How to Audit Azure SQL Database
Implementing robust auditing for Azure SQL Database is essential for security and compliance. According to recent cybersecurity statistics, organizations with comprehensive database activity monitoring detect potential breaches up to 80% faster and reduce compliance costs significantly.
This guide covers implementing Azure SQL Database auditing using both native capabilities and enhanced solutions for comprehensive security monitoring.
Native Azure SQL Database Auditing Capabilities
Azure SQL Database includes built-in auditing functionality to track database activities, user actions, and security events:
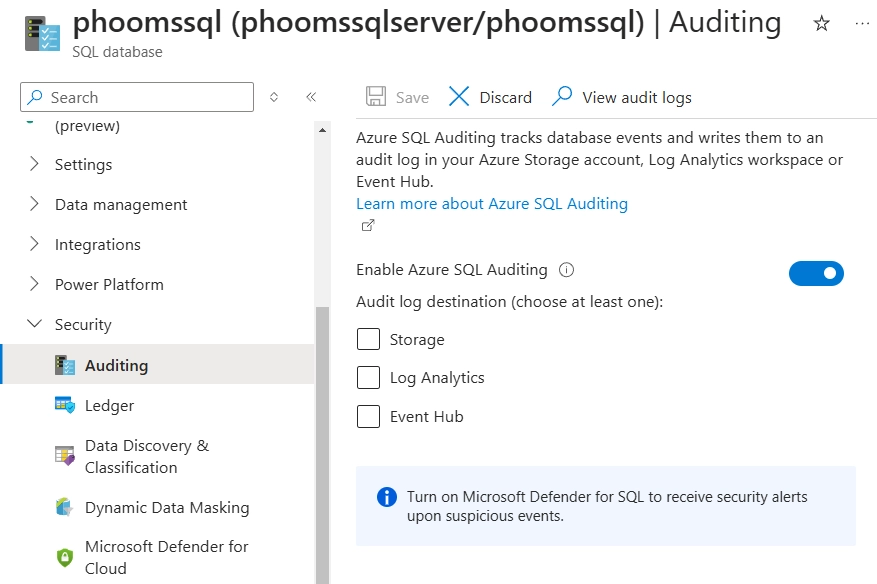
1. Enabling Basic Auditing
To enable auditing through the Azure Portal, navigate to your Azure SQL server, select “Auditing” under the Security section, toggle “Enable Azure SQL Database auditing” to ON, choose your storage destination, configure the audit log retention period, and save your settings.
# Enable auditing for an Azure SQL database Set-AzSqlDatabaseAudit -ResourceGroupName "DataServices-RG" ` -ServerName "enterprise-sql-east" ` -DatabaseName "FinancialData" ` -State Enabled ` -StorageAccountName "auditlogs" ` -RetentionInDays 90 ` -AuditActionGroup @( "SUCCESSFUL_DATABASE_AUTHENTICATION_GROUP", "FAILED_DATABASE_AUTHENTICATION_GROUP", "DATABASE_OPERATION_GROUP" )
Example output:
ResourceGroupName : DataServices-RG
ServerName : enterprise-sql-east
DatabaseName : FinancialData
AuditState : Enabled
StorageAccountName: auditlogs
RetentionInDays : 90
AuditActionGroups : {SUCCESSFUL_DATABASE_AUTHENTICATION_GROUP, FAILED_DATABASE_AUTHENTICATION_GROUP, DATABASE_OPERATION_GROUP}
2. Testing with Sample Queries
Run these operations to generate audit logs:
-- Create a test table
CREATE TABLE audit_test (
id INT PRIMARY KEY,
customer_name VARCHAR(100),
account_number VARCHAR(20),
balance DECIMAL(10,2)
);
-- Insert sample data
INSERT INTO audit_test VALUES (1, 'John Smith', 'ACT-10001', 5000.00);
-- Query sensitive data
SELECT * FROM audit_test WHERE balance > 4000;
-- Example output: 1, John Smith, ACT-10001, 5000.00
-- Update customer information
UPDATE audit_test SET balance = 5200.00 WHERE id = 1;
-- Example output: 1 row(s) affected
-- Delete a record
DELETE FROM audit_test WHERE id = 1;
-- Example output: 1 row(s) affected
3. Reviewing Audit Logs
Access logs through the Azure Portal by navigating to your SQL server/database, selecting “Auditing” and clicking “View audit logs”. Alternatively, use Log Analytics with KQL queries to analyze audit data or Azure Storage Explorer to browse log files for offline analysis.
Example of a typical audit log entry:
{
"event_time": "2025-02-18T15:42:36Z",
"action_id": "SELECT",
"server_principal_name": "finance_analyst@contoso.com",
"database_name": "FinancialData",
"object_name": "audit_test",
"statement": "SELECT * FROM audit_test WHERE balance > 4000",
"client_ip": "40.112.128.75"
}
Enhanced Auditing with DataSunrise
While native auditing provides essential monitoring, DataSunrise enhances Azure SQL auditing with advanced features:
Key Advantages of DataSunrise
- Streamlined Setup: Intuitive interface with flexible deployment options for quick implementation.
- Granular Audit Rules: Customizable audit policies based on users, applications, SQL commands, query content, and access patterns.
- Real-Time Threat Detection: Features like behavioral analytics and real-time alerts identify suspicious activities immediately.
- Compliance Automation: Pre-configured templates for GDPR, HIPAA, PCI DSS, and SOX with the Database Regulatory Compliance Manager.
- Unified Monitoring: Centralized database monitoring across multiple database platforms.
Implementing DataSunrise for Azure SQL
1. Connect to Azure SQL Database:
Connect DataSunrise to your Azure SQL instance through the administrative interface.
2. Create Audit Rules:
Define which database objects and actions to monitor using Audit Rules.
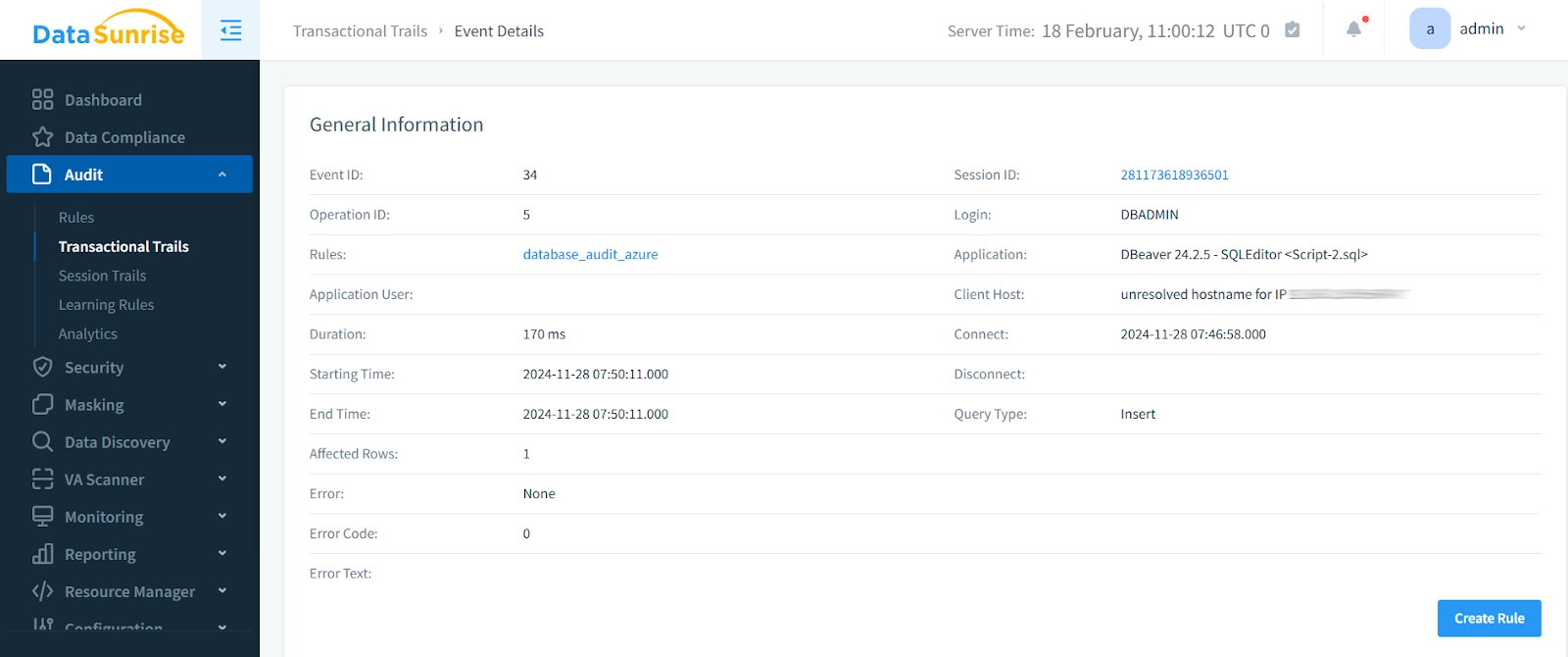
3. Monitor Activities:
View detailed audit trails through the interactive dashboard.
4. Generate Reports:
Create automated reports for regulatory compliance with pre-configured templates.
Best Practices for Azure SQL Auditing
1. Audit Scope Optimization
- Focus detailed auditing on sensitive tables
- Implement column-level auditing for PII or regulated information
2. Storage and Retention Planning
- Configure retention periods based on compliance requirements
- Implement log rotation for cost-effective storage
3. Alert Configuration
- Set up real-time alerts for critical security events
- Configure notification thresholds to prevent alert fatigue
4. Regular Audit Review
- Establish routine audit goals procedures
- Implement automated scanning for suspicious patterns
5. Enhanced Audit Solutions
- Implement DataSunrise for comprehensive audit trail capabilities
- Leverage advanced analytics and automated compliance reporting
6. Integration with Security Operations
- Forward critical audit events to your SIEM system
- Correlate database audit logs with other security monitoring
Business Benefits
| Benefit | Description |
|---|---|
| Enhanced Security | Detect unauthorized access before security incidents escalate |
| Streamlined Compliance | Simplify regulatory adherence with automated reporting |
| Improved Visibility | Gain insights into database usage and security risks |
| Incident Investigation | Maintain detailed forensic evidence for security incidents |
| Risk Mitigation | Address vulnerabilities before exploitation by malicious actors |
Conclusion
As organizations rely on Azure SQL Database for critical applications, robust auditing is essential. While native features provide a foundation, DataSunrise delivers comprehensive security with advanced auditing, real-time monitoring, and automated compliance reporting.
To enhance your Azure SQL security with advanced auditing, schedule an online demo with DataSunrise today.
