
Penetration Testing: A Complete Overview

Introduction
In today’s digital world, cyber threats are becoming more sophisticated. These threats have the potential to harm organizations by exposing their data and systems. To protect against these threats, penetration testing is important.
This entails probing for vulnerabilities in an organization’s networks, applications, and systems by mimicking actual attacks. Penetration testing, also known as pen testing or white-hat hacking.
By proactively discovering and addressing these weaknesses, businesses can fortify their defenses and protect sensitive data from malicious actors.
What is Penetration Testing?
Penetration testing is a systematic process of evaluating the security of an organization’s IT infrastructure by safely exploiting vulnerabilities. It includes authorized professionals called penetration testers or ethical hackers. They use the same techniques and tools as malicious attackers to test an organization’s security controls. The aim is to find weaknesses before cybercriminals can use them, so organizations can focus on fixing security gaps.
Penetration Testing Stages
Penetration testing typically follows a structured approach to ensure a comprehensive assessment of an organization’s security posture. The key stages of a penetration test include:
- Planning and Reconnaissance: In this initial stage, we define the scope and objectives of the penetration test. Testers collect information about systems, networks, and applications using OSINT techniques like Google dorking, social media analyzing, and DNS enumeration.
- Scanning: Testers identify the target environment and employ various scanning techniques to identify potential entry points and vulnerabilities. This stage involves port scanning, network mapping, and vulnerability scanning using tools such as Nmap, Nessus, and Burp Suite.
- Gaining Access: Penetration testers try to exploit vulnerabilities to access systems without permission. This stage may involve techniques like password cracking, social engineering, and exploiting known vulnerabilities in software or configurations.
- Maintaining Access: After successfully gaining access, testers aim to maintain a persistent presence in the compromised systems. They may install backdoors, create new user accounts, or establish covert communication channels to simulate an attacker’s actions.
- Analysis and Reporting: Testers analyze the results of the penetration test and prepare a detailed report in the final stage. The report details the discovered vulnerabilities, their potential impact, and recommendations for remediation. It serves as a roadmap for the organization to prioritize and address security weaknesses.
Penetration Testing Methods
Various methods can perform penetration testing, each focusing on different aspects of an organization’s security.
External Testing
This method evaluates the security of a company’s external systems, such as websites, email servers, and firewalls. It simulates a cybercriminal attempting unauthorized access.
For instance, a test might try to take advantage of a weakness in a website called cross-site scripting (XSS). The tester creates a harmful code and puts it into the website’s input areas. If the code works, it runs and the hacker could access user information or perform unauthorized actions.
Internal Testing
Internal testing focuses on the security of an organization’s internal network and systems. It looks at someone who is a threat from inside or an attacker who has already gotten into the internal network.
To illustrate, consider a scenario where a penetration tester gains access to an employee’s workstation through social engineering. Once inside the network, the tester attempts to escalate privileges, move laterally across the network, and access sensitive data.
This test shows how dangerous insider threats can be and the need for strong access controls and network separation.
Wireless Testing
Wireless testing assesses the security of an organization’s wireless networks, including Wi-Fi and Bluetooth. It involves attempting to intercept wireless traffic, crack encryption keys, and gain unauthorized access to the network.
For instance, a penetration tester may set up a rogue access point near the target organization’s premises. The examiner might deceive users into joining a fake network, stealing their data or infecting their devices with malware.
Social Engineering Testing
Social engineering assessment gauges the human aspect of an organization’s security. It entails tricking individuals into revealing confidential data or allowing access to secure systems. A typical instance of social engineering is phishing.
In a phishing assessment, the penetration tester dispatches meticulously designed emails to staff, imitating authentic correspondence. The objective is to deceive recipients into disclosing their login details or clicking on harmful links. The outcomes of these assessments underscore the importance of training employees on security awareness.
Penetration Testing Examples and Preliminary Setup
To provide a more practical understanding of penetration testing, let’s explore a few examples that require specific preliminary setups.
SQL Injection Vulnerability
Suppose a penetration tester is assessing a web application that uses a MySQL database backend. To check for SQL injection flaws, the tester must create a local setup with a database structure like the target system.
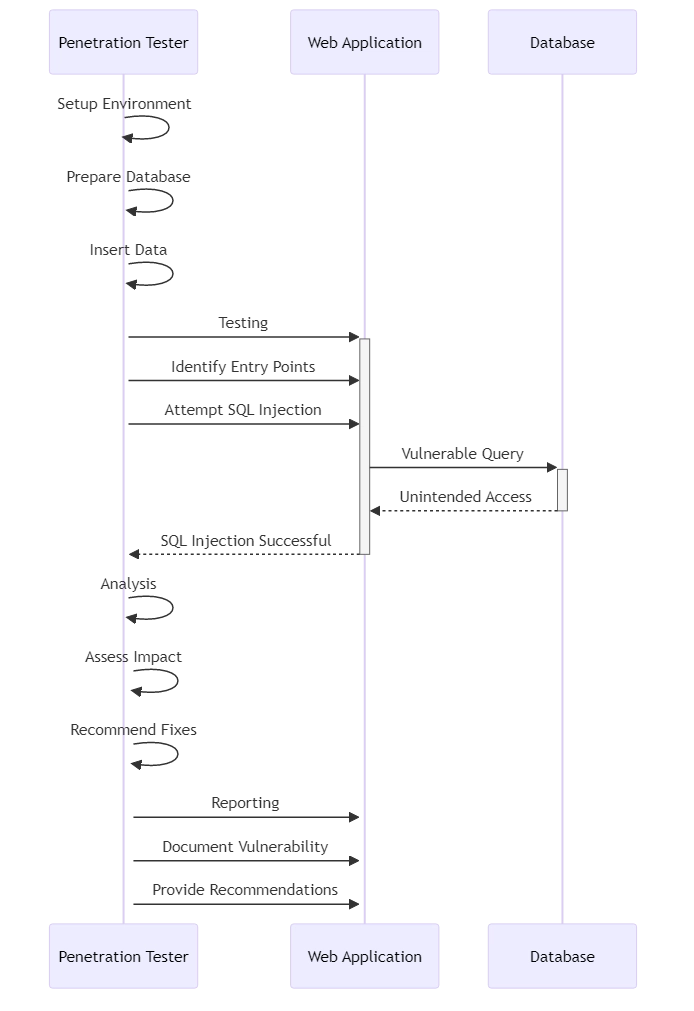
Preliminary Setup:
- Install MySQL and create a database named “webapp”.
- Construct a table called “users” having columns “id”, “username”, and “password”.
- Insert sample user data into the “users” database table.
The tester can now search for SQL injection vulnerabilities in the web application’s login form or search feature. We have completed the initial setup. The tester can try to exploit any vulnerabilities found. The tester can use malicious SQL queries to get around authentication, access sensitive data, or change database records.
If a website has a SQL injection vulnerability, someone could hack into the system without the correct login details. The tester may also be able to steal user data. This highlights the importance of proper input validation and parameterized queries to prevent SQL injection attacks.
Network Segmentation Testing
In this example, the penetration tester aims to assess the effectiveness of an organization’s network segmentation controls. The aim is to see if an attacker can move from one network area to another and reach restricted resources.
Preliminary Setup:
- Set up a virtual lab environment with multiple network segments (e.g., DMZ, internal network, production network).
- Configure firewalls and access control lists (ACLs) to enforce network segmentation policies.
- Place sensitive resources, such as a database server, in the production network segment.
The penetration tester begins by gaining access to a low-security network segment, such as the DMZ. From there, they attempt to scan and map the internal network, identifying potential paths to the production network. The tester is attempting to access the database server without permission. They are looking for mistakes or weaknesses in network devices or servers to exploit.
Should the network segmentation controls be correctly set up and adjusted, the tester ought to be incapable of accessing the production network and the confidential database server from the DMZ.
However, if the tester discovers weaknesses, they can provide recommendations to strengthen the network segmentation and prevent lateral movement.
Conclusion
Penetration testing is a vital component of an organization’s cybersecurity strategy. By simulating real-world attacks, penetration testing helps identify vulnerabilities, assess the effectiveness of security controls, and provide actionable insights for improvement.
Organizations benefit from regularly conducting penetration tests to identify and address vulnerabilities before potential exploitation. This proactive approach reduces the likelihood of data breaches occurring. By keeping their systems and data safe, organizations can better protect sensitive information.
Experienced professionals should conduct penetration testing. These professionals should follow ethical guidelines and stay informed about the latest attack methods and security practices.
Organizations need to enhance their security measures to ensure strong protection. You can achieve this through vulnerability management, employee training, and incident response planning. Furthermore, the team should conduct penetration testing to enhance security even more.
