
Oracle Data Obfuscation: Safeguarding Sensitive Data in Non-Production Environments

Introduction
Data security is a top priority for organizations today. Organizations must protect sensitive data such as personally identifiable information (PII), financial details, and trade secrets from unauthorized access. One powerful technique to achieve this is Oracle data obfuscation.
Data obfuscation involves masking or scrambling sensitive data while preserving its format and usability for development, testing and other non-production purposes. It allows businesses to comply with data privacy regulations and prevent data breaches. Let’s explore the basics of Oracle data obfuscation and how to implement it.
What is Oracle Data Obfuscation?
Oracle Data Obfuscation is a feature of Oracle Database that helps protect sensitive data from unauthorized access. It changes data so only authorized people can use it, while keeping it realistic and accurate.
Many organizations use data obfuscation to protect sensitive production data in non-production environments such as development, testing, or training. Mask sensitive details instead of using real customer names, account numbers, etc. This reduces the risk of data breaches and helps comply with data privacy laws.
Some common data obfuscation techniques include:
- Encryption: Encoding data using a cipher
- Substitution: Replacing sensitive data with fictitious but realistic values
- Shuffling: Randomly re-arranging the order of data elements
- Nulling: Replacing data with NULL values
- Masking: Obscuring parts of the data, e.g. showing only the last 4 digits of an SSN
Oracle data obfuscation supports these techniques and more through various tools and packages. The production environment never exposes the original sensitive data outside.
Data Obfuscation Across Different Platforms
While Oracle provides robust data obfuscation capabilities, the concept and importance of data obfuscation extend across all database platforms and data storage systems. Modern organizations typically manage data across multiple platforms, making a comprehensive data obfuscation strategy essential for complete protection.
Data obfuscation techniques vary by platform but share common objectives: protecting sensitive information while maintaining data usability. Microsoft SQL Server implements data obfuscation through Dynamic Data Masking and Always Encrypted features. PostgreSQL offers masking through views and row-level security. MongoDB provides field-level encryption to obfuscate specific document fields.
Cloud providers have also integrated data obfuscation capabilities into their services. AWS offers column-level encryption in Redshift and DynamoDB. Google Cloud provides data masking in BigQuery, while Azure SQL Database includes dynamic data masking similar to Oracle’s redaction features.
Third-party solutions like DataSunrise extend data obfuscation capabilities beyond native database features. These specialized tools provide consistent obfuscation policies across heterogeneous database environments, centralized management, and advanced obfuscation algorithms that preserve data relationships and statistical properties.
Regardless of the platform, effective data obfuscation adheres to key principles: maintaining data format and structure, preserving referential integrity, supporting application functionality with obfuscated data, and implementing role-based access to obfuscated versus original data. Following these principles ensures that data obfuscation serves its primary purpose—protecting sensitive information while allowing systems to function normally.
Oracle Data Obfuscation Tools
Oracle provides several tools for implementing data obfuscation:
Data Redaction
Oracle Data Redaction is a security feature that masks sensitive data before it leaves the database. It allows you to redact (mask) column data using policies based on different conditions like user roles. For example:
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'hr', object_name => 'employees', column_name => 'email', policy_name => 'redact_emp_email', function_type => DBMS_REDACT.PARTIAL, function_parameters => '0,1,XXXXXXX'); END;
This redacts employee email addresses to show only the first character with the rest replaced by ‘X’, e.g. “[email protected]” becomes “jXXXXXX”.
Data Masking and Subsetting
Oracle Data Masking Pack provides tools to mask and subset sensitive data for non-production use:
- Data Masking: Replaces sensitive data with realistic fictitious data
- Data Subsetting: Creates a subset of data based on application requirements
For example, to mask employee names:
BEGIN
DBMS_DATAPUMP.METADATA_TRANSFORM(
job_name => 'MASK EMP DATA',
object_type => 'TABLE',
transform_name => 'COLUMN_MASK',
transform_value =>
'empno_trans:EMPLOYEE_ID,
ename_trans:EMPLOYEE_NAME');
END;This replaces employee number and name columns with masked data during export.
How to Implement Oracle Data Obfuscation
Here’s a high-level process to implement Oracle data obfuscation:
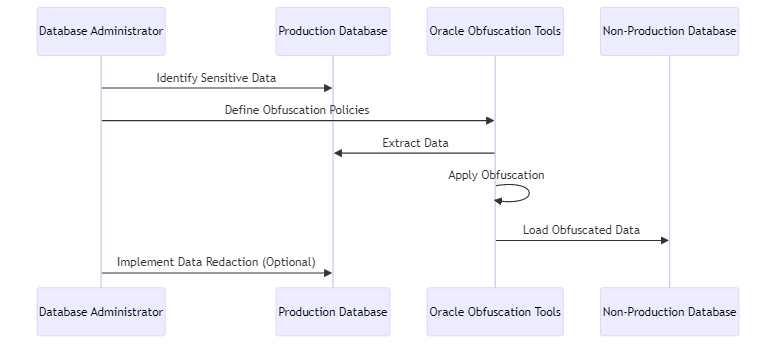
- Identify Sensitive Data: Identify the data that requires protection – PII, financial data, etc. This may involve a data discovery process.
- Choose Obfuscation Techniques: Select appropriate techniques like encryption, masking, shuffling based on data types and application needs.
- Develop Obfuscation Policies: Define the obfuscation rules and conditions using Oracle tools. Evaluate them using example data.
- Implement in Non-Production: Apply the obfuscation on data exported from production to non-production environments.
- Mask in Production (optional): For highly sensitive data, you may choose to implement data redaction policies in production itself.
Let’s walk through a simple example of masking employee salaries using Data Redaction:
First, we create a sample employees table with some data:
CREATE TABLE employees ( employee_id NUMBER, name VARCHAR2(100), salary NUMBER ); INSERT INTO employees VALUES (1, 'John Smith', 50000); INSERT INTO employees VALUES (2, 'Jane Doe', 60000);
Next, we create a redaction policy to partially mask the salary:
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'hr', object_name => 'employees', column_name => 'salary', policy_name => 'mask_emp_salary', function_type => DBMS_REDACT.PARTIAL, function_parameters => '9,1,*'); END;
This shows only the first digit of the salary and replaces the rest with ‘‘. So “50000” becomes “5***”.
When a user queries the employees table, the salary column will display the masked values:
SELECT * FROM employees;
EMPLOYEE_ID NAME SALARY
----------- -------------- ------
1 John Smith 5****
2 Jane Doe 6****They never expose the actual salaries, but the data remains realistic for development and testing purposes. The original unmasked data is accessible only to authorized production users.
Best Practices for Data Obfuscation
Here are some best practices to ensure successful Oracle data obfuscation:
- Use Least Privilege: Grant access to obfuscated/masked data on a need-to-know basis. Regularly review and adjust access permissions.
- Maintain Referential Integrity: Ensure obfuscation maintains referential integrity between related data entities. Use consistent masking across tables.
- Test Thoroughly: Test obfuscation policies on sample data and verify application functionality with obfuscated data before deploying to production.
- Document Obfuscation Processes: Ensure to maintain accurate documentation of the concealed data. Record the method used by someone to hide the data. Additionally, provide instructions on how to uncover the hidden data when necessary, like for resolving problems.
- Monitor and Audit: Establish robust monitoring and checks to detect any unauthorized attempts to access confidential information, even if it is concealed.
Oracle data obfuscation tools help protect sensitive data during development and testing, while still allowing realistic use. Obfuscation is crucial for protecting data. Combine it with other security measures such as access controls, encryption, and auditing. This combination helps to establish a robust defense strategy.
Conclusion
Oracle data obfuscation is an essential technique for protecting sensitive information in non-production environments. Developers can test applications using fake but realistic data instead of real data to avoid revealing sensitive information.
Oracle provides several obfuscation capabilities through features like Data Redaction and Data Masking. These allow defining flexible policies to mask, encrypt, or randomize sensitive data based on users and conditions. Implementing data obfuscation involves discovering sensitive data, selecting appropriate techniques, developing and testing obfuscation policies, and applying them to non-production data exports.
When using Oracle data obfuscation, it is important to follow best practices. These practices involve limiting access to the data, maintaining data relationships, testing policies, documenting processes, and monitoring usage. Data obfuscation helps organizations use data for business purposes safely. It works with other security measures to prevent costly and harmful data breaches.
As the data landscape grows increasingly complex and threats become more sophisticated, data security will only become more critical. Oracle data obfuscation helps organizations protect important data while still getting the most value from their data assets. Businesses can confidently innovate while protecting security and privacy by incorporating strong obfuscation into their data management systems.
