MySQL Compliance Management
Introduction
Data breaches are expensive. IBM’s 2023 report revealed the average cost of a breach reached $4.45 million. Organizations using MySQL must take compliance seriously to avoid these risks. From GDPR to SOX, businesses must secure sensitive data and prove they’re doing so. That’s where MySQL Compliance Management comes in.
This article explains how to meet compliance standards using native MySQL features and third-party tools like DataSunrise. We’ll cover built-in security, audit logging, SQL examples, and show how DataSunrise can simplify control over your compliance strategy.
Key Compliance Requirements for MySQL
MySQL databases often store personal, healthcare, or financial data. These regulations define how that data must be protected:
- GDPR requires access control, audit trails, and encryption for personal data.
- HIPAA demands safeguards for protected health information, including access monitoring.
- PCI DSS requires strong authentication, masked credit card data, and logging.
- SOX focuses on internal controls and audit trails for financial data.
Each framework mandates specific actions, but all share a need for strict access policies, encryption, and detailed audit logs.
Built-in Security and Auditing in MySQL
MySQL supports security at several levels: users, roles, logging, and encryption.
Role-Based Access Control (RBAC)
You can limit access by assigning roles:
CREATE ROLE auditor; GRANT SELECT ON sensitive_db.* TO auditor; GRANT auditor TO 'john'@'localhost'; SET DEFAULT ROLE auditor FOR 'john'@'localhost';
This restricts the user to read-only access across selected databases.
Logging User Activity
Turn on general query logs to track SQL activity:
SET GLOBAL general_log = 'ON'; SET GLOBAL log_output = 'FILE';
To check your logging status:
SHOW VARIABLES LIKE 'general_log%';
Binary Logs
Binary logs track changes and support rollback or audits:
SHOW BINARY LOGS;
You can extract logs for compliance reviews:
mysqlbinlog --start-datetime="2025-01-01 00:00:00" --stop-datetime="2025-01-31 23:59:59" /var/lib/mysql/binlog.000001
Encryption
To encrypt stored data, use Transparent Data Encryption (TDE) if supported:
ALTER TABLE users ENCRYPTION='Y';
For connections, MySQL supports SSL/TLS to encrypt traffic between the app and database.
Native Auditing with SQL and Enterprise Tools
MySQL Community Edition lacks a full audit log, but you can still track changes.
Manual Audit Table and Trigger
CREATE TABLE audit_log (
id INT AUTO_INCREMENT PRIMARY KEY,
user VARCHAR(100),
action_type VARCHAR(50),
old_data TEXT,
new_data TEXT,
change_time TIMESTAMP DEFAULT CURRENT_TIMESTAMP
);
CREATE TRIGGER before_update_customers
BEFORE UPDATE ON customers
FOR EACH ROW
INSERT INTO audit_log (user, action_type, old_data, new_data)
VALUES (CURRENT_USER(), 'UPDATE',
CONCAT('Email: ', OLD.email),
CONCAT('Email: ', NEW.email));
This tracks changes to customer emails for compliance purposes.
MySQL Enterprise Audit Plugin
In MySQL Enterprise Edition:
INSTALL PLUGIN audit_log SONAME 'audit_log.so'; SET GLOBAL audit_log_policy = 'ALL';
This logs all access in structured XML format. Learn more on MySQL Audit Log.
Using DataSunrise to Enhance MySQL Compliance
Native tools are good, but DataSunrise offers more granularity and flexibility. DataSunrise helps automate data discovery, dynamic masking, and audit reporting across hybrid environments.
Creating a DataSunrise Instance
Assuming DataSunrise is installed:
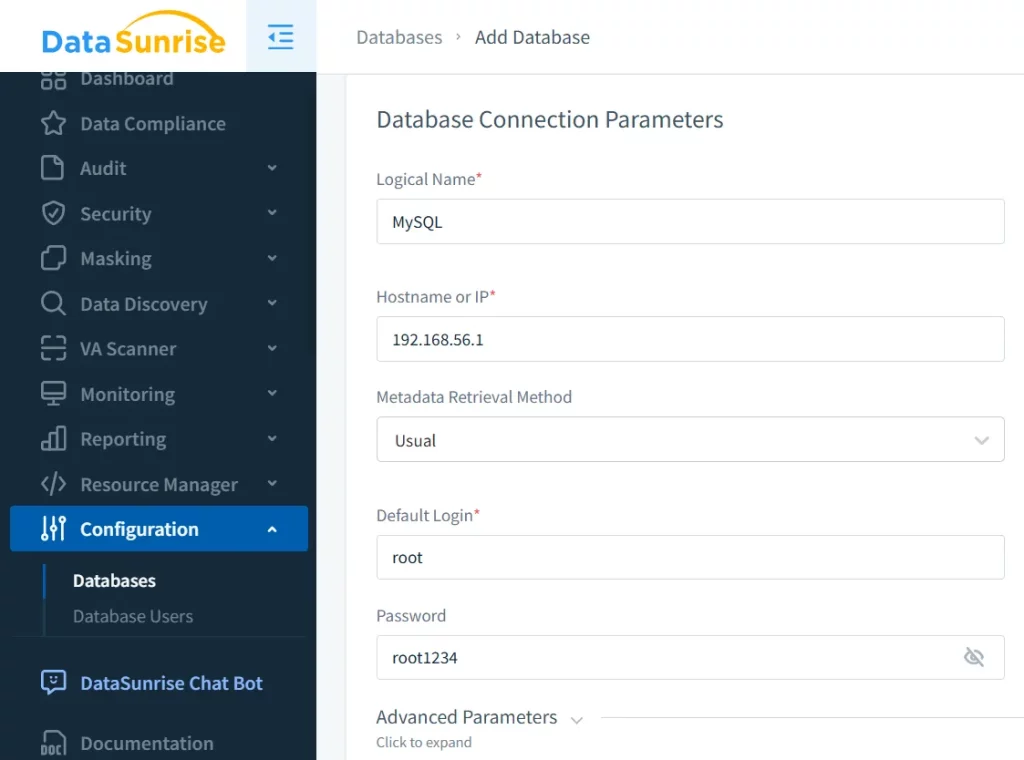
Now your MySQL instance is under centralized compliance management.
Viewing Dynamically Masked Data
DataSunrise applies dynamic masking rules to sensitive data. For example:
| id | name | |
|---|---|---|
| 1 | Alice Johnson | ali***@***.com |
| 2 | Bob Smith | bob***@***.com |
Unauthorized or untrusted users only see masked output. Learn about dynamic masking.
Benefits of Using DataSunrise’s Security Suite
With DataSunrise, you gain:
- Centralized Policy Management for masking and auditing.
- Real-Time Monitoring of user activity.
- Autonomous Compliance Manager that aligns with GDPR, HIPAA, PCI DSS, and SOX.
- Audit-Ready Reporting for inspections or breach investigations.
You can also define automatic masking policies for all connected environments using the unified interface.
Conclusion
MySQL Compliance Management is more than a checkbox—it’s a structured process of limiting access, tracking changes, and safeguarding sensitive data. Built-in features like RBAC, binary logs, and SQL triggers form the foundation. But for full-spectrum visibility, dynamic masking, and centralized control, DataSunrise fills the gap.
To explore how DataSunrise can enhance your compliance posture, book a demo or download the tool to explore it yourself.
