
How to Audit Greenplum

Maintaining comprehensive audit trails is crucial for today’s database security and compliance. As organizations face increasingly sophisticated cyber threats, implementing proper audit mechanisms in Greenplum Database environments is essential for protecting sensitive data and maintaining regulatory compliance.
For businesses managing sensitive information, Greenplum Database offers systematic tracking and verification of database activities through its native auditing features. This methodical approach supports the implementation of essential data security controls and compliance measures.
Understanding Greenplum Data Audit Trail
Greenplum’s audit system consists of several interconnected components:
- Server Log Files: Each database instance maintains its own server log containing detailed activity records.
- Audit Catalogs: System tables storing audit-related metadata.
- Segment-Level Logging: Distributed audit capture across all segments.
- Coordinator Node Aggregation: Centralized collection of audit data.
How to Audit Greenplum with Native Features
Basic Configuration
To enable comprehensive audit trailing in Greenplum, apply these essential settings:
-- Enable basic audit logging ALTER SYSTEM SET logging_collector = on; ALTER SYSTEM SET log_destination = 'csvlog'; -- Configure detailed logging parameters ALTER SYSTEM SET log_statement = 'all'; ALTER SYSTEM SET log_min_duration_statement = 1000; ALTER SYSTEM SET log_connections = on; ALTER SYSTEM SET log_disconnections = on;
Advanced Audit Configuration
For enhanced audit capabilities, implement these additional settings:
-- Enable extended logging details ALTER SYSTEM SET log_error_verbosity = 'verbose'; ALTER SYSTEM SET log_line_prefix = '%t [%p]: [%l-1] user=%u,db=%d,app=%a,client=%h '; -- Configure audit file management ALTER SYSTEM SET log_rotation_age = '1d'; ALTER SYSTEM SET log_rotation_size = '100MB'; ALTER SYSTEM SET log_truncate_on_rotation = on;
Practical Implementation Examples
Monitoring Data Access Patterns
Use the following query to monitor data access patterns:
SELECT
usename,
date_trunc('hour', query_start) as access_time,
count(*) as access_count,
string_agg(DISTINCT client_addr::text, ', ') as source_ips
FROM
pg_stat_activity
WHERE
datname = 'testdb'
AND query ILIKE '%public.clients%'
AND query_start >= current_timestamp - interval '24 hours'
GROUP BY
usename,
date_trunc('hour', query_start)
ORDER BY
access_time DESC;
Example output:
| usename | access_time | access_count | source_ips |
|---|---|---|---|
| admin | 2024-02-12 15:00:00 | 45 | 192.168.1.100, 192.168.1.101 |
| analyst | 2024-02-12 14:00:00 | 28 | 192.168.1.102 |
| etl_user | 2024-02-12 14:00:00 | 15 | 192.168.1.103 |
| support | 2024-02-12 13:00:00 | 8 | 192.168.1.104 |
Tracking Schema Modifications
To track schema modifications, use this query:
SELECT
event_timestamp,
usename,
command_tag,
object_type,
object_identity,
command
FROM
pg_audit_log
WHERE
command_tag IN ('ALTER TABLE', 'CREATE TABLE', 'DROP TABLE')
AND object_identity LIKE '%public.clients%'
ORDER BY
event_timestamp DESC;
Example output:
| event_timestamp | usename | command_tag | object_type | object_identity | command |
|---|---|---|---|---|---|
| 2024-02-12 15:30:00 | admin | ALTER TABLE | TABLE | public.clients | ALTER TABLE public.clients ADD COLUMN email VARCHAR(255) |
| 2024-02-12 14:45:00 | admin | ALTER TABLE | TABLE | public.clients | ALTER TABLE public.clients ADD PRIMARY KEY (id) |
| 2024-02-12 14:00:00 | etl_user | CREATE TABLE | TABLE | public.clients | CREATE TABLE public.clients (id serial, …) |
Monitoring Sensitive Data Access
To monitor sensitive data access, use the following query:
SELECT
a.usename,
date_trunc('minute', a.query_start) as operation_time,
count(*) as access_count,
string_agg(DISTINCT substring(a.query, 1, 50), '; ') as query_samples
FROM
pg_stat_activity a
WHERE
a.datname = 'testdb'
AND a.query ILIKE '%public.clients%'
AND (
a.query ILIKE '%birth_date%'
OR a.query ILIKE '%sex%'
)
GROUP BY
a.usename,
date_trunc('minute', a.query_start)
ORDER BY
operation_time DESC;
Example output:
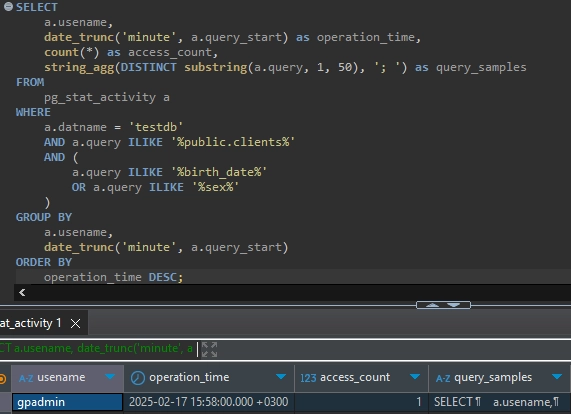
DataSunrise: Enhancing Greenplum Data Audit Trail
While Greenplum’s native audit trail capabilities provide a solid foundation, organizations with stringent security and compliance requirements can significantly enhance their auditing processes with DataSunrise’s advanced audit trail solutions.
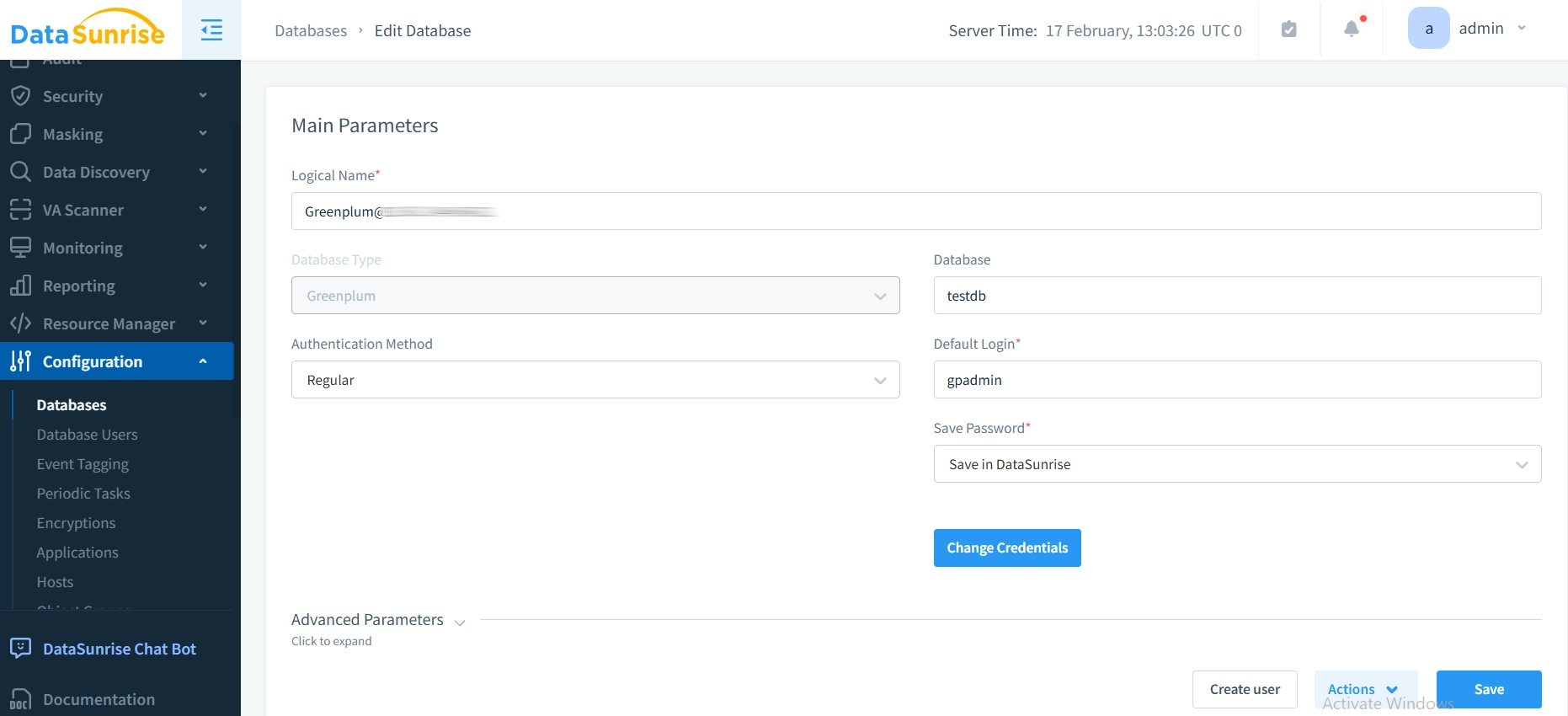
Step 1: Setting Up Integration
To connect DataSunrise to your Greenplum database, simply provide the necessary connection details via the user-friendly setup interface. DataSunrise will automatically configure the monitoring channels to begin collecting audit trail data.
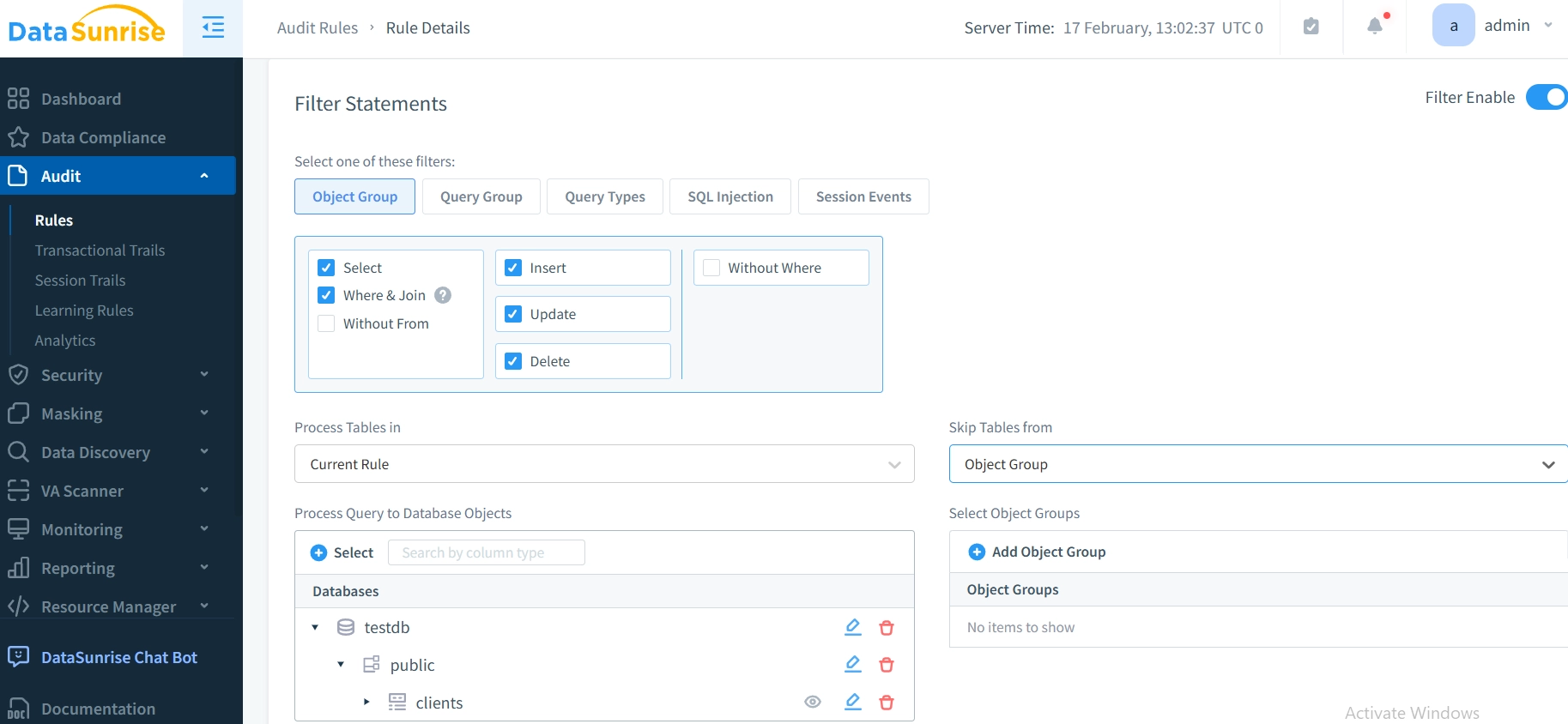
Step 2: Creating Audit Rules for Greenplum Data Audit Trail
Through DataSunrise’s interface, define which database objects and operations to monitor. Customize audit rules for various activities and security events, ensuring your Greenplum database is fully monitored.
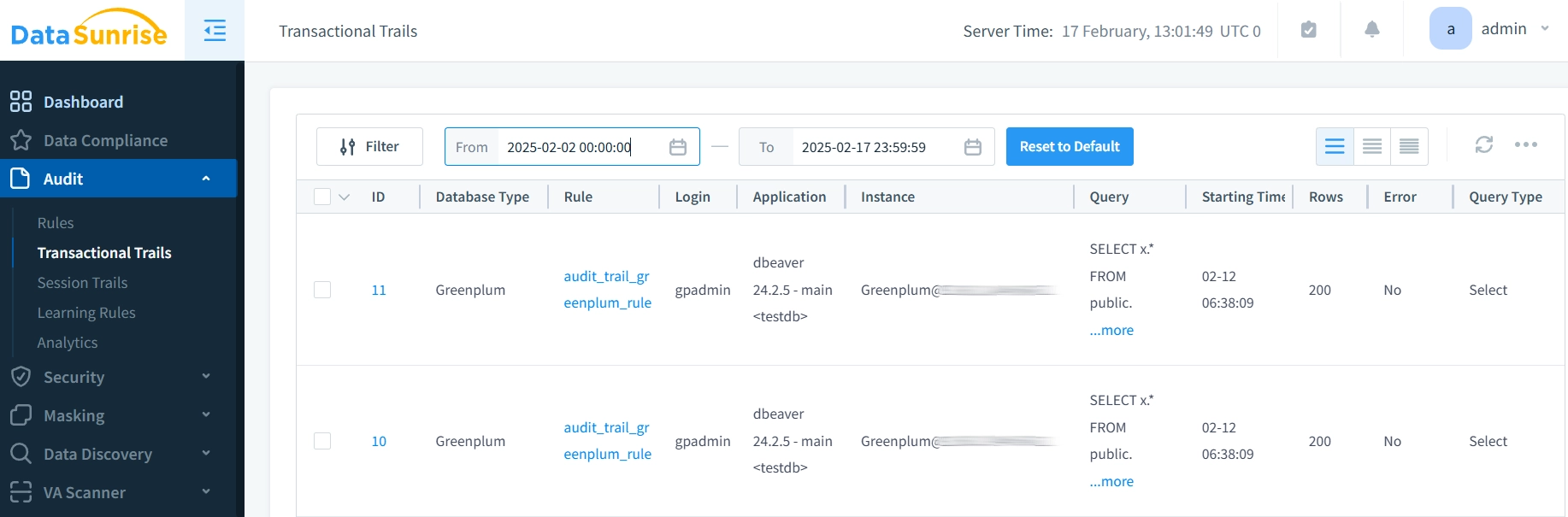
Step 3: Monitoring Activities
Once integrated, you can access the real-time dashboard to monitor all database operations. This includes detailed logs of user actions, queries, and system events. Utilize DataSunrise’s powerful analytics engine to identify abnormal behavior and potential security threats.
Key Benefits of DataSunrise Greenplum Data Audit Trail Integration:
- Database Activity Monitoring: Continuous tracking of all database activities
- Database Security: Complete protection against unauthorized access and potential threats
- Role-Based Access Control: Fine-grained user permission and access management
- Real-Time Notifications: Immediate alerts for suspicious events and security breaches
- Compliance Manager: Simplified compliance tracking and reporting
- User Behavior Analysis: Advanced detection of anomalous user behavior
Conclusion
While Greenplum offers basic audit trail features, organizations aiming for comprehensive visibility and control over their database security should integrate DataSunrise’s robust auditing capabilities. DataSunrise’s solutions provide enhanced security and compliance features, ensuring complete coverage for your Greenplum database environment.
Want to see the solution in action? Schedule a demo to discover how DataSunrise can elevate your Greenplum database security and compliance efforts.
