
MySQL Audit Trail

Data breaches and unauthorized access can have devastating consequences for businesses. To protect sensitive information and maintain regulatory compliance, tracking database activities is essential. This is where a MySQL Audit Trail becomes invaluable. An audit trail records every change, access, and action within your MySQL database, providing a clear history of all interactions.
In this article, we’ll explore what an audit trail is, how you can create one in MySQL using both native tools and plugins, and how you can achieve enhanced auditing with DataSunrise.
What is an Audit Trail?
An audit trail is a detailed record of all activities performed within a database. It logs actions such as data insertion, updates, deletions, and user access. By maintaining this record, organizations can track changes, identify potential security breaches, and ensure regulatory compliance.
For businesses, maintaining an audit trail is not just about security – it’s also a requirement for compliance with regulations like GDPR, HIPAA, or SOX. An audit trail provides a way to demonstrate that proper controls are in place and that data is being handled responsibly. It also helps in forensic analysis, should an incident occur.
Moreover, audit trails are crucial for internal audits and reporting. By having a comprehensive record of database activities, organizations can conduct thorough reviews, identify patterns, and make informed decisions about future database policies and security measures. This not only helps in preventing potential breaches but also in optimizing database performance by understanding user behavior and system interactions.
Creating an Audit Trail in MySQL
Using MySQL’s Native Tools
MySQL offers built-in tools for setting up an audit trail, with the MySQL Enterprise Audit plugin being the most prominent. This plugin allows you to log a variety of database activities, ensuring a comprehensive audit trail.
Enabling the MySQL Enterprise Audit Plugin
To create an audit trail using MySQL’s native tools, you can enable the Enterprise Audit plugin. Here’s a simple example to get you started:
- Verify Installation: First, ensure the plugin is installed by running:
SHOW PLUGINS;
- Install the Plugin: If not installed, activate it using:
INSTALL PLUGIN audit_log SONAME 'audit_log.so';
- Configuration: Modify the MySQL configuration file (my.cnf) to specify which activities should be logged, such as connections, queries, or data changes.
Once set up, this plugin will automatically log the specified activities to a secure audit log file, creating a detailed audit trail in MySQL.
Creating an Audit Trail with Triggers
Another method to build an audit trail is by using triggers. Triggers are automated actions that execute in response to specific database events like INSERT, UPDATE, or DELETE. They are particularly useful for capturing detailed data changes.
Suppose you have a table called employees and want to log every update to this table:
- Create an Audit Log Table: First, create a table to store the audit logs:
CREATE TABLE audit_log ( id INT AUTO_INCREMENT PRIMARY KEY, action VARCHAR(255), old_data TEXT, new_data TEXT, action_time TIMESTAMP DEFAULT CURRENT_TIMESTAMP );
- Set Up the Trigger: Create a trigger that logs updates:
CREATE TRIGGER before_update_employee
BEFORE UPDATE ON employees
FOR EACH ROW
BEGIN
INSERT INTO audit_log (action, old_data, new_data)
VALUES ('UPDATE', OLD.name, NEW.name);
END;
This trigger will capture the old and new values whenever an update occurs, adding a detailed entry to the audit_log table.
Enhancing MySQL Audit Trails with DataSunrise
While MySQL’s native tools offer solid auditing capabilities, they may not meet all needs, especially in complex or high-security environments. DataSunrise provides a more comprehensive and user-friendly solution, designed to simplify the auditing process and offer additional features like data masking and real-time alerts.
DataSunrise integrates easily with MySQL, offering an intuitive interface to configure your audit trails. The process is straightforward, focusing on setting up what to monitor rather than dealing with complex installation procedures. To see DataSunrise in action, you can schedule a demo and ask questions to our tech support team.
Let’s say you want to monitor all SELECT queries on a sensitive table:
- Connect DataSunrise to MySQL. Add the database and wait until the proxy becomes active.
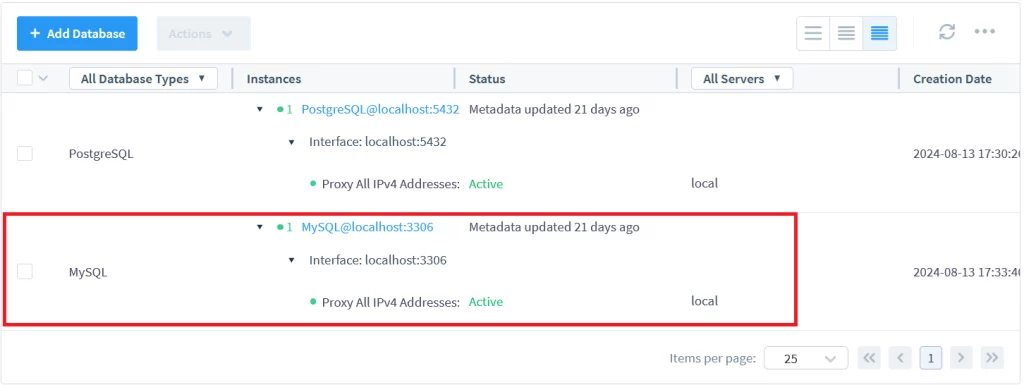
Audit is possible only when operations are held via DataSunrise proxy. Make sure to use the correct connection. See this article for additional information on setting up MySQL with DataSunrise for masking and audit.
- Create a New Rule: Define a rule that logs SELECT statements on the specific table.
Select checkboxes under the Filter Statements as below: Select, Where Join, Without Where.
Save the rule.
What Does an Audit Trail Look Like in DataSunrise?
To check the rule, connect to the database via proxy. For instance, you can use DBeaver application.
Then, execute the SQL query against your sensitive table. For instance:
select * from audit_example;
After SQL execution, you can check audit trails in the Data Sunrise application.
DataSunrise offers a visual dashboard where you can view and analyze the audit logs. Go to Audit – Transactional Trails.
The logs are presented in a clear format, showing details such as the type of action, the user involved, and the exact time it occurred.

Click on the entry ID for additional info. It would look as below:
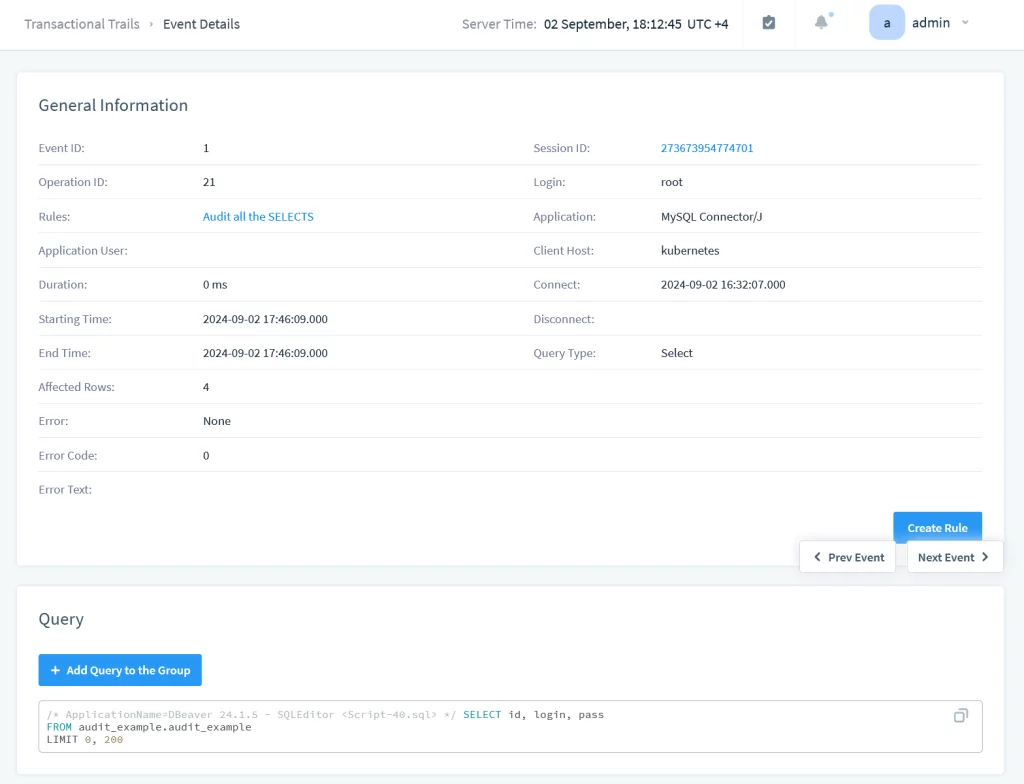
As you can see, all the information is accessible in one place. You don’t need to collect it from logs or set up complex triggers.
Conclusion
Creating a robust MySQL Audit Trail is essential for protecting your data and ensuring compliance with regulatory standards. Whether using MySQL’s native tools or opting for the enhanced features of DataSunrise, having a reliable audit trail helps you maintain control over your database environment.
DataSunrise offers a flexible, user-friendly solution for database security, including auditing, masking, and data discovery. To learn more about how DataSunrise can help secure your MySQL databases, visit our website and request an online demo.
