How to Audit ScyllaDB?
Introduction
In the era of big data and distributed systems, how to audit ScyllaDB has become a critical question for organizations aiming to ensure data security, compliance, and operational transparency. ScyllaDB, a high-performance NoSQL database compatible with Apache Cassandra, is widely used for its scalability and low-latency capabilities. However, as with any database handling sensitive information, auditing is essential to track user activities, monitor changes, and detect potential security breaches. This article explores the native auditing capabilities of ScyllaDB and how advanced tools like DataSunrise can enhance your auditing processes.
Native Database Audit in ScyllaDB
ScyllaDB provides built-in auditing features, particularly in its
Enterprise Edition, which allow administrators to monitor and log
database activities effectively. These native tools are configurable
through the scylla.yaml file, enabling you to specify what
types of activities to audit, where to store the logs, and how to
structure the audit data.
Configuring Native Auditing
To enable auditing in ScyllaDB, you can modify the scylla.yaml configuration file. Below is an example
configuration:
audit: "table"
audit_categories: "DCL,DDL,AUTH,ADMIN"
audit_tables: "mykeyspace.mytable"
audit_keyspaces: "mykeyspace"This configuration ensures that activities related to Data Control Language (DCL), Data Definition Language (DDL), Authentication (AUTH), and Administrative Operations (ADMIN) are logged. The logs can be stored in a dedicated ScyllaDB table or sent to Syslog for further analysis.
Example Audit Table Structure
When using table storage, the audit logs are stored in a structured format. Here’s an example of how to create an audit log table:
CREATE TABLE IF NOT EXISTS audit.audit_log (
date timestamp,
node inet,
event_time timeuuid,
category text,
consistency text,
table_name text,
keyspace_name text,
operation text,
source inet,
username text,
error boolean,
PRIMARY KEY ((date, node), event_time));Example Audit Log Output
Here’s an example of what the audit logs might look like when queried:
SELECT * FROM audit.audit_log;
date | node | event_time | category | consistency | table_name | keyspace_name | operation | source | username | error
---------------------+------------+-------------------------------------+----------+-------------+------------+---------------+-----------+------------+----------+-------
2024-02-20 09:00:00 | 192.168.1.1| 123e4567-e89b-12d3-a456-426614174000 | DCL | QUORUM | mytable | mykeyspace | SELECT | 192.168.1.2| admin | false
2024-02-20 09:05:00 | 192.168.1.1| 123e4567-e89b-12d3-a456-426614174001 | DDL | QUORUM | mytable | mykeyspace | CREATE | 192.168.1.2| admin | false
2024-02-20 09:10:00 | 192.168.1.1| 123e4567-e89b-12d3-a456-426614174002 | AUTH | QUORUM | mytable | mykeyspace | LOGIN | 192.168.1.3| user1 | false
2024-02-20 09:15:00 | 192.168.1.1| 123e4567-e89b-12d3-a456-426614174003 | ADMIN | QUORUM | mytable | mykeyspace | ALTER | 192.168.1.4| user2 | trueThis output demonstrates how ScyllaDB captures various database activities, including SELECT and ALTER operations, login attempts, and administrative changes. Each log entry provides detailed information such as the event time, category, consistency level, and source IP.
Database Audit with DataSunrise
While ScyllaDB’s native auditing tools are powerful, organizations with advanced security and compliance needs often require more comprehensive solutions. DataSunrise offers a robust set of tools designed to enhance ScyllaDB auditing capabilities, providing real-time monitoring, detailed audit trails, and automated compliance reporting.
Real-Time Monitoring and Query Analysis
DataSunrise provides real-time monitoring of all database activities, ensuring that every interaction with ScyllaDB is logged and analyzed. This includes privileged user monitoring, which is critical for detecting insider threats or unauthorized access.
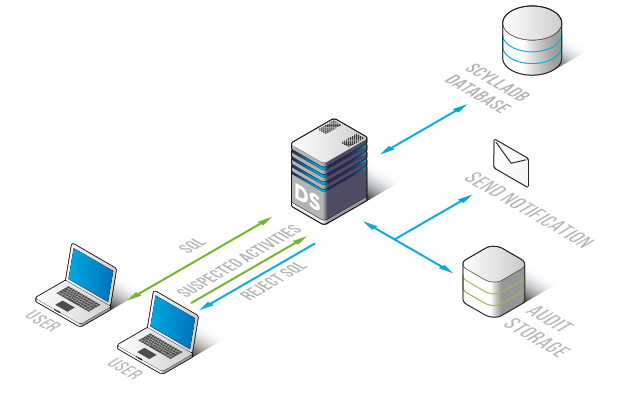
Advanced Audit Trails and Compliance Reporting
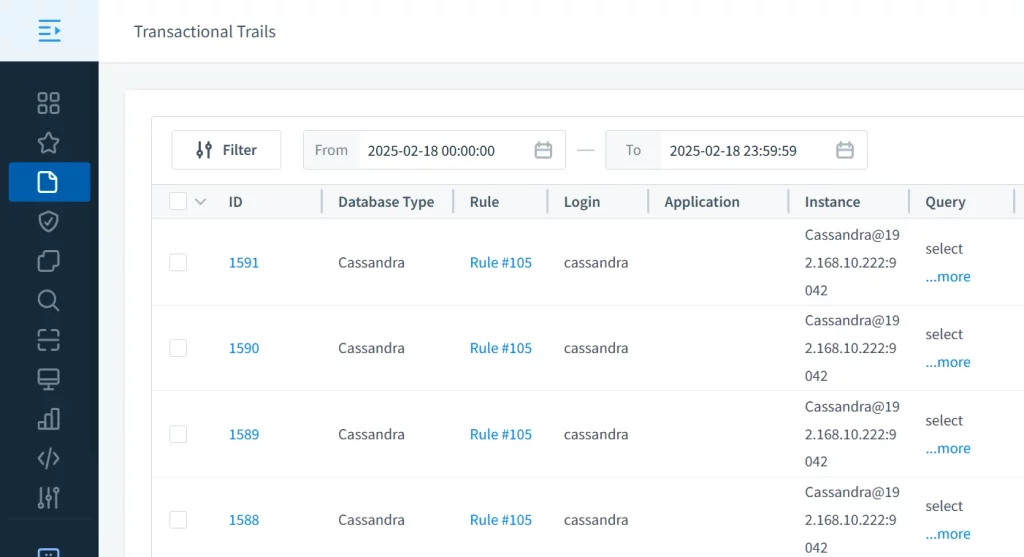
DataSunrise’s ScyllaDB Data Activity History feature maintains detailed logs of all database operations, enabling organizations to track changes, investigate incidents, and demonstrate compliance with regulatory requirements such as GDPR, HIPAA, and PCI DSS.
Automated Alerts and Incident Response
DataSunrise also includes automated alerting mechanisms that notify administrators of suspicious activities or policy violations. This proactive approach helps organizations respond quickly to potential security threats.
Conclusion
Auditing ScyllaDB is essential for maintaining data security, ensuring compliance, and detecting potential threats. While ScyllaDB’s native auditing tools provide a solid foundation, DataSunrise offers a more comprehensive solution with advanced features like real-time monitoring, detailed audit trails, and automated compliance reporting.
To experience the full capabilities of DataSunrise for ScyllaDB auditing, we encourage you to download the trial version or schedule a personalized demo today. Enhance your database security and compliance with the industry-leading tools provided by DataSunrise.
