
Qdrant Database Activity History

Introduction
Qdrant excels as a vector similarity search engine, powering recommendation systems and AI-powered insights. However, maintaining a comprehensive Qdrant database activity history presents significant challenges due to its lack of built-in auditing and user management features. While Qdrant’s performance is impressive, its native capabilities fall short when it comes to tracking database activities, making it difficult to monitor interactions and detect unauthorized access.
The 2016 Uber data breach demonstrated how inadequate database activity logging can severely impact security and incident response, highlighting why robust tracking systems are essential.
To address this, Role-Based Access Control (RBAC) can be implemented using JWT tokens, allowing administrators to manage collection-specific permissions. Though this approach provides basic access control, organizations still need additional solutions for comprehensive activity logging. In this guide, we will explore how implementing JWT-based RBAC can enhance Qdrant security and provide strategies to maintain detailed Qdrant database activity history for further auditing and compliance purposes.
Setting Up Qdrant with JWT for Role-Based Access Control
Step 1: Set Up Local Qdrant Instance
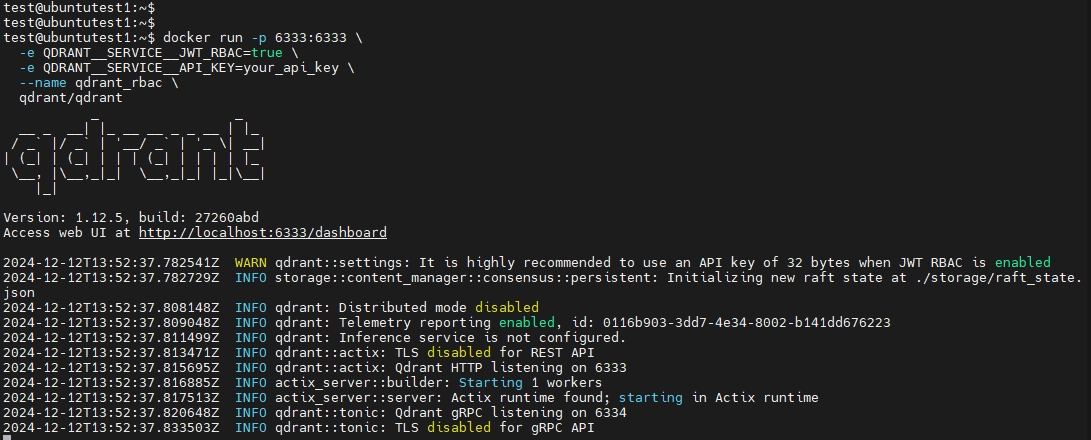
To begin, ensure Docker is installed on your system. Then, run the following command to start a Qdrant instance with JWT authentication enabled:
Run Qdrant Using Docker:
docker run -p 6333:6333 \
-e QDRANT__SERVICE__JWT_RBAC=true \
-e QDRANT__SERVICE__API_KEY=your_api_key \
--name qdrant_rbac \
qdrant/qdrant
This command starts Qdrant on localhost:6333 with JWT-based RBAC enabled. Replace your_api_key with your desired API key.
Configuring Qdrant Manually
If you’re not using Docker, you can enable JWT RBAC by modifying the qdrant.yaml configuration file:
jwt_rbac: true
api_key: "your_api_key"
Restart Qdrant to apply these changes.
Step 2: Create Collections
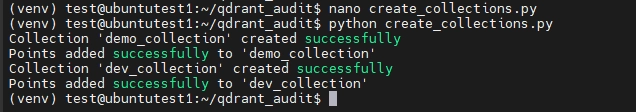
For testing purposes, use the following script to create collections with access control capabilities:
create_collections.py
import requests
base_url = "http://localhost:6333"
headers = {"Authorization": "Bearer your_api_key"}
def create_collection(name):
r = requests.put(
f"{base_url}/collections/{name}",
json={"vectors": {"size": 4, "distance": "Dot"}},
headers=headers
)
print(f"Collection '{name}' {'created successfully' if r.status_code == 200 else f'error: {r.status_code}'}")
def add_points(name):
r = requests.put(
f"{base_url}/collections/{name}/points",
json={"points": [{"id": 1, "vector": [0.1, 0.9, 0.3, 0.7], "payload": {"city": "New York"}}]},
headers=headers
)
print(f"Points {'added successfully' if r.status_code == 200 else f'error: {r.status_code}'} to '{name}'")
for name in ["demo_collection", "dev_collection"]:
create_collection(name)
add_points(name)
Step 3: Generate JWT Tokens with Access Levels
Install PyJWT to Generate JWTs:
You need to install PyJWT for Python to generate the JWTs. Run the following command:
pip install pyjwt`
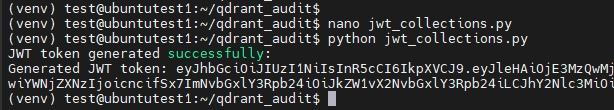
JWT tokens define access permissions for collections. Use the following script to generate JWT token with custom access levels:
jwt_collections.py
import jwt
import datetime
api_key = "your_api_key"
payload = {
"exp": datetime.datetime.now(datetime.timezone.utc) + datetime.timedelta(hours=1),
"access": [
{"collection": "dev_collection", "access": "rw"},
{"collection": "demo_collection", "access": "r"}
]
}
token = jwt.encode(payload, api_key, algorithm="HS256")
print("JWT token generated successfully:")
print(token)
This script generates a JWT token granting:
- Read-write access to
dev_collection. - Read-only access to
demo_collection.
Step 4: Test Access Controls
Use this script to test the generated JWT tokens:
jwt_test.py
import requests
QDRANT_URL = 'http://localhost:6333'
JWT_TOKEN = input("Enter JWT token: ")
headers = {'Authorization': f'Bearer {JWT_TOKEN}'}
def test_collection_access(collection_name):
response = requests.post(
f'{QDRANT_URL}/collections/{collection_name}/points/scroll',
json={"limit": 10, "with_payload": True, "with_vector": True},
headers=headers
)
print(f"{'✓ success' if response.status_code == 200 else '✗ failed'} {collection_name}: Read access - {response.status_code}")
return response
def test_add_points(collection_name):
points_data = {
"points": [
{"id": 1, "vector": [0.1, 0.9, 0.3, 0.7], "payload": {"city": "New York"}},
{"id": 2, "vector": [0.4, 0.5, 0.8, 0.1], "payload": {"city": "Los Angeles"}}
]
}
response = requests.put(
f'{QDRANT_URL}/collections/{collection_name}/points',
json=points_data,
headers=headers
)
print(f"{'✓ success' if response.status_code == 200 else '✗ failed'} {collection_name}: Write access - {response.status_code}")
return response
collections = ['dev_collection', 'demo_collection']
for col in collections:
test_collection_access(col)
test_add_points(col)
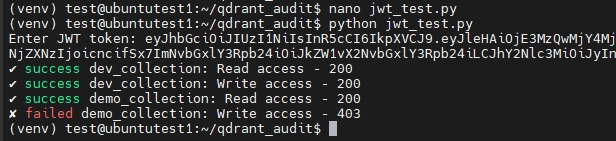
When run, this script:
- Attempts to read points from
dev_collectionanddemo_collection. - Attempts to add points to both collections.
Expected Results:
dev_collection: Both read and write operations succeed.demo_collection: Only read operations succeed; write operations fail.
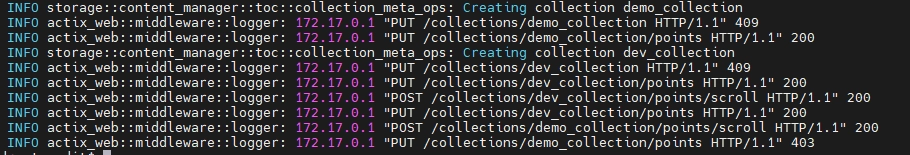
Step 5: Check system logs
To further validate access control behavior and monitor system activity, you can review Qdrant's system logs.
docker logs qdrant_rbac
For more information about access controls in Qdrant, you can refer to the security page in the official documentation.
Challenges of Tracking Qdrant Database Activity History
Qdrant, while excelling as a vector database for similarity search and machine learning, lacks robust native tools for tracking database activity history. This limitation presents significant challenges for organizations that require detailed logging for compliance, security, or operational visibility.
1. Limited Native Audit Functionality
Qdrant provides no built-in audit logging. Users must rely on basic system logs, which are:
- Minimal in detail: Logs lack granularity, making it hard to track queries, modifications, or user interactions.
- Unfit for audits: They offer little insight into user actions, unauthorized access, or suspicious behavior, leaving compliance needs unmet.
2. Limitations of JWT Token Access Control
While JWT tokens enable role-based access control (RBAC), they fall short as an auditing solution:
- Complex to manage: Configuring and maintaining tokens for different users and roles is time-consuming and prone to errors.
- No activity insights: Tokens restrict access but don’t log actions, leaving gaps in visibility.
- Scalability issues: Managing access across many users and collections can quickly become overwhelming.
3. Security and Compliance Risks
Without detailed activity tracking or session monitoring, organizations face significant challenges:
- Limited visibility: Qdrant does not log critical actions like queries, vector additions, or collection modifications in an accessible format.
- Compliance hurdles: Meeting standards like GDPR, HIPAA, or SOC 2 is difficult without comprehensive audit trails.
In short, Qdrant’s current capabilities are inadequate for robust activity tracking. While JWT tokens address some access control needs, they require expertise to implement and maintain, offering limited scope for audit and compliance purposes.
Simplify Qdrant Database Activity History and Security with DataSunrise
While implementing JWT authentication and access control in Qdrant provides basic security, it requires significant configuration effort. DataSunrise, with its robust security capabilities, offers a more comprehensive and efficient alternative.
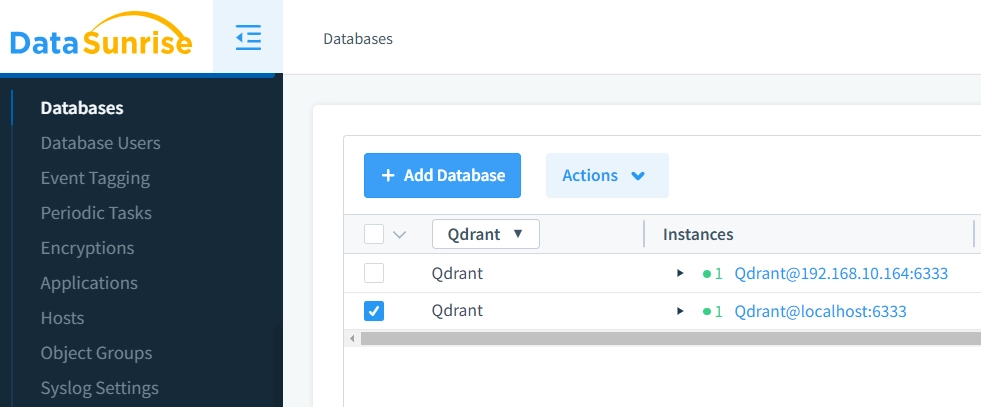
DataSunrise offers:
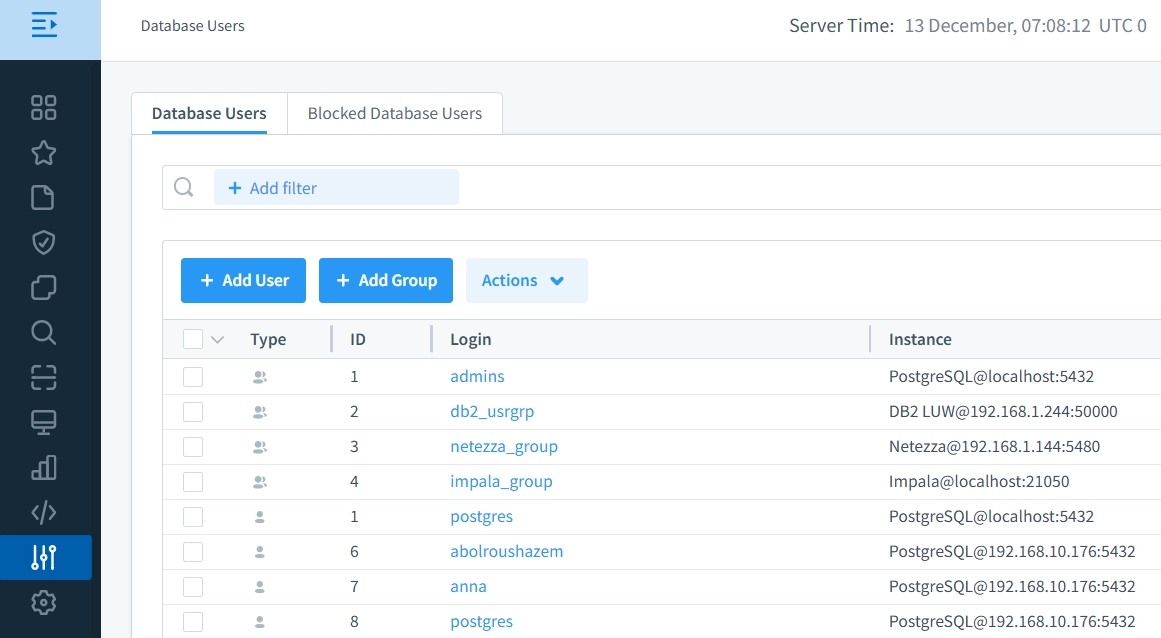
- Granular Role Management: Implement fine-grained data access control policies that precisely define who can access specific collections and data, allowing organizations to enforce the principle of least privilege across their database infrastructure.
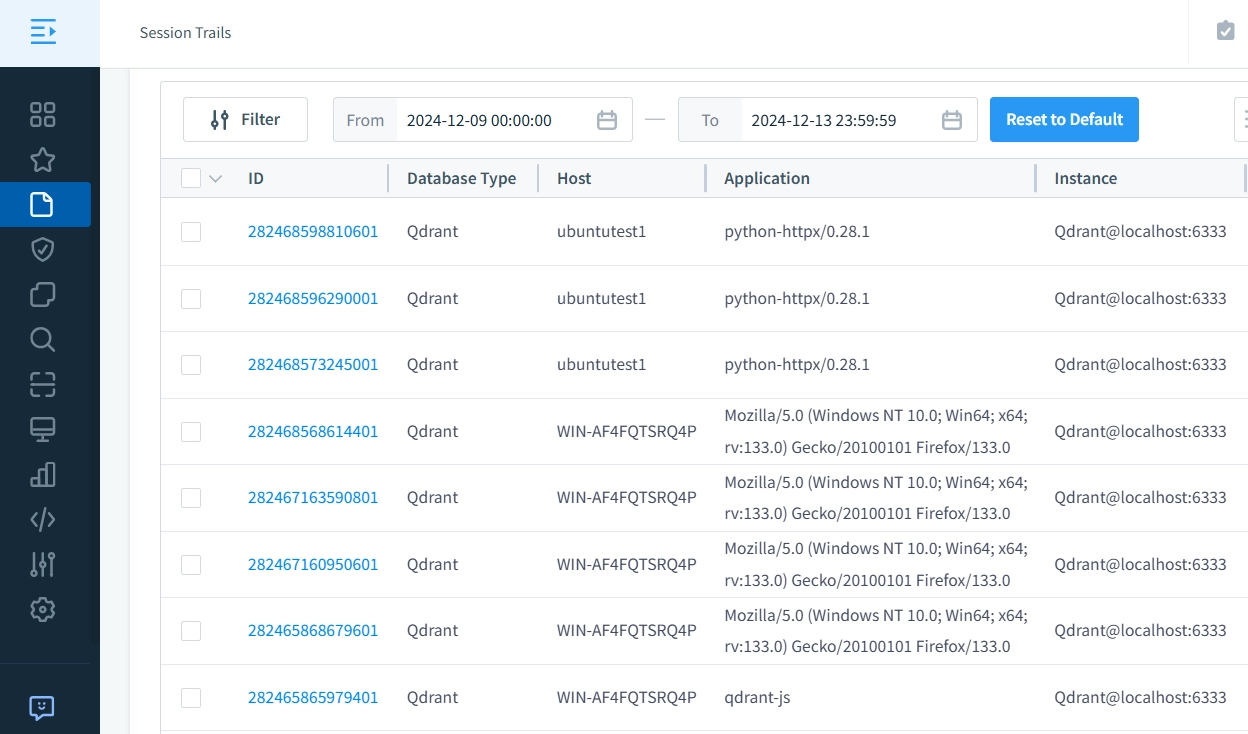
- Detailed Session Tracking: Track user sessions in real-time to gain insights into who is accessing your Qdrant database and what actions they are performing. This feature allows for monitoring activities of individual users, ensuring full visibility of database operations and enhancing accountability.
- Complete Audit Trails: Generate detailed database activity logs, including extensive audit trails, to monitor and analyze every action performed on your Qdrant database.
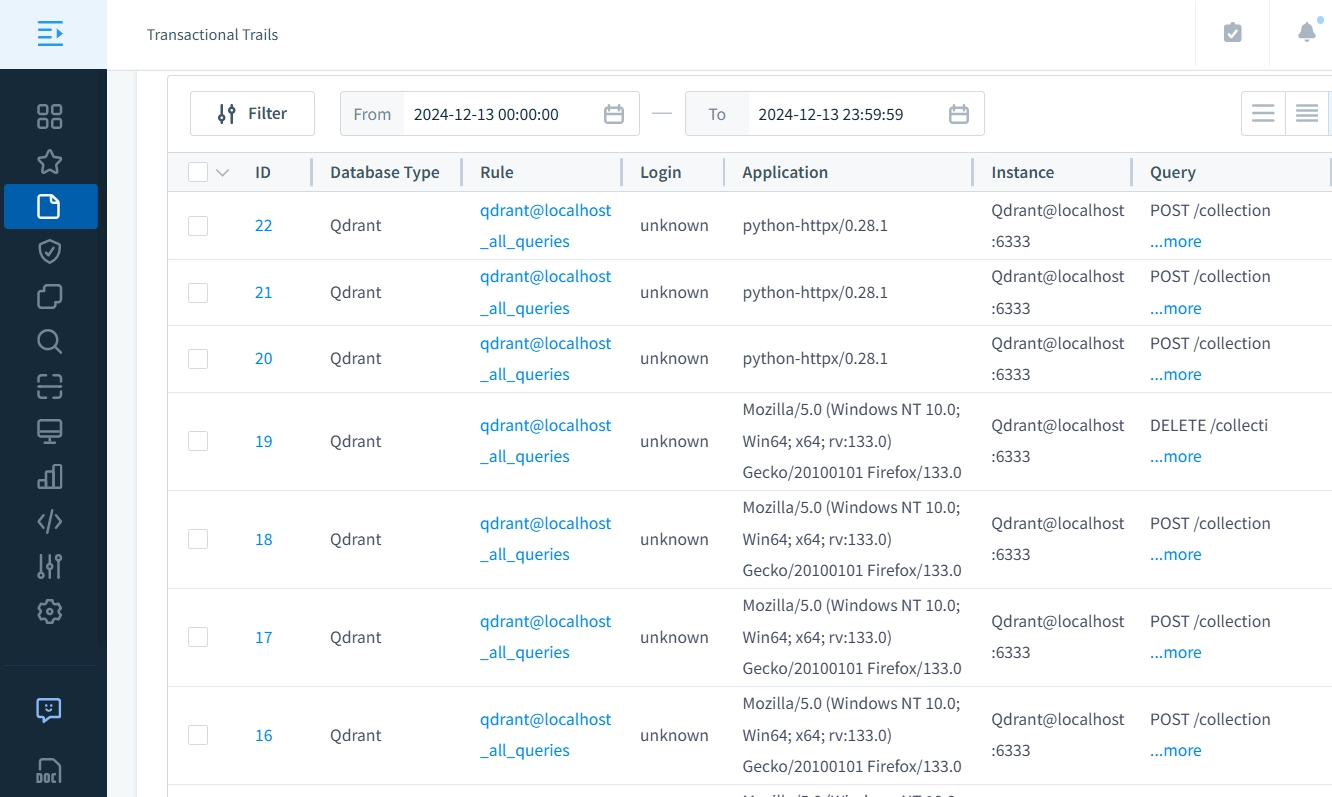
DataSunrise Advantages
DataSunrise unifies database security management by providing comprehensive audit trails and security policies through a single interface, eliminating the need for manual JWT configuration, log analysis, or multiple monitoring tools. This consolidated approach offers administrators complete visibility into database operations while simplifying auditing, access control, and compliance management.
Enhancing Qdrant Database Activity History with DataSunrise
As the adoption of Qdrant accelerates, addressing its limitations in user functionality and security becomes vital. While JWT-based RBAC lays a foundational framework for access control, it falls short in providing robust security and comprehensive database activity tracking. This is where DataSunrise shines, offering advanced solutions to bridge these gaps.
DataSunrise integration can allow organizations to achieve precise access control and maintain an extensive Qdrant database activity history. With detailed audit trails and multi-faceted filtering options, DataSunrise ensures Qdrant databases are secure and fully compliant with regulatory standards.
Take the next step toward redefining your Qdrant database activity history management—schedule an online demo today and experience the unparalleled benefits of DataSunrise’s advanced monitoring and auditing capabilities.
Next
