How to Ensure Compliance for MySQL: Comprehensive Overview
Introduction
In today’s data-driven world, organizations are increasingly reliant on databases like MySQL to store and manage sensitive information, ranging from personal data to financial records and healthcare details. With the growing emphasis on data privacy and security, ensuring regulatory compliance for MySQL has become a critical priority for businesses. Non-compliance can result in hefty fines, legal consequences, and reputational damage.
MySQL, being one of the most widely used relational database management systems, offers a range of built-in features to help organizations meet compliance requirements. However, achieving full compliance often requires a combination of MySQL’s native capabilities and additional security measures, such as third-party tools.
This guide explores the key compliance frameworks relevant to MySQL, delves into its built-in security and auditing features, and highlights how third-party solutions like DataSunrise can further enhance your compliance efforts. Whether you’re managing personal data under GDPR, healthcare information under HIPAA, or financial records under SOX, this article provides actionable insights to help you secure your MySQL databases and meet regulatory standards.
Understanding Key Compliance Requirements for MySQL
Organizations handling sensitive data must comply with industry regulations. MySQL databases often store personal, financial, and healthcare data, making compliance essential. Below are major compliance frameworks relevant to MySQL:
- GDPR (General Data Protection Regulation): Requires encryption, user access controls, and audit logs to protect personal data.
- HIPAA (Health Insurance Portability and Accountability Act): Mandates security controls for healthcare data, including access monitoring and encryption.
- PCI-DSS (Payment Card Industry Data Security Standard): Requires secure storage, logging, and role-based access for payment information.
- SOX (Sarbanes-Oxley Act): Demands audit trails and access control for financial data integrity.
Ensuring compliance involves using MySQL’s built-in features and additional security measures. For more details on MySQL’s security features, refer to the MySQL documentation.
Built-in MySQL Security and Auditing Features
User Privileges and Roles
MySQL supports role-based access control (RBAC) to restrict data access. You can create roles and assign privileges:
CREATE ROLE auditor; GRANT SELECT ON database.* TO auditor; GRANT SHOW DATABASES ON *.* TO auditor;
Then, assign the role to users:
GRANT auditor TO 'user1'@'localhost'; SET DEFAULT ROLE auditor FOR 'user1'@'localhost';
Logging and Auditing
MySQL provides various logging mechanisms to track changes and access attempts:
- General Query Log: Records all queries.
- Binary Log: Tracks changes for replication and recovery.
- MySQL Enterprise Audit: Offers structured audit logging.
Enable logging with:
SET GLOBAL general_log = 'ON'; SET GLOBAL log_output = 'FILE';
Encryption
MySQL supports Transparent Data Encryption (TDE) for protecting stored data and SSL/TLS for secure connections.
ALTER TABLE sensitive_data ENCRYPTION='Y';
Auditing MySQL Using Native Tools
Using SQL Logs
MySQL logs queries in a general query log file. You can monitor it using:
SHOW VARIABLES LIKE 'general_log%'; SHOW VARIABLES LIKE 'log_output';
Using Binary Logs
Binary logs store database changes, useful for compliance audits.
SHOW BINARY LOGS;
MySQL Enterprise Audit
This tool provides XML-based logs for security audits. Enable it with:
INSTALL PLUGIN audit_log SONAME 'audit_log.so'; SET GLOBAL audit_log_policy = 'ALL';
Enhancing MySQL Compliance with Third-Party Tools
While MySQL’s built-in security features are robust, third-party tools like DataSunrise enhance security with:
Setting Up DataSunrise for MySQL
Assuming DataSunrise is installed, create an instance and enable dynamic masking:
- Log into DataSunrise as administrator.
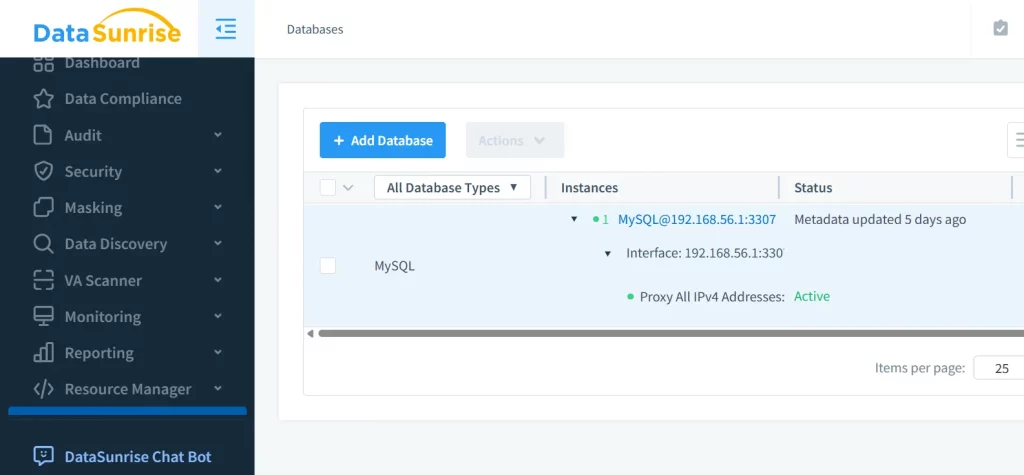
- Add a MySQL database instance in “Configuration” tab.
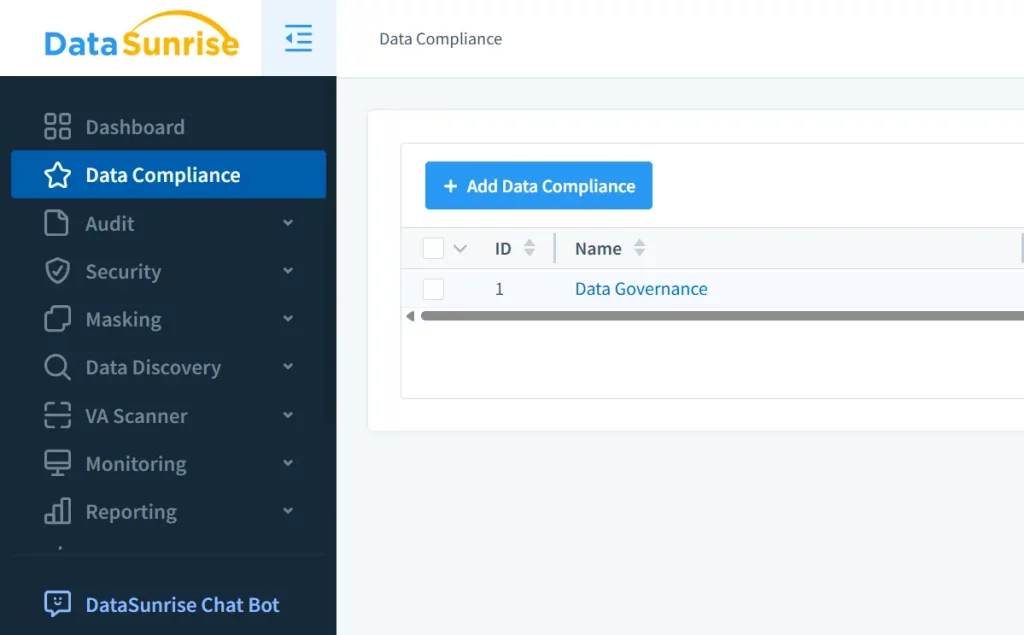
- Define Compliance rules in “Data Compliance” tab.
Conclusion
Ensuring MySQL compliance involves using built-in security features, logging, and third-party tools like DataSunrise. By implementing role-based access, audit logs, and encryption, businesses can meet regulatory requirements efficiently.
For enhanced security and compliance, consider DataSunrise’s security platform, which offers dynamic masking, real-time monitoring, and centralized control. Visit the DataSunrise website for an online demo.
