
IBM Db2 Data Activity History

Introduction
The IBM Db2 Data Activity History plays a crucial role in understanding and monitoring database operations. Database auditing in IBM Db2 not only ensures operational transparency but also strengthens the security posture of organizations. A well-implemented data activity history acts as a detailed log of all interactions and modifications within the system. This is essential for achieving regulatory compliance, deterring fraud, and identifying potential security risks. In this article, we will delve into the native Db2 features for tracking database activity and demonstrate how DataSunrise can enhance these processes, making them more efficient and robust.
Native Audit Options in IBM Db2
IBM Db2 provides powerful built-in auditing functionality through the db2audit tool. This tool captures database events across multiple categories, such as security operations, data access, and system maintenance. With detailed audit records containing timestamps, user details, and SQL statements, it offers a strong foundation for tracking database activities. However, managing and analyzing these logs in complex environments often presents challenges. Let’s examine the capabilities and limitations of db2audit in detail.
| Feature | Limitation |
|---|---|
| Flexible Scope: Tracks activities at both instance and database levels, ensuring comprehensive coverage of user actions. | Complex Log Management: Separate logs for each instance require manual aggregation and analysis for a unified view. |
| Event Categorization: Monitors login attempts, data access, administrative changes, and more through predefined event classes. | Labor-Intensive Processing: Extracting and interpreting logs often involves a lengthy manual process with multiple commands, or alternatively, the use of custom scripts or additional tools for proper log parsing. |
| Detailed SQL Logging: Records executed SQL statements, their outcomes, and associated user details for enhanced traceability. | Instance Isolation: Native tools in Db2 store logs separately for each instance, necessitating manual aggregation to perform cross-instance analysis. |
Example: Auditing the "sensitive_data" Table
To monitor sensitive operations on a table named sensitive_data, you can extend db2audit with a focused policy:
1. Enable Database-Level Auditing
Run the following command to configure auditing at the database level:
db2audit configure scope <db_name> status both
2. Define an Audit Policy
Create a policy to monitor EXECUTE actions on sensitive data. This logs both normal and error events:
-- Create an audit policy for sensitive data
CREATE AUDIT POLICY audit_sensitive_data
CATEGORIES EXECUTE WITH DATA
STATUS BOTH
ERROR TYPE NORMAL;
3. Apply the Policy to the Table
Link the created policy to the sensitive_data table:
-- Apply the policy to the table
AUDIT TABLE sensitive_data USING POLICY audit_sensitive_data;
4. Verify the Policy Configuration
Use the following queries to confirm the policy is active:
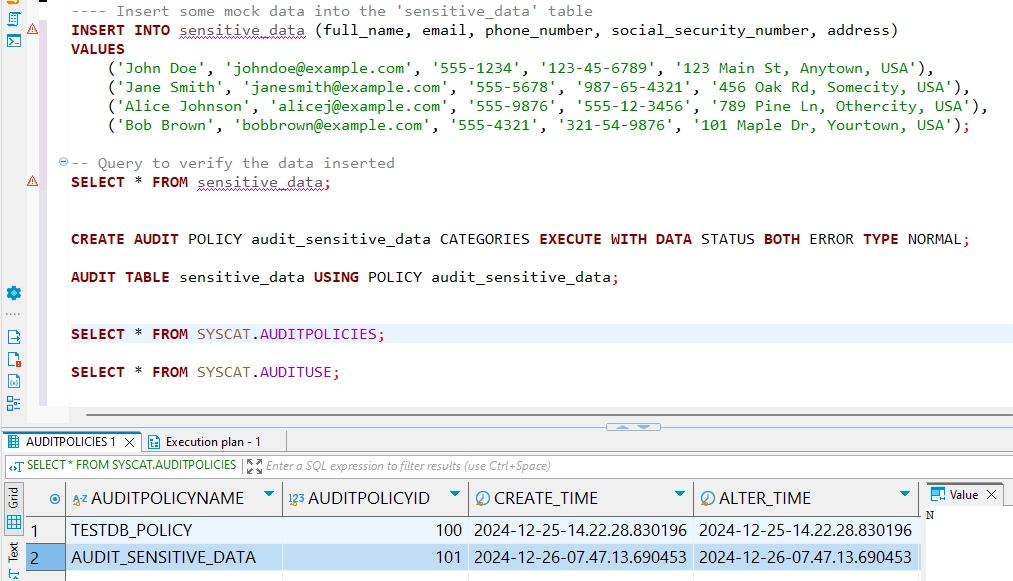
-- List all configured audit policies
SELECT * FROM SYSCAT.AUDITPOLICIES;
-- Check which objects are being audited
SELECT * FROM SYSCAT.AUDITUSE;
5. View the Logs
After applying the audit policy and running several queries to audited table, logs can be retrieved and analyzed as follows:
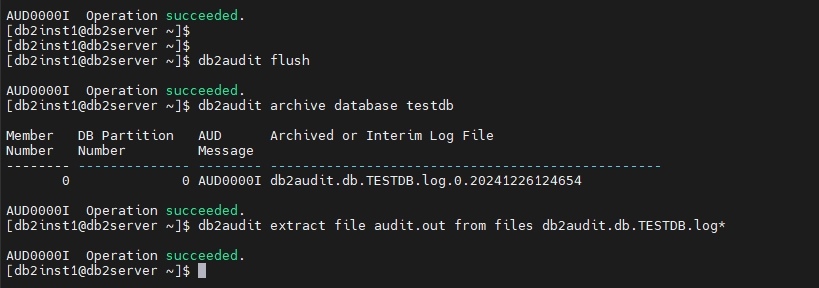
- Extract the audit log files:
db2audit flush
db2audit archive database <db_name>
db2audit extract file audit.out from files db2audit.db.TESTDB.log*
Replace
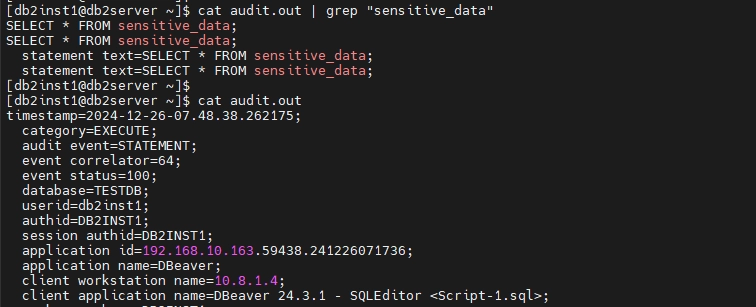
- Review the extracted logs using any text editor or custom tools. The extracted logs will contain entries for all
EXECUTEactions on thesensitive_datatable, for example
cat audit.out | grep "sensitive_data"
This configuration logs all access attempts and modifications to the sensitive_data table, helping to safeguard critical information.
Enhancing IBM Db2 Data Activity History with DataSunrise
DataSunrise offers advanced tools to address the limitations of native Db2 auditing, enabling seamless management of data activity history. Its intuitive interface, real-time monitoring capabilities, and configurable audit policies make it a valuable addition to Db2 environments.
Setting Up DataSunrise for IBM Db2
Here’s how to get started with DataSunrise to optimize your Db2 data activity history:
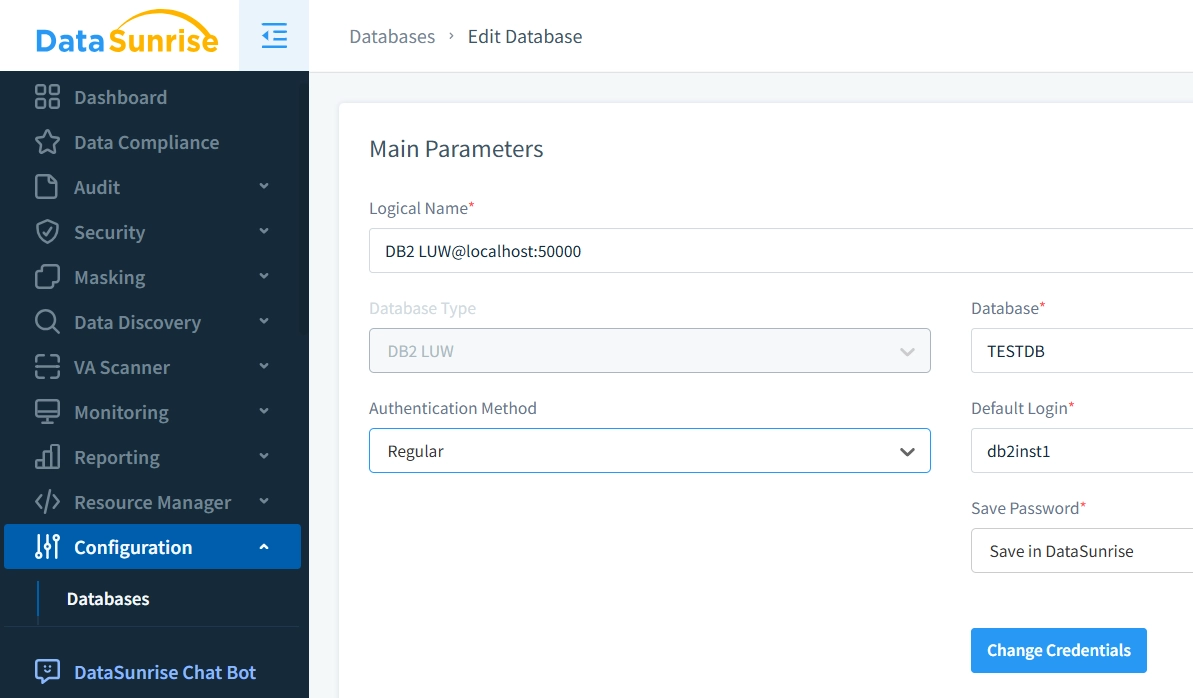
Step 1: Establish a Connection
Launch the DataSunrise web interface and connect your Db2 instance. Provide server details, credentials, and the database name. DataSunrise’s pre-installed drivers simplify the setup, ensuring quick integration.
Step 2: Define Data-Specific Audit Policies
Create tailored audit policies within DataSunrise to focus on sensitive data. For example, to monitor the sensitive_data table:
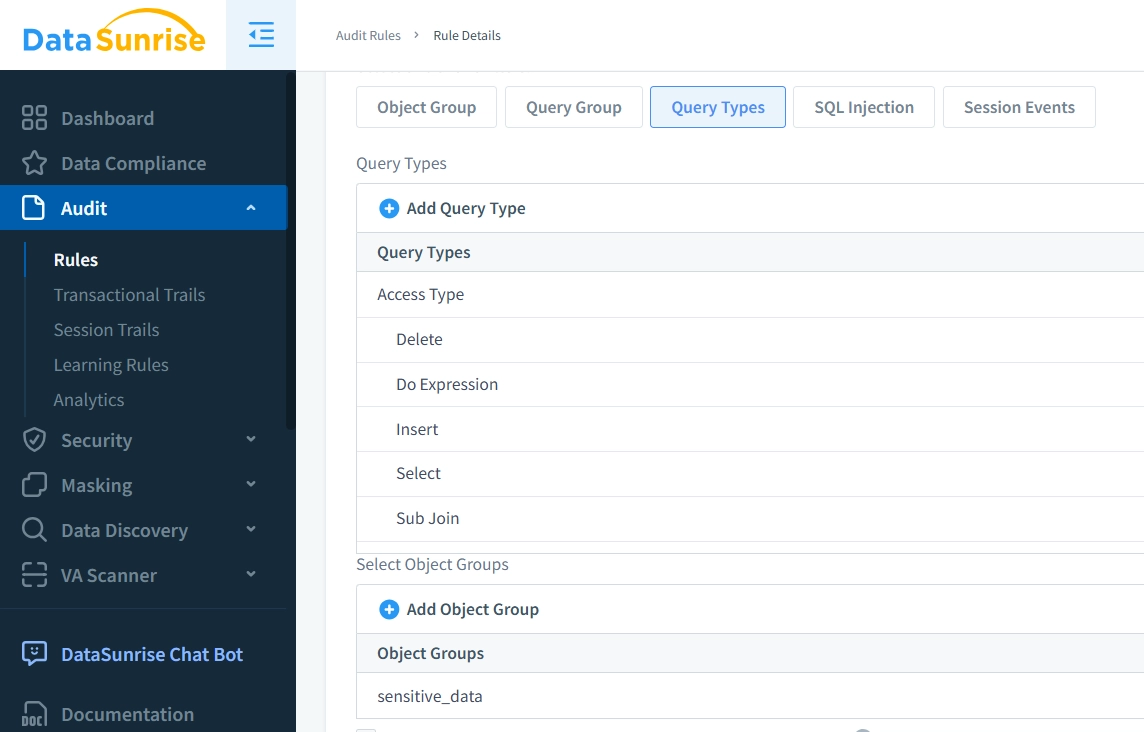
Navigate to the “Audit Rules” section.
Define a new rule targeting
sensitive_data.Specify the operations to track (e.g., SELECT, INSERT, DELETE).
Assign user roles or IP ranges for detailed control.
Step 3: Monitor Activity in Real Time
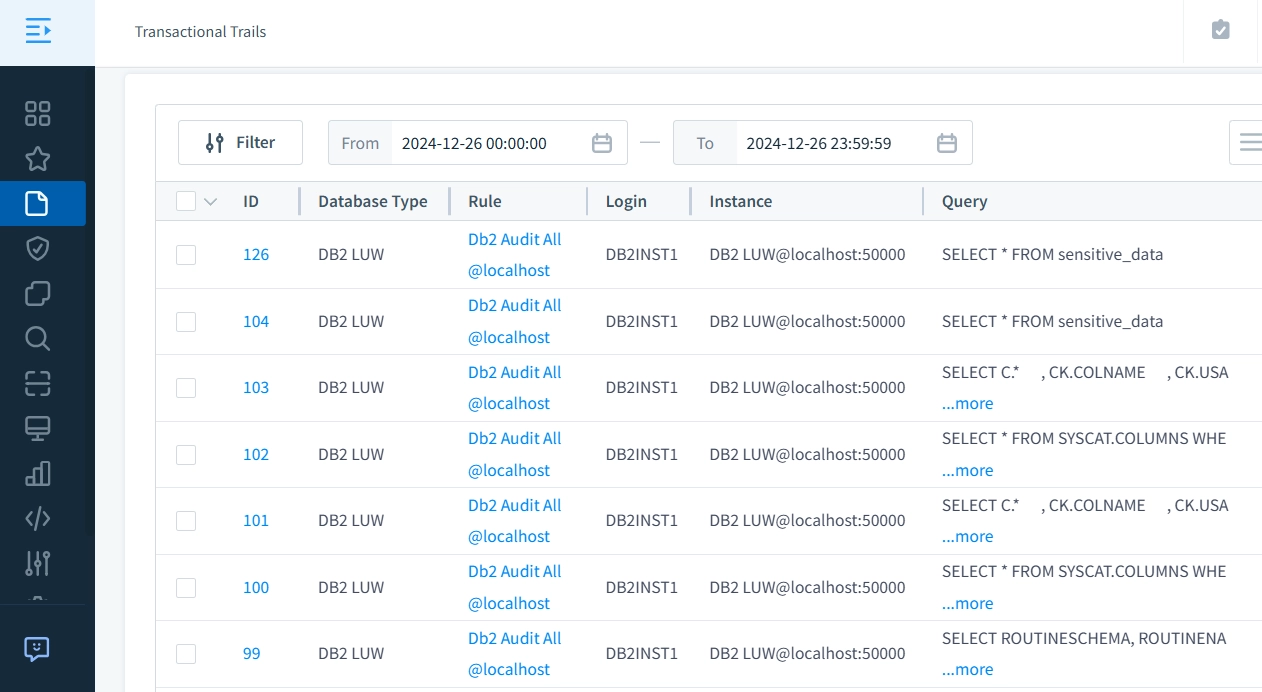
Once configured, DataSunrise captures database activities and displays them in a user-friendly dashboard. You can filter and search activities by user, action, or object for quick analysis. Alerts can be set up to notify administrators of suspicious actions immediately.
Step 4: Automate Compliance Reporting
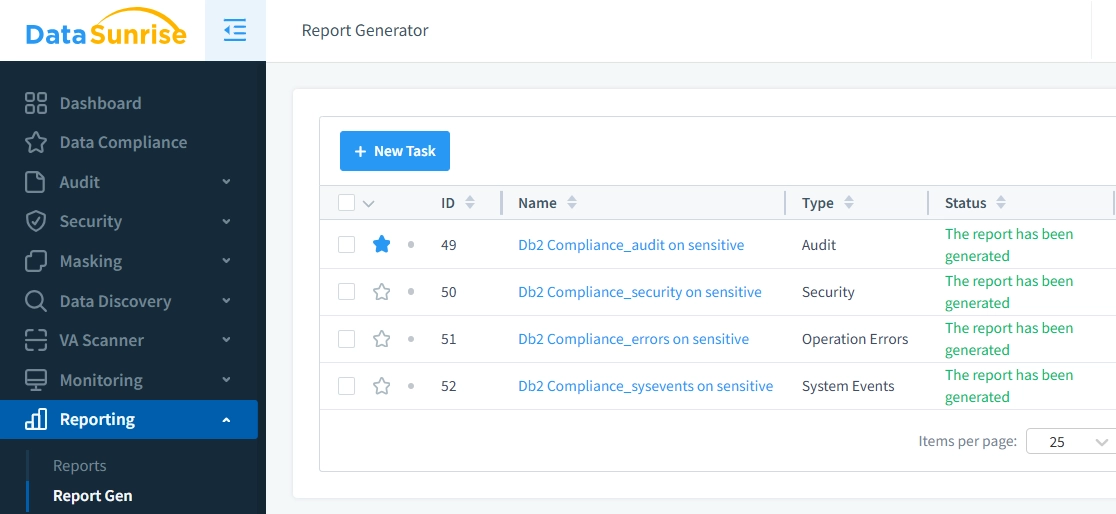
DataSunrise’s automated reporting tools streamline compliance efforts. Pre-configured templates for regulations like GDPR, HIPAA, and PCI DSS ensure accurate documentation with minimal effort.
DataSunrise: Advanced Capabilities for Db2 Data Activity History
Beyond enhancing audit trails, DataSunrise provides a suite of advanced features to strengthen security and compliance:
Centralized Log Management: Aggregate logs from multiple data storage platforms with support for over 40 databases for unified analysis and reporting.
Flexible Deployment Options: Supports various environments, including on-premises, cloud, and hybrid setups, for maximum adaptability.
Dynamic Data Masking: Protect sensitive data without disrupting application functionality.
Real-Time Threat Detection: Prevent unauthorized access and SQL injection attacks with proactive security measures.
Behavior Analytics: Detect anomalies and potential threats using advanced user behavior analysis.
Conclusion
Even though IBM Db2’s native tools provide a strong foundation for data activity history tracking, they may not fully address the needs of modern, dynamic environments.
DataSunrise complements and enhances Db2’s capabilities, offering centralized management, real-time alerts, and granular control over database auditing. By integrating DataSunrise into your Db2 setup, you can achieve streamlined compliance, robust security, and actionable insights with ease.
To see DataSunrise in action, request a live demo today and discover how it can transform your Db2 data activity history management.
