
Qdrant Data Audit Trail

Introduction
Vector databases like Qdrant often lack robust data audit trails. Yet these databases handle sensitive information for machine learning, NLP, and AI-based search applications. Organizations rely on Qdrant for search optimization, semantic search, and recommendation engines. This makes implementing a Qdrant data audit trail essential for protecting your data.
A comprehensive Qdrant data audit trail tracks who accesses your data, what changes they make, and when these actions happen. Without proper audit mechanisms, organizations risk violating privacy regulations like GDPR and HIPAA. These laws demand strict protection of sensitive information, making data audit trails crucial for compliance.
The Importance of Qdrant Data Audit Trail
Qdrant stores vector embeddings as mathematical representations rather than direct personal identifiers. However, these embeddings still require careful monitoring through data audit trails. The Article 29 Working Party Opinion 05/2014 warns that transformed data needs protection when it could help identify individuals through inference or data combination.
The ISO/IEC 27701:2019 privacy standard reinforces this requirement. It directs organizations to protect mathematical transformations of personal data just like the original information. This makes maintaining a Qdrant data audit trail vital for security and compliance.
The 2017 Equifax data breach demonstrates why organizations need strong data audit trails. Poor data access monitoring led to a breach affecting 147 million people and a $425 million settlement. The GDPR’s Article 30 now requires organizations to log all data processing activities. This includes monitoring transformed data like vector embeddings through comprehensive Qdrant data audit trails.
Qdrant Native Logging Capabilities
Qdrant is a powerful vector database, but it lacks comprehensive native audit logging capabilities. As of now, Qdrant does not have built-in audit-specific features. The available system logs are basic and mainly designed for debugging purposes, providing minimal details about user actions, data access, or data modifications. Relying on these system logs as an audit trail would not meet the regulatory requirements or provide the level of detail needed for data security and compliance.
Because of this, organizations willing to ensure their compliance with regulations, would most likely need to implement custom solutions or third-party tools to ensure that all relevant activities, such as data modifications, access attempts, and query executions, are properly logged.
Search Tracking Implementation Example
A basic approach for implementing Qdrant audit trails could involve wrapping the Qdrant client to capture audit logs for database operations. Below is an example of how one could implement a wrapper to track the search operation:
from qdrant_client import QdrantClient
from datetime import datetime
import json
from pathlib import Path
class AuditedQdrantClient:
def __init__(self, host='localhost', port=6333, log_file='logs/qdrant_audit.jsonl'):
self.client = QdrantClient(host=host, port=port)
self.log_file = log_file
# Create log directory if needed
Path(self.log_file).parent.mkdir(parents=True, exist_ok=True)
def log_operation(self, operation_details: dict):
# Add timestamp
operation_details["timestamp"] = datetime.now().isoformat()
# Log to console
print(f"Audit log: {json.dumps(operation_details, indent=2)}")
# Log to file
with open(self.log_file, 'a') as f:
json.dump(operation_details, f)
f.write('\n')
def search(self, collection_name: str, query_vector: list, **kwargs):
start_time = datetime.now()
try:
results = self.client.search(
collection_name=collection_name,
query_vector=query_vector,
**kwargs
)
self.log_operation({
"operation": "search",
"collection": collection_name,
"parameters": {
"vector_size": len(query_vector),
"limit": kwargs.get('limit', None),
"other_params": kwargs
},
"results_count": len(results),
"status": "success",
"duration_ms": (datetime.now() - start_time).total_seconds() * 1000
})
return results
except Exception as e:
self.log_operation({
"operation": "search",
"collection": collection_name,
"status": "error",
"error": str(e),
"duration_ms": (datetime.now() - start_time).total_seconds() * 1000
})
raise`
This basic wrapper will capture all search operations, which were run through it, including the query parameters, results count, execution time, and status (success or error).
Test Script Example
To test this implementation, you can use the following script, which will add a couple of points, perform a basic search and call the audit script to log the search operation to a JSON file:
`from qdrant_audit import AuditedQdrantClient
# Create client with logging enabled
client = AuditedQdrantClient(log_file='logs/qdrant_audit.jsonl')
try:
# Get collection info
collection_info = client.client.get_collection("test_collection")
print("Collection info:", collection_info)
# Add some test points
client.client.upsert(
collection_name="test_collection",
points=[
{"id": 1, "vector": [0.1, 0.2, 0.3], "payload": {"description": "test point 1"}},
{"id": 2, "vector": [0.2, 0.3, 0.4], "payload": {"description": "test point 2"}}
]
)
print("Test points added")
# Do a search
results = client.search(
collection_name="test_collection",
query_vector=[0.1, 0.2, 0.3],
limit=10
)
print("Search results:", results)
except Exception as e:
print(f"Error: {e}")`
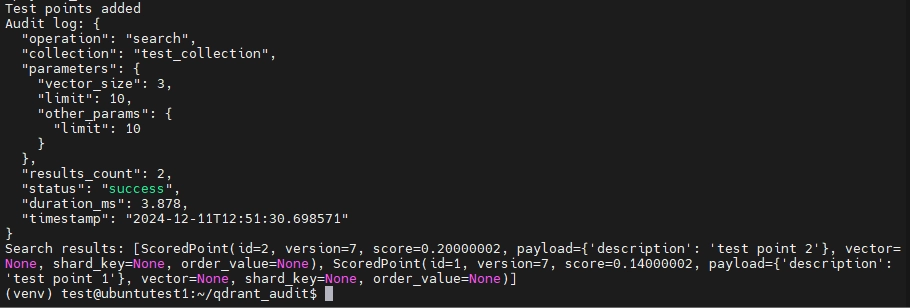
Below is an output of successful execution of the script:
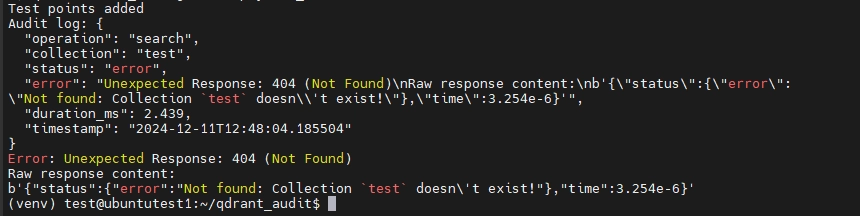
We can also try modifying the test query within the script to perform an operation on a non-existing collection to see if it would also log unsuccessful requests
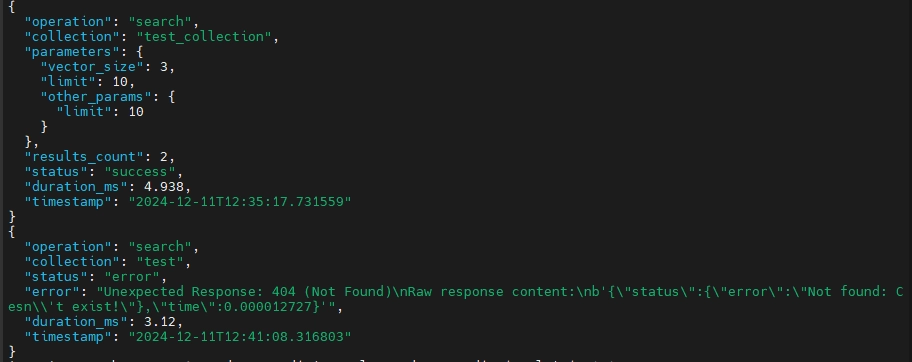
Now, that we have both failed and successful search attempts, we can try accessing the logs:
cat logs/qdrant_audit.jsonl | jq '.'
In summary, this script logs search operations, however it only captures the specific details defined in its implementation and limited to its operational scope.. If you want to include additional details, such as the client's IP address or broader metadata, or if you aim to audit other operations like upsert, delete, or create_collection, you would need to extend the script with additional logic or wrap these methods individually.
Addressing Audit Limitations
While this custom implementation can demonstrate how basic Qdrant data audit trails for search operations could be implemented, it still has significant limitations:
- Limited Coverage: Only the search operation is tracked. Other actions such as
upsert,delete, andcreate_collectionneed additional wrappers. - Client-Specific: To ensure auditing, all interactions with Qdrant must be routed through this wrapper. If another developer uses the default
QdrantClientdirectly, those operations won't be logged. - Manual Maintenance: Building a comprehensive audit system would require significant effort to track all operations and maintain the wrapper code.
To address these limitations, organizations might consider:
1. Custom Solutions
- Develop log collectors tailored for Qdrant.
- Create centralized audit databases for compliance.
- Build custom reporting tools for compliance and anomaly detection.
2. Third-Party Integration
- Leverage log management platforms for centralized storage and processing.
- Integrate with SIEM systems for real-time monitoring and alerts.
- Use compliance monitoring tools to ensure regulatory requirements are met.
3. Architectural Modifications
- Implement proxy layers to capture detailed logs from all user requests.
- Introduce authentication and authorization services to track access controls.
- Build dedicated audit logging services to capture and analyze changes in real time.
Why DataSunrise is the Perfect Solution for Qdrant
While custom solutions and third-party integrations can help address audit limitations in Qdrant, a more seamless and effective option is integrating DataSunrise with Qdrant. DataSunrise offers a comprehensive data auditing solution that can track all database interactions, ensuring compliance with regulations and enhancing data security.
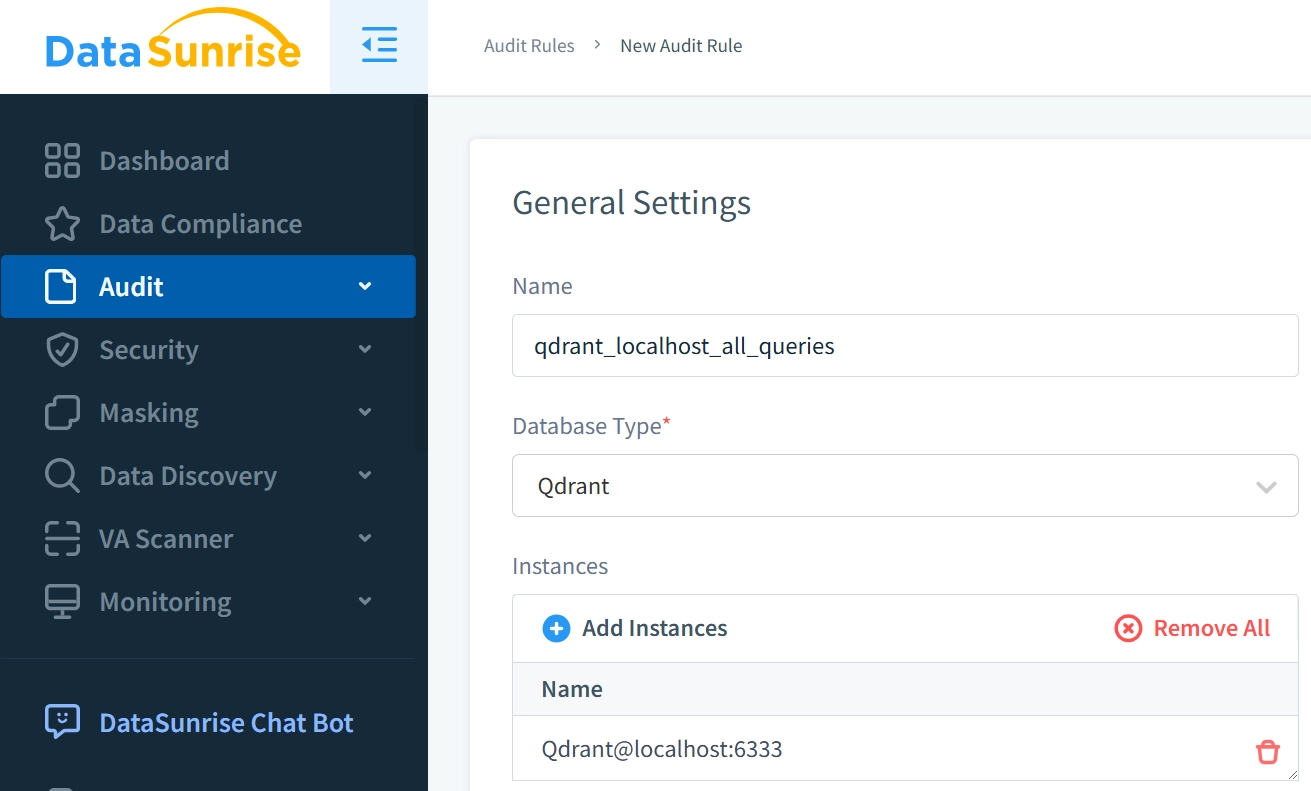
DataSunrise provides an extensive range of audit capabilities, including:
- Full Data Change Tracking: Monitors all data modifications, including insertions, updates, and deletions.
- Complete User Attribution: Tracks session IDs, user roles, and application details.
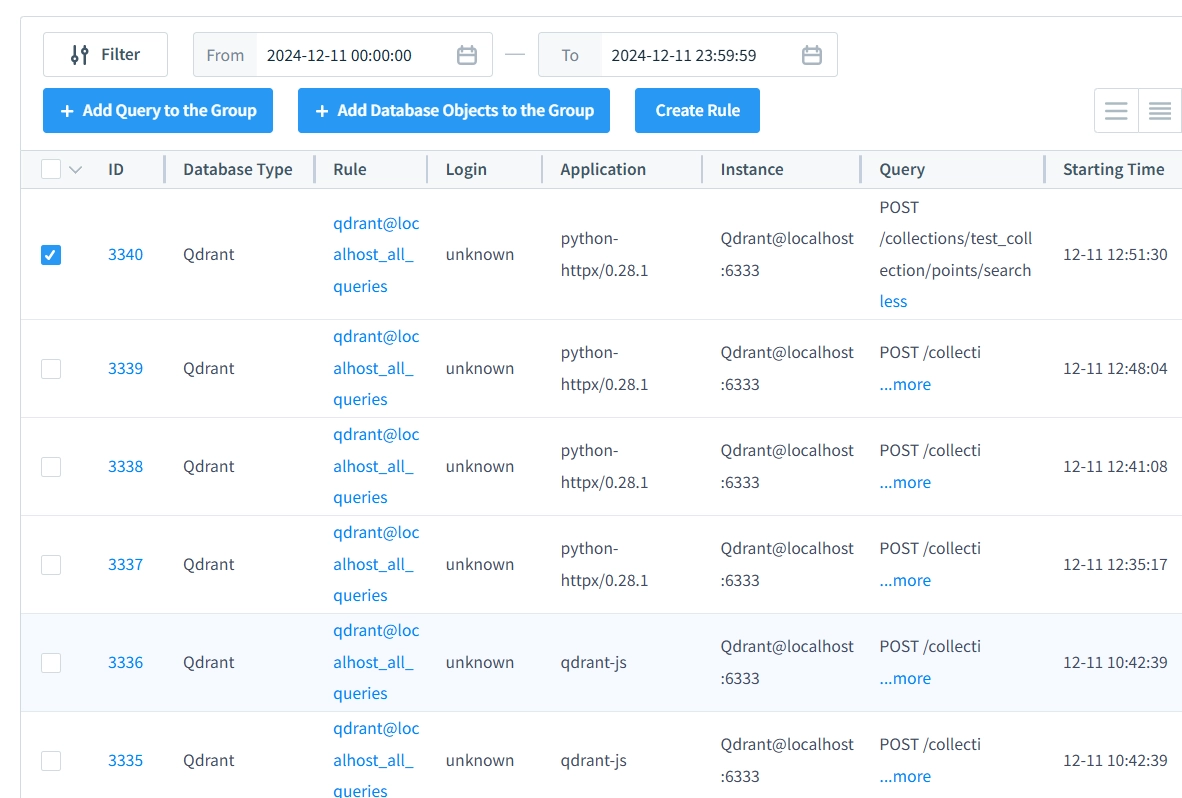
- Real-Time Query Logging: Captures the full query lifecycle, from execution to results.
- Access Monitoring: Logs all access attempts, successful or not, along with the associated actions.
- Regulatory Compliance: Ensures compliance with GDPR, HIPAA, and other data protection standards.
With DataSunrise, organizations can automate the monitoring of Qdrant’s database operations, reduce the complexity of manual logging, and significantly enhance their ability to comply with regulatory standards.
Conclusion
While Qdrant is a powerful vector database, its native audit logging capabilities are minimal and insufficient for compliance and security purposes. By implementing custom wrappers or leveraging third-party tools, organizations can achieve a basic level of auditability. However, for comprehensive, scalable, and easily managed audit trails, integrating a solution like DataSunrise is the best approach.
DataSunrise offers an advanced, out-of-the-box solution for tracking and monitoring all Qdrant data interactions, making it an invaluable tool for organizations aiming to protect sensitive data and ensure compliance with regulatory standards. Experience the benefits firsthand—schedule an online demo today and redefine your Qdrant data audit trails collection process with DataSunrise.
