Microsoft SQL Server Audit Log
Tracking changes and activity in your Microsoft SQL Server databases is essential when handling sensitive data. Whether you're monitoring for potential threats, meeting compliance standards, or simply ensuring accountability, the Microsoft SQL Server Audit Log offers detailed insights. SQL Server includes powerful native tools to help administrators trace queries, monitor user access, and log events systematically.
Before diving into audit techniques, it's helpful to review Microsoft's official resources:

Native Audit Capabilities in Microsoft SQL Server
Starting with SQL Server 2008, native auditing features became available, letting you create audit specifications directly in the database engine. With the Microsoft SQL Server native Audit Log, you can:
Track who accessed what, when, and how
Log schema changes and DML/DDL events
Output logs to files, the Windows Application log, or the Security log
This method helps enforce compliance regulations such as SOX, HIPAA, and PCI DSS while minimizing impact on server performance.
To get started:
-- Enable the Server Audit
ALTER SERVER AUDIT Audit_Activity_Log WITH (STATE = ON);
GO
--Create a Database Audit Specification
USE YourDatabaseName;
GO
CREATE DATABASE AUDIT SPECIFICATION Audit_Select_Statements FOR SERVER AUDIT Audit_Activity_Log
ADD (SELECT ON SCHEMA::dbo BY public),
ADD (INSERT ON SCHEMA::dbo BY public) WITH (STATE = ON);
GO
Audit logs are best analyzed using SSMS or PowerShell, though they can also be imported for further processing. To reduce overhead, be selective with what you log, and store output efficiently. More tips on storage strategies are discussed here: Database Performance for Audit Storage.
SQL Server also offers support for Dynamic Data Masking, which protects sensitive data during read operations but doesn't log access. For full tracking, combine masking with native audit logs and rule-based monitoring like Audit Rules.
Common Audit Use Cases
You might use Microsoft SQL Server Audit Logs for:
Detecting unusual login patterns
Tracing the source of unauthorized updates
Verifying that users follow access policies
Auditing supports both compliance and internal policies. Consider reading more about audit goals here: What is Data Audit Used For.
If you need to go beyond DML/DDL tracking and monitor real-time query behavior or detect threats, Microsoft's audit layer can be combined with external tools.
Microsoft SQL Server Audit Log with DataSunrise
DataSunrise enhances the SQL Server audit layer by adding real-time query monitoring, dynamic masking, and anomaly detection. It integrates smoothly with MSSQL in proxy or bridge mode.
To configure DataSunrise to work with SQL Server:
Install the platform and register the SQL Server instance.
Choose Reverse Proxy or Network Bridge deployment (Deployment Modes of DataSunrise)
Navigate to the Audit tab and define your rules (e.g., track
SELECTon tables with sensitive data)Activate logging and select your preferred log output: file, database, or external SIEM
Learn more here: Audit Logs
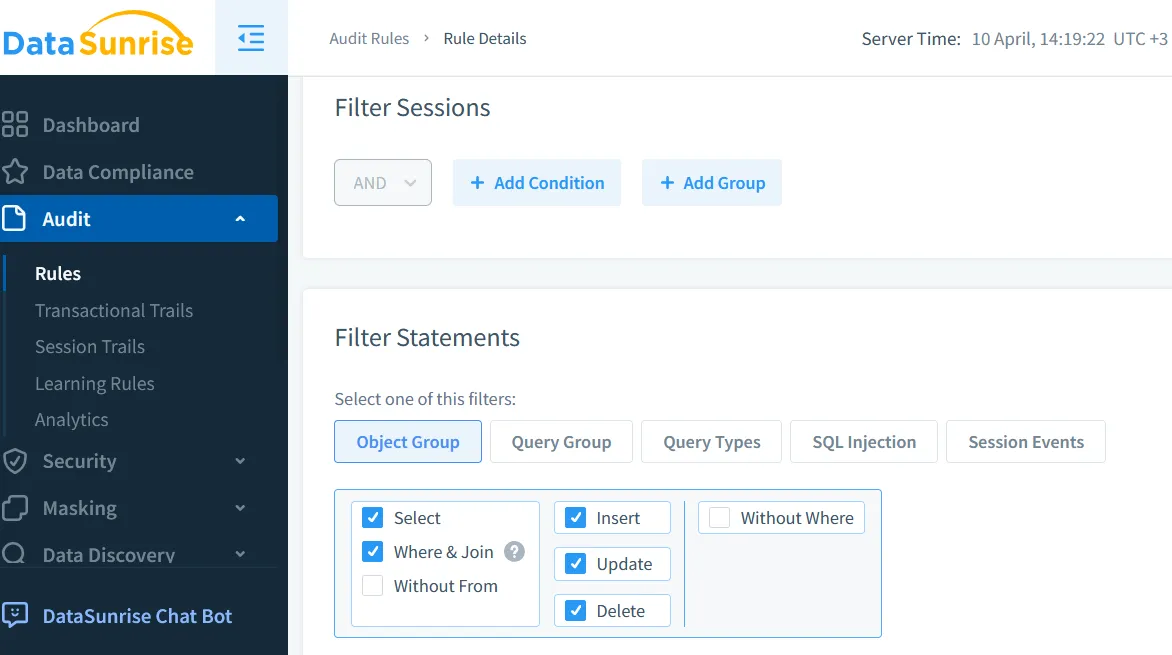
Sample audit rule:
The system uses learning mode to understand baseline user behavior and flag deviations. More on that here: Learning Rules and Audit.
Managing Audit Logs in DataSunrise
Once enabled, logs in DataSunrise can be sorted, filtered, and exported. You can generate detailed reports for audits or compliance checks using Report Generation Tools. These reports cover all critical user actions, which supports GDPR, HIPAA, and PCI DSS requirements (Data Compliance Regulations).
To support performance, archived logs can be compressed or offloaded. DataSunrise also integrates with third-party systems like MS Teams for alerts (MS Teams Notifications).
To secure log access, DataSunrise follows strict access control (Role-Based Access Controls) and protects audit storage, described here: Audit Storage.
Conclusion
The Microsoft SQL Server native Audit Log is powerful but needs careful configuration to avoid performance hits and log overflow. For sensitive or high-volume environments, DataSunrise adds valuable tools like masking, behavior analytics, and flexible audit rules.
Whether you’re looking to meet GDPR standards or want to secure internal operations, combining both native features and DataSunrise creates a thorough auditing strategy.
For a deeper look into security posture and audit strategies:
You can also try a live walkthrough via the DataSunrise Demo.
