
How to Audit Hydra

Introduction
In today's data-driven landscape, implementing robust data audit trails is crucial for database security, compliance, and operational oversight. Hydra, an innovative open-source database that combines PostgreSQL's transactional capabilities with DuckDB's analytical prowess, offers various methods for tracking and monitoring data activities.
While Hydra provides native Postgres auditing capabilities, organizations often need comprehensive database activity monitoring solutions to meet regulatory requirements and security standards. This article explores how to effectively implement database security in Hydra environments, covering both built-in features and enhanced monitoring approaches for maintaining a robust audit trail.
Hydra’s Native Audit Capabilities
As a PostgreSQL-based database, Hydra supports fundamental audit logging through PostgreSQL’s built-in logging features and extensions. While it doesn’t offer a comprehensive, plug-and-play auditing solution, users can implement effective tracking mechanisms using various tools.
Key Audit Logging Methods
PostgreSQL Standard Logging
- Logs database activity via
postgresql.confsettings - Records query execution, errors, and connection attempts
- Can be customized for different verbosity levels
- Logs database activity via
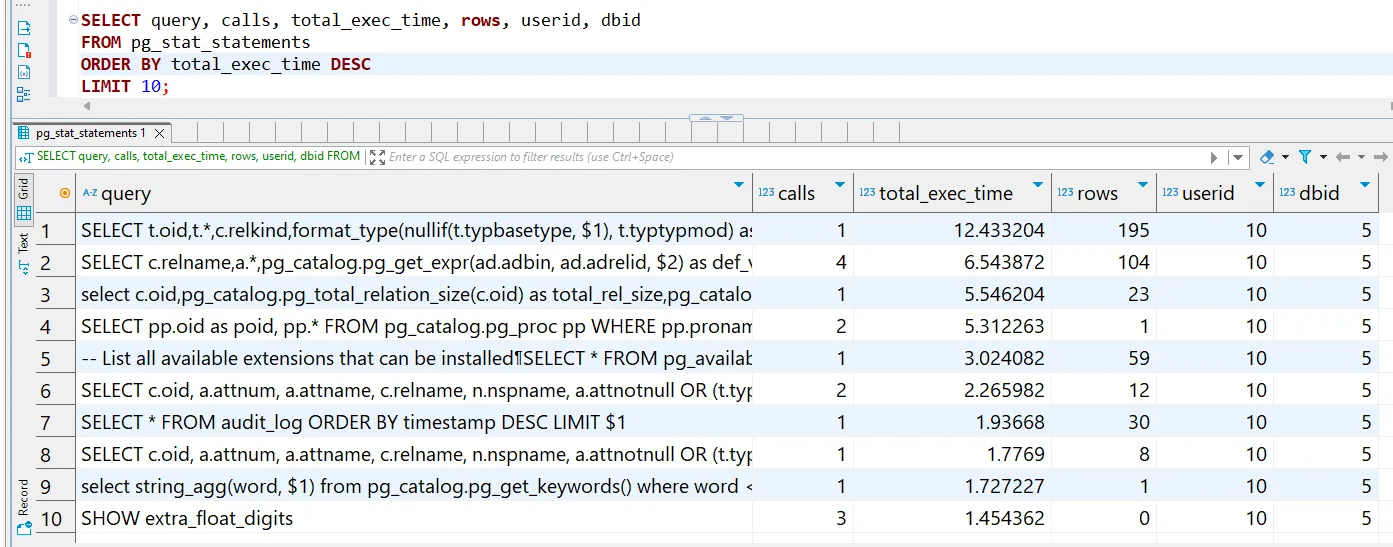
- pg_stat_statements Extension
- Captures query execution statistics
- Useful for tracking frequently run or resource-heavy queries
- Provides a basic level of audit trail functionality
- pg_audit Extension
- Enables detailed activity logging
- Supports fine-grained tracking of database transactions
- Recommended for organizations needing compliance-level audit logs

Best Practices for Hydra Audit
- Configure PostgreSQL’s native logging for basic activity tracking.
- Enable
pg_stat_statementsto monitor query performance and detect anomalies. - Implement
pg_auditfor a structured and detailed audit trail. - Integrate with external monitoring tools for enhanced log analysis.
Limitations of Hydra’s Built-In Audit Features
- No dedicated, built-in advanced auditing framework.
- Requires additional setup and configuration.
- May introduce performance overhead when logging is extensive.
- Lacks automated security alerts and compliance reporting.
For organizations with strict security and compliance needs, these native options may not be sufficient.
How to Audit Hydra with DataSunrise
To achieve comprehensive audit logging and proactive security monitoring, integrating DataSunrise with Hydra offers significant advantages.
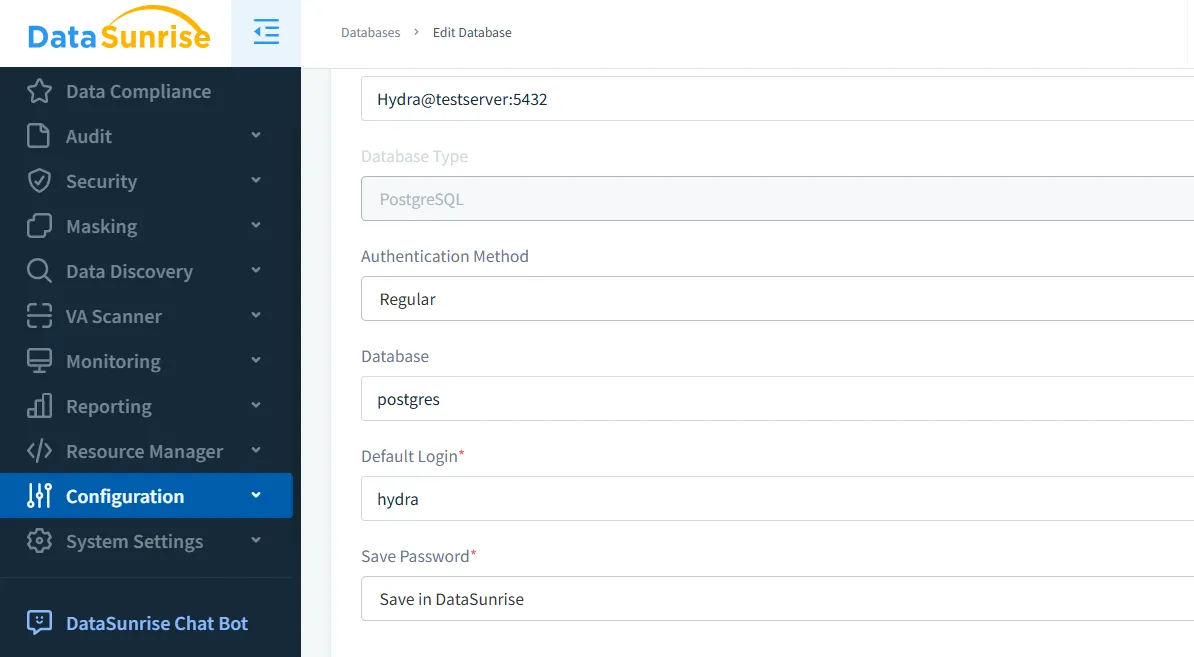
Step 1: Setting Up DataSunrise for Hydra Auditing
Connecting Hydra to DataSunrise is straightforward. Provide the necessary database credentials, and DataSunrise will automatically establish monitoring channels to track all relevant database activities.
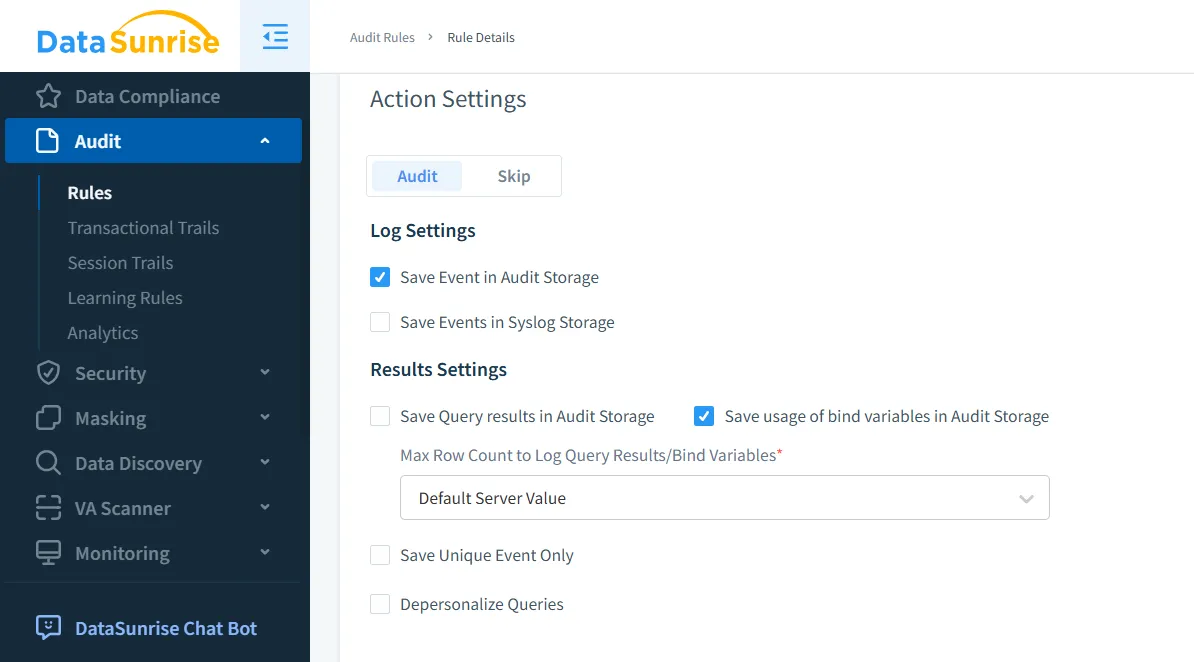
Step 2: Defining Audit Rules
DataSunrise enables you to create tailored audit policies for Hydra. You can specify which tables, queries, or user activities need monitoring and define alerts for potential security violations.
Step 3: Real-Time Monitoring and Analysis
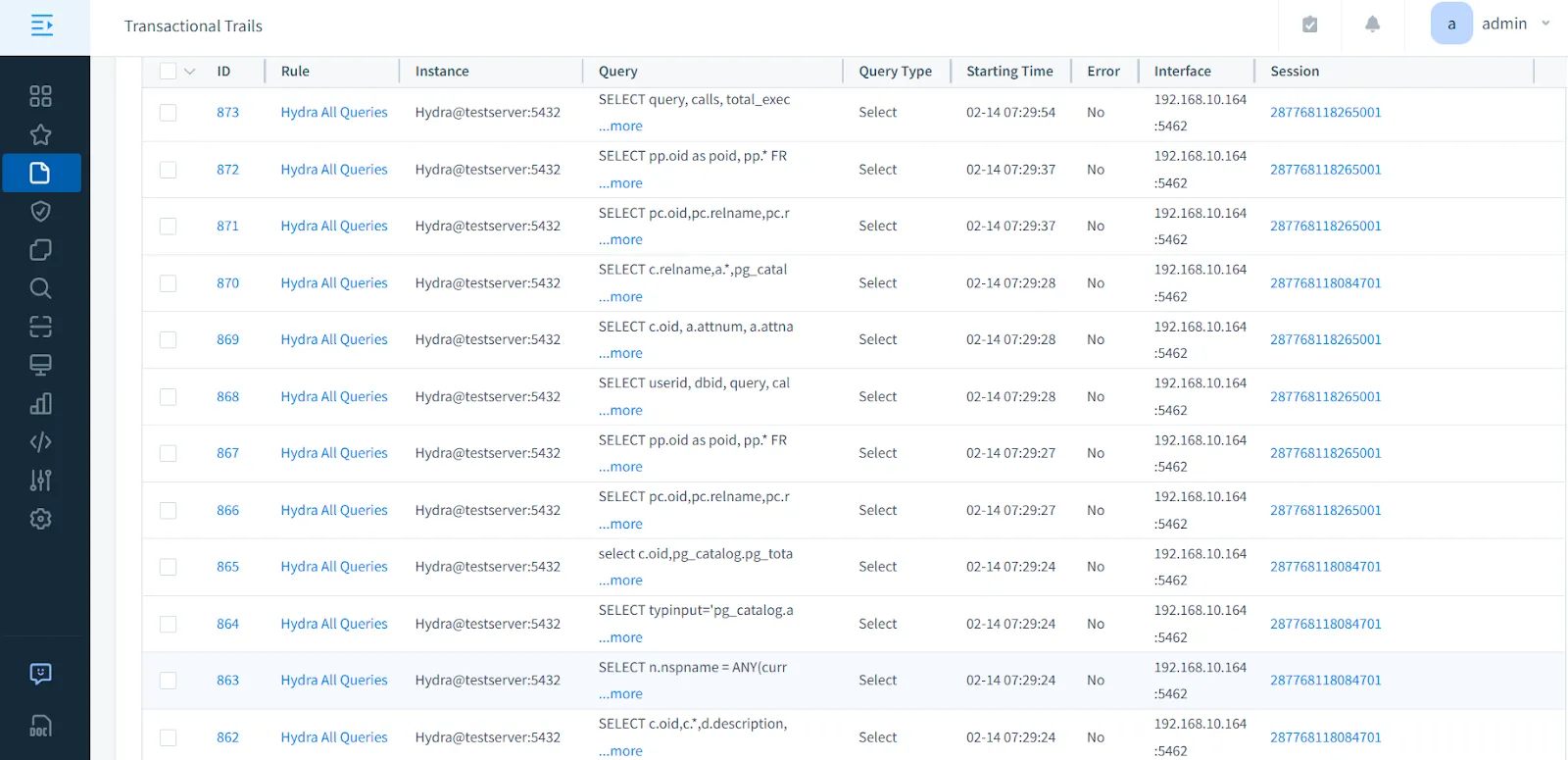
With DataSunrise’s dashboard, you gain real-time insights into database operations. You can analyze query execution trends, user behavior, and system events to detect potential threats.
Advantages of Using DataSunrise to Audit Hydra
Database Activity Monitoring Provides comprehensive visibility into all database operations in real-time, including SQL queries, schema changes, and user sessions. This continuous monitoring helps organizations maintain a complete audit trail of who accessed what data, when, and how. The system captures both successful and failed attempts, making it easier to identify potential security breaches or performance issues.
Database Security Goes beyond basic access controls by implementing multiple layers of security. This includes SQL injection prevention, firewall capabilities, and advanced threat detection. The system actively monitors for suspicious patterns and can automatically block potentially harmful operations before they impact your data.
Real-Time Alerts Delivers immediate notifications about suspicious or unusual database activities through multiple channels including email, Slack, and custom webhooks. These alerts can be customized based on severity levels and specific trigger conditions, enabling rapid response to potential security incidents or compliance violations.
Compliance Automation Streamlines the process of meeting regulatory requirements by automatically generating required audit reports and compliance documentation. Built-in templates and workflows support various compliance frameworks, reducing the manual effort needed for audit preparation and reporting while ensuring consistency in compliance processes.
User Behavior Analytics Employs advanced analytics to establish baseline user behavior patterns and identify anomalies that might indicate security threats. The system learns from historical data to detect unusual access patterns, excessive data retrieval, or other suspicious activities that could signal potential data breaches or misuse.
Each of these features works together to create a comprehensive audit and security framework for Hydra databases, ensuring both protection of sensitive data and compliance with regulatory requirements.
Conclusion
Hydra’s built-in logging tools offer a starting point for auditing, but for organizations needing full-scale compliance and security monitoring, a more advanced solution is required. DataSunrise significantly enhances Hydra’s auditing capabilities, providing real-time insights, threat detection, and regulatory compliance support.
Looking to improve your database security? Schedule a demo to explore how DataSunrise can optimize your Hydra auditing strategy.
