
Percona Server for MySQL Data Audit Trail

Introduction
In today’s data-centric landscape, establishing a dependable and consistent approach to a Data Audit Trail is essential. This holds particularly true for Percona Server for MySQL, a robust open-source MySQL-compatible solution. Percona Server for MySQL functions as a flexible and efficient tool for managing databases, offering superior performance, scalability, and security enhancements. As a result, it emerges as a top-tier option for organizations seeking to streamline and enhance their database operations. However, to fully leverage its capabilities, organizations must prioritize auditing mechanisms such as a Data Audit Trail.
What is a Data Audit Trail?
A data audit trail refers to the process of collecting and maintaining detailed records of database activities. This includes accessing audit logs to track changes, monitor access, and investigate potential security incidents. Implementing a robust audit trail is essential for ensuring data integrity, compliance, and security. It helps organizations meet regulatory requirements, detect suspicious activities, and maintain a clear record of all database operations. Given these benefits, it’s critical to examine how Percona Server for MySQL implements such capabilities.
Percona Server for MySQL: Native Audit Capabilities
Installing Percona Server for MySQL
The easiest way to install Percona Server for MySQL is by using Docker. You can pull the official Percona image with the following command:
docker pull percona/percona-server:8.0Once the image downloads, you can run the container using this command:
docker run -d --name percona-mysql \
-p 3306:3306 -p 33060:33060 \
-e MYSQL_ROOT_PASSWORD=yourpassword \
percona/percona-server:8.0This command sets up a Percona MySQL server with the root password specified and exposes ports 3306 and 33060 for database access. With the server now operational, the next step involves configuring the audit trail.
Setting Up the Data Audit Trail
Percona Server for MySQL offers native audit capabilities through the Audit Log Plugin, which allows you to track and log database activities seamlessly. To enable the native audit feature, execute the following SQL command:
INSTALL PLUGIN audit_log SONAME 'audit_log.so';To verify whether the audit plugin has been successfully enabled, you can run the following SQL query:
SELECT * FROM information_schema.PLUGINS WHERE PLUGIN_NAME LIKE '%audit%';Next, set the audit policy (i.e., what needs to be logged). The simplest way to test if the feature is working is to set the auditing policy to ALL:
SET GLOBAL audit_log_policy = 'ALL';You’ll also need to set up the format of the logs. Let’s choose JSON for simplicity:
SET GLOBAL audit_log_format = 'JSON';Then, configure the output log file:
SET GLOBAL audit_log_file = '/var/log/mysql/audit.log';Finally, you can check the logs inside the container:
tail -f /var/log/mysql/audit.logKey Features of Percona’s Audit Log Plugin
Notably, Percona’s Audit Log Plugin offers several standout features:
- Granular Logging: Tracks specific user activities, queries, and connections.
- Customizable Filters: Allows filtering by user accounts, SQL command types, and databases.
- Real-Time Monitoring: Provides real-time insights into database activities.
- Tamper-Evident Logs: Ensures the integrity of audit logs by making them resistant to tampering.
Advanced Setup: Percona Server for MySQL Data Audit Trail with DataSunrise
While Percona Server for MySQL is a robust open-source solution for database management, there are scenarios where additional tools can further enhance your audit capabilities. One such tool is DataSunrise, an all-in-one solution for relational databases that offers advanced security and auditing features. Although DataSunrise does not natively support Data Audit Trail for Percona MySQL Server, it can still significantly improve the security and robustness of your database environment. To illustrate, here’s how to integrate DataSunrise with Percona Server:
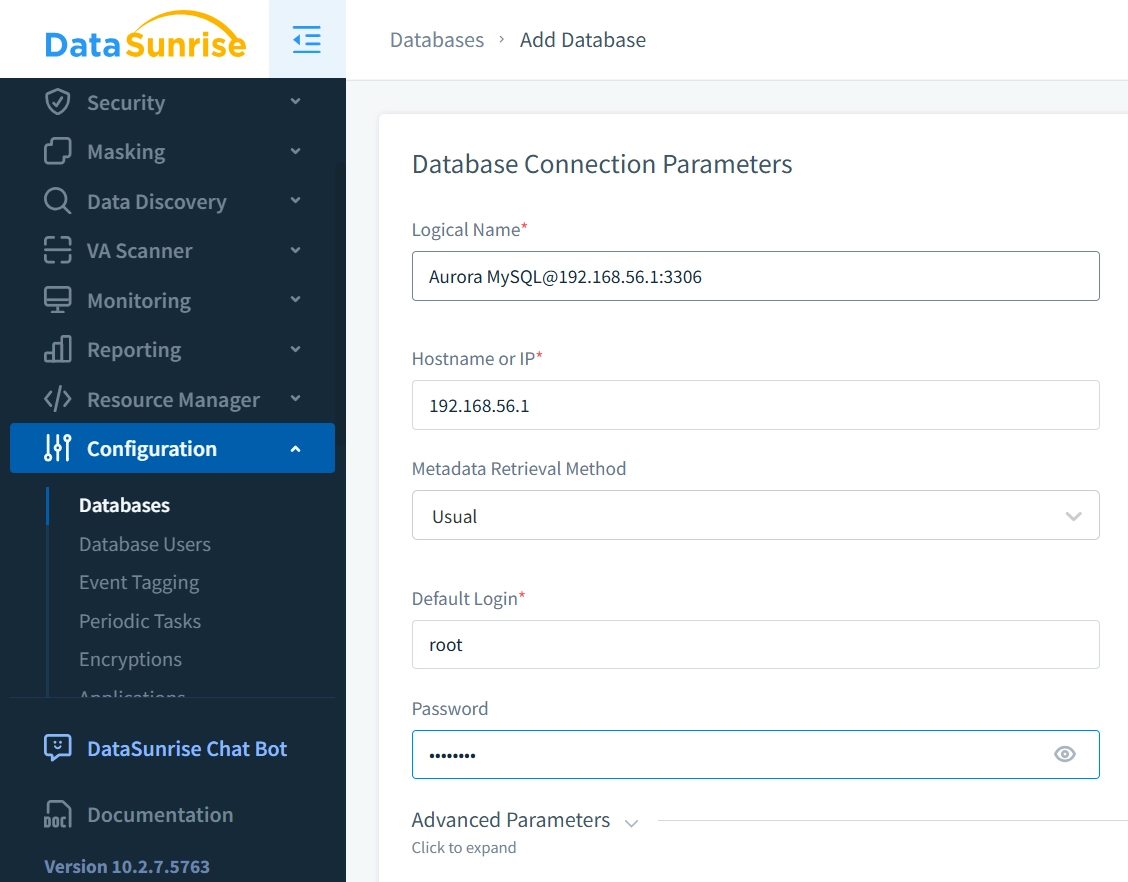
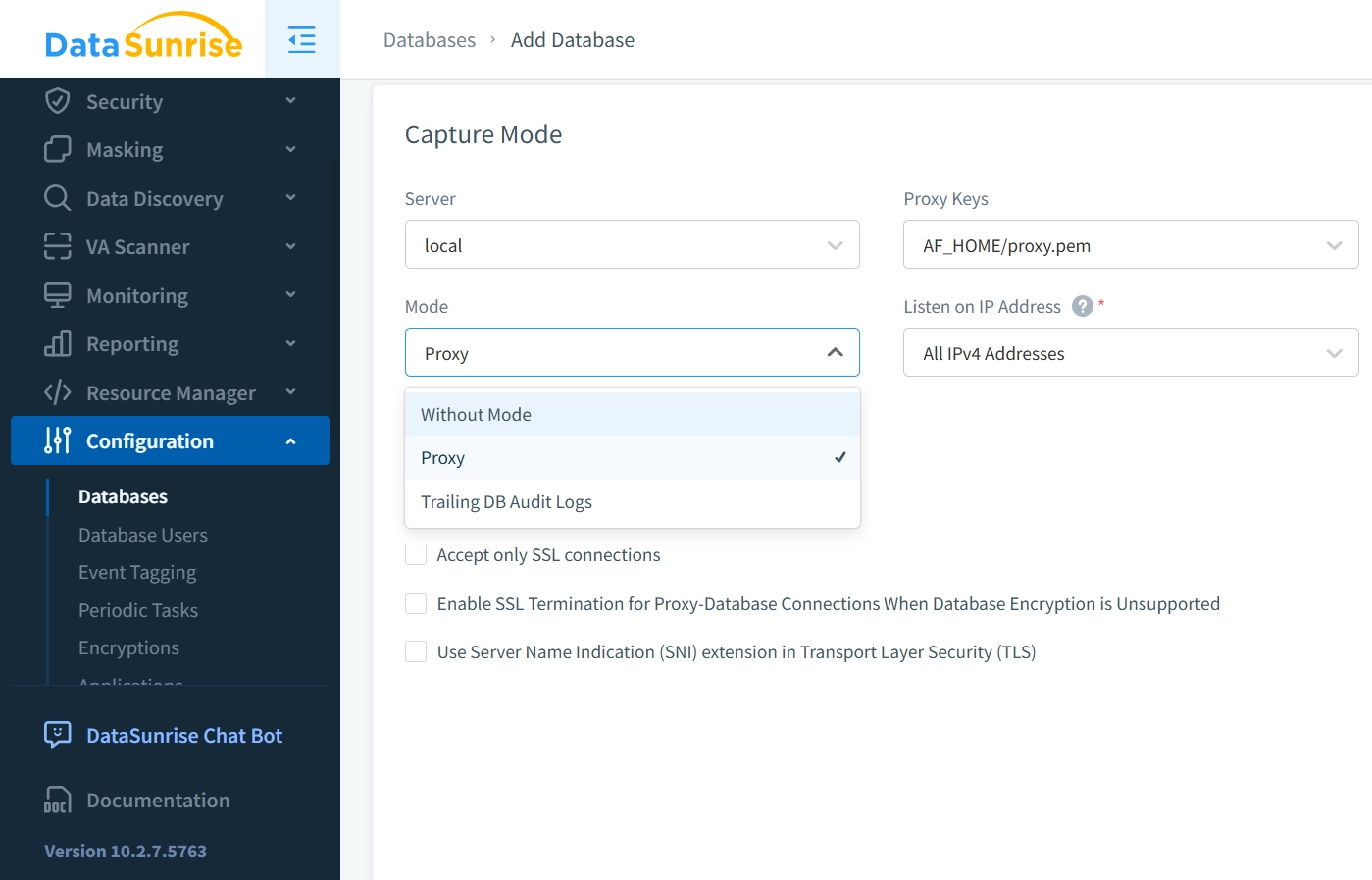
During the setup process, you can select the auditing mode that best suits your requirements:
Once your database is added, you gain access to DataSunrise’s powerful rule-based system, which can be used for database auditing, enhanced security, and more. For example, let’s explore a simple example of creating a security rule to block connections from a specific local address.
Creating a Security Rule
First, create a test audit rule to let DataSunrise gather necessary information about the host you plan to block. Only select the target instance and leave all settings as-is:
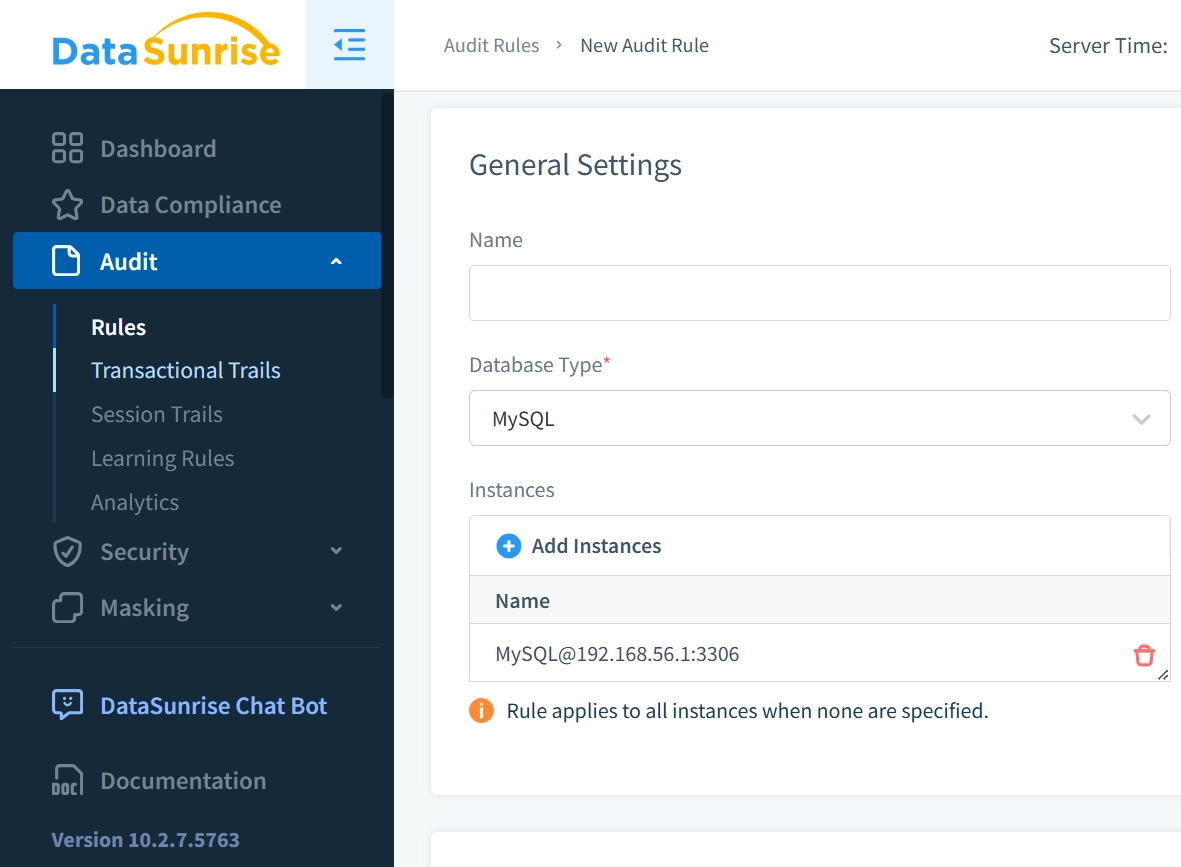
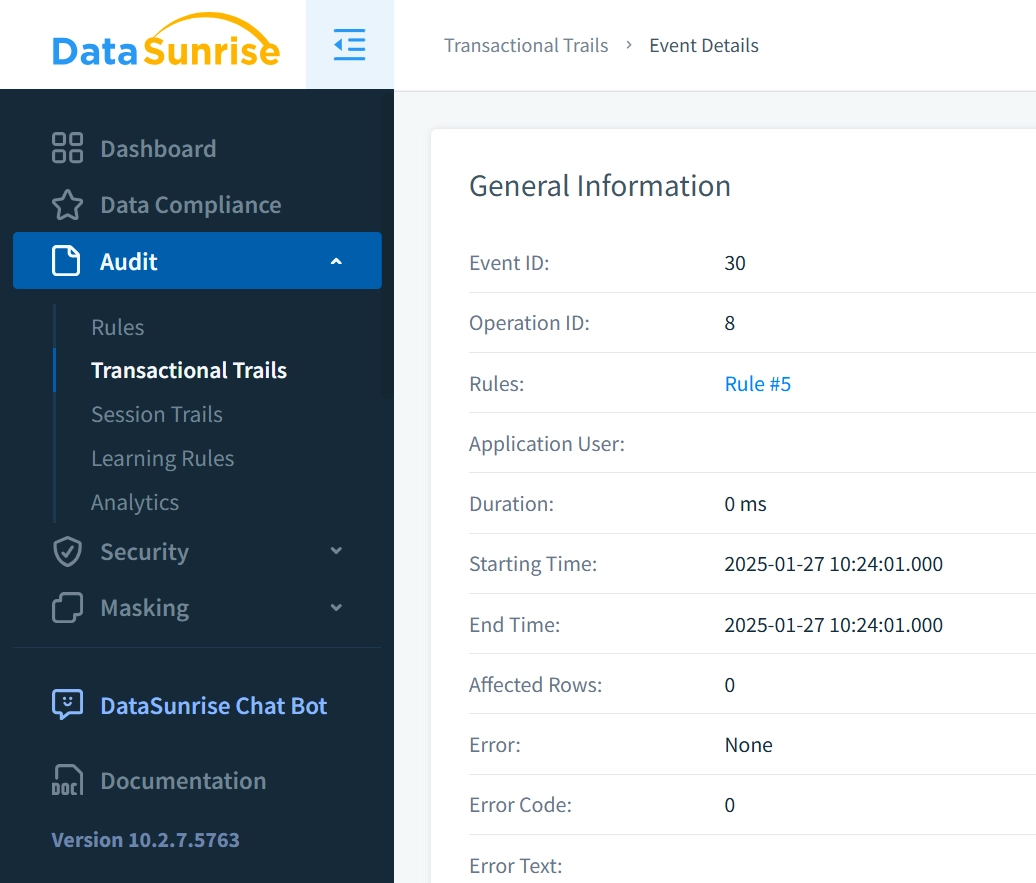
Once this preliminary step is complete, proceed to the ‘Transactional Trails’ tab to analyze recorded activities.
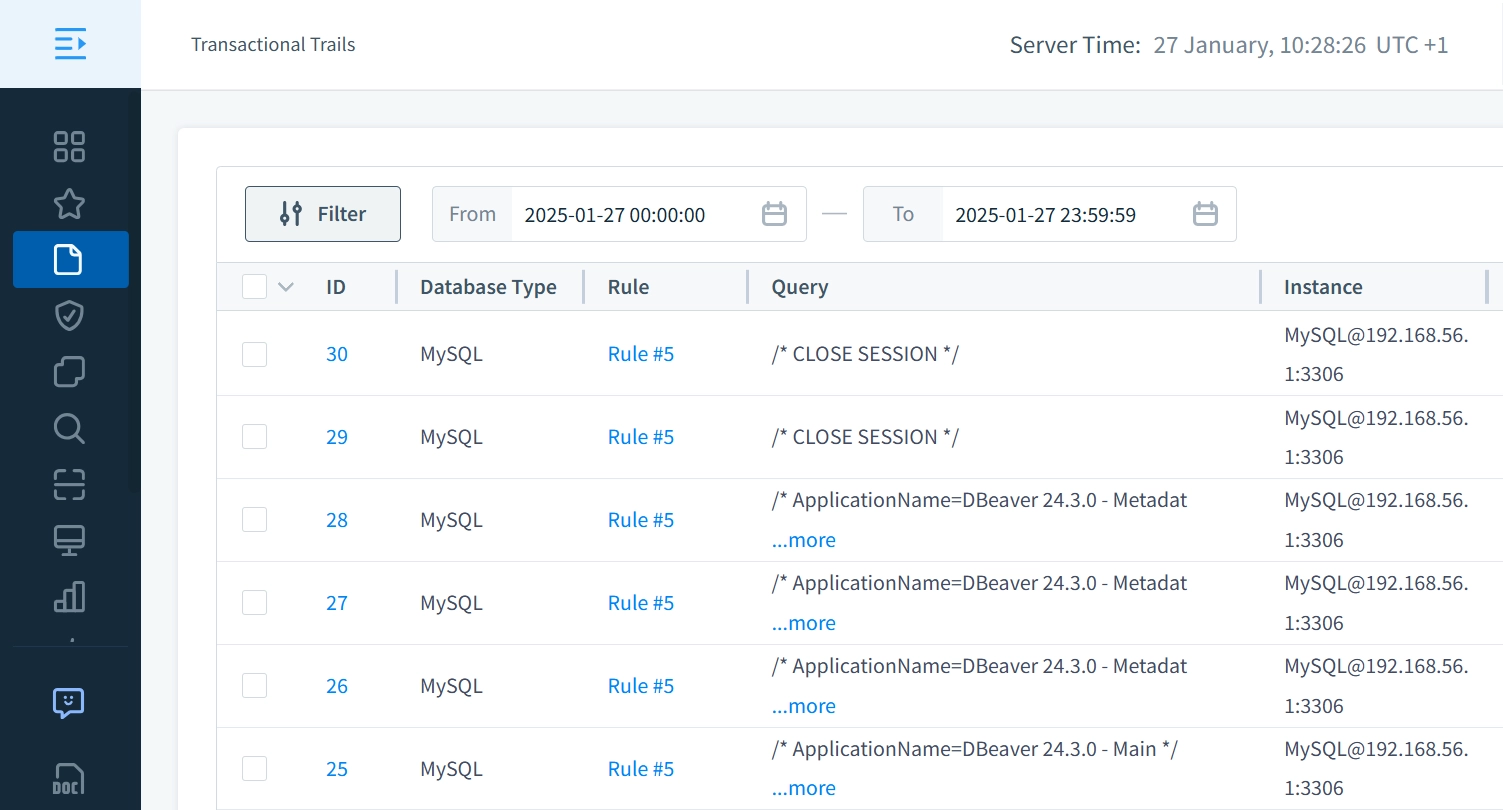
In the record’s detailed information, click the “Create Rule” button:
Select the “Security” rule type and the necessary condition (in this case, “Client host equals 192.168.56.1”), then click the “Create” button:
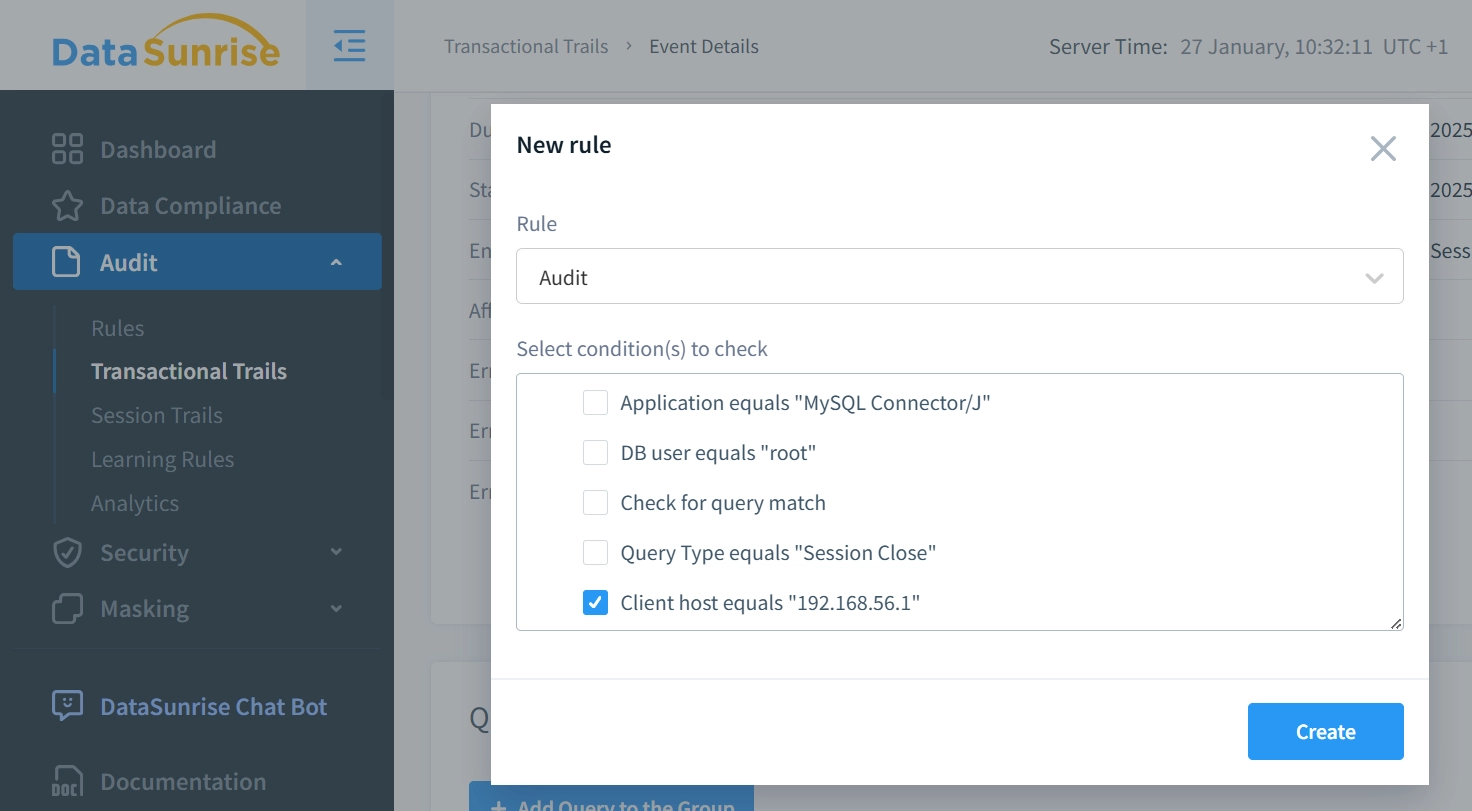
You can leave other settings at their defaults and save the rule.
To validate the rule’s effectiveness, attempt a connection from the restricted host:
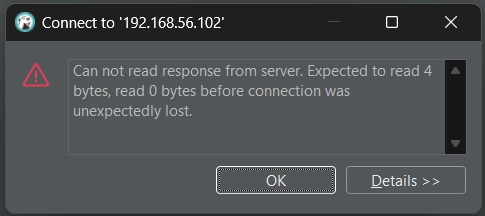
As expected, the connection is blocked because DBeaver (the database manager used) tries to query the database meta when establishing a connection. If you wish to explore the extensive features of DataSunrise further, you can either download the trial version or schedule a personalized online demo.
Percona Server for MySQL Data Audit Trail Best Practices
Some practices might help maintain consistency, security, and compliance in your database environment. To maximize the effectiveness of your audit trail, consider the following best practices:
- Regularly Review Audit Logs: Analyze audit logs periodically to detect suspicious activities or unauthorized access.
- Automate Log Rotation: Use automated log rotation and pruning to manage log file sizes and prevent excessive disk usage.
- Implement Role-Based Access Control: Restrict database access to only those users who need it, and monitor their activities closely.
- Integrate Third-Party Tools: For advanced analytics and reporting, consider integrating third-party tools like DataSunrise to complement Percona’s native capabilities.
Conclusion
Setting up a Data Audit Trail can be challenging, especially for complex database systems. However, by leveraging native capabilities, third-party tools like DataSunrise, and adhering to best practices, you can achieve a secure and compliant database environment. Whether you’re managing a small setup or a large-scale system, investing in a robust audit trail is essential for long-term success. Percona Server for MySQL, with its open-source audit plugin and advanced features, provides a cost-effective and powerful solution for database auditing.
For further details or assistance, refer to the Percona server for MySQL documentation or explore community forums for additional insights. Ultimately, investing in these strategies ensures a secure, compliant, and high-performing database environment.
