
IBM Db2 Audit Trail
Introduction
As highlighted in IBM's 2024 Cost of a Data Breach Report, organizations with robust audit and monitoring systems reduced their average breach costs by USD 2.2 million compared to those without such measures. Enabling IBM Db2 audit trail helps database administrators ensure regulatory compliance, investigate security incidents, and maintain a detailed operational record.
What is IBM Db2 Audit Trail?
The audit trail provides a comprehensive log of database events and activities. In IBM Db2, this functionality is powered by the db2audit facility, which supports independent auditing at both the instance and database levels. According to IBM's official documentation, this dual-level auditing capability offers precise control over what actions are monitored, making it a standout feature of Db2 for ensuring security and compliance.
Enabling IBM Db2 Audit Trail with db2audit
To enable audit trails in IBM Db2, you must activate and configure the Db2 audit facility at the instance level. This guide explains how to achieve this step-by-step.
Prerequisites
You can run a testing Db2 instance on Docker using IBM's official guide. The setup process will give you a working Db2 instance where you can configure audit trails.
Step 1: Verify Current Audit Settings
Start by checking the default audit settings in your Db2 instance using the following command:
db2audit describe
A typical output looks like this:
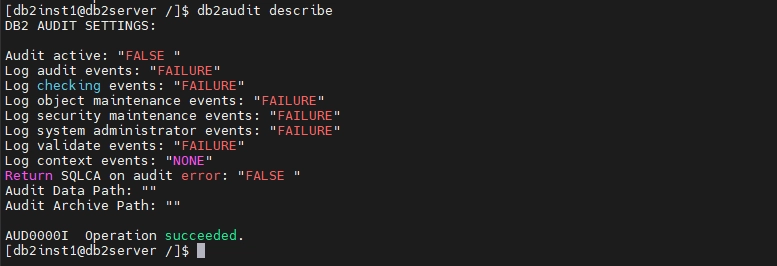
This indicates:
- Audit active: Auditing is currently disabled (
FALSE). - Log audit/checking/object maintenance/etc: Specific categories of events are not being logged.
- Audit Data Path: No path is defined to store audit logs.
- Audit Archive Path: No path is set for archiving audit logs.
Important Note: By default, the audit facility is inactive, and no paths are configured for logs. To enable proper auditing, you'll need to specify the data and archive paths for storing audit logs.
Step 2: Configure IBM Db2 Audit Trail Paths
Set up the directories where audit logs will be stored:
db2audit configure datapath /path/to/audit_logs
db2audit configure archivepath /path/to/audit_archive
- datapath: Directory for storing current audit logs.
- archivepath: Directory for archiving old audit logs.
Important Note: Ensure these directories exist and have the necessary permissions for the Db2 instance user.
Step 3: Enable and Start Auditing
Enable auditing by specifying the scope and status, then start the audit facility:
db2audit configure scope all status both
db2audit start
Command Breakdown:
scope all: Audits all activities, including object access, system-level events, and security changes.status both: Captures both successful and failed actions.db2audit start: Activates the audit facility.
Verify Audit Activation
After completing the configuration, verify that auditing is active:
db2audit describe
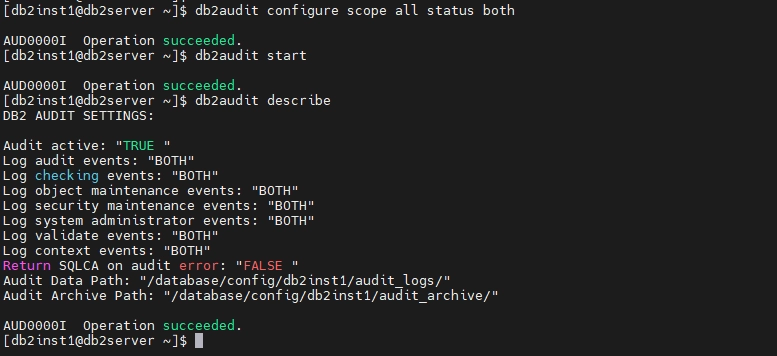
The updated settings should now show Audit active: "TRUE"and display the configured paths.
By following these steps, you’ll have a fully operational audit trail system in IBM Db2, ready to capture and log database activities effectively.
Generating and Extracting IBM Db2 Audit Trail
The following steps demonstrate how to set up and extract audit logs for instance-level auditing in IBM Db2. Instance-level auditing captures events related to the Db2 instance as a whole, such as user authentication, configuration changes, and system-level operations. If you're looking to implement database-level auditing for more granular tracking, you can refer to IBM's page on database-level audit policies and their configuration for more detailed guidance.
Step 1: Flush and Archive Audit Records
Before extracting logs, ensure that all pending audit records are written to the log and archived:
db2audit flush
db2audit archive`
flush: Forces any pending audit records to be written to the audit log to prevent data loss.archive: Creates a timestamped copy of the current audit logs for safekeeping. The generated filename follows the format:db2audit.instance.log.member_number.YYYYMMDDHHMMSS
Step 2: Extract Audit Data
To make the archived logs human-readable, extract them into a text file:
db2audit extract file audit_report.txt from files db2audit.instance.log.*
This command converts the binary audit logs into a text file named audit_report.txt, making it easier to review.
Step 3: Reviewing the Extracted IBM Db2 Audit Trail
The extracted file is in text format and contains detailed audit information. Open it in any text editor to review events such as user logins, data modifications, and authorization failures.
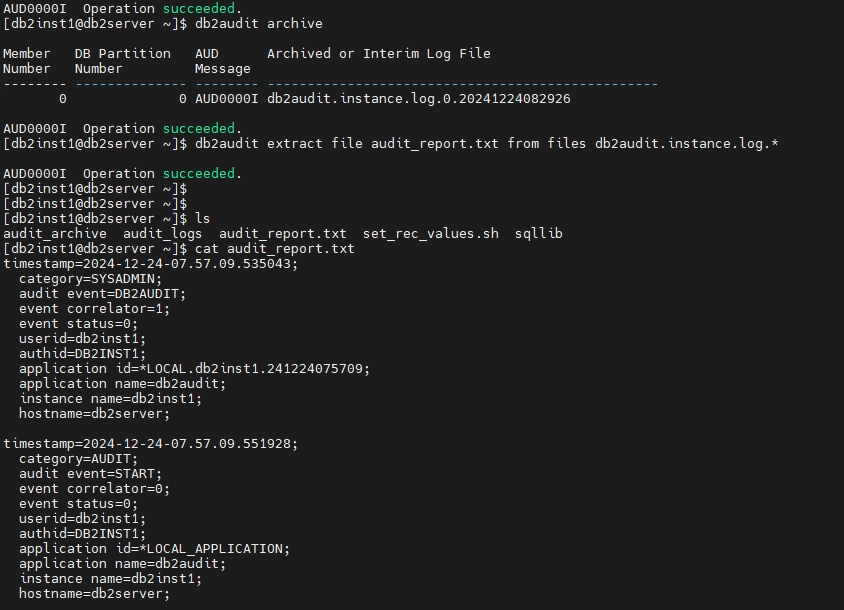
The extracted file contains detailed information about instance-level activities, such as:
- Authentication attempts
- Object access and modifications
- Security changes
- System administration operations
- Audit configuration updates
Each record includes the timestamp, user information, details of operation, and success/failure status. You can refine the extracted data further using tools or scripts for enhanced analysis.
Advanced Features for IBM Db2 with DataSunrise
While Db2's native auditing tools provide comprehensive logging capabilities, integrating with DataSunrise can significantly enhance these features. DataSunrise offers:
- Centralized Control: Manage audit logs across multiple databases from a single interface, enabling real-time monitoring of database activities, user behavior patterns, and security events across not just your Db2 infrastructure, but across over 40 different database platforms, both SQL and NoSQL, in the cloud or on-premises.
- Advanced Reporting: Generate detailed compliance reports and analytical insights with customizable templates, automated scheduling, and comprehensive audit trail analysis for both internal security reviews and regulatory requirements.
- Dynamic Data Masking: Protect sensitive information in audit logs through intelligent masking algorithms that maintain data usability while ensuring confidentiality – particularly crucial for PII, financial data, and other regulated information types.
DataSunrise complements Db2's db2audit facility by providing enhanced visibility, streamlined compliance reporting, and advanced data protection capabilities. These features help organizations meet evolving security requirements while maintaining operational efficiency.
Conclusion
While IBM Db2's native db2audit facility provides powerful auditing capabilities, modern security challenges often demand comprehensive solutions that go beyond just tracking database interactions.
DataSunrise enhances Db2's built-in features with next-generation security tools that scale with your enterprise needs. With flexible deployment options and comprehensive audit features, organizations can build a secure, compliant data infrastructure that's ready for future challenges.
Ready to augment your Db2 audit capabilities? Try our online demo today and see how advanced audit trail management can transform your data security.
