
Oracle Data Audit Trail
Introduction to the Oracle Data Audit Trail
In today’s complex IT environment, securing databases and ensuring regulatory compliance is a top priority. Oracle, as a leader in database management systems, offers advanced tools to track, monitor, and audit user activities within its databases. This article explores the Oracle Data Audit Trail and how its features—along with third-party solutions—can strengthen your database security and compliance efforts.
What is an Oracle Data Audit Trail?
An Oracle Data Audit Trail refers to the process of capturing detailed logs of database activities to track user actions and ensure a secure and compliant environment. These logs provide critical insights into database operations, helping organizations detect unauthorized access and maintain control over sensitive data. Oracle’s advanced auditing tools generate extensive logs that can be configured for real-time monitoring, ensuring that suspicious activities are detected quickly and effectively.
The Role of the Oracle Data Audit Trail in Security
The Oracle Data Audit Trail plays a pivotal role in enhancing database security and meeting compliance requirements. It helps organizations:
- Track user activities: Oracle’s audit trail logs important actions like logins, data modifications, and schema changes, allowing administrators to monitor who did what and when.
- Detect security breaches: By analyzing audit logs, administrators can identify suspicious behavior, such as unauthorized access or privilege escalation attempts.
- Ensure regulatory compliance: The Oracle Data Audit Trail aids in meeting compliance standards like GDPR, HIPAA, and PCI DSS by maintaining detailed audit logs that prove adherence to industry regulations.
- Prevent unauthorized changes: Detailed logs of data manipulations (inserts, updates, deletes) help detect unauthorized changes, preventing data tampering.
Types of Auditing in Oracle and How to Implement Them
Oracle provides various auditing mechanisms that help administrators monitor database activities and ensure compliance with security standards. Below are the key types of auditing, along with steps on how to enable them.
1. Standard Auditing
Standard auditing captures database events like logins, data accesses, and schema changes. While this method is easy to implement, it may not provide the detailed information required for high-level security or compliance needs.
Enabling Standard Auditing:
To enable standard auditing in Oracle, use the following SQL command:
ALTER SYSTEM SET audit_trail = DB, EXTENDED SCOPE = SPFILE;
SHUTDOWN IMMEDIATE;
STARTUP;- This command configures Oracle to store audit logs within the database itself.
- The
EXTENDEDoption ensures that both SQL statements and associated bind variables are captured.
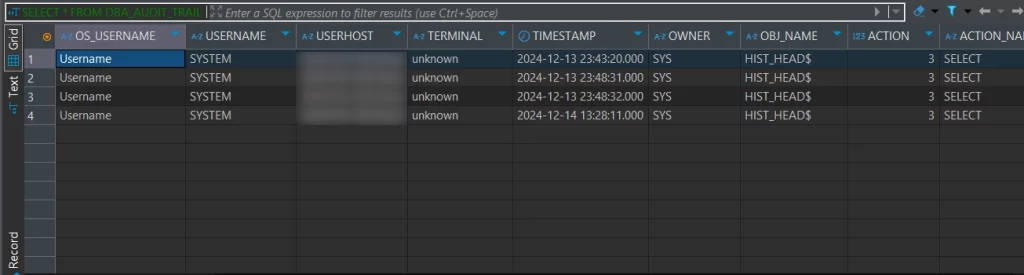
Once enabled, query the DBA_AUDIT_TRAIL table to review audit logs.
2. Fine-Grained Auditing (FGA)
Fine-Grained Auditing (FGA) allows administrators to audit access to specific data based on conditions. This feature is essential for monitoring sensitive data and high-risk actions, reducing the volume of logs by focusing only on relevant events.
Enabling Fine-Grained Auditing:
To set up FGA for auditing high-salary employee records, use the following SQL:
BEGIN
DBMS_FGA.add_policy(
object_schema => 'HR',
object_name => 'EMPLOYEES',
policy_name => 'audit_high_salary',
audit_condition => 'SALARY > 100000',
audit_column => 'SALARY',
enable => TRUE
);
END;- This creates a policy that audits access to employee records where the salary exceeds $100,000.
- The
audit_conditionfilters the logs to capture only relevant events.
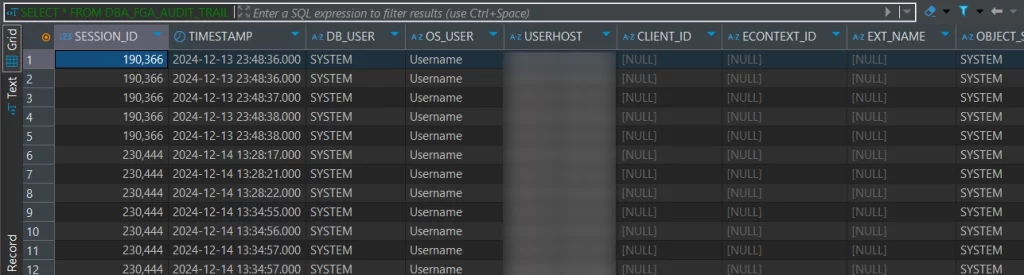
The results can be viewed in the DBA_FGA_AUDIT_TRAIL table.
3. Operating System Auditing (OS Auditing)
Oracle’s built-in auditing captures database activities, but OS Auditing extends monitoring to the operating system level, tracking file accesses, network connections, and other system-level events. This provides a comprehensive security view when combined with database logs.
Enabling OS Auditing:
To enable OS-level auditing, use the following command:
ALTER SYSTEM SET audit_trail = OS SCOPE = SPFILE;
SHUTDOWN IMMEDIATE;
STARTUP;- This sends audit records to the operating system’s audit trail (e.g., syslog on Linux or Event Logs on Windows).
OS Auditing helps you correlate database and system-level activities, improving your overall security posture.
Oracle Data Audit Trail with DataSunrise: Enhanced Data Audit System
While Oracle’s native Data Audit Trail features offer solid capabilities, third-party solutions like DataSunrise can provide additional layers of security and control. DataSunrise enhances Oracle’s auditing system with the following features:
- Granular Rule-Based Data Auditing: DataSunrise allows for highly customizable audits, from logging specific user actions to applying regular expressions (RegEx) to queries for more targeted data tracking.
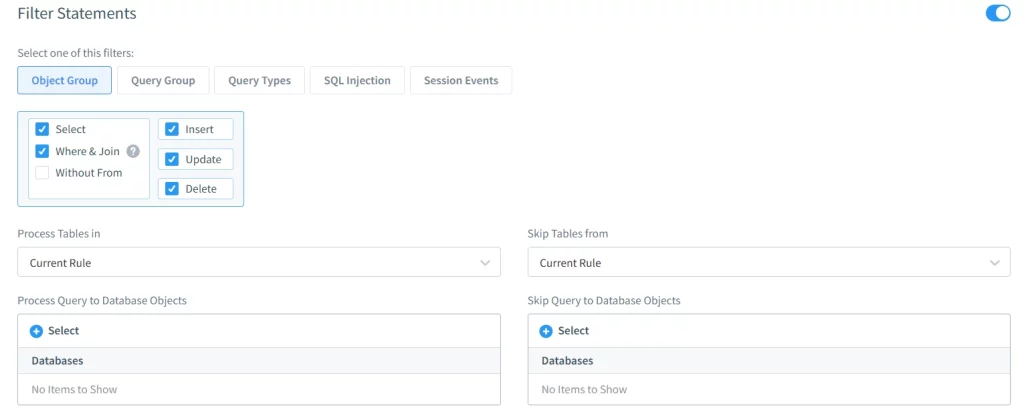
- Enhanced Security with Database Proxy: DataSunrise acts as a proxy between your Oracle Database and end users, enabling you to log every query and server response while also offering the ability to block unauthorized access or even deny requests in real time.
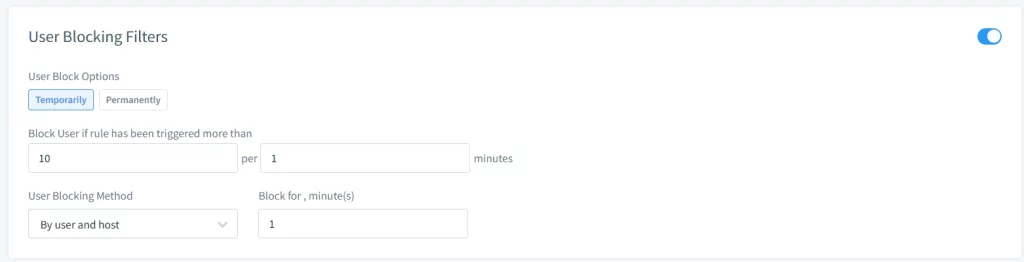
- Data Masking Implementation: DataSunrise automatically discovers sensitive data and applies dynamic and static data masking. This helps organizations comply with various data privacy regulations by protecting sensitive information.
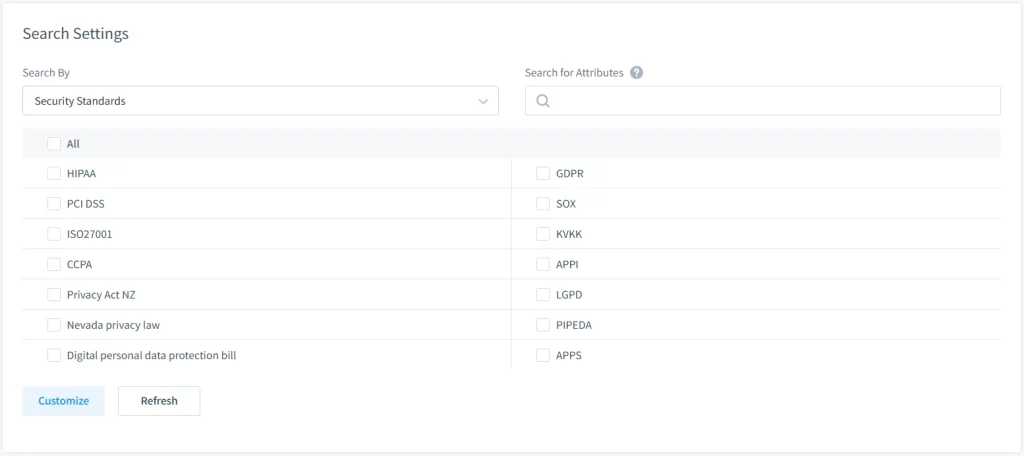
If you’re looking to enhance your Oracle data auditing capabilities, DataSunrise offers a comprehensive suite of features that can help you secure your Oracle Database environment more effectively. You can book an online demo to see things working in action.
Best Practices for Implementing Oracle Data Audit Trails
To get the most out of your Oracle Data Audit Trail and ensure compliance, consider the following best practices:
- Define Clear Audit Policies: Set specific goals for your audit trail, such as tracking login attempts, monitoring access to sensitive data, or logging changes to critical database objects.
- Use Fine-Grained Auditing: Enable FGA for sensitive data, such as financial records, personally identifiable information (PII), or high-value transactions. This reduces log volume and helps focus on high-risk activities.
- Regularly Review Audit Logs: Set up automated processes to periodically review audit logs, either manually or through a third-party solution like DataSunrise. Regular log review ensures that suspicious activity is detected early.
- Implement Access Control: Leverage OS Auditing to track system-level events and combine them with database logs for a more comprehensive view of user activities.
- Optimize Performance: If using native Oracle audit tools, ensure that logging doesn’t degrade performance. Tools like DataSunrise can help manage audit load efficiently without impacting system performance.
By following these best practices, you can enhance your Oracle Data Audit Trail, ensuring that you maintain robust security while meeting regulatory compliance requirements.
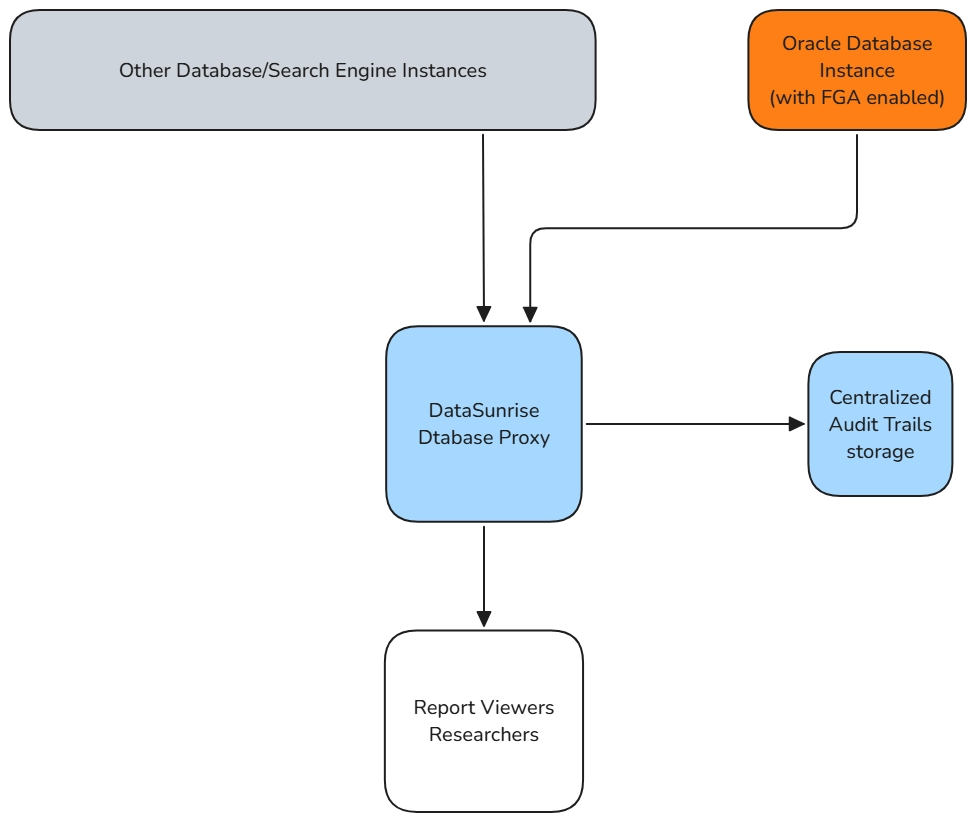
Conclusion
Implementing an Oracle Data Audit Trail is essential for securing sensitive data and ensuring compliance with industry regulations. By leveraging Oracle’s built-in auditing features alongside third-party solutions like DataSunrise, organizations can enhance security, track user activities, and detect potential threats more effectively. Follow best practices to optimize your audit trail and maintain a robust defense against data breaches and unauthorized access.
At DataSunrise, we respect your time and strive to make things easy for you. You can quickly download a trial version of our data security platform with just a valid email address. Once the form is submitted, you’ll receive your trial license key instantly, right as the download begins. If you’d like to explore your specific data security needs and see how DataSunrise can help, we also offer the option to schedule an online demo for a more in-depth discussion.
