
Hydra Audit Log

Introduction
In modern data infrastructure, maintaining comprehensive audit log is crucial for security, troubleshooting, and compliance. Hydra, as a powerful hybrid database that combines PostgreSQL's transactional capabilities with DuckDB's analytical prowess, provides robust database activity monitoring capabilities inherited from its PostgreSQL foundation. Understanding and properly configuring these audit logs is essential for maintaining system health and meeting data security requirements.
Understanding Hydra Audit Log
Hydra's audit logging system captures detailed information about database operations, user activities, and system events. These logs are crucial for:
- Tracking database operations and performance
- Monitoring user activities and access patterns
- Investigating security incidents
- Maintaining compliance requirements
- Troubleshooting database issues
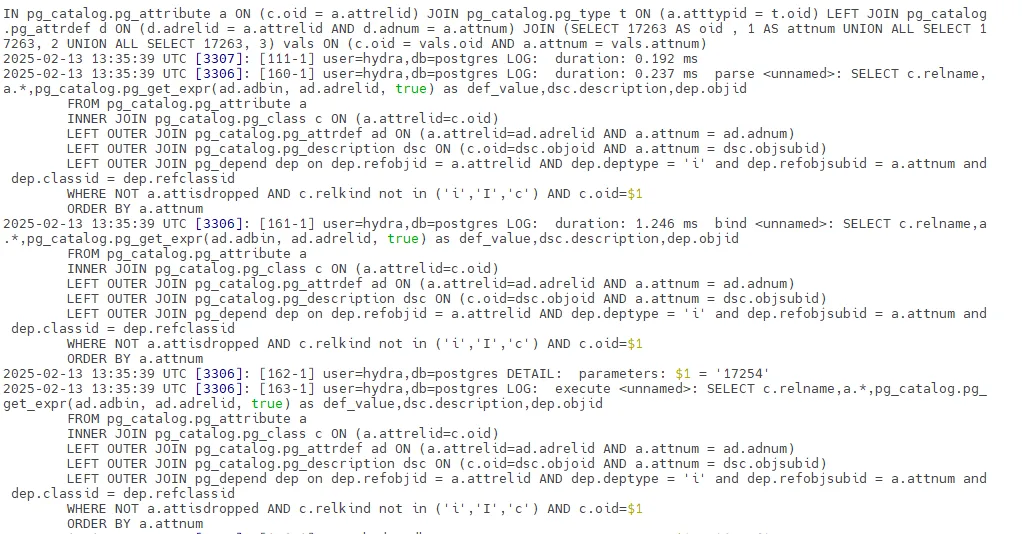
Log File Location and Structure
Hydra stores its audit logs in standard PostgreSQL log locations, typically found in:
/var/log/postgresql/postgresql-*.log
For containerized deployments, logs can be accessed using:
docker logs hydra_db_1
Configuring Hydra Audit Log
To optimize Hydra's audit logging capabilities, you can modify the logging parameters in postgresql.conf:
# Basic logging configuration
logging_collector = on
log_destination = 'stderr'
log_directory = 'pg_log'
log_filename = 'postgresql-%Y-%m-%d.log'
# Define logging level
log_min_messages = 'warning' # Log warnings and above
log_min_error_statement = 'error' # Log SQL causing errors
# Detailed statement logging
log_statement = 'all' # Log all SQL statements
log_line_prefix = '%t [%p]: [%l-1] user=%u,db=%d,app=%a,client=%h '
Types of Logged Information
Hydra's audit logs capture various types of events:
- Connection Events: User login attempts, disconnections
- Query Execution: SQL statements, execution times
- Schema Changes: Table creation, index modifications
- Error Events: Failed queries, system errors
- Performance Data: Slow queries, resource usage
Analyzing Hydra Audit Log
Basic Log Analysis
View recent log entries using standard Unix tools:
# View last 100 log lines
tail -n 100 /var/log/postgresql/postgresql-*.log
# Search for specific events
grep "error" /var/log/postgresql/postgresql-*.log
# Monitor logs in real-time
tail -f /var/log/postgresql/postgresql-*.log
Advanced Monitoring
For more detailed analysis, Hydra supports integration with various monitoring tools:
-- Check current database activity
SELECT
pid,
usename,
application_name,
client_addr,
query_start,
state,
query
FROM pg_stat_activity
WHERE state != 'idle';
-- View statement statistics
SELECT
query,
calls,
total_exec_time,
rows
FROM pg_stat_statements
ORDER BY total_exec_time DESC
LIMIT 10;
Best Practices for Hydra Audit Log Management
- Log Rotation: Implement proper log rotation to manage disk space:
# Example logrotate configuration /var/log/postgresql/*.log { weekly rotate 12 compress delaycompress notifempty create 0640 postgres postgres } Security Considerations:
- Protect log files with appropriate permissions
- Monitor log file access
- Regularly archive logs for compliance
Performance Impact:
- Balance logging detail with system performance
- Monitor log file sizes
- Adjust logging levels based on requirements
Enhanced Hydra Audit Log with DataSunrise
Hydra's built-in logging provides essential capabilities, but DataSunrise takes it further with advanced security, compliance, and log management features.
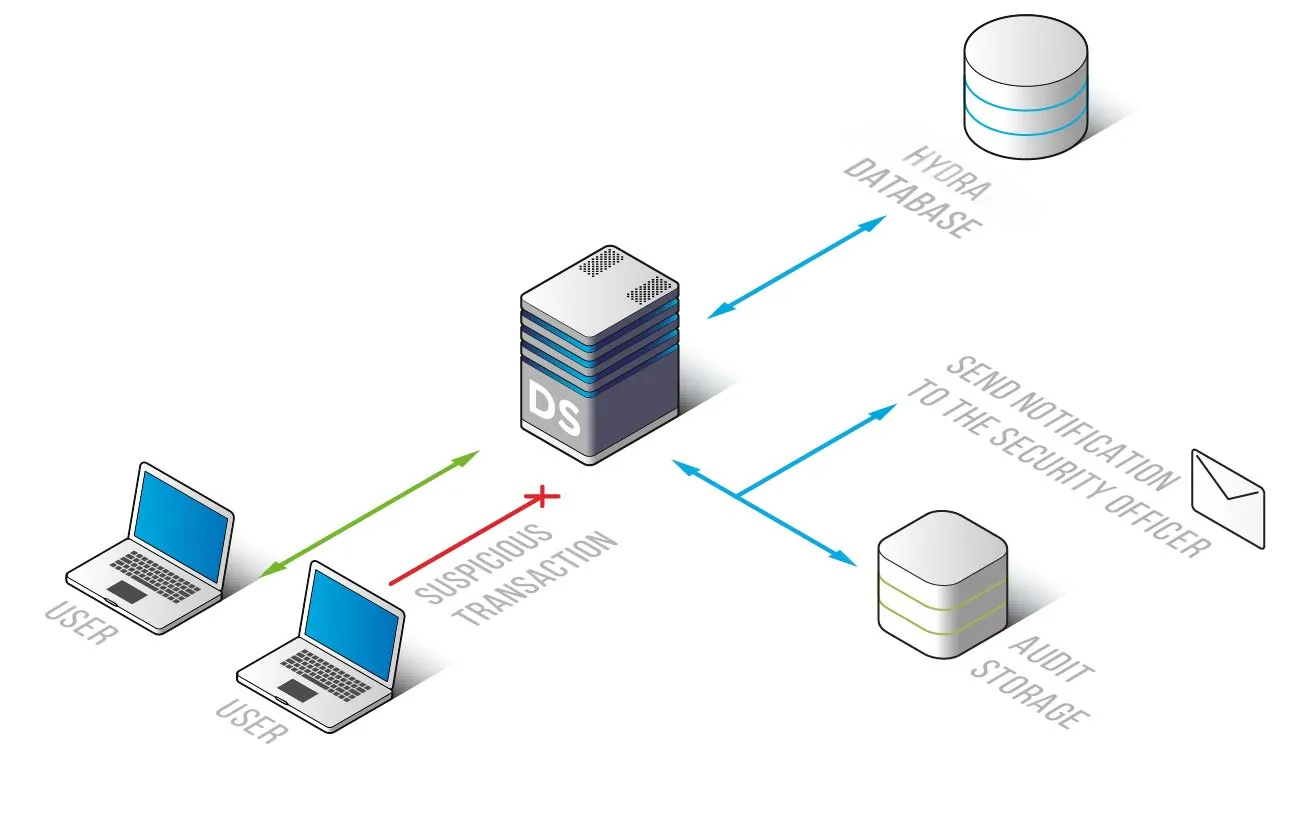
Streamlined Hydra Audit Log Management
DataSunrise simplifies database log oversight with a centralized interface, offering:
- Live log monitoring and analysis for real-time security insights
- Powerful search and filtering tools for quick data retrieval
- Secure long-term log storage for compliance and audit purposes
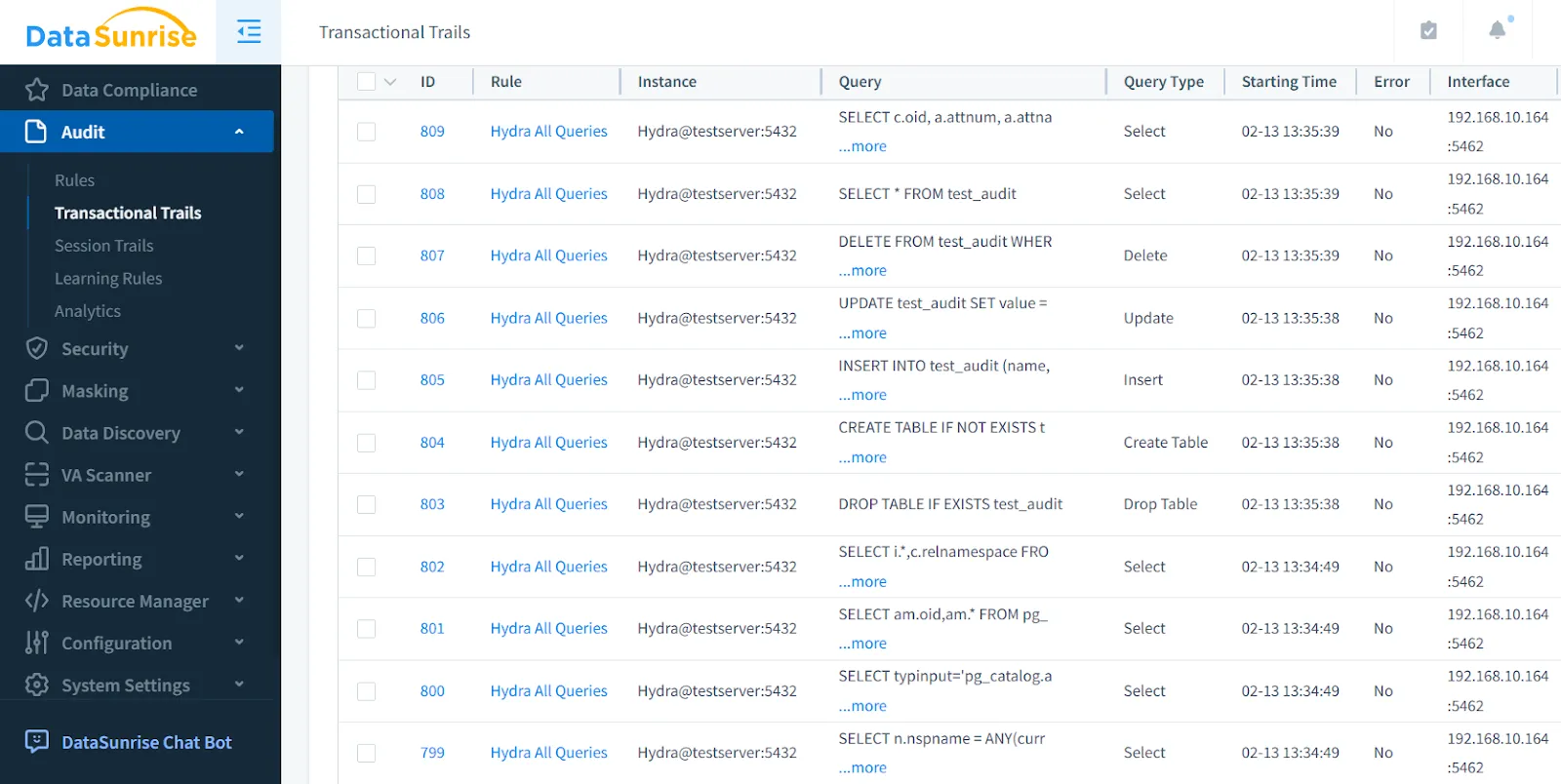
Robust Audit Capabilities
Comprehensive auditing is key for security and regulatory compliance. DataSunrise enhances Hydra’s audit logging with:
- Database Activity Monitoring – Consolidates logs from various sources for complete visibility.
- Regulatory Compliance Support – Aligns database activity tracking with GDPR, HIPAA, PCI DSS, and other standards.
- Automated Audit Reports – Generates detailed compliance reports with minimal manual effort.
These tools make auditing more efficient while reinforcing data security and regulatory adherence.
Multi-Layered Security Protection
A secure database setup requires more than just logging. DataSunrise strengthens Hydra databases with:
- Network Security Controls – Restricts unauthorized access by filtering traffic between external and internal systems.
- Threat Detection & Prevention – Monitors for anomalies and blocks suspicious activity in real time.
- Granular Access Management – Implements role-based access control (RBAC) to safeguard sensitive data.
By combining these measures, DataSunrise helps mitigate risks from cyber threats and insider misuse.
Proactive Security Enhancements
In addition to logging, DataSunrise offers advanced security solutions, including:
- Dynamic Data Masking – Hides sensitive data in queries to prevent unauthorized exposure.
- Instant Security Alerts – Notifies admins of critical security incidents in real time.
- AI-Driven Threat Detection – Uses machine learning to identify and stop potential risks.
With these combined features, DataSunrise not only enhances Hydra’s audit logging but also strengthens security and compliance, offering a complete solution for protecting database activity.
Conclusion
While Hydra provides essential logging capabilities, organizations requiring comprehensive log management, security, and compliance solutions can significantly benefit from integrating DataSunrise.
DataSunrise with its advanced features, intuitive interface, and robust security controls becomes an ideal choice for enterprises serious about log management and analysis.
Ready to experience advanced logging capabilities for your Hydra database? Schedule a demo today to see how DataSunrise can enhance your database monitoring and security.
