
Informix Data Activity History
Introduction
Understanding the importance of tracking Informix data activity history is crucial for organizations using this database. Moreover, monitoring your data activity history is vital for identifying potential threats and ensuring your organization meets legal and security requirements.
The need for robust database auditing has never been greater. Verizon’s 2024 report highlights frequent threats such as system intrusions, human errors, and social engineering, emphasizing the value of proactive database monitoring in protecting sensitive data.
IBM Informix simplifies the audit process with built-in tools that allow you to monitor activity, detect unauthorized access, and meet regulatory requirements efficiently. This guide provides a clear, step-by-step approach to setting up these capabilities.
Accessing Informix Data Activity History with Native Tools
To set up and view data activity history in IBM Informix, you need to enable auditing. Then, run test queries and analyze the audit logs. Below is a streamlined approach:
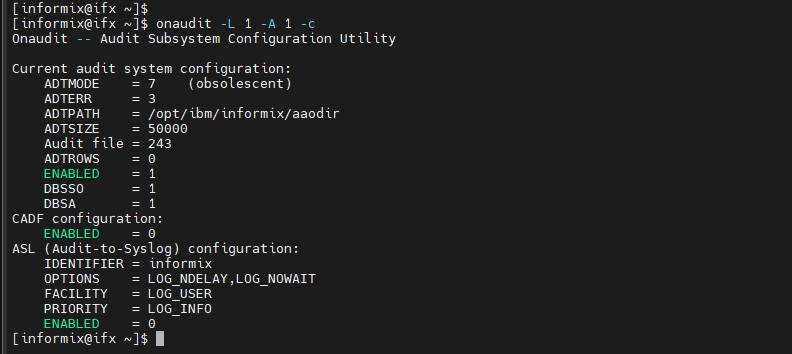
1. Enable Auditing for Informix Data Activity History
Activate Auditing:
To enable auditing, use the following commands:
onaudit -L 1 # Set the audit log mode
onaudit -A 1 # Enable auditing for the Informix admin group user
onaudit -c # Verify the current audit configuration
Alternatively, you can run a single command to achieve the same result:
onaudit -L 1 -A 1 -c
These commands activate auditing for administrative users and ensure that the audit system is functioning correctly.
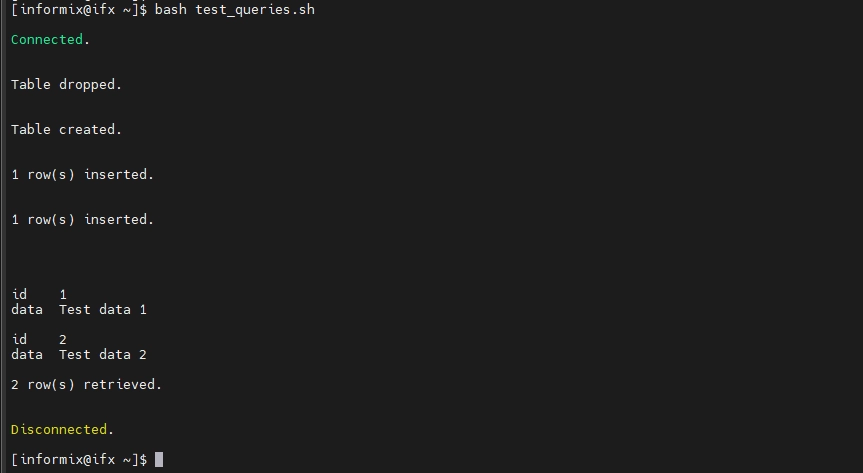
2. Perform Test Queries to Generate Informix Data Activity History
Run various queries to generate audit data. For example, you can use the following script:
#!/bin/bash
cat > test.sql <<EOF
CONNECT TO 'testdb@informix' USER 'informix' USING 'in4mix';
DROP TABLE IF EXISTS audit_test;
CREATE TABLE audit_test (id SERIAL PRIMARY KEY, data VARCHAR(255));
INSERT INTO audit_test (data) VALUES ('Test data 1');
INSERT INTO audit_test (data) VALUES ('Test data 2');
SELECT * FROM audit_test;
EOF
dbaccess - test.sql
rm test.sql
Additionally, you can also test unauthorized actions, such as attempting to log in with incorrect credentials, to ensure these events are captured in the audit logs as well.
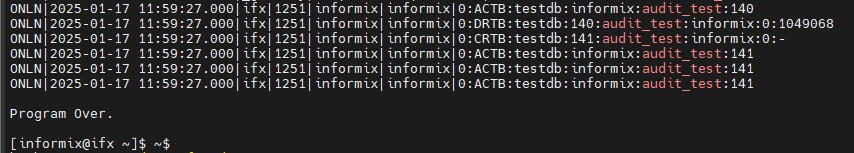
3.Analyze Informix Data Activity History Logs
1. View Logs:
Use the onshowaudit utility to read and interpret audit logs:
onshowaudit
This command retrieves the general audit log. You can apply filters to narrow the results and focus on specific activities or users.
2. Interpret Log Entries:
The audit logs contain various codes, such as ACTB (Access Table), that describe the actions captured during auditing. These entries provide details about executed queries, failed login attempts, and other database operations. For more information on audit codes and their meanings, refer to the official documentation page on onaudit event codes.
3. Enhance Logging Precision
Use audit masks to enable detailed logging for specific users or actions. For example:
onaudit -a -u admin_user -e ACTB
This command configures an audit mask for the user admin_user, enabling logging specifically for ACTB events (Access Table). By doing so, only table access activities performed by this user are recorded, ensuring precise and relevant audit trails without unnecessary noise.
For more details on specific commands or log analysis, you can refer to the IBM Informix Documentation.
Best Practices for Managing Informix Data Activity History
Archive and Rotate Logs:
Regularly manage audit logs to prevent storage overflow and maintain system performance.Secure the Logs:
Ensure audit logs are stored in a protected location to prevent unauthorized access or tampering.Optimize Audit Scope:
Avoid auditing unnecessary activities to reduce performance overhead and focus on critical actions.
DataSunrise: A Modern Approach to Informix Data Activity History
DataSunrise offers a robust solution that addresses the limitations of both native Informix tools and legacy systems. Its advanced architecture provides significant advantages tailored for modern data security needs:
Streamlined Management
The platform features a unified monitoring dashboard that simplifies oversight across multiple database instances, including Informix. With support for over 40 data storage platforms, this centralization reduces administrative complexity and improves response times to security events.
Advanced Data Masking Features
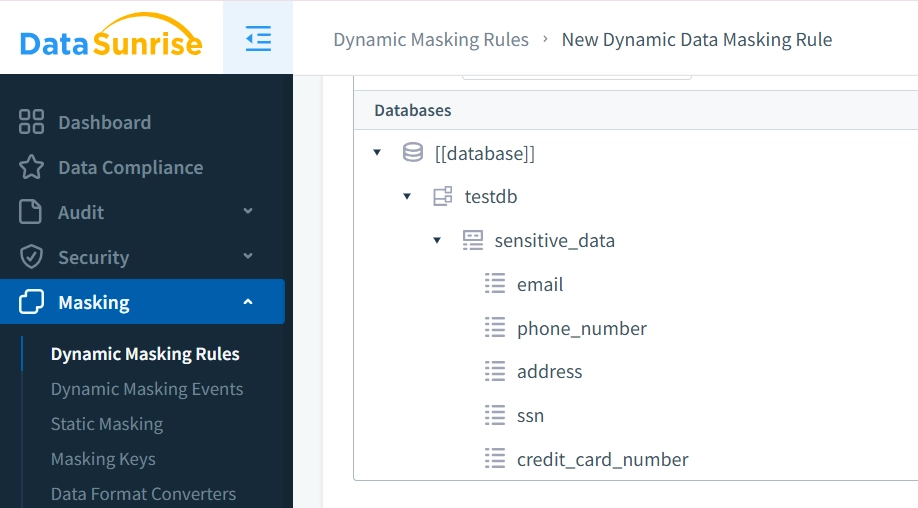
DataSunrise enhances Informix's security with dynamic data masking, ensuring sensitive data is protected in real-time. By adapting to user roles, access levels, and data filters, the platform maintains granular control over access without compromising usability for authorized users.
Comprehensive Compliance Framework
Organizations using Informix benefit from automated compliance monitoring and reporting for major standards like SOX, GDPR, HIPAA, and PCI DSS. Pre-configured templates and real-time monitoring simplify adherence to regulations by automatically tracking required metrics and generating compliance documentation. A centralized dashboard ensures instant alerts for violations, reducing manual effort and regulatory risks.
Additional Features
DataSunrise brings a suite of tools to optimize security, monitoring, and analytics for Informix environments. Notable features include:
- Real-Time Notifications: Instantly receive alerts for critical events to ensure timely responses.
- Behavior Analytics: Detect unusual patterns and identify potential threats using advanced analytics.
- LLM and ML Tools: Leverage machine learning and large language models to bolster security and improve monitoring capabilities.
Conclusion
While Informix provides basic native tracking features, modern environments demand more advanced solutions. DataSunrise delivers next-generation tools that scale with organizational needs. Its flexible deployment options and comprehensive audit features allow organizations to build a secure, compliant data infrastructure prepared for future challenges.
Ready to elevate your Informix data activity history tracking? Try our online demo today and see how advanced audit trail management can transform your data security.
