NLP, LLM & ML Data Compliance Tools for MySQL
Introduction
Every 39 seconds, a cyberattack targets someone online. For businesses using MySQL, storing sensitive personal or financial data without proper compliance tools can lead to massive breaches—and serious penalties. Regulations like GDPR, HIPAA, PCI DSS, and SOX demand strict data control, especially when AI systems such as NLP, LLMs, and ML models interact with databases.
In this article, we’ll explore how native MySQL features and third-party solutions like DataSunrise help enforce data protection. You’ll see SQL examples, learn to set up dynamic masking, and discover how to achieve Autonomous Compliance in MySQL using advanced ML-driven security tools.
Key Compliance Requirements for MySQL
MySQL databases often store personal, health, or payment data. Here’s how major regulations apply:
- GDPR: Requires encryption, audit trails, and access controls to protect personal data of EU residents.
- HIPAA: Enforces strict controls over protected health information (PHI), including logging and user tracking.
- PCI DSS: Protects payment data using masked fields, encryption, and real-time auditing.
- SOX: Requires full audit trails and accountability over financial record changes.
All of these frameworks demand limited access, encrypted storage, and logged activity. AI systems built with NLP or LLMs must respect these boundaries too—especially when ingesting or querying database content.
Built-in Security and Auditing in MySQL
Role-Based Access Control (RBAC)
Limit access using roles and privileges:
CREATE ROLE readonly_user; GRANT SELECT ON employees.* TO readonly_user; GRANT readonly_user TO 'ml_engine'@'localhost'; SET DEFAULT ROLE readonly_user FOR 'ml_engine'@'localhost';
Table Output:
| Role | User | Privileges |
|---|---|---|
| readonly_user | ml_engine@localhost | SELECT |
This ensures your ML app reads data without modifying it.
Logging SQL Activity
To record SQL queries:
SET GLOBAL general_log = 'ON'; SET GLOBAL log_output = 'FILE'; SHOW VARIABLES LIKE 'general_log%';
Table Output:
| Variable Name | Value |
|---|---|
| general_log | ON |
| log_output | FILE |
Logs are stored as text and help detect misuse or overreach by AI queries. See the MySQL query log guide for full configuration options.
Binary Logs for Audit Trail
MySQL’s binary logs support rollback and change monitoring:
SHOW BINARY LOGS;
Table Output:
| Log File | File Size |
|---|---|
| binlog.000001 | 587642 |
| binlog.000002 | 712398 |
mysqlbinlog --start-datetime="2025-03-01 00:00:00" \ --stop-datetime="2025-03-31 23:59:59" /var/lib/mysql/binlog.000001
Example Output:
| Event Time | Action | Query |
|---|---|---|
| 2025-03-02 09:30:12 | UPDATE | UPDATE employees SET salary = 75000 WHERE id = 3; |
| 2025-03-15 14:11:05 | INSERT | INSERT INTO customers (name) VALUES (‘Jane Doe’); |
Data Encryption
Encrypt tables to secure data at rest:
ALTER TABLE patients ENCRYPTION='Y';
Table Output:
| Table Name | Encryption |
|---|---|
| patients | YES |
Use SSL/TLS to secure connections between apps, LLM pipelines, and the database. For full setup instructions, refer to MySQL encrypted connections.
Native MySQL Auditing with Triggers and Plugins
Manual Audit Table with Trigger
Track data changes with SQL:
CREATE TABLE audit_log (
id INT AUTO_INCREMENT PRIMARY KEY,
user VARCHAR(100),
action_type VARCHAR(50),
old_data TEXT,
new_data TEXT,
change_time TIMESTAMP DEFAULT CURRENT_TIMESTAMP
);
CREATE TRIGGER before_update_salary
BEFORE UPDATE ON employees
FOR EACH ROW
INSERT INTO audit_log (user, action_type, old_data, new_data)
VALUES (CURRENT_USER(), 'UPDATE',
CONCAT('Salary: ', OLD.salary),
CONCAT('Salary: ', NEW.salary));
Table Output (Sample Audit Log):
| id | user | action_type | old_data | new_data | change_time |
|---|---|---|---|---|---|
| 1 | root@localhost | UPDATE | Salary: 70000 | Salary: 75000 | 2025-03-15 12:00:00 |
This is a lightweight way to monitor AI model updates in production databases.
MySQL Enterprise Audit Plugin
If you’re using MySQL Enterprise Edition:
INSTALL PLUGIN audit_log SONAME 'audit_log.so'; SET GLOBAL audit_log_policy = 'ALL';
Table Output (Audit Plugin Log in XML):
| Event Type | User | Action | Time |
|---|---|---|---|
| CONNECT | ml_engine | ALLOW | 2025-03-10 09:01:12 |
| QUERY | ml_engine | SELECT | 2025-03-10 09:01:15 |
This enables structured XML logs, helpful for forensic and compliance reviews. Learn more
NLP, LLM & ML Data Compliance Tools for MySQL Using DataSunrise
MySQL’s native features provide a good foundation. But managing AI, LLM, and ML integrations securely at scale calls for automation. That’s where DataSunrise steps in—with zero-touch compliance, autonomous policy enforcement, and ML-powered audit tools.
View masking in action: Dynamic Masking in DataSunrise
Benefits of DataSunrise for LLM, ML, and NLP Use Cases
Autonomous Compliance Manager
- Auto-Discovery & Classification of sensitive fields across SQL, JSON, documents, and OCR images.
- No-Code Policy Automation to define rules for audit, masking, and access control.
- ML Audit Rules adapt to user behavior and flag suspicious AI activity.
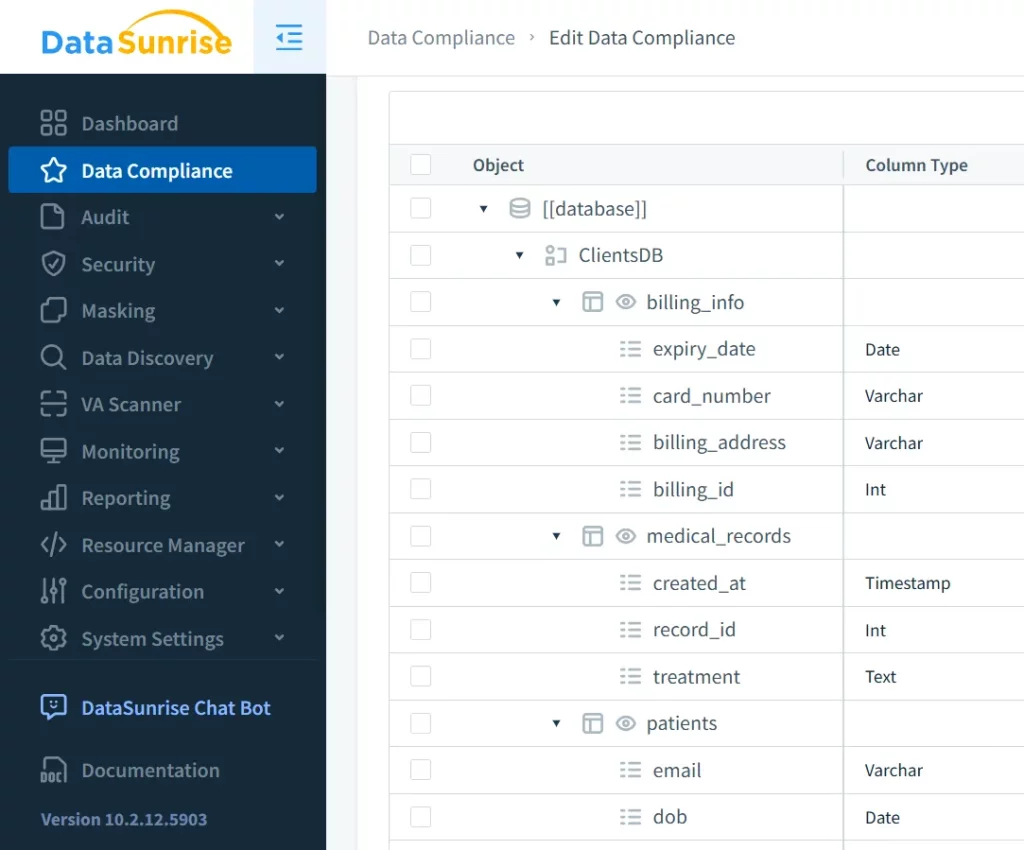
Centralized Policy Control
- Unified dashboard to control all masking and auditing rules.
- Compatible with over 40 platforms and cloud-native databases.
- Works in proxy, sniffer, or native log mode with no downtime.
Real-Time Anomaly Detection
- Built-in UEBA (User & Entity Behavior Analytics) detects outliers in AI queries.
- Flags behavior outside normal NLP/ML workflows.
Why Choose DataSunrise for Autonomous Compliance in MySQL?
- Autonomous Policy Alignment with GDPR, HIPAA, PCI DSS, and SOX.
- Streamlined Compliance Workflows for faster audits and less overhead.
- Cross-Platform Visibility from SQL to unstructured file systems.
- Real-Time Masking & Monitoring of LLM and NLP-driven data flows.
- Audit-Ready Reporting in clicks—no scripting needed.
Explore how DataSunrise’s Compliance Suite simplifies MySQL security and gives you confidence in AI-driven environments.
Conclusion
NLP, LLM & ML Data Compliance Tools for MySQL are no longer optional. Whether you’re training an LLM on structured data or running sentiment analysis from a database stream, compliance must be part of your data strategy.
Native MySQL features like roles, logs, and encryption lay the groundwork. But tools like DataSunrise bring the automation, real-time protection, and centralized visibility that today’s AI workflows demand.
Visit our demo page or download the platform to see how it supports Autonomous Compliance in MySQL—from discovery to masking to audit-ready reporting.
