MySQL Data Compliance Automation
Introduction
A data breach costs more than just money—it damages trust. According to IBM, the average cost of a breach hit $4.45 million in 2023. For companies using MySQL, regulatory compliance isn’t optional. It’s essential. Whether it’s GDPR, HIPAA, PCI DSS, or SOX, businesses must protect sensitive data and prove that protection. That’s where MySQL Data Compliance Automation becomes crucial.
In this article, we’ll explore the built-in features of MySQL that support compliance, from access control to logging. We’ll also show how tools like DataSunrise can take security and automation to the next level.
Key Compliance Requirements for MySQL
MySQL databases often hold personal, financial, or health data. Here’s how key regulations apply:
- GDPR: Enforces encryption, data access control, and the right to audit trails.
- HIPAA: Demands strict protection of health records, with traceable user access.
- PCI DSS: Requires encrypted storage, masked payment info, and detailed logs.
- SOX: Calls for internal controls and financial data audit logs.
All require security best practices—limited access, encryption, and consistent logging.
Built-in Security and Auditing in MySQL
MySQL offers several built-in tools that support autonomous compliance in MySQL.
Role-Based Access Control (RBAC)
Limit access using roles:
CREATE ROLE auditor; GRANT SELECT ON finance_db.* TO auditor; GRANT auditor TO 'jane'@'localhost'; SET DEFAULT ROLE auditor FOR 'jane'@'localhost';
This setup restricts Jane’s access to read-only operations in `finance_db`. More on RBAC
General Query Logging
Enable activity tracking:
SET GLOBAL general_log = 'ON'; SET GLOBAL log_output = 'FILE';
Check log status:
SHOW VARIABLES LIKE 'general_log%';
Table Output:
| Variable | Value |
|---|---|
| general_log | ON |
| log_output | FILE |
This creates a real-time record of all SQL queries. MySQL logging details
Binary Logging for Audit and Rollback
Binary logs store data-change events:
SHOW BINARY LOGS;
Table Output (Example):
| Log File | File Size |
|---|---|
| binlog.000001 | 134217728 |
| binlog.000002 | 52428800 |
You can extract audit trails:
mysqlbinlog --start-datetime="2025-01-01 00:00:00" --stop-datetime="2025-01-31 23:59:59" /var/lib/mysql/binlog.000001
Extracted Entry Example:
| Date/Time | User | Event | SQL Statement |
|---|---|---|---|
| 2025-01-15 10:32:01 | jane@localhost | Query | UPDATE employees SET salary = 70000 WHERE id = 3; |
Useful for recovery and audit reviews.
Transparent Data Encryption (TDE)
Encrypt at rest:
ALTER TABLE employees ENCRYPTION='Y';
And for transit, use SSL/TLS between clients and the server.
Native Auditing: SQL Logs, Triggers, and Enterprise Features
Manual Auditing with Triggers
Create a basic audit log:
CREATE TABLE audit_log (
id INT AUTO_INCREMENT PRIMARY KEY,
user VARCHAR(100),
action_type VARCHAR(50),
old_data TEXT,
new_data TEXT,
change_time TIMESTAMP DEFAULT CURRENT_TIMESTAMP
);
CREATE TRIGGER before_update_employees
BEFORE UPDATE ON employees
FOR EACH ROW
INSERT INTO audit_log (user, action_type, old_data, new_data)
VALUES (CURRENT_USER(), 'UPDATE',
CONCAT('Salary: ', OLD.salary),
CONCAT('Salary: ', NEW.salary));
Table Output (Example Entry):
| id | user | action_type | old_data | new_data | change_time |
|---|---|---|---|---|---|
| 1 | jane@localhost | UPDATE | Salary: 65000 | Salary: 70000 | 2025-01-15 10:32:01 |
Enterprise-Grade Auditing
If you’re using MySQL Enterprise Edition:
INSTALL PLUGIN audit_log SONAME 'audit_log.so'; SET GLOBAL audit_log_policy = 'ALL';
This logs detailed activity in XML format for auditors. Learn more about MySQL audit plugin
Using DataSunrise for MySQL Data Compliance Automation
DataSunrise allows you to define audit rules based on user roles, IPs, query types, or even behavior anomalies. You can monitor specific tables (e.g., salary, payments) and set granular conditions for logging.
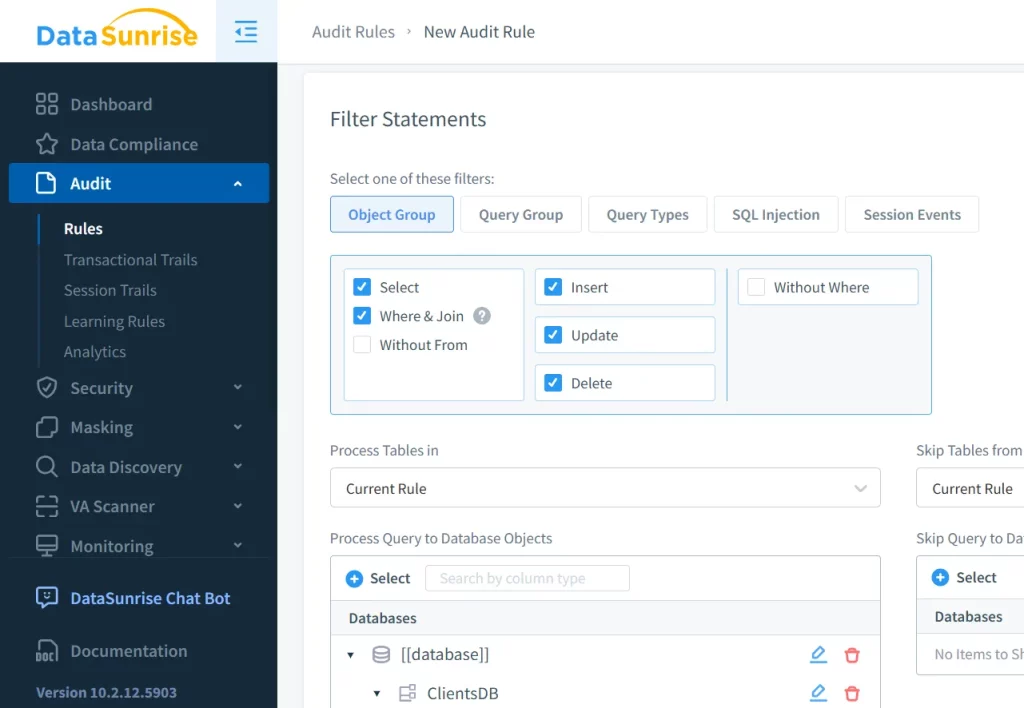
Once enabled, each action—such as an UPDATE to a sensitive table—is recorded with full metadata: user, time, query, and before/after values.
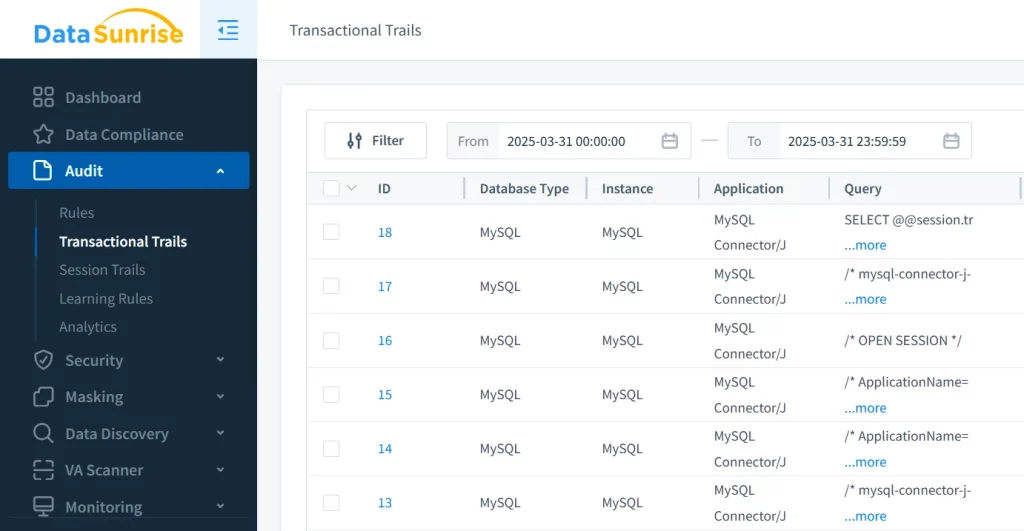
Managing Dynamic Masking Rules
Beyond masking data on output, DataSunrise provides a visual masking rule editor. You can define who sees what, how it’s masked, and under what conditions.
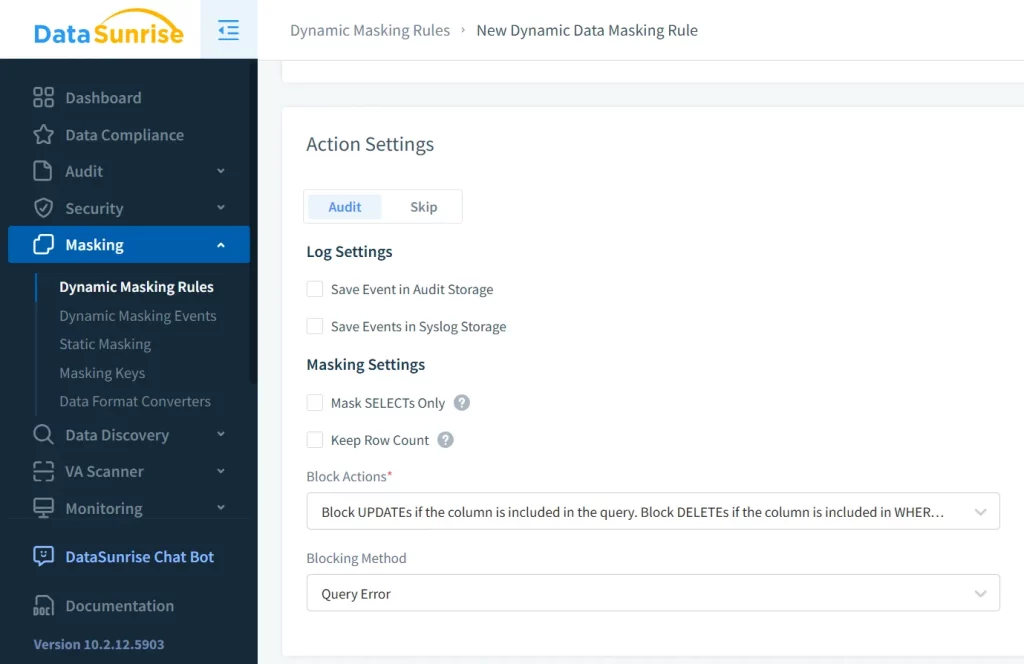
This ensures sensitive data—like emails, SSNs, or credit cards—is hidden from unauthorized users without breaking app functionality.
Why Use DataSunrise for Autonomous Compliance in MySQL?
DataSunrise automates what native MySQL tools can’t:
- Auto-Discovery & Classification: Identify sensitive fields across tables, file systems, and cloud storage.
- No-Code Policy Automation: Create masking, audit, and alerting rules using an intuitive UI.
- Autonomous Compliance Manager: Stay aligned with evolving standards like GDPR, HIPAA, PCI DSS, and SOX.
- Real-Time Threat Detection: Leverage UEBA to detect and respond to abnormal activity.
Benefits of Full MySQL Data Compliance Automation
- Centralized Control: Manage masking, auditing, and security from one platform.
- Streamlined Audits: Generate audit-ready reports quickly.
- Reduced Overhead: No manual policy setup or tuning.
- Hybrid-Ready: Works across on-premises, cloud, and multi-platform environments.
- Rapid Deployment: Non-intrusive setup—proxy, sniffer, or native log mode.
Conclusion
Compliance in MySQL isn’t just about checking boxes. It’s about consistently protecting data and proving it. Native MySQL tools—RBAC, encryption, binary logs—lay the groundwork. But true MySQL Data Compliance Automation needs more.
With DataSunrise, you get a zero-touch platform for masking, audit, behavior analytics, and reporting. It’s built for hybrid environments and evolving regulations.
Explore the full solution by booking a demo or downloading DataSunrise. Take the next step toward centralized, secure, and automated compliance.
