
Transforming Database Security with LLM, ML, NLP, and OCR Technologies
Introduction
As data breaches and cyber attacks become increasingly common, organizations are turning to advanced technologies like large language models (LLMs), machine learning (ML), natural language processing (NLP), and optical character recognition (OCR) to enhance their database security posture. These cutting-edge LLM and ML tools can automate key security tasks, detect suspicious user behavior, and discover sensitive data across both structured and unstructured databases.
In this article, we’ll explore how LLMs, ML, NLP and OCR are being used to revolutionize database security. We’ll look at real-world examples of these technologies in action and discuss the benefits they offer for protecting critical data assets. By the end, you’ll have a solid understanding of the role these advanced tools can play in a comprehensive database security strategy.
LLMs for Customer Experience Automation
One exciting application of large language models in database security is automating customer experience (CX) tasks. LLMs like GPT-4 have the ability to engage in human-like dialog, answer questions, and even assist with troubleshooting issues.
For example, DataSunrise offers an LLM-powered virtual assistant that can handle many common customer inquiries related to their database security products. When a customer has a question or encounters a problem, they can simply describe the issue in natural language. The LLM assistant then provides relevant information or guides the customer through step-by-step troubleshooting.
By automating frontend customer interactions, LLMs free up human staff to focus on higher-level security tasks. LLM-based CX automation can help database security vendors provide responsive 24/7 customer service in a cost-effective way. One case study by IBM found that a company using an LLM assistant was able to handle 80% of routine customer inquiries without human intervention.
DataSunrise has introduced CX automation into the UI itself, providing the same level of assistance on our website and in the DataSunrise Solution UI.
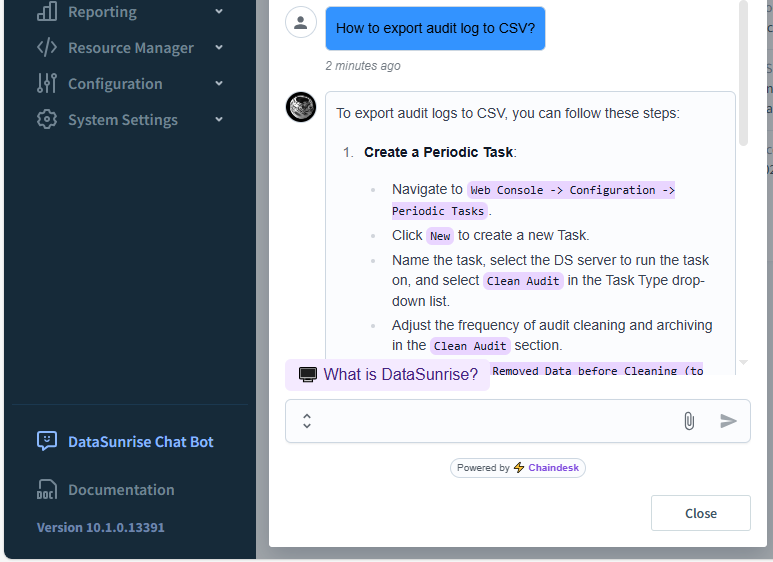
Figure 1 – DataSunrise Chat Bot is now available in UI.
DataSunrise Chat Bot is a GDPR-compliant feature. Its LLM temperature is set to 0, and its datastore contains all the documentation that comes with the software installation. In addition to the documentation, the chatbot’s datastore includes an extensive user Q&A base compiled by our support engineers.
The LLM is limited to the information from the datastore and a prompt. This is to ensure that the user can be confident that the answer doesn’t contain general or imaginary information on the topic.
ML for User Behavior Monitoring
Another key application area for advanced technologies in database security is monitoring user behavior for signs of malicious activity. Machine learning algorithms can be trained on historical access patterns to develop a baseline of normal behavior for each user. The ML model can then analyze user actions in real-time and flag any unusual or suspicious activities.
Behavior-based ML monitoring can detect issues like:
- Excessive failed login attempts that could indicate a brute force attack
- Large data downloads or exports outside a user’s normal patterns
- Accessing databases or tables not typically used by that individual
- Logging in from unfamiliar locations or devices
When DataSunrise detects suspicious behavior, the ML system can automatically alert security staff and even take proactive measures like locking the account in question. ML behavior monitoring acts as an always-on security guard, identifying and responding to database threats 24 hours a day.
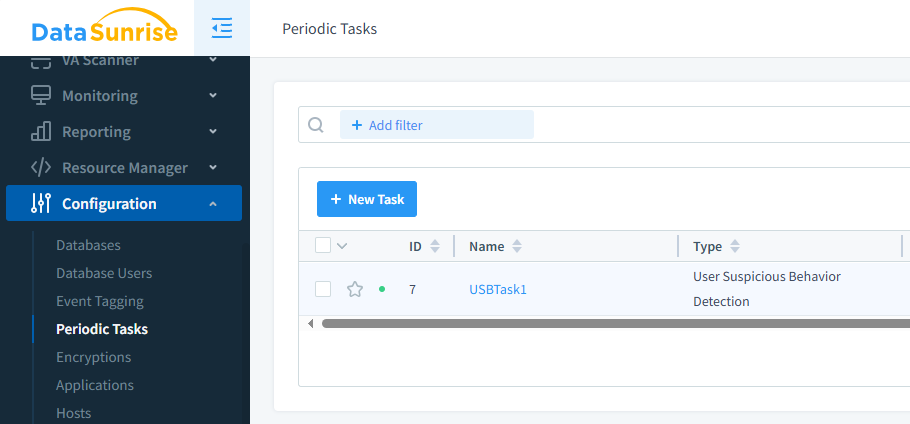
Figure 2 – User Suspicious Behavior Detection Task is based on NLP statistical models.
The growing attack surfaces and increasing complexity of cyber threats are compounded by a persistent shortage of cybersecurity professionals. To address the global shortfall of over 3 million cybersecurity experts, the workforce in this field would need to expand by approximately 89%. LLM and ML tools offer a potential solution to bridge this talent gap.
NLP for Complex Data Discovery
Discovering and classifying sensitive data is a crucial but often time-consuming part of database security and compliance. Organizations need to know where regulated information like personal data, financial details, and health records reside so that appropriate protections can be put in place.
This is where natural language processing comes in. NLP can parse and extract meaningful information from unstructured data sources like text fields, document stores, and log files. By understanding the context around data elements, NLP can accurately identify sensitive information that may be “hidden in plain sight.”
In real-world use case, a healthcare provider used NLP to scan a huge database of physician notes and patient records. The NLP tool was able to find instances of protected health information (PHI), enabling the provider to secure that data and meet HIPAA compliance requirements. Without NLP, it would have been nearly impossible to manually review such a massive volume of unstructured information.
DataSunrise’s NLP-powered data discovery scanner can search databases for 12 different types of personal information – names, addresses, ID numbers, and more. The NLP algorithms understand the semantics of the data, not just the syntax, so they can find sensitive details even if they aren’t perfectly formatted or labeled.
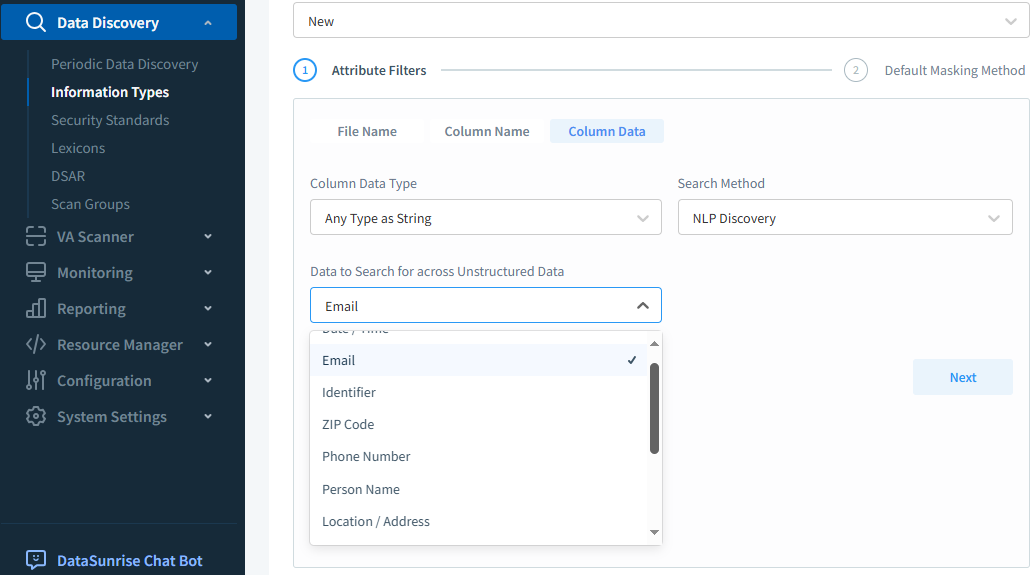
Figure 3 – NLP Discovery Search Method in the Information Type Attribute definition.
OCR for Securing Scanned Documents
Not all sensitive data originates in a digital format. Many organizations still rely on physical documents like scanned contracts, invoices, and forms that may contain regulated details. Securing these scanned documents requires first extracting text from images, which is where optical character recognition comes in.
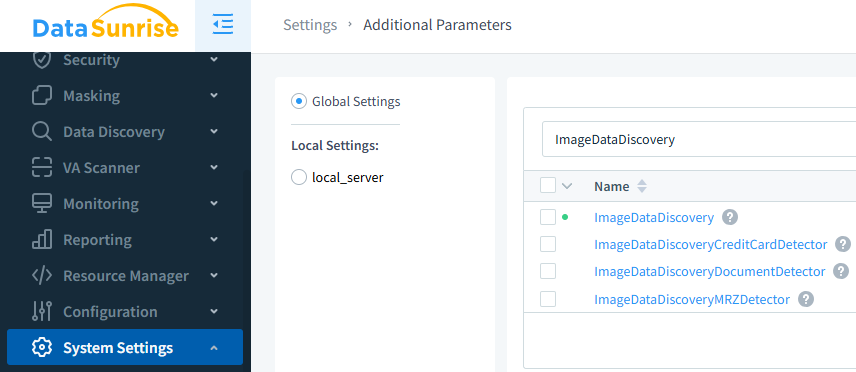
Figure 4 – Enabling OCR for data discovery in System Settings – Additional Parameters.
OCR tools analyze the patterns of pixels in an image to identify individual letters and words. Advanced OCR solutions use machine learning and computer vision to improve the accuracy of text extraction, even for low-quality or handwritten scans. Once we extracted the text, we can feed it into an NLP pipeline to discover any sensitive data the document contains.
DataSunrise has integrated multiple OCR technologies into its data security platform. In addition to classical ML-based OCR models, DataSunrise can leverage the OpenCV computer vision library for sophisticated image pre-processing. If users have highly complex documents, DataSunrise also supports the Amazon Textract OCR service for maximum accuracy.
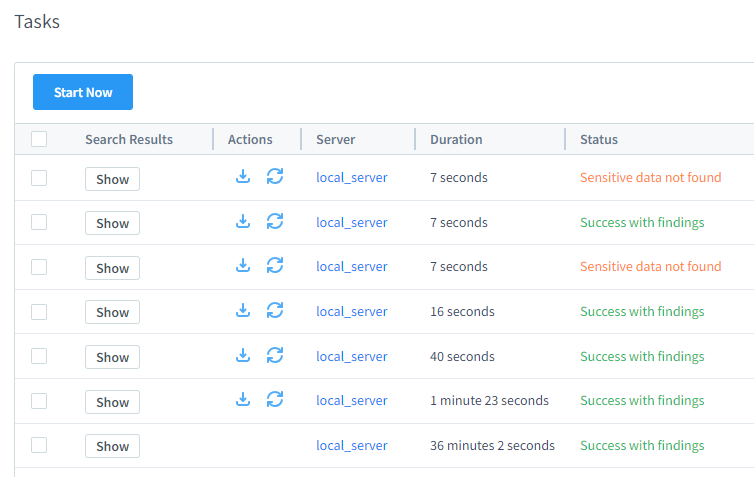
Figure 5 – OCR-based sensitive data discovery results.
For example, consider a bank that needs to secure a large volume of scanned loan applications stretching back several decades. By running these documents through DataSunrise’s OCR tool, the bank can extract key personal data fields. With this information identified, the user can process files as needed to comply with financial data protection laws.
NLP for Unstructured Data Masking
65 percent of all valued unstructured data is text. To prevent data leakages and to perform dynamic masking of the data that needs protection, DataSunrise offers NLP tools for unstructured data masking.
The Dynamic Masking rule setup for unstructured data is almost the same as for structured data, except for the Masking Method. This type of masking is extremely helpful when you don’t know the sensitive data format beforehand and you can’t simply search for regular expression matches throughout the entire file.
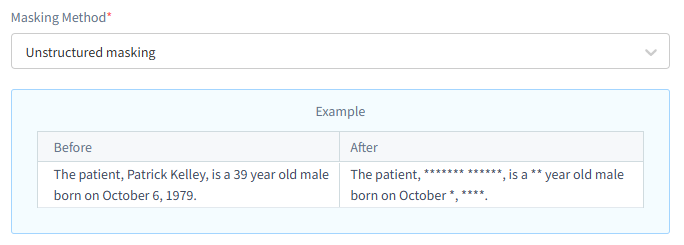
Figure 6 – Dynamic masking rule setup. You can see we selected the Unstructured masking method.
The Unstructured Masking method in DataSunrise supports various formats of unstructured data in the database as binary data (such as Word documents or simple txt files). When we access such unstructured data through the DataSunrise proxy port, the DataSunrise automatically masks sensitive parts.
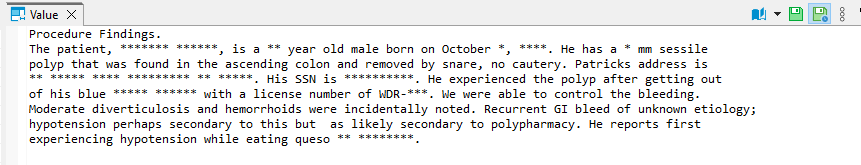
Picture 7 – DataSunrise masks the data as the user accesses it through the proxy port. Here we accessed the data with DBeaver software. Notice the asterisks instead all the sensitive parts.
Summary and Conclusion
As we’ve seen, large language models, machine learning, natural language processing, and optical character recognition are all playing a vital role in the future of database security. These LLM and ML tools allow organizations to:
- Automate customer support for more responsive service
- Detect malicious user behavior in real time
- Discover and classify sensitive data across structured and unstructured sources
- Secure regulated information lurking in scanned documents
While implementing these cutting-edge tools may seem daunting, platforms like DataSunrise are making them accessible for enterprises of all sizes. By combining multiple complementary technologies in one user-friendly interface, DataSunrise simplifies and streamlines database security operations. DataSunrise’s flexible and feature-rich tools can help any organization enhance data protection, ensure compliance, and guard against ever-evolving cyber threats.
For more information about how DataSunrise can leverage the power of LLM, ML, NLP, and OCR to safeguard your databases, please submit a request for an online demo at a time and date that suits you.
