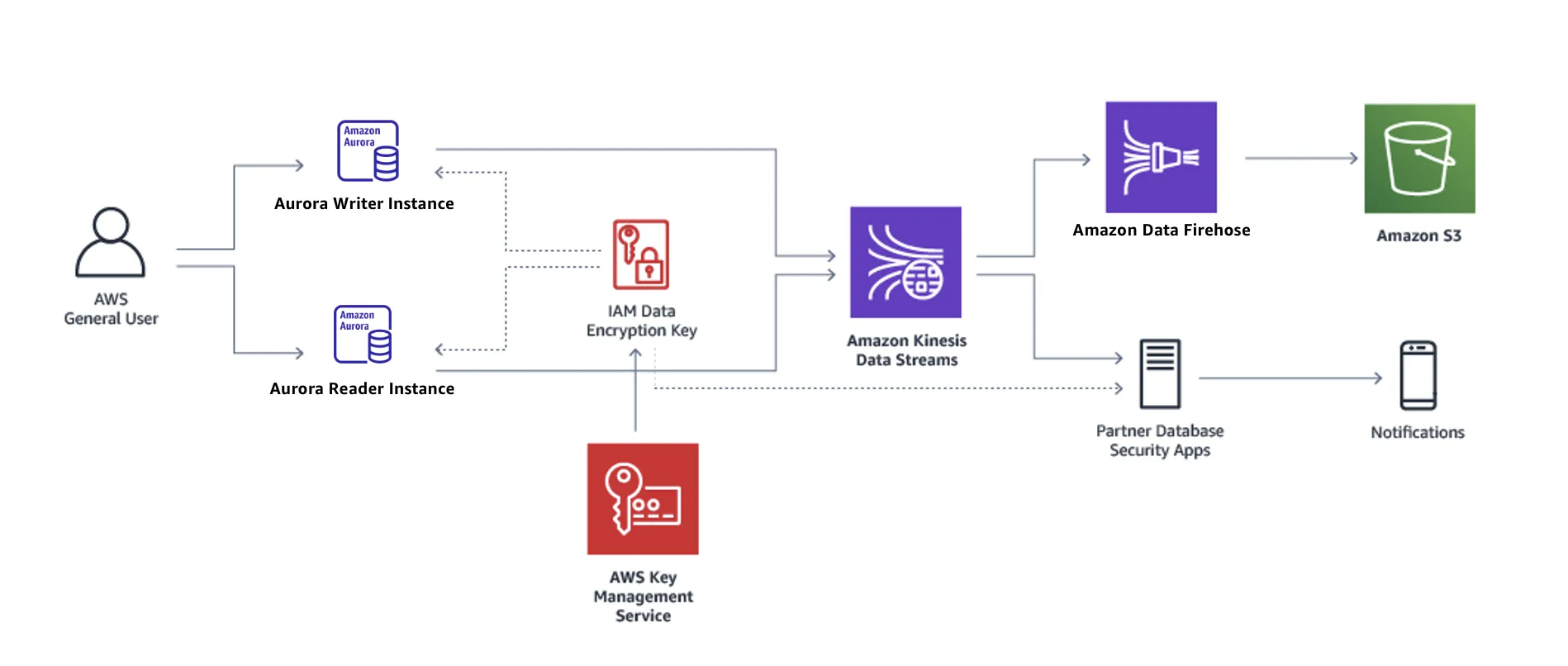
Database Activity Streams is a native AWS feature that provides near real-time monitoring of database activity. It offers:
- Near real-time activity monitoring
- Integration with AWS services
- Encrypted audit data using AWS KMS
- Separation of duties between DBAs and security personnel
Implementation Steps
As detailed in AWS's Database Blog, implementation involves:
- Enable Database Activity Streams
Navigate to RDS > Databases > Your Aurora Cluster > Actions > Start database activity stream Configure Kinesis Data Firehose
- Create a delivery stream
- Set Amazon S3 as the destination
- Configure stream settings
Set Up Monitoring
- Create Lambda functions for processing
- Configure CloudWatch alerts
- Set up SNS notifications
Considerations
- Cost: While the feature itself is free, associated AWS services (Kinesis, Lambda) incur charges
- Performance Impact: Minimal when using asynchronous mode
- Storage: Consider S3 lifecycle policies for log management
pgAudit Extension
Overview
The PostgreSQL Audit Extension (pgAudit) provides detailed session and object audit logging through PostgreSQL's native logging facility. For detailed implementation, refer to AWS's guide on implementing pgAudit.
Implementation Steps
Enable pgAudit in Parameter Group
Configure Audit Logging
-- Enable session logging ALTER DATABASE your_database SET pgaudit.log = 'ALL'; -- Enable object logging ALTER ROLE your_role SET pgaudit.role = 'auditor';Set Up Log Analysis
- Configure CloudWatch Logs
- Set up log parsing and alerting
- Implement log rotation policies
For more details refer to AWS Aurora Documentation
How to Audit Aurora PostgreSQL with DataSunrise
Securing sensitive data in Aurora PostgreSQL requires a robust auditing solution. AWS provides basic auditing tools, but for deeper insights, proactive security, and compliance automation, DataSunrise offers a powerful, easy-to-deploy solution. By following these steps, you can integrate DataSunrise with Aurora PostgreSQL to strengthen database security and maintain compliance effortlessly.
Implementation Steps
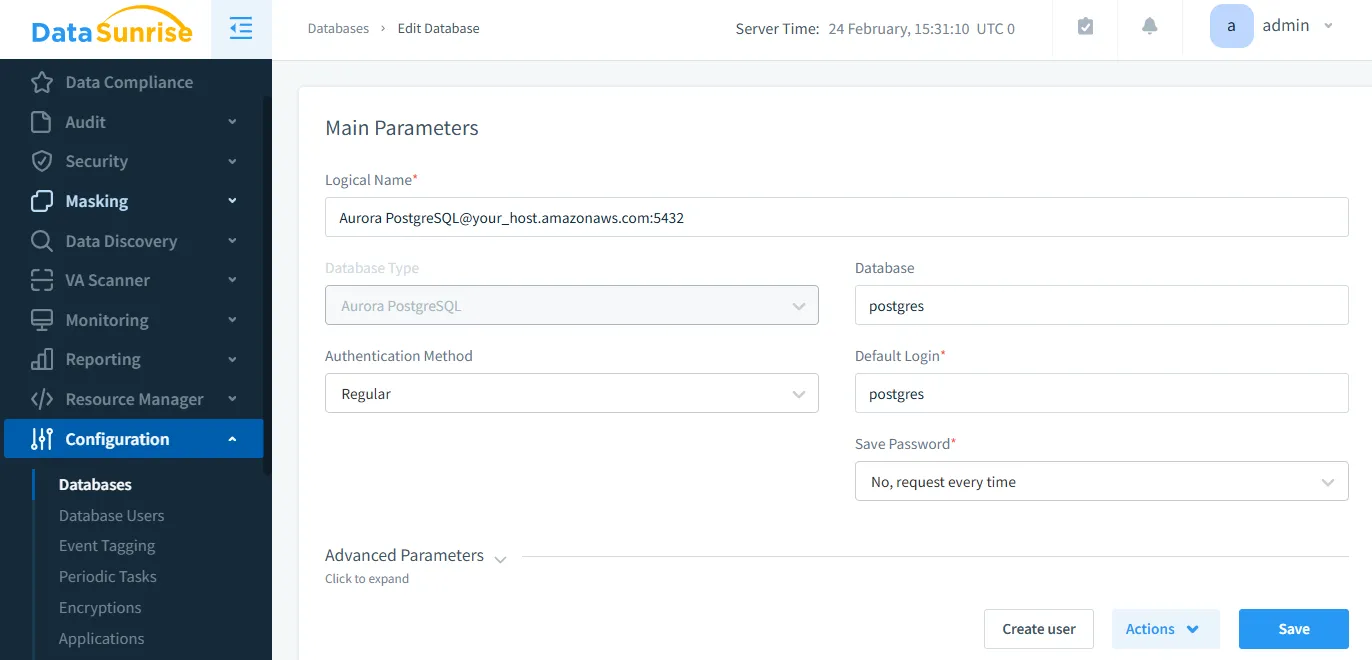
1. Connect to Aurora PostgreSQL Before setting up audit rules, DataSunrise must be connected to your Aurora PostgreSQL instance. This process involves configuring network access, authentication, and permissions to ensure smooth integration.
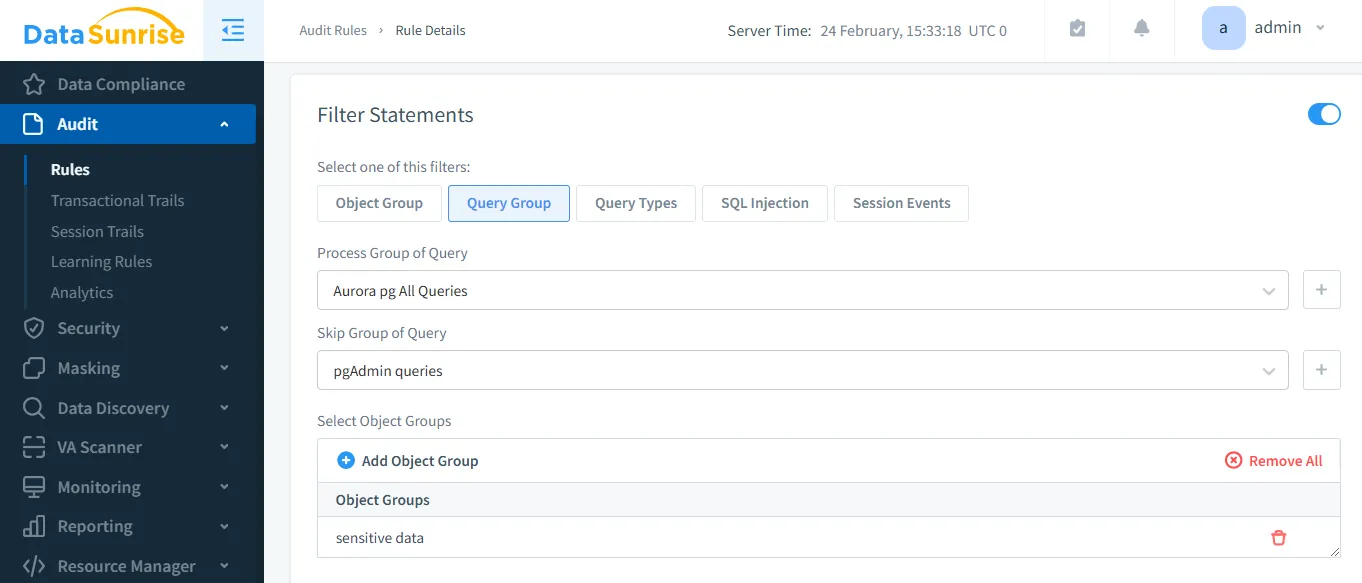
2. Configure Audit Rules Once connected, defining audit rules is key to tracking database activity. DataSunrise allows you to specify which actions to monitor—such as queries, logins, schema changes, or sensitive data access—helping you detect anomalies and enforce security policies.
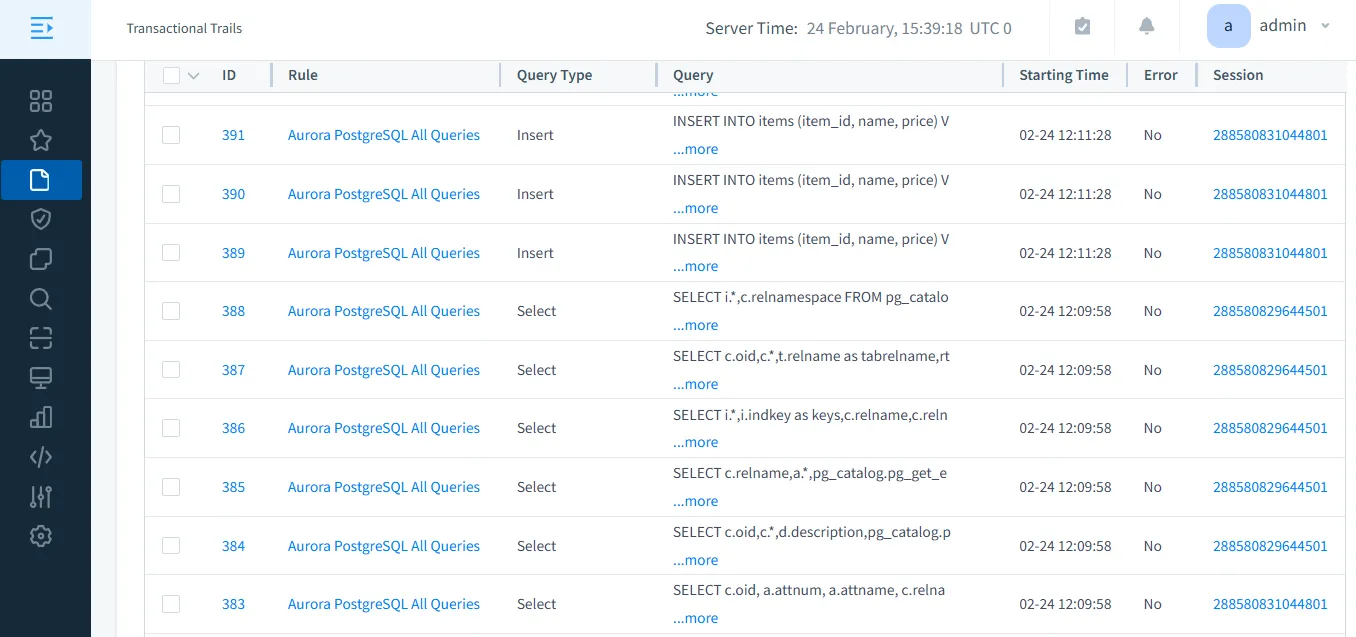
3. View Transactional Trails in Real-Time With audit rules in place, DataSunrise captures and displays database activities in real-time. This enables security teams to monitor transactions as they occur, detect suspicious behavior, and respond to threats proactively.
For detailed setup instructions, visit DataSunrise's Audit Guide.
Why Choose DataSunrise for Aurora PostgreSQL?
DataSunrise enhances Aurora PostgreSQL’s security with advanced auditing, real-time monitoring, and compliance automation. Here’s why it stands out:
- Seamless Integration – Deploy DataSunrise effortlessly alongside Aurora PostgreSQL with flexible deployment options tailored to your infrastructure.
- Customizable Audit Rules – Define granular audit policies to track specific database events, ensuring precise security and compliance coverage.
- Pre-configured Compliance Reports – Generate audit-ready reports aligned with industry standards like SOX, PCI DSS, and HIPAA.
- Dynamic Data Masking – Protect sensitive information by masking data dynamically, ensuring security without impacting performance.
- Sensitive Data Discovery – Identify and classify sensitive data across your Aurora PostgreSQL environment for improved governance.
The platform also employs advanced analytics and user behavior analysis, which helps DataSunrise detect anomalies, prevent unauthorized access, and provide actionable insights from audit logs.
To explore more, visit the DataSunrise Documentation.
Conclusion
For organizations using Aurora PostgreSQL to handle sensitive data, strong auditing is essential. While AWS offers native tools, integrating DataSunrise enhances visibility, security, and compliance.
DataSunrise extends Aurora PostgreSQL’s audit capabilities with advanced analytics and proactive protection. Strengthen your security with our flexible deployment options or request a demo to see it in action.
