
PostgreSQL Audit Trail

Introduction: The Rising Need for Robust Audit Trails
Importance of audit trails cannot be overstated. Especially in the realm of financial statements analysis, the demand for thorough audit capabilities has skyrocketed. This surge is driven by the need for third-party auditing and increased transparency in corporate finances. As we delve into the world of PostgreSQL audit trails, we’ll explore how proper database security measures can safeguard against such catastrophic events.
Did you know that a single accounting irregularity can cause a company’s stock to plummet by up to 30% in just one day? This startling fact underscores the critical nature of maintaining accurate and secure financial records.
The Historical Context: SOX and Data Compliance Standards
The Birth of Sarbanes-Oxley Act
The early 2000s saw a wave of corporate accounting scandals that shook investor confidence. In response, the U.S. Congress passed the Sarbanes-Oxley Act (SOX) in 2002. This landmark legislation aimed to protect investors by improving the accuracy and reliability of corporate disclosures.
Impact on Database Management
SOX introduced stringent requirements for maintaining financial records. Consequently, companies had to implement robust audit trails in their database systems. This shift highlighted the need for advanced database security measures, particularly in systems like PostgreSQL.
The Challenge of Sensitive Data Auditing
While the need for comprehensive audits is clear, the process is far from simple. Financial data is highly sensitive, and its exposure can have severe consequences. Therefore, auditing must strike a delicate balance between thoroughness and data protection.
Key Challenges:
- Maintaining data confidentiality
- Ensuring data integrity
- Providing comprehensive audit logs
- Balancing performance with auditing depth
PostgreSQL’s Built-in Audit Trail Capabilities
PostgreSQL, a powerful open-source database system, offers several built-in features for creating audit trails. These tools provide a foundation for meeting basic auditing requirements.
To enable PostgreSQL’s built-in auditing features, you don’t need any extensions. A few simple configuration changes are all that’s required. For PostgreSQL 16 installed on Ubuntu Linux from the official repositories, follow these steps to edit the configuration file:
sudo nano /etc/postgresql/16/main/postgresql.conf
Next, locate and modify the following lines in the configuration file:
… log_statement = 'all' … log_destination = 'stderr' … log_directory = 'pg_log' log_filename = 'postgresql-%Y-%m-%d_%H%M%S.log' … log_min_duration_statement = 0 # Log all statements and their durations
The first setting logs all SQL queries. The second specifies the log destination. You can choose different log event destinations, but some may require additional modules.
To customize the prefix for log entries, modify this setting:
log_line_prefix = '%m %a [%p] %q%u@%d '
Remember to restart the database after changing the configuration.
sudo systemctl restart postgresql
The logged database activity appears as follows (example from DBeaver metadata loading):
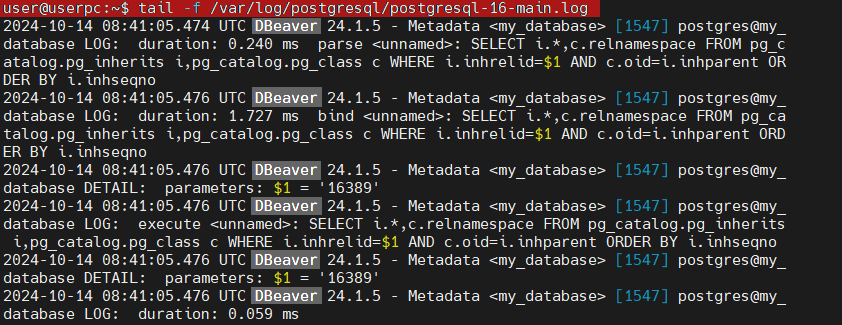
Dynamic Queries
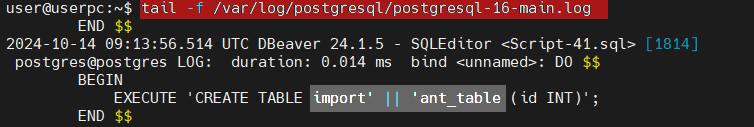
A notable limitation of PostgreSQL’s standard audit capabilities is its handling of PL/pgSQL logging. For instance, consider this example from the pgAudit documentation, which shows a PL/pgSQL anonymous code block dynamically creating a table:
DO $$ BEGIN EXECUTE 'CREATE TABLE import' || 'ant_table (id INT)'; END $$;
may be logged in a way that hinders analysis. The table creation statement is split across the log entry, making it difficult to locate using text searches. This fragmentation complicates audit trail reviews and potential security investigations.
pg_audit Extension
The pg_audit extension enhances PostgreSQL’s native logging capabilities. It provides more detailed audit logs, including information about session start/stop, role changes, and object access.
Limitations of Native PostgreSQL Audit Features
While PostgreSQL’s built-in features are valuable, they have limitations:
- Limited granularity in logging options
- Potential performance impact with extensive logging
- Lack of real-time alerting mechanisms
- Limited options for log analysis and reporting
DataSunrise: Advanced PostgreSQL Audit Trail Solutions
To address these limitations, third-party solutions like DataSunrise offer enhanced audit trail capabilities for PostgreSQL. DataSunrise employs proxy technology to audit PostgreSQL sessions comprehensively.
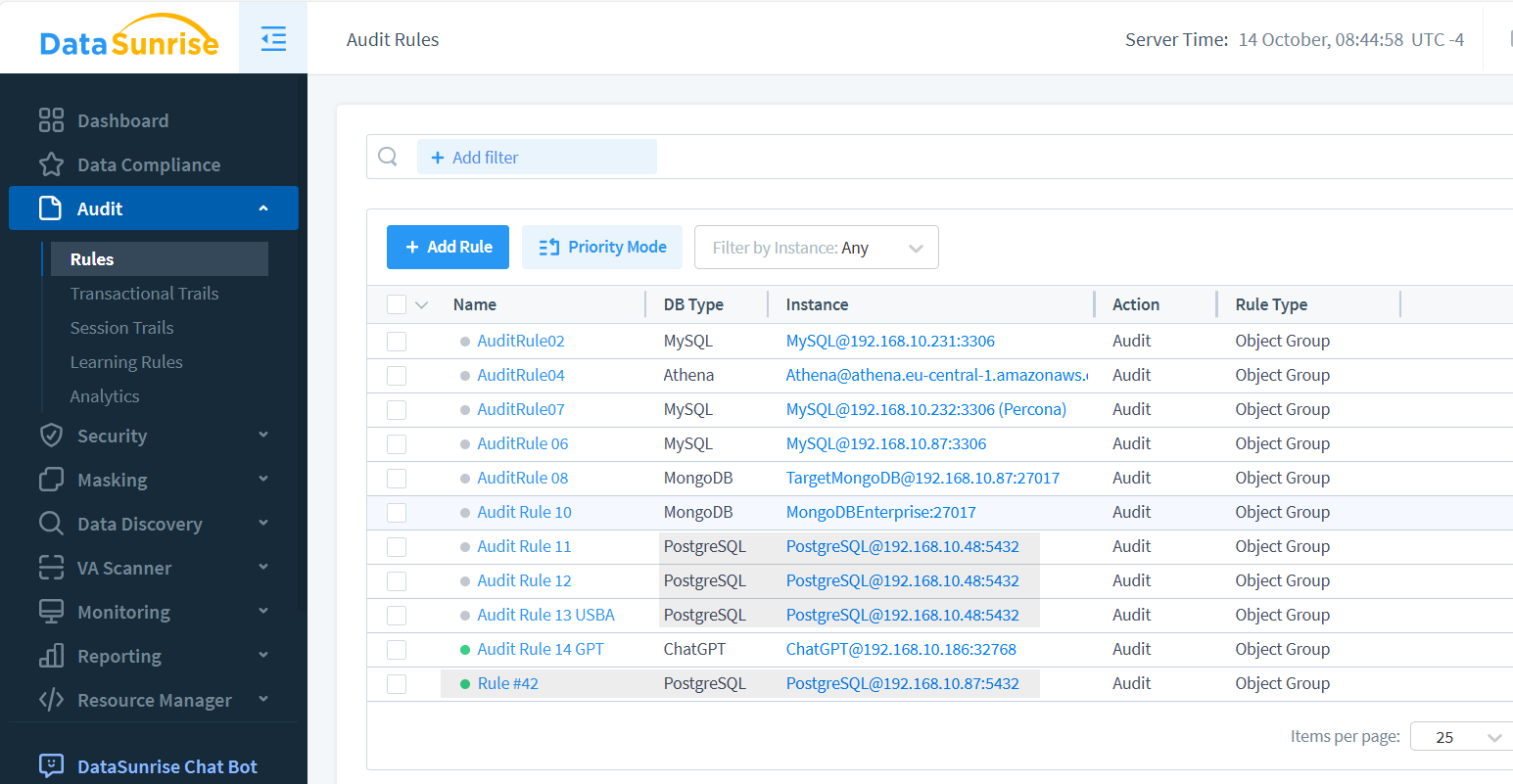
Key Features of DataSunrise PostgreSQL Audit:
- Real-time monitoring of database activity
- Granular control over audit policies
- Advanced log analysis and reporting tools
- Integration with SIEM systems for enhanced security
Comparing Native PostgreSQL Audit vs. DataSunrise
Let’s compare the capabilities of native PostgreSQL audit features with DataSunrise’s offerings:
Feature | Native PostgreSQL | DataSunrise |
Granularity | Limited | High |
Performance Impact | Can be significant | |
Real-time Alerting | Not available | Available for Messengers or email |
Log Analysis Tools | Basic | Advanced |
Compliance Reporting | Limited |
A key advantage of DataSunrise is its comprehensive data security solution, supporting dozens of databases and data warehouses. This solution goes beyond simple auditing, incorporating audit-based learning rules that enable a seamless transition from passive monitoring to active protection.
The system’s adaptive approach allows for controlled growth of security measures based on audit findings. Furthermore, DataSunrise’s rules and security policies can be tailored to the specific data being accessed, ensuring precise and effective protection.
Best Practices for Implementing PostgreSQL Audit Trails
Regardless of the tools used, certain best practices should be followed:
- Define clear audit objectives
- Implement least privilege access
- Regularly review and analyze audit logs
- Ensure secure storage of audit trails
- Establish a retention policy for audit data
The Future of Database Auditing
As data regulations continue to evolve, so too will auditing requirements. Future trends may include:
- AI-powered audit analysis
- Blockchain for immutable audit trails
- Integration with cloud-based security tools
Conclusion: Strengthening Financial Integrity through Robust Audit Trails
In conclusion, PostgreSQL audit trails play a crucial role in maintaining database security, particularly in financial statements analysis. While PostgreSQL offers built-in capabilities, tools like DataSunrise provide enhanced features to meet complex auditing needs.
As financial data becomes increasingly valuable and vulnerable, robust audit trails are no longer optional. They are essential for maintaining trust, ensuring compliance, and protecting against financial fraud.
DataSunrise offers a comprehensive suite of database security tools, including cutting-edge AI-based solutions. Our offerings extend beyond audit trails to include data and LLM sessions monitoring, vulnerability assessment, and more. These flexible tools are designed to meet the evolving needs of modern database security.
For a firsthand experience of how DataSunrise can enhance your PostgreSQL security, we invite you to visit our website to schedule an online demo. Discover how our advanced solutions can fortify your database security and streamline your compliance efforts.
