
How the OSI 7-Layer Model Facilitates Effective Network Communication
Introduction
The OSI model explains how computers send data to each other on a network in a standard way. Developed in the late 1970s, the OSI model breaks down network communication into seven distinct layers. Each layer has specific functions and interacts with the layers above and below it.
While the modern internet primarily uses the simpler TCP/IP model, the OSI 7-layer model remains an essential tool. It helps network engineers design networks, troubleshoot issues, and ensure interoperability between systems. Let’s take a closer look at each of the seven OSI layers and how they enable network communications.
The 7 Layers of OSI Model
Why Understanding OSI Layers Still Matters
Grasping the layers of the OSI model helps IT teams manage, secure, and troubleshoot complex networks. Even though many systems use the TCP/IP model, the OSI model gives a clear, layered view that makes it easier to identify where problems or security gaps may occur.
For example, implementing tools like DataSunrise benefits from OSI-based thinking. DataSunrise focuses on monitoring and protecting data at specific OSI layers, such as inspecting traffic at the transport and application layers to detect threats or unauthorized access.
This layered understanding ensures better compliance, smarter architecture, and faster issue resolution across modern networks.
Divide the seven OSI layers into two groups: upper layers and lower layers. The upper layers (7, 6, 5) focus on applications and how users interact with data. The lower layers (4, 3, 2, 1) handle data transport.
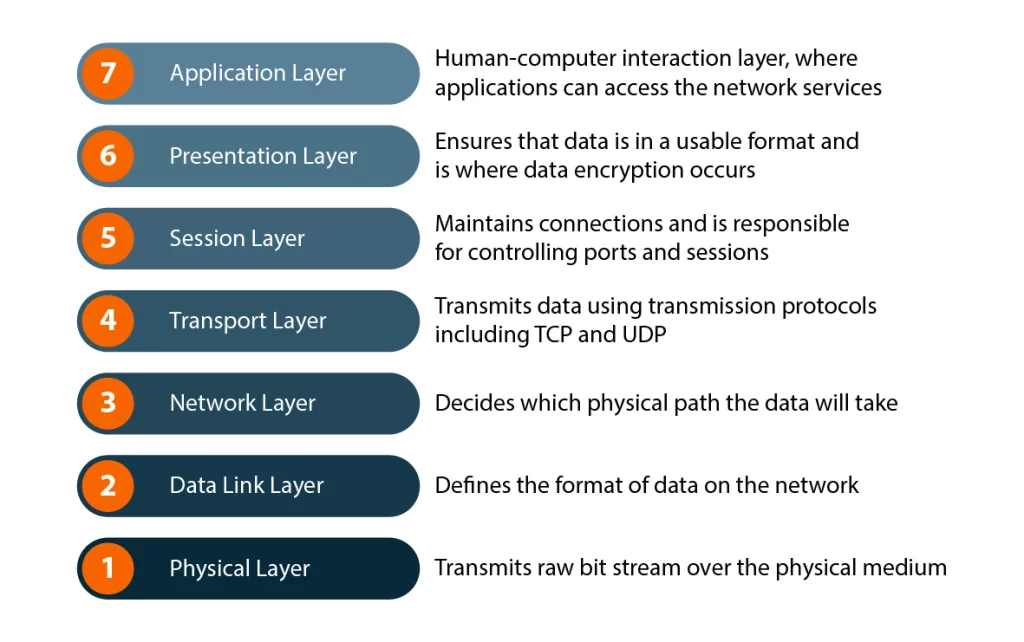
The Upper Layers of OSI Model
Layer 7: The Application Layer The application layer is closest to the end user. It provides network services directly to applications like web browsers, email clients, and messaging apps. When you load a webpage or send an email, the application layer formats that data and sends it to layer 6.
DNS is responsible for associating domain names with IP addresses. The application layer ensures that it correctly structures data for the respective application.
Layer 6: The presentation layer gets data from the app layer and readies it for sending over the network. This often involves translation, encryption, and compression.
The presentation layer formats data using a common syntax agreed upon by the sending and receiving devices. For example, it may convert ASCII text into a standardized format. Encryption secures sensitive data, and compression decreases the amount of data that needs transmission.
Layer 5: The Session Layer The session layer establishes, maintains, and terminates connections between devices. It sets up sessions, or temporary communication channels, that allow devices to exchange data over a prolonged period.
If the connection is interrupted, the session layer resends data from the last checkpoint using checkpoints. It also implements dialog control to ensure two applications don’t try sending data at the same time.
The Lower Layers of OSI Model
Layer 4: The transport layer breaks down data from the session layer and prepares it for transmission over the network. Responsible for end-to-end delivery and error-free data transfer between systems.
The two primary transport layer protocols are TCP and UDP. TCP ensures data arrives at its destination by checking and requesting retransmission if it loses any data. UDP is connectionless and does not guarantee delivery, but is faster. The transport layer also performs traffic control, adjusting data flow to match network speed.
Layer 3: The Network Layer The network layer handles logical addressing and routing of data between nodes. The transport layer breaks data segments into smaller packets and attaches source and destination addresses.
How Routers Use IP Addresses
Routers use IP addresses to find the best way for data to go through different networks and reach its destination. The network layer finds the best route and switches packets between networks until they reach the receiving device.
Layer 2: The Data Link Layer connects two nodes directly on a network. It takes packets from the network layer, breaks them into frames, and sends them to the correct destination using MAC address.
The data link layer examines incoming frames for errors and requires a retransmission if it detects any corruption. It regulates flow control to ensure the receiving device isn’t overwhelmed with data. The data link layer also arbitrates access to the physical media so multiple devices can safely share network links.
Layer 1: The Physical Layer provides the foundation for building the higher layers. It defines the physical and electrical characteristics of the network, including cables, connectors, radio frequencies, voltages, modulation, and line coding.
The physical layer transmits raw bit streams over the physical medium as electrical pulses, light signals, or radio waves. It specifies data rates, maximum transmission distances, and physical network topology. Different physical layer standards exist for copper, fiber optic, and wireless media.
Sending an Email with OSI
To illustrate the OSI model, let’s examine what happens when you send an email:
- The email client application formats the message and attachments. (Application)
- The system translates the data to SMTP format, encrypts it, and compresses it. (Presentation)
- The user opens a session with the email server. (Session)
- The system segments the message, adds a header, and hands it to the network layer. (Transport)
- The segments break into packets with IP address information. (Network)
- The system breaks the packets into frames with MAC addresses. (Data Link)
- The system changes frames into bits and sends them over ethernet or wifi as electrical or radio signals. (Physical)
The email server sends the data to the recipient’s email application by moving it up through the OSI layers.
OSI Model vs TCP/IP Model
The TCP/IP model is a basic four-layer model used for internet communication in the real world. Developed by the US DoD, it predates the OSI model.
The key difference is that TCP/IP combines the functions of multiple OSI layers. The application layer includes OSI layers 5, 6, and 7. The transport layer matches OSI layer 4. The internet layer is equivalent to the OSI network layer 3. Finally, the network access layer includes OSI layers 1 and 2.
The OSI model is important, but the TCP/IP model is better for internet communication. However, both help us understand the many complex processes required for network data delivery.
Practical Applications of the OSI Model Today
While the TCP/IP model dominates practical networking implementations, the OSI model remains invaluable for understanding, designing, and troubleshooting network systems. Network engineers still use the OSI model as a conceptual framework to isolate and address issues efficiently.
When troubleshooting connectivity problems, technicians commonly work through the OSI model layers systematically. They might begin by checking physical connections (Layer 1), then verify data link functionality (Layer 2), and continue upward until identifying the problematic layer. This structured approach, often called “bottom-up” or “top-down” troubleshooting, significantly reduces diagnostic time.
Security professionals also leverage the OSI model to implement comprehensive protection strategies. Different security measures target specific OSI layers – firewalls operate at Layers 3-4, while encryption works at Layers 6-7. Understanding these relationships helps organizations build defense-in-depth security architecture.
Network equipment vendors frequently reference OSI model layers when describing product capabilities. For instance, a Layer 2 switch primarily operates at the data link layer, while a Layer 3 switch incorporates network layer functionality. This standardized terminology allows clear communication about device capabilities across the industry.
The OSI model also provides a common language for network certification programs. CompTIA Network+, Cisco CCNA, and other professional certifications test candidates on their understanding of how the OSI model applies to real-world networking scenarios, demonstrating its continued relevance in professional development.
Conclusion
The OSI 7 layer model is a fundamental concept in computer networking. By abstracting out specific functions at each layer, OSI enables interoperability between diverse systems and provides a common troubleshooting model.
Knowing the OSI layers can benefit network professionals, even if they don’t work with them directly. The layers go from the application layer at the top to the physical layer at the bottom. When you have a networking issue, using the OSI model can help you find and fix the problem quicker.
