
IBM Db2 Database Activity History
Introduction
Understanding and tracking database activities is crucial for maintaining security and compliance in modern enterprises. Database activity history in IBM Db2 provides organizations with detailed insights into database operations, user actions, and system events. This brief guide explores how to effectively implement and manage database activity monitoring in Db2 environments.
Understanding IBM Db2 Database Activity History
IBM Db2, IBM's enterprise database solution, includes robust auditing capabilities through its native db2audit facility. This tool generates detailed activity logs that help organizations track database access, modifications, and security events.
Key Components of Database Activity Monitoring
The db2audit trail system captures various types of database activities:
- Authentication events and access attempts
- Database object modifications
- Security policy changes
- Query execution details
- System-level operations
Setting Up Database-Level Audit Policies
To implement effective database activity monitoring in DB2, you need to configure appropriate audit policies. This guide outlines the steps for setting up basic database-level auditing, from configuring the audit tool to creating policies and running test queries.
Prerequisites
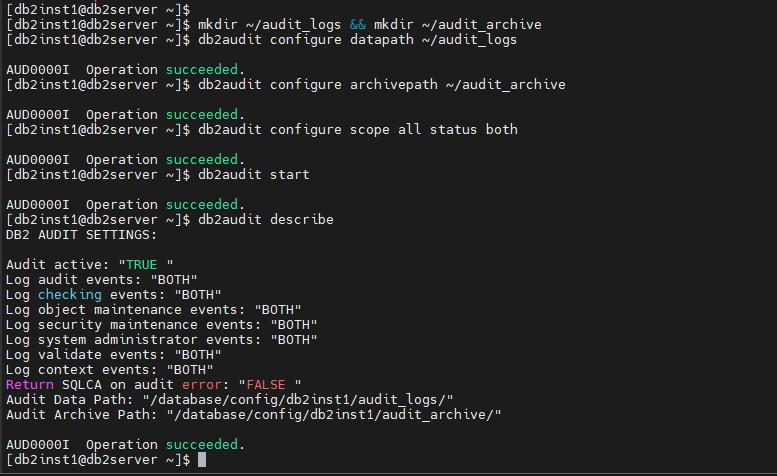
Before setting up database-level auditing, ensure that the db2audit tool is properly configured and ready for use. If the tool has never been used before, you may need to specify:
- Data Path: Defines where the audit data is stored.
- Archive Path: Specifies where archived audit logs are saved.
- Scope of Audit: Determines what activities should be monitored.
For more information on the initial configuration, refer to the appropriate page on IBM official documentation
Below is an example of a basic configuration:
Creating Policies and Recording Test Queries
After ensuring the db2audit tool's proper configuration, you can test its database-level audit functionality using a simple rule and a series of test queries. Follow these steps:
1. Connect to Your Database
Replace the example credentials with your actual database information:
# Connect to your database
db2 connect to testdb user db2inst1 using password
2. Create and Apply an Audit Policy
# Create a database-wide audit policy
db2 -v "CREATE AUDIT POLICY TESTDB_POLICY CATEGORIES ALL STATUS BOTH ERROR TYPE NORMAL"
# Apply the audit policy to the database
db2 -v "AUDIT DATABASE USING POLICY TESTDB_POLICY"
3. Start the Audit
# Start recording database activity
db2audit start
4. Perform Test Queries
Run a series of commands to generate audit records:
# Create a test table
db2 -v "CREATE TABLE audit_table (id INT, name VARCHAR(50), created_at TIMESTAMP DEFAULT CURRENT_TIMESTAMP)"
# Insert records
db2 -v "INSERT INTO audit_table (id, name) VALUES (1, 'Test User')"
db2 -v "INSERT INTO audit_table (id, name) VALUES (2, 'Another User')"
# Select records
db2 -v "SELECT * FROM audit_table"
# Update a record
db2 -v "UPDATE audit_table SET name = 'Updated User' WHERE id = 1"
# Delete a record
db2 -v "DELETE FROM audit_table WHERE id = 2"
# Select records again
db2 -v "SELECT * FROM audit_table"
5. Detach the Audit Policy and Clean Up
# Remove the audit policy from the database
db2 -v "AUDIT DATABASE REMOVE POLICY"
# Drop the audit policy
db2 -v "DROP AUDIT POLICY TESTDB_POLICY"
# Stop the audit
db2audit stop
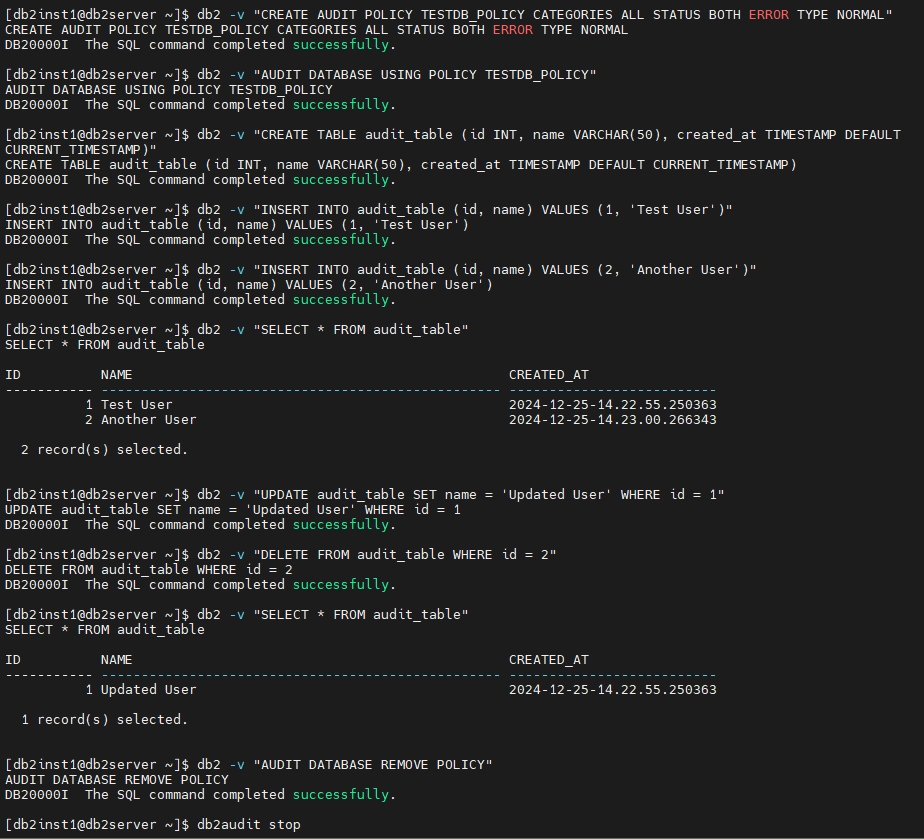
Expected Output
The output of the commands will confirm the execution of the policy creation, test queries, and cleanup steps. Below is an example of the expected output:
Extracting and Viewing IBM Db2 Database Activity History Records
To ensure all audit records are properly captured and stored, you'll need to manage the audit logs regularly. Here's the process:
1. Flush Current Audit Buffer
db2audit flush
This ensures all pending audit records are written to the audit log files.
2. Archive Database-Specific Audit Logs
db2audit archive database testdb
This command creates an archive of audit logs specific to the 'testdb' database, with a timestamp-based filename.
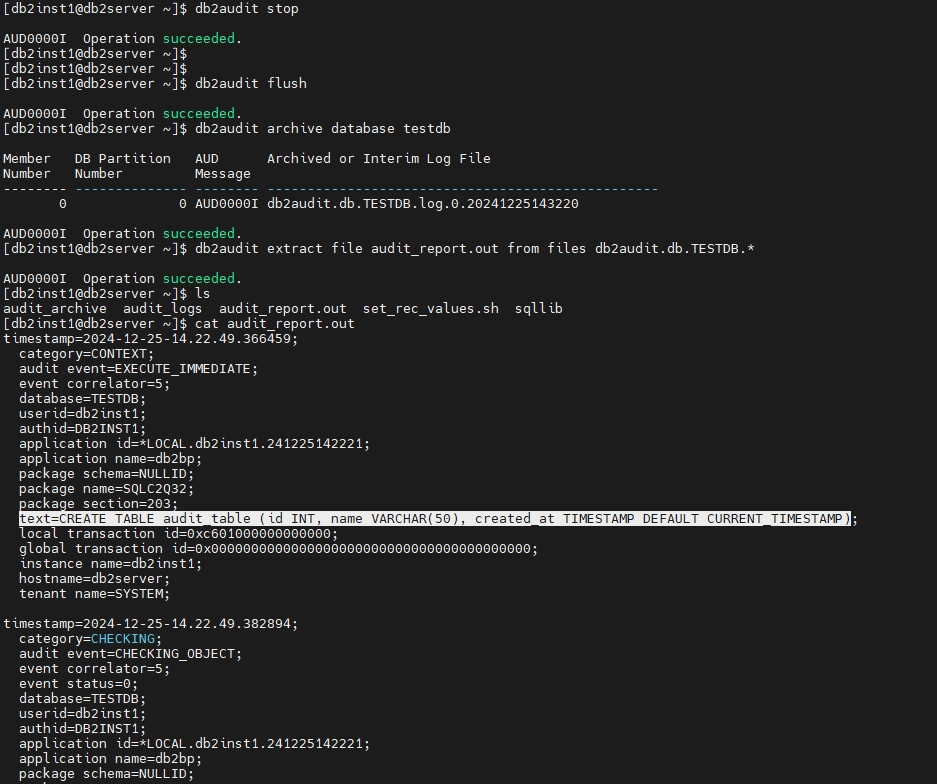
3. Extract Logs to Readable Format
db2audit extract file audit_report.out from files db2audit.db.testdb.log.*
This extracts the audit records into a human-readable format. The filename pattern includes the database name and today's date.
Analyzing IBM Db2 Database Activity History Records
The extracted audit file contains detailed information about database activities. Here's how to interpret key sections:
- Authentication Events
- Shows successful and failed login attempts
- Records user IDs, timestamps, and connection details
- Object Access Records
- Lists all operations on audited tables
- Includes SQL statements executed against sensitive data
- Records user context for each operation
For more information about what gets logged by db2audit you can navigate to this page of IBM's official documentation
Enhanced IBM Db2 Database Activity History and Security with DataSunrise
DataSunrise enhances IBM Db2 data audit capabilities by providing advanced features for real-time activity monitoring, comprehensive audit trails, and robust security policies. With its Database activity monitoring solution, organizations gain detailed analytics, proactive alerting, and support for compliance regulations, such as GDPR, HIPAA, and PCI DSS. The integration of DataSunrise allows for centralized management, automated compliance reporting, and advanced data protection through
Key Benefits of DataSunrise Integration
- Centralized Management: Monitor multiple databases from a single dashboard, streamlining oversight and reducing administrative overhead across your database infrastructure.
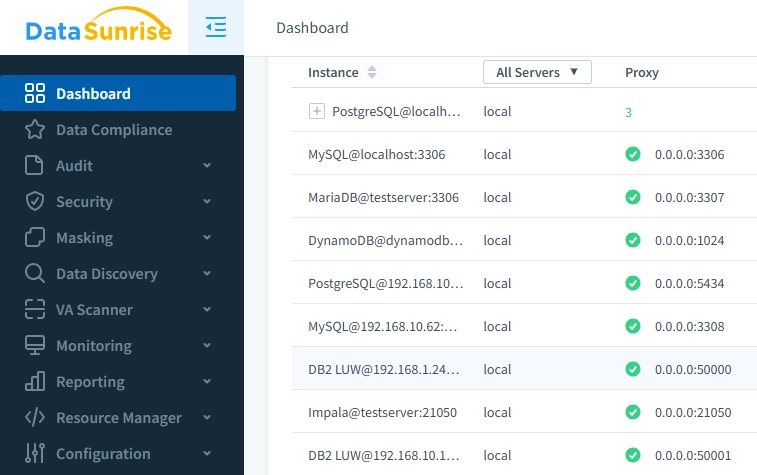
Dashboard Showing Multiple Different Database Connections in DataSunrise - Automated Reporting: Generate compliance reports automatically, saving time while ensuring consistent documentation for auditors and stakeholders.
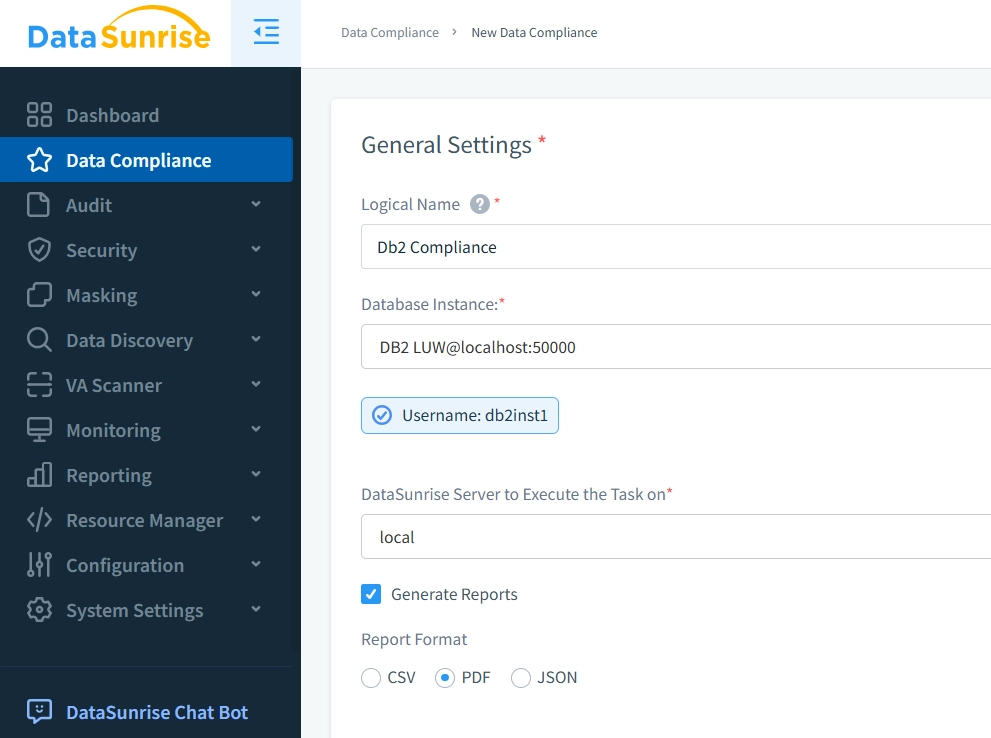
- Data Protection: Implement dynamic masking for sensitive information, which ensures data privacy without compromising application functionality or user experience.
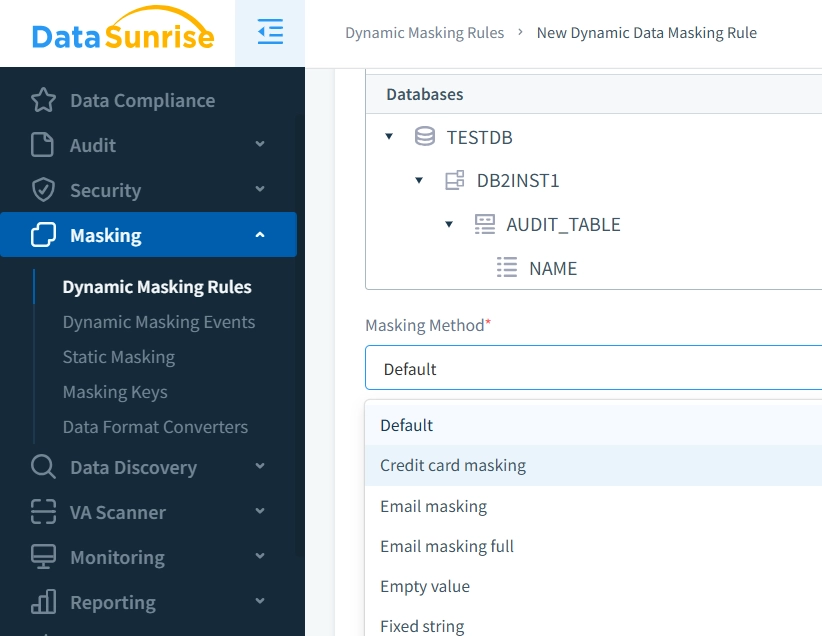
Additional Features: Beyond these capabilities, DataSunrise offers a wide range of advanced functionalities, including behavior analytics for proactive threat detection, robust access controls, dynamic security policies, and more—all designed to enhance database security and streamline compliance efforts.
Conclusion
Effective Db2 database monitoring may often require more just built-in capabilities. DataSunrise extends Db2's auditing features with centralized management, real-time alerting, and granular control, helping organizations maintain security and compliance efficiently.
DataSunrise integrates seamlessly with Db2, offering streamlined auditing and enhanced security through various deployment modes to accommodate different infrastructure needs.
Experience these capabilities firsthand by requesting a live demo to see how DataSunrise can enhance your database security and compliance.
