
Oracle Audit Trail

Introduction to Audit Trail
In today’s increasingly complex IT environments, database security and compliance are more critical than ever. Oracle, a leader in database management systems, provides a robust suite of tools to monitor, track, and audit user activities within its databases. This article will explore some of these tools, focusing on Oracle’s auditing mechanisms and examining third-party solutions that can further enhance your auditing system.
What is an Audit Trail?
A database audit involves gathering useful information about activities within a target database through its audit logs. Auditing can improve security, provide valuable insights, and enhance the database administration experience. The more advanced the auditing system, the more detailed and precise the data captured. However, complexity comes at a cost. In some cases, a regular database audit may not be enough to ensure solid security. For instance, Oracle database has an advanced audit system, but its complexity can make operations more challenging. The audit trail technique simplifies data extraction and makes auditing more manageable. It can be implemented in various ways, including real-time auditing, where audit logs are queried at regular intervals.
Oracle Audit Trail: Enhanced Security
The Oracle Audit Trail plays a pivotal role in maintaining database security and ensuring regulatory compliance. It enables organizations to:
- Track user activity: Audit logs can track who did what, when, and where. This visibility is crucial for identifying potential threats or unauthorized actions.
- Detect security breaches: By reviewing audit logs, administrators can quickly spot unusual or suspicious activity, such as unauthorized access or privilege escalation attempts.
- Ensure compliance with regulations: Many industries are subject to strict data protection regulations, such as GDPR, HIPAA, and PCI DSS. Oracle’s auditing features help organizations meet these regulatory requirements by recording and storing audit logs that demonstrate compliance.
- Prevent data manipulation: The Oracle Audit Trail logs actions such as insertions, deletions, and updates to critical data, making it easier to prevent and identify unauthorized changes.
Types of Auditing in Oracle and How to Implement Them
Oracle provides several auditing mechanisms to help administrators monitor database activities and ensure compliance with security and regulatory requirements. Below are the key types of auditing available, along with steps to enable them:
1. Standard Auditing
Standard auditing is the traditional method used in Oracle to track specific database events, such as logins, object accesses, and schema changes. While simple to implement, it may not provide the granularity required for advanced security or compliance needs.
Enabling Standard Auditing:
To enable standard auditing, use the following SQL command:
ALTER SYSTEM SET audit_trail = DB, EXTENDED SCOPE = SPFILE;
SHUTDOWN IMMEDIATE;
STARTUP;- This command configures Oracle to log database activities within the database itself.
- The
EXTENDEDoption ensures that both SQL statements and the bind variables used in SQL queries are captured in the audit logs.
After executing queries through any suitable database manager (e.g., DBeaver), you can query the DBA_AUDIT_TRAIL to view the logs.
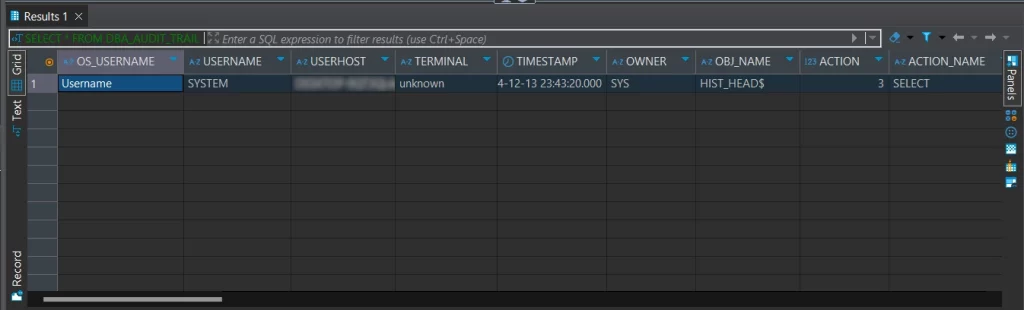
2. Fine-Grained Auditing (FGA)
Fine-Grained Auditing (FGA) allows more specific and tailored auditing. It enables you to monitor access to particular data based on conditions (e.g., auditing only accesses to sensitive information, such as high-value transactions). FGA reduces the size of audit logs by focusing on high-risk activities, providing more detailed and efficient auditing.
Enabling Fine-Grained Auditing:
To enable FGA on a specific table, such as auditing access to high-salary employees, use the following code:
BEGIN
DBMS_FGA.add_policy(
object_schema => 'system',
object_name => 'EMPLOYEES',
policy_name => 'audit_emp_access',
audit_condition => 'SALARY > 100000',
audit_column => 'SALARY',
handler_schema => NULL,
handler_module => NULL,
enable => TRUE
);
END;- This command creates a policy on the
EMPLOYEEStable, auditing any access where theSALARYexceeds $100,000. - The
audit_conditionfilters what qualifies for auditing, ensuring that only relevant activities are logged.
After executing statements that meet this condition, you can view the results in the DBA_FGA_AUDIT_TRAIL table.
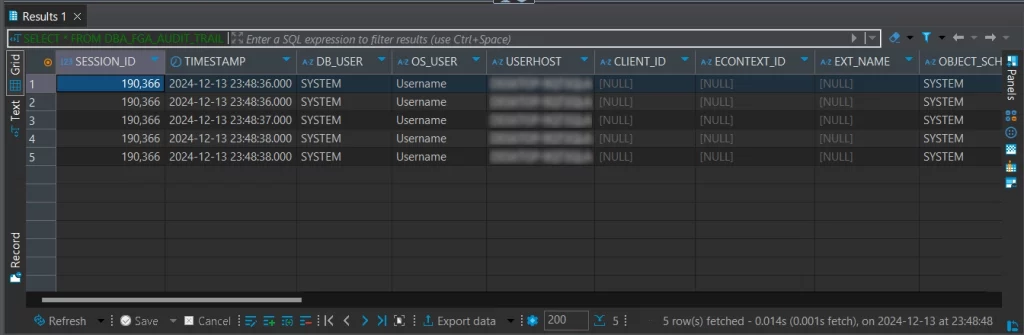
3. Operating System Auditing (OS Auditing)
While Oracle’s database-level auditing captures a wide range of activities, OS Auditing allows administrators to track activities at the operating system level, such as file system access and network connections. This can be especially useful when correlating database and system-level events for enhanced security monitoring.
Enabling OS Auditing:
To enable OS-level auditing, set the audit_trail parameter to OS:
ALTER SYSTEM SET audit_trail = OS SCOPE = SPFILE;
SHUTDOWN IMMEDIATE;
STARTUP;- This configuration sends audit records to the operating system’s audit trail, which can then be reviewed alongside system-level logs (e.g., syslog on Linux or Windows Event Logs).
This feature is particularly useful when consolidating system and database-level audit information for comprehensive security auditing.
With these auditing methods in place, Oracle provides a flexible and robust way to monitor user activity, track suspicious behavior, and ensure compliance with regulatory standards.
Enhancing Oracle Auditing with DataSunrise’s Real-Time Monitoring
While Oracle’s built-in auditing capabilities are robust, some organizations may need more advanced features such as real-time monitoring, reporting, and alerting. Third-party tools like DataSunrise offer enhanced auditing solutions for Oracle databases. These tools provide features such as:
- Real-Time Auditing: Track and respond to suspicious activities as they occur.
- Centralized Reporting: Aggregate logs from multiple databases into a single interface for easier analysis.
- Alerting: Set up custom alerts for specific database activities, such as unauthorized login attempts or schema changes.
DataSunrise’s auditing tools extend Oracle’s native features, offering more flexibility and control for database security. You can easily integrate your Oracle Database instance with DataSunrise:
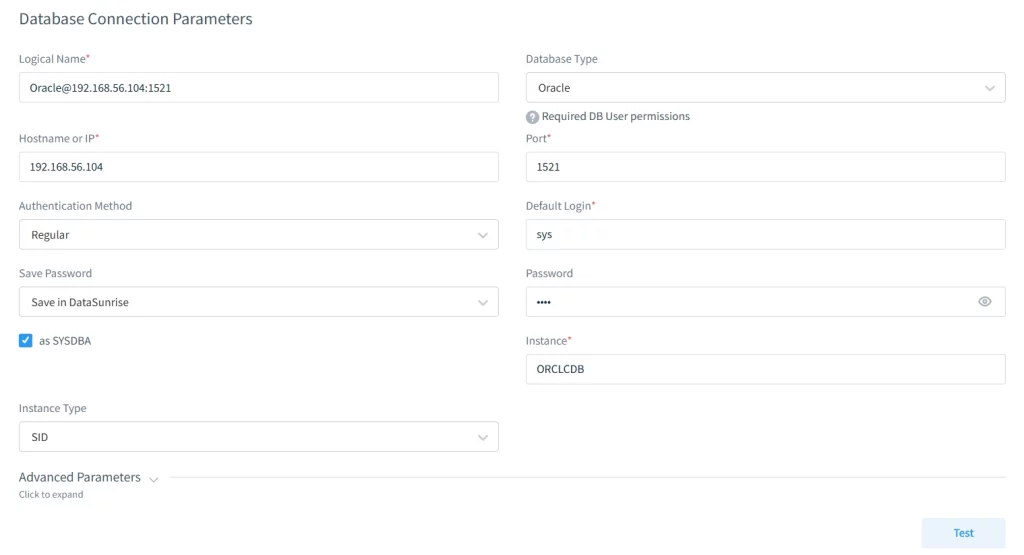
Once integrated, you can interact with DataSunrise’s powerful rule-based Audit Trail feature for Oracle Database. This system acts as a database proxy, filtering all queries and sessions. For example, you can configure logging for every system user action on the EMPLOYEES database, as well as in Fine-Grained audits:
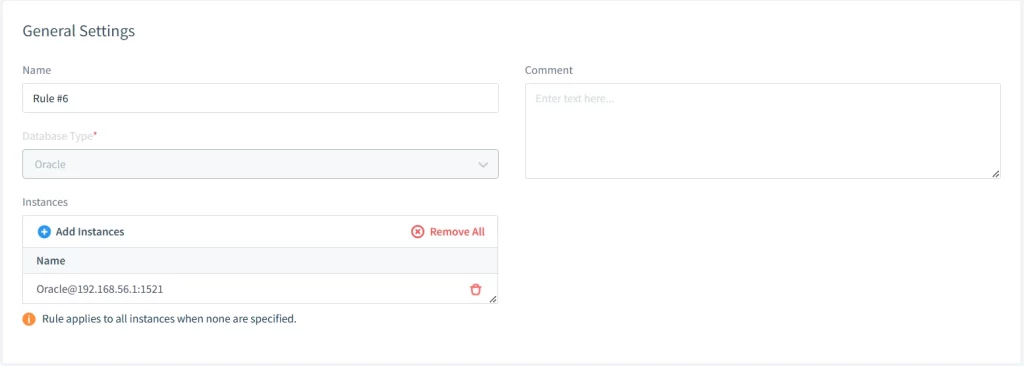
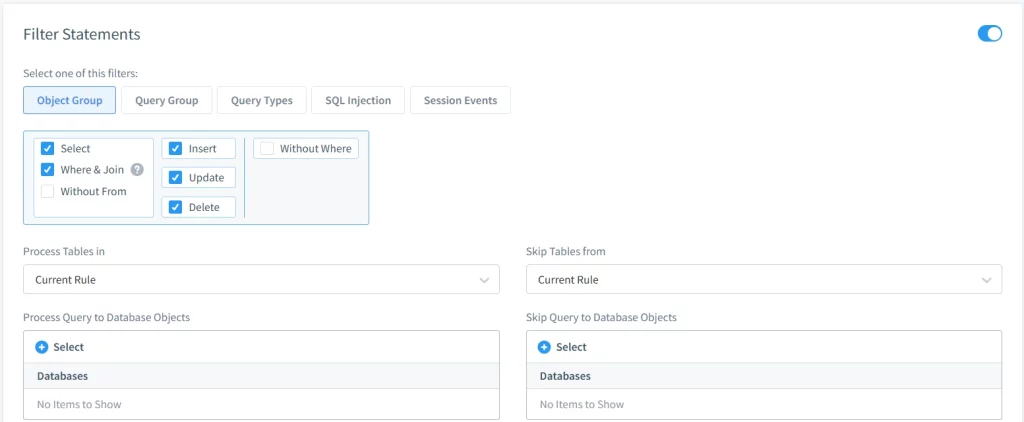
You can also review interactive events in the “Transactional Trails” tab of the application:
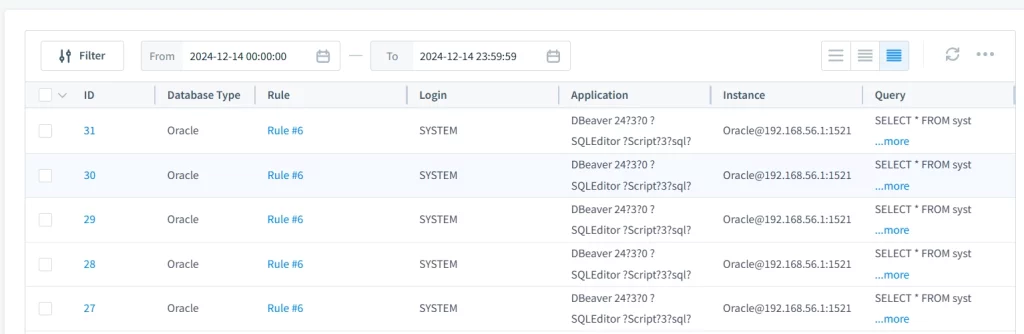
DataSunrise can further enhance the security of your Oracle Database with features such as security rules, data analysis, and more. If you’re interested in any of these features, be sure to book an online demo.
Conclusion
The Oracle Audit Trail is an essential tool for tracking and monitoring database activity, ensuring both security and compliance. By offering different auditing options, such as Standard, Fine-Grained, and Unified auditing, Oracle provides flexibility for businesses with varying security and regulatory needs. Whether you’re trying to comply with GDPR, HIPAA, or PCI DSS, Oracle’s auditing capabilities help safeguard your database and provide the necessary logs for compliance reporting.
To further enhance your database security, consider integrating Oracle’s audit features with third-party solutions like DataSunrise, which offer advanced features such as real-time monitoring and alerting.
By leveraging Oracle Audit Trail and third-party tools, organizations can meet security standards, respond swiftly to threats, and maintain full compliance with regulatory requirements.
