
PEM Files

Introduction
When working with cryptography, certificates, and keys, you’ll often encounter the PEM file format. PEM stands for Privacy Enhanced Mail and is a widely used method for storing and sharing cryptographic keys, certificates, and other sensitive data. In this article, we’ll dive into the basics of PEM files, exploring their structure, usage, and how they relate to secure communication.
What is a PEM File?
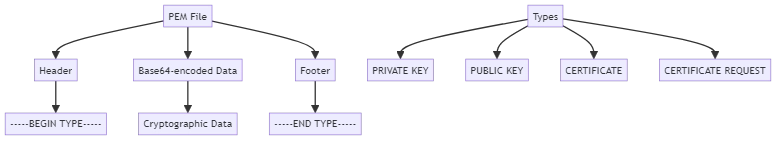
PEM files are text-based files that follow a specific format for storing cryptographic data. They contain base64-encoded data encapsulated between plain-text headers and footers. The headers and footers indicate the type of data being stored, such as a private key, public key, certificate, or certificate request.
Here’s an example of a PEM-formatted RSA private key:
-----BEGIN RSA PRIVATE KEY----- MIIEogIBAAKCAQEAqhAx9UqRW/rP/3uw5UDHENVOzlq2ljPbe0TqA8+KKS7dABYJ ... K5xGP+LPgzCc7Dkp2+jE8SJOuTrFLRWhlkBvZKRwfQ== -----END RSA PRIVATE KEY-----
The base64-encoded data is sandwiched between the —–BEGIN RSA PRIVATE KEY—– and —–END RSA PRIVATE KEY—– markers, clearly identifying the contents as an RSA private key.
The PEM Format
The PEM format is designed to be human-readable and easily transferable. It uses base64 encoding to represent binary data in a text-based format. Base64 encoding converts binary data into a limited set of ASCII characters, making it suitable for transmission over text-based protocols like email.
PEM File Structure
PEM files can store various types of cryptographic data, including:
- Private keys (RSA, DSA, EC)
- Public keys
- Certificates (X.509)
- Certificate signing requests (CSRs)
- Certificate revocation lists (CRLs)
Each type of data has its own specific header and footer markers. For example:
- Private key: —–BEGIN PRIVATE KEY—– and —–END PRIVATE KEY—–
- Public key: —–BEGIN PUBLIC KEY—– and —–END PUBLIC KEY—–
- Certificate: —–BEGIN CERTIFICATE—– and —–END CERTIFICATE—–
By using these clear markers, PEM files make it easy to identify and extract the relevant data.
PEM Certificates
One common use case for a PEM file is storing X.509 certificates. An X.509 certificate is a digital document that binds a public key to an identity, such as a domain name or an organization. Certificates are issued by trusted Certificate Authorities (CAs) and are used to establish secure connections over the internet using protocols like SSL/TLS.
Here’s an example of a PEM-formatted X.509 certificate:
-----BEGIN CERTIFICATE----- MIIFSzCCBDOgAwIBAgIQV5Kwra1VwjZdYbSqBlp1DDANBgkqhkiG9w0BAQsFADBG ... Rti0xS/YCrQMsDJD2A8FnhyofiZdkZovFDG4NmSWxRU4AXrWTg== -----END CERTIFICATE-----
The certificate contains information such as the issuer, subject, validity period, and the public key associated with the certificate. When a client connects to a server over SSL/TLS, the server presents its certificate to the client for verification. The client checks the certificate’s validity and authenticity before establishing a secure connection.
Working with PEM Files
When working with cryptographic operations, you’ll often need to read, write, and manipulate PEM files. Most programming languages and libraries provide support for handling PEM-formatted data. For example, in Python, you can use the cryptography library to load and parse a PEM file:
from cryptography import x509
from cryptography.hazmat.backends import default_backend
with open("certificate.pem", "rb") as cert_file:
cert_data = cert_file.read()
cert = x509.load_pem_x509_certificate(cert_data, default_backend())
print(cert.subject)This code snippet reads a PEM-formatted certificate from a file, parses it using the x509 module from the cryptography library, and prints the subject information.
Similarly, you can use the appropriate libraries and functions in other programming languages to work with PEM, such as OpenSSL in C/C++, java.security in Java, or crypto in Node.js.
PEM Files in Modern Cloud Infrastructure
PEM files are vital in today’s cloud infrastructure. Cloud platforms use them for SSH access and certificate management. They enable secure logins to AWS, Azure, and Google Cloud services. Kubernetes depends on PEM certificates for cluster security. Certificate services like Let’s Encrypt make PEM management easier by automating generation and renewal. Infrastructure as Code tools such as Terraform and Ansible also rely on proper PEM file handling. As zero-trust models become the norm, secure certificate workflows built around PEM are critical for system integrity.
Conclusion
PEM files are a fundamental component of cryptography and secure communication. They provide a standardized format for storing and exchanging cryptographic keys, certificates, and related data. Understanding how a PEM file is structured and used is essential for anyone working with SSL/TLS, public key infrastructure (PKI), or secure APIs.
By following the PEM format and using trusted libraries and tools, you can effectively manage certificates and keys in your applications. Whether you’re implementing encryption protocols, setting up server security, or automating cloud infrastructure, familiarity with PEM files is a valuable skill.
Always remember to handle private keys with care, validate certificate sources, and rotate credentials regularly to maintain trust and protect sensitive data.
